Analytic-Based and Non-Traditional Approaches
Dr. Paul Davis, principal researcher, Pardee Graduate School, RAND Corporation, led the panel titled “Analytic-based Approaches for Deterrence Analysis” at the first workshop session. He began by discussing some lessons learned from past work, including the following: (1) study deterrence with relatively simple models; (2) the paradigm of “rational actors” is not viable; and (3) use alternative models to defeat tyranny of best estimate since our best-estimate guesses of utility functions for the other side are not that useful and “history is replete with us getting it wrong.” Dr. Davis believes much of past deterrence work has been driven by theory, and new methods can be brought to bear to inform revised theory, such as evidence from case studies, crowd-sourcing to uncover factors and mindsets, the man-machine search of data for patterns, and “historical-statistical empirical analysis.” Dr. Davis added that newly developed factor-tree methods (qualitative modeling) are also quite useful in thinking about deterrence and other issues. Similarly, he noted that simple models, describable in a few viewgraphs, can frame potential adversary reasoning to help inform U.S. strategy. This can be called, with an admittedly pretentious label, synthetic cognitive modeling because it can be actor specific and highlight what the adversary worries about and has to balance.
Dr. Rob Axtell, chair, Department of Computational Social Science, Krasnow Institue for Advanced Study, George Mason University, followed with a presentation titled “Robustness and Resilience of Models Involving Social Agents.” An abstract of Dr. Axtell’s presentation is provided in Box 4-1.
Dr. Rita Parhad, associate partner, Monitor360, then addressed elicitation of subject-matter experts and crowd-sourcing. To illustrate the point about whether an adversary does or does not want stability, she raised a series of questions like (1) how can we tailor deterrence in that situation; (2) what can we learn from the adversary's response to our actions, messages, and policies; and (3) how can we “profile” adversaries with complex, factionalized, or opaque decision making? For deterrence to be effective she believes the socio-cultural context, along with associated motivations and actions, needs to be understood and elicitation of subject-matter experts and crowd-sourcing offer analytic techniques to gather non-U.S. perspectives and insights. Typical products of that analytical process include (1) master narratives, such as mindsets and beliefs for a country; (2) analyses of the future, such as persistent and forward-
BOX 4-1
Robustness and Resilience of Models Involving Social Agents
Dr. Rob Axtell, George Mason University
We are experiencing a revolution in the social sciences as conventional conceptions of human behavior—rationality, well-mixedness, equilibrium—are replaced by (1) the behavioral revolution in which experiments are used to elicit human behavior in specific environments, and (2) the computational revolution, in which we can scale up from the 10-25 subjects typical in the laboratory to tens of thousands or even millions of agents. Individual agent-based computational experiments in such environments can point out brittleness of policies based on optimization calculi. Systematic exploration of policy spaces can lead to more robust and resilient policies than can be predicted or achieved by other means. In order to accomplish this research program, significant resources need to be dedicated to understanding behavior in relevant domains. Specifically, regarding deterrence, signatures of sudden changes in societal behavior are not well understood, with conflicting hypotheses being advanced—e.g., some researchers claim that loss of diversity brings on rapid change while others argue that rapid growth of diversity signals abrupt transitions. An extended example from finance was indicated as a harbinger of things to come across the social sciences.
looking critical questions for a country; and (3) key influencers, such as understanding who matters in a country and how they might act, all of which could be helpful for deterrence by providing a critical context in which to make decisions.
Dr. Rafael Alonso, vice president and division manager, Autonomy and Analytics Division, Science Applications International Corporation (SAIC), finished the panel presentations by focusing on social network analysis. He indicated that most current deterrence tools do not work all that well in the context of state actors leveraging non-state actors, including terrorists. If a state is using a terrorist network, deterrence becomes very hard. He noted that it is difficult to understand the power relationships in those kinds of social networks, and the networks are seldom complete and change a lot. Mining the financial and communications data of such networks has been effective, however. He described some improvements that are underway, such as enriching text data with video or imagery and better analyzing power relationships in social networks. Dr. Alonso also touched on crowd-sourcing, suggesting its intuitive appeal due to the “safety” of large numbers may be illusory because—for example, of uninformed opinions and possible group-think—the desired result is not the same as dividing the group result by the number of individuals in the group (N).
Some key comments from various workshop participants followed. For example, all three techniques offer a framework. There is potentially useful information in these methods. After a U.S. announcement, one could sweep through responses—for example, in a country's media to suggest how the announcement was received. A participant posited sentiment mining as a tool for how to gauge what a whole population is thinking. A participant argued that these tools are more art than science. Another participant questioned how these tools could be used for deterrence. There was a suggestion that agent-based modeling captures complex behaviors,
so, in principal, it can be used to see the behaviors of N states interacting. Crowd-sourcing [which refers to learning from experts and is not the same as social media or sentiment mining from a broad population], according to another participant, could be useful where leadership is centralized but cares about how the people feel (e.g., China). Another view was that for crowd-sourcing to be viable, one must get subject-matter experts engaged from day one. Crowd-sourcing is potentially useful, not just for what deters but for what can reassure allies. Several participants agreed that these tools are good for expanding knowledge of possible outcomes and allow for greater numbers of actors and interactions.
During the second workshop session, two speakers explained the analytical techniques their organizations employ for strategic forces. These presentations, summarized below, covered in more detail some of the information discussed at the first workshop session.
Mr. Patrick McKenna, chief, Plans Evaluation and Research Division, U.S. Strategic Command (USSTRATCOM), provided an overview of the analytic methodology used by USSTRATCOM to develop the desired strategic force structure and associated capabilities. He emphasized that strategy (against the backdrop of world environment) drives the force requirements. Strategy is followed by desired ends and ways and means of achieving the ends. He provided an illustrative strategic end, deter aggression against the United States and its allies and maintain stability. One of several effective ways to do that might be demonstrate credible capability to hold at risk values or capabilities or assets an adversary values highly. Mr. McKenna stated that one of several assessment metrics for that way could be difference between U.S. and adversary force size in terms of prompt, survivable weapons; this metric would then be used as part of the overall analysis of, for example, required U.S. counterforce capability (numbers and types of missiles and bombers)—the means. In response to a question about bringing metrics into a political debate, Mr. McKenna said his organization provides quantitative indicators with a qualitative summary, but he thought they could do better, and he challenged the workshop participants to help.
Maj Justin Sorice, scientific analyst, Air Force Office of Studies and Analyses, Assessments, and Lessons Learned, provided a presentation titled “A Framework for Strategic Deterrence Analysis.” An abstract of Maj Sorice’s presentation is found in Box 4-2.
BOX 4-2
A Framework for Strategic Deterrence Analysis
Maj Justin Sorice, Air Force Office of Studies and Analyses, Assessments, and Lessons Learned
An analytical framework is required to examine the interdependencies of strategies, capabilities and partnerships given planned as well as potential future reductions in the role and number of United States nuclear weapons. This presentation will examine how such a framework can be used to allow the U.S. military to think about studying strategic deterrence in the 21st century security environment, what factors and initial assumptions are required, and what conclusions are derived from the proposed framework.
NON-TRADITIONAL ANALYTIC APPROACHES
Dr. Allison Astorino-Courtois, executive vice president, National Security Innovations, Inc., set the stage by leading a panel titled “Non-Traditional Approaches to Deterrence” at the first workshop session. “How does all this relate to deterrence?” she asked rhetorically and answered, “We do not know.” She acknowledged the complex relationships, multi-actor scenarios, and nth-order effects of the 21st century and introduced a suggested set of organizing columns, as shown in Figure 4-1, which could help characterize the tools, approaches, and methods.
For example, analysis of social networks and leader profiling could be selected from a long list of possible tools (column 1) to be used to help characterize a threat (one choice from many possible purposes in column 2) in one of several domains (nuclear, non-nuclear in column 3) under conditions of peace or conflict (column 4). She noted that this organization demonstrates the broad net of conditions under which these tools might be applicable. In other words, the question must be known before the right tools can be employed.
CAPT Gail Kulisch (USCG, Ret.), Kiernan Group Holdings, provided a presentation titled “The Crafty Bastard Innovation Cycle and Solution Creation Methodology.”1 An abstract of CAPT Kulisch’s presentation is found in Box 4-3.
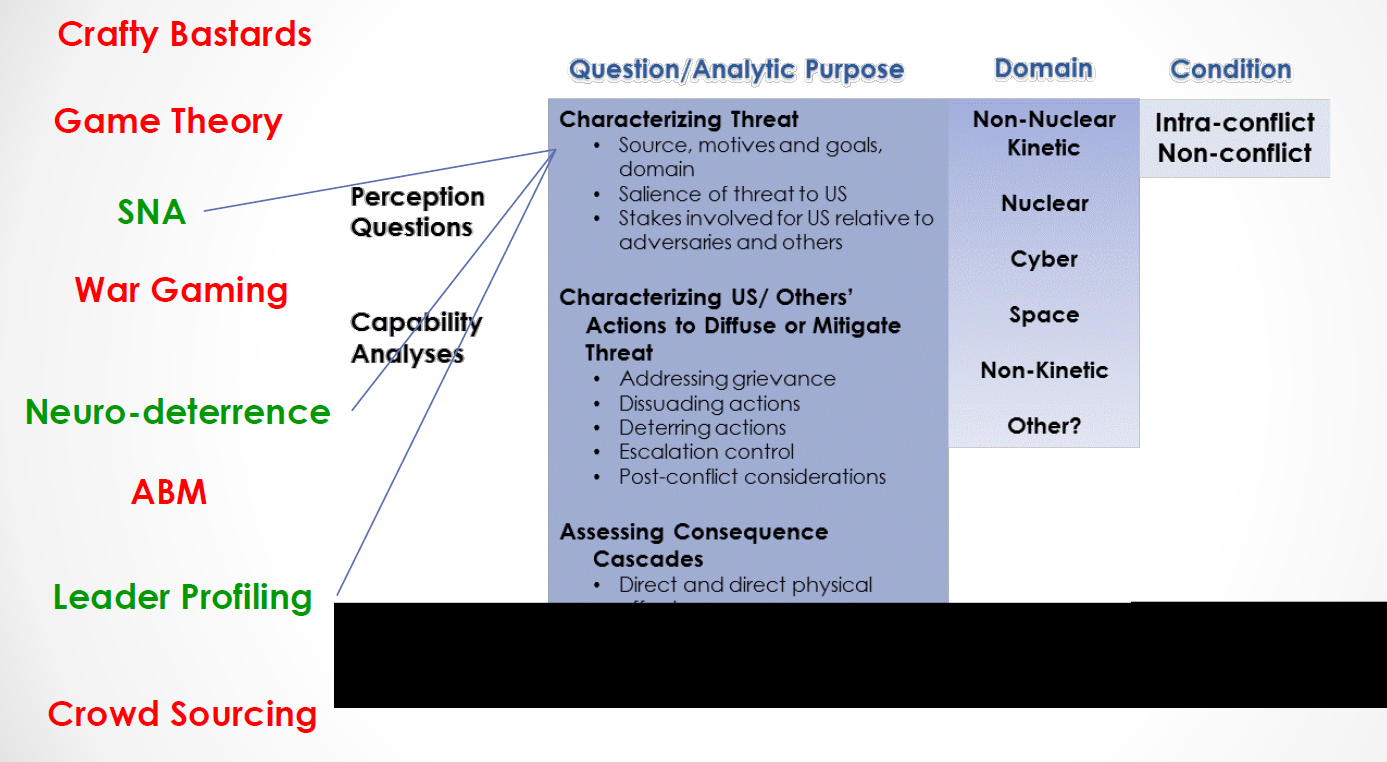
FIGURE 4-1 Characterizing tools, approaches, and methods. SOURCE: Dr. Allison Astorino-Courtois.
______________________
1“Crafty bastard” war gaming (“blue on red” to test alternative deterrence scenarios) recognizes the challenges of anticipating an intelligent adversary. An example would be a leader of a rogue state employing a "hard to pinpoint" subversive or terrorist organization without national or regional political responsibilities to deploy a "dirty" bomb or small nuclear device to create economic havoc (e.g., take out a major port of entry) or create fear to test national resolve and response.
Dr. Diane DiEuliis, deputy director, Office of Policy and Planning, Office of the Assistant Secretary for Preparedness and Response, U.S. Department of Health and Human Services, provided a presentation titled “Neurobiology and Deterrence: “Neurodeterrence?”An abstract of Dr. DiEuliis’ presentation is found in Box 4-4.
Dr. John Sawyer, program manager/senior researcher, National Consortium for the Study of Terrorism and Responses to Terrorism, University of Maryland, described the background and current work of this center of excellence for the study of terrorism and responses to terrorism. The center advances knowledge about the causes and consequences of terrorism for homeland security policy-makers. His group within the larger organization is an incubator of innovation that embraces new methodologies and undertakes projects that may have high risk and short deadlines and be very collaborative and operationally focused. He explained one example project—essentially, a case study on ways to influence violent extremists. The methodological approach has three steps: hypothesis identification, micro literature reviews, and generation of a knowledge matrix. The resulting matrix provides access to a wide range of theories and their supporting evidence and offers a tool that could guide concepts and doctrine. Admittedly, this is a very qualitative process.
BOX 4-3
The Crafty Bastard Innovation Cycle and Solution Creation Methodology
CAPT Gail Kulisch (USCG, Ret.), Kiernan Group Holdings
The “crafty bastard” methodology is based on research and case studies which reveal that administrative, bureaucratic structures inhibit design innovation, creating self-induced constraints in a battle against unrestricted adversaries. Disruptive threats, by definition, do not fit an organization’s own value chain and innovation cycle. Thinking faster than the speed of threat requires refinement of cognitive agility and the appetite for acceptance of divergent opinions and earned experience. Today’s, but more importantly tomorrow’s threats, demand an ability to learn more effectively and quickly and out think potential and real adversaries, whether from non-state or state sponsored organizations. Innovative and creative problem-solving design requires new hard skills that are learned through workshop encounters with exceedingly diverse and even rare combinations of talented people who work flexibly and in detail with an array of non-kinetic strategic vectors which offer innovative methods and means for unique problem sets. The crafty bastard process incorporates these critical tenets. It is an 8 week, well-defined development cycle that optimizes these attributes. Unique talent is engaged and includes experienced practitioners from the public and private sector who are practiced in applying learning and experience viewed through unique apertures that imagine new contexts. Initial analysis and assessment is conducted based on focused exploitation of deep open-source materials factoring in culture and context—the new C2 of this environment. Experienced facilitators agitate and guide critical thinking in an open, vendor-agnostic arena guided by carefully crafted questions and content. Actionable recommendations are developed and result in recommendations that disrupt the adversary’s adaptation cycle, exploit emerging technologies, and generate operational and tactical level solutions that support Commander’s Intent.
BOX 4-4
Neurobiology and Deterrence: “Neurodeterrence?”
Dr. Diane DiEuliis, U.S. Department of Health and Human Services
The past several decades have seen a convergence of neurobiological data with cognitive sciences, psychology and behavioral sciences—largely due to technological advances such as genomics, non-invasive imaging, and the wider availability of expansive data sets. We are thus beginning to bridge neurobiological understanding with the environmental and social backdrop upon which it occurs. An example framework for visualizing this could be the classic “OODA” loop (Observe, Orient, Decide, Act) juxtaposed onto the anatomical backdrop of limbic system function. Further affectors of this framework could be genetic predisposition, genetic heritage, and previous experience. Other fields have adapted this kind of framework for understanding the role of underlying neurobiology in human behavior and decision making, such as the emergent field of neuroeconomics. Some tenants of this field would indicate that human decision making for economics is influenced by relativistic comparisons and perceptions—and is not always rational. Similarly one could apply this framework and understanding to deterrence: understanding the underlying neurobiology that contributes to aggression, and decision making related to “intent to do harm” could provide important inputs to shaping new models and tools for the deterrence community.
Again, many questions and comments arose when the panel presentations were done. One participant asked, “If we know how people behave, does it matter what part of the brain lights up?” Dr. DiEuliis answered that this approach adds another layer of understanding. Another participant noted that, regarding the overall challenge for this workshop, an issue is how we apply neurodeterrence to what is needed for current situations, like headlines about drawing red lines related to Israel and Iran's uranium enrichment. A general issue is how can we use this. Dr. DiEuliis commented that relative to bio-weapons, in nations with lots of deaths due to diseases, bio-weapons are not that worrisome because the population is used to losing lots of people. A participant noted that some leaders are conditioned from childhood to not have empathy for others. Another participant asked whether there is any statistical way to identify some types of behavior. CAPT Kulich answered that red teams have rigor that could be helpful. In a related comment, a participant suggested that an area for research might be to observe behavior during games.
Dr. Tony Cox, president, Cox Associates, LLC, began the first panel of the second workshop session by noting that scenario-based analytic tools are meant to be used by teams, and those teams must validate both the inputs and the outputs of such tools to be sure they are trusted. A systems engineering approach in terms of an insight-generating model was presented, and analytic approaches in the context of making sense of patterns in big data were
discussed. At the end, Dr. Cox explained that these presentations show the types of scenario-based tools available; much infrastructure is in place, and this represents the state of the art.
Lt Gen Robert Elder (USAF, Ret.), research professor, George Mason University, provided a presentation titled “Integrated Influence and Effects Analyses for Use in Deterrence Planning.” An abstract of Gen Elder’s presentation is found in Box 4-5.
Ms. Anne Russell, director, social systems analysis, SAIC, compared “old-school” analyses of data with newer approaches that augment traditional techniques with new processes, such as social network visualization and analysis techniques as well as chronological or geo-spatial visualizations like Google Earth. Among other benefits, she noted that advanced tools (e.g., a narrative pattern analyzer) can save enormous amounts of time for analysts producing outputs. An illustrative application would be assessing factionalism to help understand the degree of stability or instability of a particular country. Another illustration was use of influence-net modeling for socio-behavioral applications, which can aid reasoning under uncertainty. Ms. Russell added that the effectiveness of any one tool would depend on what the user is trying to do; it is likely that one tool would not be enough for any specific case.
BOX 4-5
Integrated Influence and Effects Analyses for Use in Deterrence Planning
Lt Gen Robert Elder (USAF, Ret.), George Mason University
Timed Influence Nets (TINs), a variant of Bayesian Nets, are used to capture cause/effect relationships that relate timed sequences of actions to the probability of an effect or outcome occurring. TIN models are thus well suited to capture the diverse aspects of nuclear strategy issues. Specifically, TIN models can be used to gain insights into the effects of actions on one or more nuclear strategy objectives and can be adapted to reflect different actors, international environments, phase of military operations, and scenarios. The TIN models can be enhanced through the use of multi-modeling techniques to leverage the ability of multi-agent-based modeling to capture the dynamic interactions among groups. TIN models were used in two service wargames and an Office of the Secretary of Defense-led geopolitical stability study to assess the deterrence and nuclear stability effects of different courses of action across a range of operational phases. The results suggest that such models can be used to inform analyses addressing nuclear policy and strategy questions.
Dr. Jerrold Post introduced the panel titled “Leadership Profiling Approaches” for the second workshop session, noting that leadership profiling techniques had already received much attention prior to this session. Also, he noted that trying to understand an opposing side's leadership has deep traditional roots, even though some of the approaches suggested here rightly deserve the “non-traditional” label.2
___________________
2 Correctly ascertaining the intentions of an adversary is one of the key reasons why profiling was discussed so thoroughly during the workshop.
Dr. Margaret Hermann, director, Moynihan Institute of Global Affairs, Syracuse University, provided a brief set of remarks titled “Policymakers’ Interpretations Matter.” An abstract of Dr. Hermann’s presentation is found in Box 4-6.
Dr. David Winter, Department of Psychology, University of Michigan, provided a presentation to the workshop titled “Leaders’ Drives, Perceptions, and Justifications of Power: Analyzing the Signs in Crisis Situations.” An abstract of Dr. Winter’s presentation is provided in Box 4-7.
Dr. Stephen Walker, professor emeritus of political science, Arizona State University, provided a presentation to the workshop titled “Tailored Deterrence and Operational Code Analysis.” An abstract of Dr. Walker’s presentation is found in Box 4-8.
There were many comments, questions, and answers after the three presentations. For example, there was considerable discussion among participants about the pros and cons of hand-coding text versus machine coding; about getting to know the “real” persona versus the “public” persona; and the great amount of material that is available and could be analyzed. As another example, the panel speakers described what they would like to see regarding these techniques, such as (1) an easier coding process (biggest bottleneck); (2) more translations, especially of spontaneous utterances; (3) more tracing of interactions between leaders; and (4) lots of human analysis, which in the end was deemed necessary because one must look at circumstances, public statements, and what the leadership actually does (perhaps the best method). Additionally, the amount of time available to make a decision received attention from the participants—a lot of time means decentralization of power, whereas little time means “act now,” which leads to contraction of power.
BOX 4-6
Policymakers’ Interpretations Matter
Dr. Margaret Hermann, Syracuse University
The U.S. government employs subject matter experts to assist in the development of models to explore how particular governments are going to respond to deterrent threats and sanctions, which governments are likely to be crisis-prone, and to assess the stability of a government. What if we could, instead or in addition, determine how the leadership itself is likely to interpret a particular situation and to respond? Consider that in the past decade the 29 Asian countries located along the Pacific Rim have had 133 different governments involving changes in the leadership and their orientations to the world. The Profiler Plus software is designed to assess the leadership styles and likely behaviors of such leaders using media interviews with them, their speeches, and their written materials. The techniques have been validated by comparing results with the views of policy makers and diplomats who have interacted with the leaders.
BOX 4-7
Leaders’ Drives, Perceptions, and Justifications of Power:
Analyzing the Signs in Crisis Situations
Dr. David Winter, University of Michigan
In crisis situations, the intentions of the “other side” are critically important, but they are also difficult to judge. This presentation reviewed research on three concepts and measures relating to power, in order to suggest a way to estimate the aggressive intentions of potential adversaries. (1) High levels of power motive imagery in speeches, diplomatic documents, and broadcast commentaries, for example, are associated with crisis escalation. (2) In escalating crises (as compared with peacefully resolved crises), the implicit perceptions of threat each side exaggerate the threat presented by the other side, as measured by levels power imagery in summaries, précis, or “sound bites” of the other side’s statements. (3) Finally, in order to secure acceptance of aggression and war by significant elites, members of the military, legislators, and ordinary citizens, leaders must frame their actions as “just,” using the classical criteria suggested by Just War Theory. Taken together, these results suggest that monitoring these three measures—the other side’s expression of power in political documents, the exaggerated implicit perception of threat-power in the other side’s summaries of own side’s statements, and the other side’s justification of its power and actions—may help to estimate the intentions of potential adversaries.
BOX 4-8
Tailored Deterrence and Operational Code Analysis
Dr. Stephen Walker, Arizona State University
Tailored deterrence focuses on the problem of tailoring effective deterrence strategies to fit the beliefs, personalities, and cultural norms of diverse target populations regarding the exercise of power. The operational code construct refers to the conceptions of political strategy that inform an agent’s decisions, tactics, and strategies in escalating or de-escalating conflict situations. The conceptions are measured as configurations of attributions in the public statements exchanged between agents in a strategic dyad, which index each agent’s respective beliefs about the nature of the political universe (friendly or hostile), their degree of control over historical development (low or high), strategic direction (cooperation or conflict), tactical intensity (low or high), and risk-taking orientation (acceptant or averse) regarding the employment of various instruments of power (rewards, promises, threats, and punishments) in strategic interactions. These diagnostic, choice, and shift propensities are modeled formally as subjective games that each agent plays with different allies and adversaries in the political universe. The models indicate when and how members of these strategic dyads will make or respond to deterrent threats and whether such threats are necessary, desirable, or counter-productive.
THREAT ANTICIPATION AND INTELLIGENCE ANALYSIS
Dr. Michael Wheeler's opening remarks for the panel titled “Threat Anticipation and Intelligence Analysis” at the second workshop session gave an overview of the U.S. intelligence community (what it is today and how we got here) and a bit about national intelligence estimates (NIEs, the U.S. “master” estimates). He also framed how Congress got into (and stays in) the intelligence oversight business, not only through the intelligence committees but through studies it mandates, such as the one on China that was in the Fiscal Year 2013 National Defense Authorization Act. Dr. Rich Wagner, emeritus technical staff, Los Alamos National Laboratory, then provided a brief set of remarks, an abstract of which is given in Box 4-9.
BOX 4-9
How Policymakers Utilize Intelligence
Dr. Rich Wagner, Los Alamos National Laboratory
The organizing framework for thinking about U.S. strategic capabilities, including nuclear weapons, is, or should be, warning and response, over timescales ranging from minutes or hours (attack/tactical warning), to many years (strategic or geopolitical warning). The strategy should be to deliberately assess how much warning time we expect to have across this time range, and to have in place the ability to respond adequately within the warning time. This would not be just a reactive strategy; maintaining the capability to respond within warning shapes the current and future security environment. So how should the United States improve intelligence and warning capabilities to support such a strategy? (1) The powerful new capabilities for wide-area, persistent tactical intelligence, surveillance, and reconnaissance developed for Iraq, Afghanistan, and for terror interdiction can and should be adapted for nuclear attack warning and to understand other short-term threat developments short of attack. (2) The intermediate time frame of months to years is especially important for assurance of allies and for regional deterrence. Here, the model should be the NATO ShockWave program of the later phases of the Cold War. In ShockWave, full-scope U.S. and allied national intelligence, coupled with tactical ISR (which was improved expressly for these purposes), was coupled to NATO exercises designed to elicit Warsaw Pact behaviors in their subsequent exercises, in order both to help validate NATO indicator and warning capabilities and to understand changes in Pact operational concepts. (3) Nuclear weapons are mainly relevant for highest-possible-stakes geopolitical challenges of the sort that distinguished the 20th century. Since the end of the Cold War, we have been in a "strategic pause," and the question is when (if ever) and how (if at all) some highest-stakes geopolitical challenge might emerge in the future. Over the past several decades (and perhaps always), major geopolitical shifts have almost never been anticipated. "Path-gaming"—geopolitical games with notional time-scales of years or decades—have had some utility, and should be rejuvenated.
The current U.S. nuclear weapon posture is poorly suited to both near-term extended deterrence/assurance and some future major geopolitical challenge. Its main value is as a basis and starting point for its own future reconfiguration, if and when that is needed, and it should be managed expressly with that in mind.
Mr. David Hamon, principal, National and International Security Strategies, Analytic Services, Inc., provided a brief set of remarks titled “Threat Anticipation.” An abstract of Mr. Hamon’s remarks is found in Box 4-10.
Additional dialog among the participants surfaced other key issues, such as a need to focus on non-negotiated monitoring; a need for more effort in pulling signals out of clutter; the fact that nuclear applications need some sort of monitoring test bed; despite all the work on threat anticipation there was surprise by the “sprint-to-zero” emphasis; and—at the end of the day—humans make decisions, so there is a need to look at and understand human behavior.
BOX 4-10
Threat Anticipation
Mr. David Hamon, Analytic Services, Inc.
To Identify and develop social sciences-based research and analyses to support the anticipation and reduction of weapons of mass destruction (WMD) and related threats along a rolling long-term horizon, the Advanced Systems and Concepts Office (ASCO) of the Defense Threat Reduction Agency (DTRA), undertook a Threat Anticipation Project (TAP). Since its inception in 2002, ASCO has initiated TAP projects to explore productive areas of threat anticipation, including workshops to identify and acquire relevant expertise from the social science, computational science, and other communities; development of conceptual computer models to better understand and anticipate asymmetric threats; and staff activities involving networking with universities and other federal and private sector organizations to survey the current thinking on these issues and leverage outside expertise. TAP has produced a variety of concepts, computer and theoretical models, workshop proceedings, and reports of value to the future mission needs of DTRA. It is extremely important to have these products preserved, validated in some practical sense, and more widely used within the larger national security community. Threat anticipation by computational and social sciences is rapidly gaining recognition for potential utility; hence, TAP can become a major contributor to the Department of Defense, other federal agencies, universities, and other organizations in this area.











