3
Managing the Career/Employee Lifecycle for a Diverse Cybersecurity Workforce
CHAPTER OVERVIEW
This chapter and the next provide a discussion of human resource and management approaches as they relate to a diverse and effective Federal Aviation Administration (FAA) cybersecurity workforce. The discussion uses the employee lifecycle model (ELC), a widely adopted across industry as a human capital management approach (Burke, ND; Lowenstein, 2017; Santos 2019). This model allows for a holistic understanding of workforce needs and strategies, with each stage offering opportunities to address general workforce needs and also focus on specific considerations related to compensation, diversity, organizational culture and mindsets.
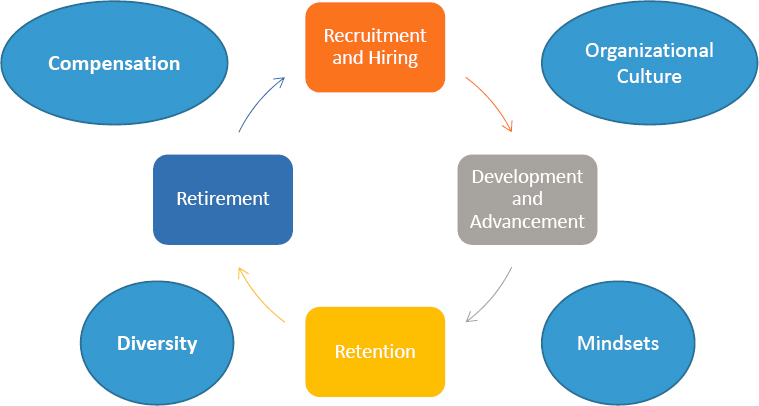
The ELC divides an employee’s career into six stages: (1) attraction, (2) recruitment and hiring (onboarding), (3) development, (4) advancement, (5) retention, and (6) retirement (separation). Managing an employee’s success, and thus the organization’s success happens over the entirety of this career cycle. See Box 3-1 for more information on the ELC model.
A diverse, cyber-aware workforce and a security mindset across the organization are essential for effectively maintaining a strong cybersecurity workforce. These characteristics can be best developed and maintained when integrated into the beginning of the human capital process. Figure 3-1 shows the committee’s adaptation of the ELC model for this report. The adaptation targets the key items that the committee felt were important to this project. It also incorporates important concepts that an organization should look at in all the phases of the ELC: organizational culture, mindsets, diversity, and compensation.
This chapter and the next use this adapted ELC model to structure the discussion about building a diverse cybersecurity workforce that can support the FAA’s needs in the 21st century. The chapter begins with an overview of the current cybersecurity workforce, which serves as a background for the subsequent discussion of specific practices and needs. Following this overview, the chapter elaborates on the first and second stages of the ELC model, “Recruitment and Hiring” and “Development and Advancement.” For each of these two stages, the committee begins with a consideration of aspects of these stages as they pertain to cyber organizations in general and then considers implications in light of the FAA’s particular needs and capacities. Chapter 4 discusses the third and fourth stages of the ELC model, “Retention” and “Retirement.”
CHARACTERISTICS OF THE CYBERSECURITY WORKFORCE IN THE 21ST CENTURY
Before investigating specific stages of the ELC as a way of understanding best practices for cyber organizations, it is helpful to have a cursory understanding of the current cybersecurity workforce as a whole. This section discusses three key features of this workforce: characteristics of the cybersecurity workforce, the cybersecurity workforce labor market, and diversity in the 21st century cybersecurity workforce.
Characteristics of the Cybersecurity Workforce
To address the rapidly evolving cybersecurity threat landscape, the cybersecurity workforce requires a variety of skills and the flexibility to quickly adapt to a changing environment. This is in part a function of the dynamic processes involved with adaptation to the attackers who continue to evolve and adapt (NASEM, 2017). The Cybersecurity Workforce Development Toolkit: How to Build a Strong Cybersecurity Workforce discusses the characteristics of high-performing cybersecurity teams (DHS, 2016). The toolkit (p. 5) states that a team should be
- Agile: Attacks can emerge at any time; teams must be ready to change course and solve problems quickly.
- Multifunctional: Teams need diverse knowledge and skills to perform many activities.
- Dynamic: To respond to new threats, teams need to always learn new skills and methodologies to secure systems.
- Flexible: Strong teams can shift priorities to meet the challenge of the day.
- Informal: Cyber teams favor flexible work hours and shifting duties to remain engaged and on top of their game.
In addition to considering broad characteristics of the workforce, organizations must also consider the specific operational needs of their cyber operations (NRC, 2013). The National Initiative Cybersecurity Education (NICE) Cybersecurity Workforce Framework (see Box 2-1) helps organizations to identify these needs by outlining job tasks for cyber workers and assigning to these tasks related knowledge and skills to help match learners to the workforce.
Cybersecurity Workforce Labor Market
As stated by Dreibelbis and colleagues (2018, p. 352), “A robust cybersecurity strategy begins with selecting the right people to identify, build, and protect an organization’s cyber defense systems. The reality is, however, that finding and selecting the right talent is more challenging than ever.” The national need for trained cybersecurity professionals across both industry and government is documented, and globally estimates predict 3.5 million cybersecurity positions will be unfilled by the end of 2021 (Morgan, 2017). According to Cyber Seek, as of April 2021, the United States has a total employed cybersecurity workforce consisting of 941,904 people, and there are currently 521,617 unfilled positions. Cyber Seek, is a project supported by NICE, a program of the National Institute of Standards and Technology (NIST) in the U.S. Department of Commerce.1 Given the global shortage of cybersecurity professionals, every federal agency will be continuing to compete for a relatively small number of cybersecurity professionals, and therefore a robust long-term strategy for ensuring a cybersecurity workforce will rely on growing the pool of available candidates and developing the required skills in the existing workforce.
The gaps are not only in the number of cybersecurity professionals but also in the skills of the existing professionals to meet job requirements. The estimated global gap of more than 3 million cybersecurity professionals and a recognized skills gap in the available workforce (Oltsik, 2017; Wright, 2015) persists even though there are a prolific number of academic and industry-based training programs for cybersecurity. For example, 59 percent of organizations noted the lack of qualification of job candidates in cybersecurity professions, and once hired, individuals in cybersecurity positions also report a lack of training, which is needed to stay abreast of the most recent vulnerabilities and countermeasures (Oltsik, 2017; Wright, 2015).2
Diversity in the 21st Century Cybersecurity Workforce
Diversity is a necessary and integral part of any human resource and management program. The cybersecurity field includes “the creation, operation, analysis, and testing of secure computer systems” (JFT, 2017). The breadth of the tasks, coupled with the constantly evolving threat environment, necessitates a workforce with a diverse set of skills, backgrounds, and experiences.
When solving complex problems, having a variety of backgrounds gives a richer foundation for finding solutions. As discussed in Chapter 1, it is important to recruit, select, and train candidates from diverse backgrounds not only because it is the “right thing to do” and a rational response to changing demographics, but also because increasing diversity in the workforce fosters diversity of thought, which is an advantage in cognitively demanding occupations such as those in cybersecurity (Page, 2019; Smith-Doerr et al., 2017). Research consistently demonstrates that teams with diverse perspectives outperform homogeneous teams (Smith-Doerr et al., 2017; Tadmor et al., 2012; Wang et al., 2019). Increasing the pool of diverse candidates through recruitment and workforce development will likely increase the number of qualified candidates and improve decision making.
Diverse perspectives come from diversity in the gender, racial, education, and cultural background of teams. Devon Bryan, the executive vice president and the Chief Information Security Officer (CISO) for the National IT Organization of the Federal Reserve System, and co-founder of the International Consortium of Minority Cyber Security Professionals (ICMCP), discussed the need for diversity in a cybersecurity workforce in a recent interview.3 He stated:
No one would disagree that cybersecurity is one of the most critical risks we face from a national economic and a national security perspective . . . And certainly, a woeful lack of participation by large segments of our population in women and people of color, especially when you juxtapose that against the number of unfilled jobs each year and, certainly again, juxtaposed against what we know to be a dramatic rise in cyber crime…
___________________
1 More information is available at: https://www.cyberseek.org/heatmap.html.
2 More information is available at: https://www.isaca.org/go/state-of-cybersecurity-2020.
3The Need for Diversity in a Cyber Security Workforce: Leading High-Performance Cyber Teams as a Recipe for Success. Interview of Devon Bryan by Andy Bonillo. Article written by Jeff Orr. August 1, 2019. Available at: https://www.cshub.com/interviews/interviews/the-need-for-diversity-in-a-cyber-security-workforce.
High-performing teams typically constitute folks from diverse perspectives, which include diversity of thought, diversity of opinions, and diversity of backgrounds. And certainly, being all in and making sure that all perspectives, all opinions are being brought to bear and with the cybersecurity challenges as real as they are, we certainly have to tackle and approach the problem in a significantly different way than we’ve done in the past to try and keep abreast of what the bad actors are doing.
To meet this imperative for workforce diversity, employers can leverage programs such as Women in Cybersecurity (WiCyS) and ICMCP, which are designed to increase the participation of women and underrepresented people of color in the cybersecurity workforce.
Diversifying the cybersecurity workforce extends beyond the recruitment stage and is considered below at every stage of the ELC. The mere addition of a small number of employees from underrepresented groups does not significantly improve the representation of diverse perspectives on teams (Jackson and Joshi, 2004; Mannix and Neal, 2005; Mendelberg et al., 2014). Organizations must also take great care to foster inclusive environments that are both representative of the larger population and supportive of the active participation of all team members.
Finding 3-1: The complexity of challenges that cybersecurity professionals address requires a workforce with a diversity of experiences and cognitive approaches, making diversity a functional imperative of cyber operations.
Finding 3-2: The need for diversity represents an opportunity to grow the talent pool.
RECRUITMENT AND HIRING
In the committee’s adapted ELC model, the first stage is recruitment and hiring, which addresses how organizations recruit candidates and subsequently hire them into the organization. Recruitment focuses on identifying and attracting the appropriate pool of candidates who match the knowledge, skills, abilities, and other characteristics required for competent job performance. Hiring an employee happens after selection. Selection can be considered the process of matching the characteristics and needs of the organization and those of the individual. After recruitment yields a pool of potential candidates, selection systems are utilized to further identify individuals who will fit within the organization and match the job needs. Once a candidate is selected, they go through a hiring process where an offer is made and terms are negotiated and finally the employee is onboarded. After reviewing key aspects of recruitment and selection, including cyber aptitude assessment, this chapter considers federal approaches to talent development and recruitment, as well as federal recruitment flexibilities.
Key Aspects of Recruitment
Recruitment is the first step in the selection process and is therefore essential in building a cybersecurity workforce. Organizational recruitment4 practices have evolved steadily over the past decades for a variety of reasons, including legal compliance through increased competitiveness and the availability of a global workforce. Darnold and Rynes (2013) discuss the activities and decisions that comprise organizational recruitment, including administrative procedures, selection standards, vacancy characteristics, sources of talent, and recruiters. Each of these aspects influences the recruitment process, which itself involves a series of sub-processes, including “self-selection processes, time-related processes, information-related processes, interactive processes, post-hire adjustment processes, and individual differences” (p. 59). Thus, when addressing its recruitment strategy, an organization needs to be concerned with many facets of the recruitment process.
Darnold and Rynes (2013) describe how the environment of recruitment has changed and is ever-evolving due to transformations in the global economy, the globalization of work, and job choice. Organizational characteris-
___________________
4 More information is available at: https://ecommons.cornell.edu/bitstream/handle/1813/75915/Collins13_Organizational_Recruitment_post_print.pdf?sequence=1.
tics such as image, geographic location, and size are important factors to many potential candidates and must be considered as part of the recruitment process. Organizations such as the FAA, which can offer both remote work and several satellite office locations, may have an advantage in attracting talent.
The committee found that research also points to the importance of an organization’s brand image. Brand image building, or essentially increasing the familiarity of an organization, is an essential element in turning a potential applicant into an actual applicant (Collins and Stevens, 2002). Collins and Stevens (2002) demonstrate the importance of organizational branding to candidates. They found that to potential candidates, organizational brand-building is related to the organizational image and ultimately organizational attraction, which in turn influences whether a candidate considers a particular organization.
Finding 3-3: Organizational reputation and positioning is a critical component of recruitment and talent attraction efforts.
An organization uses many tools in the recruitment process. Industry approaches to recruiting talent have an ever-larger online component, often incorporating internal job postings (via the company’s internal web site), external job postings (e.g., Monster.com and Indeed), and other social media such as Glassdoor, Facebook, LinkedIn, and Twitter. This ever-increasing push toward online recruitment received an intense increase during the pandemic of 2020/2021, when organizations were pushed to carry out core aspects of business via the internet. This online presence brings its own set of challenges, including managing and tracking candidate information. The Reynolds and Dickter (2017) model depict the process as beginning with casting a wide net via resume parsing and search (e.g., web scraping) to identify potential candidates. Algorithmic screening techniques, such as an email campaign with click-through tracking, can help to build a pool. Information culled from social media can be included as well in developing a suitablility composite score of each potential recruit. Those with higher composite scores are targeted for recruiter contact.
Key Aspects of Selection
Generally speaking, in the committee’s judgement, organizations have a set of characteristics defined as needs, values, and goals; similarly, applicants have a set of characteristics defined as capabilities, values, and goals. As stated above, selection can be considered the process of matching these parallel sets of characteristics and needs. The better the match between organization and individual, the better the fit between them. This concept of fit is an essential component of a successful organizational selection and retention process. This section looks at the process of determining fit (including assessment of cognitive and personality traits), applicant screening tools, and the role certifications can play in selection.
There are several types of fit to be considered. One type of fit is the match involving the person and the organization (P-O) (Yang et al., 2008). Here, the focus is on the shared values and goals of the two. A second type of fit is between the person and the job (P-J). The better the knowledge, skills, aptitudes, and other characteristics (e.g., non-cognitive factors such as personality) better match the demands of the job. The relationship between P-O fit and organizational attraction is similar in scale to the relationship between P-J fit and organizational attraction (Kristof-Brown et al., 2005). It appears increasingly important to examine P-O and P-J fit simultaneously (Resick et al., 2007); when it is, P-J fit appears more important than P-O fit. Fit assumes validity for improving satisfaction, teamwork, performance, and other outcomes—but a researcher needs the actual outcome data to test/validate that assumption. Finally, depending on the job, other types of fit may become equally important. For example, if the work is team-based then the fit of the applicant within the team (P-T) is a central tenet of selection.5
___________________
5 More information is available at: https://www.apa.org/ed/accreditation/about/policies/personnel-selection-procedures.pdf, and the AERA/APA/NCME Standards, which contain professional guidelines relevant to personnel testing, are available at: https://www.testingstandards.net/open-access-files.html.
Determining fit is an important part of the selection process, but it can be challenging. A clear and realistic description of job duties allows applicants to identify potential matches for their knowledge, skills, and abilities, which are often presented in a resume. Although a resume is still seen as essential in many applicant situations, the brief format of the resume often does not do justice to the experience or the quality of the applicant’s prior work (Reynolds and Dickter, 2017). Federal hiring imposes very particular requirements including a specific format for applications using the USAJobs, the official website for federal government employment, and that can limit a candidate’s ability to show their strengths (and weaknesses) thereby excluding qualified candidates from selection.
The selection process also often involves an assessment of candidates’ cognitive abilities and personality traits. These assessments need to be made by tests that are both reliable and valid. General and often specific cognitive abilities are determined by a test such as the Armed Services Vocational Aptitude Battery (ASVAB) in the military or the commercially available Wonderlic contemporary cognitive ability test. Personality constructs are often assessed via the Big 5 personality traits or similar measures in the civilian world, or the Tailored Adaptive Personality Assessment System (TAPAS) used by the military. Many other test types (e.g., assessment centers, physical standards, integrity, job knowledge, work sample, and simulations) can be utilized as well if there is a clear linkage between performance on the test and performance on the job. The link between performance on personality6 and psychological traits7 is not always straightforward (Pelt et al., 2017; Tisu et al., 2020). For example, one study found that a sample of skilled hackers had a high need for cognition, but that need for cognition did not predict peer-reported skill within that group (Le Blanc and Freeman, 2016).
Selection also involves gathering information on applicants’ backgrounds. Applicant screening tools, including questions targeted at specific jobs, are used to provide standardized methods for obtaining background and qualification information on potential candidates. Questions typically focus on work experience and education, including licensing when appropriate. Automated testing in general often plays a role via the administration of standardized tests with established reliability and validity. Behavioral assessment of candidates comes from online assessment centers and simulations incorporating controlled instant messaging, emails, and video email. These techniques can be either fully automated or supported by artificial intelligence (AI) and/or human participants.
The utilization of game-based assessment for selection and, specifically, assessment of professionals is being explored (e.g., Coovert et al., 2017, 2020; Gestwicki and Strumbaugh 2015). Gestwicki and Strumbaugh (2015) argue that currently more than 21 different games can be applied to selection. Such games assess multiple perspectives of an applicant, model scaffold learning progressions, and can present complex situations faced by cyber professionals, thus presenting an assessment in line with the work demands of those in cyber occupations.
Internal referrals, wherein a current employee vouches for an applicant to a given position, can be a valuable source of applicants, and most organizations have a process for handling these referrals. This source can be advantageous to the organization, since the candidate often has received information that helps them consider their fit within the organization and self-screens on that informal information. Darnold and Rynes (2013) observe that an applicant that is referred by an employee is more likely to be given a job offer. Their research indicates that these candidates are more prepared for screening assessments and perform better on scored selection procedures (Donald and Rynes, 2013). A potential limitation is that internal referrals often introduce new workers who resemble the organization’s current demographics and culture, which can make it difficult to diversify the workforce and address diversity goals.
Certifications also play a role in the selection of individuals in many of these occupations. While certifications would seem to be at least a practical way to measure competency in cyber job performance, they are not without their detractors, who observe that in some instances, certifications appear not to be predictive of cyber competency (CISA, 2019). As discussed later in this chapter, certifications for a broad field such as cybersecurity can encompass several skill sets.
___________________
6 More information is available at: https://blog.hubspot.com/marketing/personality-indicates-job-performance.
7 More information is available at: https://www.apa.org/topics/predict-job-performance.
Cyber Aptitude Assessment
Assessing for cyber aptitude as part of the selection process will be important as an organization works to expand its cybersecurity workforce. A 2019 study by Coovert and colleagues offers an evaluation of both cognitive and non-cognitive aptitudes and traits important in cyber occupations. The study identified those tests and assessments utilized to screen individuals on those cognitive aptitudes and traits. However, the study found that while cognitive abilities were well covered by existing tests, tools were as readily available for assessing aptitudes for active learning, deductive reasoning, systems thinking, and the traits analytical thinking, adaptability, and situational awareness. The researchers did identify one such tool: a face valid8 approach for assessment—a serious game, which is emerging as a recruitment tool that has been developed to provide a construct valid9 assessment of these other aptitudes and traits (Coovert et al., 2020).
Cognitive and personality factors, however, do not explain all the variance in the success of a selection system and an individual’s later competency on the job. Social influences from family, friends, relatives, and other informal sources are important in not only recruitment and selection, but also any subsequent decision to stay with the organization. As early as 2005, Chapman and colleagues pondered that there is an increasing emphasis on the relationship between social influences on organizational and job choice (Chapman et al., 2005).
Federal Cyber Talent Development
The 2016 Office of Management and Budget Memorandum 16-15 on Federal Cybersecurity Workforce Strategy directed the federal government to “act to expand the cybersecurity workforce to meet the increasing demand for talent” (OMB, 2016, p. 1). This section discusses several federal programs aimed at developing cybersecurity talent, as well as the guidance that helps federal agencies define their cybersecurity workforce. This section further describes the cultivation of talent before hiring as a way of increasing the candidate pool. As such, it differs from development as discussed below in the section on the “Development and Advancement” stage of the ELC model, which focuses on the development of skills and approaches once a person is hired.
Helping to fill these work cyber roles has been the aim of a significant number of federal talent development programs and regulations. In 2000, the CyberCorps® Scholarship for Service Program (SFS) was formed as part of the Federal Cyber Service Training and Education Initiative “to enhance the security of critical information infrastructure, increase the national capacity of educating IT specialists in Information Assurance (IA) disciplines, produce new entrants into the Government IA workforce, increase national Research & Development (R&D) capabilities in IA, and strengthen partnerships between institutions of higher learning and relevant employment sectors.”10 SFS provides grant support for students earning degrees in areas relevant to cybersecurity in exchange for a commitment to work for a federal, state, local, or tribal government agency after graduation. As of January 2020, 4,040 individuals have received SFS scholarships, 2,834 individuals have entered government service in 357 government organizations, and more than 1,000 are still in the academic phase. Of those, about 95 percent have been placed in a federal agency (Piotrowski, 2020). In fall 2019, a survey was sent to 1,164 SFS students that have already completed their public service obligation. Of the 403 individuals who responded to the survey, 65 percent stated that they are still working in the SFS covered position (i.e., beyond the required period). Of the remaining 35 percent of the responders, 23 percent are working in the private sector, 10 percent are working for the government as a contractor, and 2 percent are either self-employed or not working (Piotrowski, 2020). This suggests that opportunities that expose young professionals to government work can help to recruit individuals to a long-term commitment to public service cybersecurity as a career.
___________________
8 Face validity refers to selection or other procedures that appear relevant from the candidate’s perspective regardless of any empirical evidence of validity (Tippins et al., 2018, pp. 26–27).
9 Construct validity refers to the assessment of a concept or characteristic of individuals inferred from empirical evidence and theory (Tippins et al., 2018, p. 46).
10 More information about the history of the Scholarship for Service Program is available at: https://www.sfs.opm.gov/Overview-History.aspx.
The Cybersecurity Enhancement Act of 2014 stated that the director of the National Science Foundation, in coordination with the director of the Office of Personnel Management (OPM) and the Secretary of Homeland Security (DHS),
shall continue a Federal cyber Scholarship-For-Service program to recruit and train the next generation of information technology professionals, industrial control system security professionals, and security managers to meet the needs of the cybersecurity mission for Federal, State, local, and tribal governments; provide scholarships through qualified institutions of higher education, including community colleges; provide the scholarship recipients with summer internship opportunities; and, prioritize the employment placement of scholarship recipients in the Federal Government.11
For younger students, NIST also funded five pilot programs for the Regional Alliances and Multistakeholder Partnerships to Stimulate (RAMPS) Cybersecurity Education and Workforce Development in 2016. The pilot programs worked to address cybersecurity workforce needs in their region through academic partnerships between regional groups of K–12 schools, colleges, and local employers.12 Analyzing the methods and best practices used by each program led to the creation of a plan developing comparable regional alliances through such partnerships (Santos et al., 2020).
Two years later, the 2018 National Defense Authorization Act (115th Congress Public Law 91) “prioritized the employment placement of at least 80 percent of scholarship recipients in an executive agency” (p. 131). In addition, it directed the development and implementation of a “pilot program at not more than 10, but at least 5, community colleges to provide scholarships to eligible students who (1) are pursuing associate degrees or specialized program certifications in the field of cybersecurity; and, (2) (A) have bachelor’s degrees; or (B) are Veterans of the Armed Forces” (p. 475). The Act also provided “awards to improve cybersecurity education at the kindergarten through grade 12 level—(A) to increase interest in cybersecurity careers; (B) to help students practice correct and safe online behavior and understand the foundational principles of cybersecurity; (C) to improve teaching methods for delivering cybersecurity content for kindergarten through grade 12 computer science curricula; and (D) to promote teacher recruitment in the field of cybersecurity” (p. 475).
Recruitment for cyber roles typically targets individuals with an early interest in the field. It has become common for interest camps and competitions to feature cyber activities. These typically occur for individuals as early as junior high and high school, such as the Air Force’s Wright Scholars program13 or the Girls Go CyberStart.14 During these intense summer programs, students have the opportunity to develop skills and further their interest in cyber activities. Continuing through college, groups such as the National Collegiate Cyber Defense Competition15 bring together highly skilled individuals about to enter the cyber workforce.
Federal Recruitment
Workforce development strategy for federal employers must also align with the requirements for government hiring. At the broadest level, these requirements are set forth by the OPM for federal civil service agencies such as the FAA. Under the OPM process, agencies must progress through a defined series of steps that include reviewing workforce needs, submitting a Request for Personnel Action (RPA) to OPM for approval, drafting a position description, comparing the knowledge and skills of the drafted position against an organization’s strategic needs, posting a job on the official USAJobs website, reviewing candidates, interviewing candidates, and extending a formal offer.
___________________
11 The full description is available at: https://www.congress.gov/bill/113th-congress/senate-bill/1353/text.
12 Program descriptions are available at: https://www.nist.gov/itl/applied-cybersecurity/nice/regional-alliances-and-multistakeholderpartnershipsstimulate-ramps.
13 More information is available at: https://afrlscholars.usra.edu/locations/wright-patterson/.
14 More information is available at: https://girlsgocyberstart.org/.
15 More information is available at: http://www.nationalccdc.org/.
Additionally, OPM rules also mandate certain factors, such as Veteran’s preference, when assessing applications for a specific posting. These requirements often lead to a lengthy period between a position being posted and its being filled, though hiring-side tools such as the DHS PushButton PD™ Tool,16 which allow agencies to easily draft a position description describing an opening, have introduced some efficiencies into the process.
Throughout the process, federal agencies are further constrained in the compensation packages they can offer employees. Salaries are typically set through a pay system, the most common of which is the General Schedule (GS). The GS system sets compensation for positions within predetermined bands, using a base salary and locality adjustments.
Federal Recruitment Flexibilities
Agencies can, with proper authorization, supplement the conventional federal hiring system through certain flexibilities. One example of hiring flexibilities is the “on-the-spot hiring” authority, which authorizes an agency to extend a job offer to candidates for specific positions without a required public posting period. As discussed in Chapter 2, the FAA currently uses direct-hire positions, or on-the-spot hiring, “when it is determined there is a severe shortage of candidates, a critical hiring need for a position (or group of positions).”17 This hiring option can be a particularly effective tool when recruiting highly sought-after candidates that have in-demand skills and help to diversify the agency’s workforce. Federal agencies also have the flexibility to request special pay rates for high-demand positions and offer other incentives such as loan repayment assistance for federally insured student loans.
Finding 3-4: To aid in the recruitment process federal agencies are able “To recruit and retain personnel with the critical skills needed to accomplish their missions, federal agencies can offer incentives, such as recruitment, relocation, and retention incentive payments; student loan repayments; annual leave enhancements; and scholarships” (Marinos, 2017).
Finding 3-5: Flexibility of on-the-spot hiring is an important tool for hiring a diverse workforce and aids in the recruitment of diverse candidate.
Due to the often-lengthy process that is typical for onboarding individuals into government roles—one that often ranges from 2 months to a year—it is important to expedite the process wherever possible, especially since private sector employers are often able to offer more attractive positions to high-demand applicants as compared to their government counterparts (Hernandez, 2020).
While the clearance process takes up much of this time and is often an unavoidable aspect of the delay, as of 2014, programs such as the Federal Information Security Modernization Act (FISMA) allow conditional offers of noncompetitive placement to be given at job fairs to interested parties who are graduates of the Scholarship for Service program (Hernandez, 2020). Evidence for the success of this hiring authority can be found in its use by DHS and the Department of Defense, though it should be noted that this initiative takes an enormous amount of coordination, cooperation, and understanding between the Chief Human Capital Officer and the CISO (Hernandez, 2020).
Concerns with this approach often center on the potential for arbitrary or capricious practices or decisions that ignore equal opportunity employment considerations. Therefore, extra sensitivity to issues of diversity, equity, and inclusion should be given when considering the exercise of these hiring authorities (Hernandez, 2020). Overall, there is an apparent need to signal to applicants that this process can be accelerated as a means of increasing the likelihood of their continued interest in positions within government roles in general and the FAA in particular.
Finding 3-6: Certain procedural flexibilities (e.g., on-the-spot hiring) and compensation flexibilities can be useful tools for filling positions in high-demand job markets.
___________________
16 More information is available at: https://niccs.us-cert.gov/workforce-development/dhs-pushbuttonpdtm-tool.
17 Document on hiring flexibilities provided to committee by the FAA. April 20, 2020.
FAA RECRUITMENT AND HIRING
The FAA cybersecurity workforce requirements span multiple disciplines and skill levels. There are many best practices in industry that the FAA could benefit from; these include strategies for recruiting multidisciplinary cybersecurity teams at the junior, mid, and senior levels through lateral hiring practices, academia partnerships, and cybersecurity-focused partnerships. The role of lateral hiring practices (Amankwah-Amoah, 2015) in industry means that companies will compete to hire the best talent as an effective strategy to both address their own needs and to compete against other companies. Industry research indicates that career advancement, inclusion, culture, innovation, and mission alignment are key factors in attrition and job movement.18 Organizations that highlight the diversity of mission, training, and career opportunities coupled with mentorships have been successful at attracting and retaining employees for hard-to-fill cybersecurity positions (Lewis, 2020).
Academia is an important recruiting source. Many computer science majors, including more than one-half of those with a Ph.D., are hired by industry (NASEM, 2019). The concentration of these majors in industry speaks to the high quality of industry’s recruiting techniques. Industry insights in attracting highly skilled cybersecurity staff include education reimbursement, defined career paths including those specified in the NICE Framework, (Lewis, 2020; Perez, 2020, Worden and Romero, 2020), mobility, and continuous internal and external learning programs. These organizations also have strong affinity groups and employee resource groups that recognize diversity and inclusion within the organizations.
It should be recognized that computer science is not the only major relevant to cybersecurity. Previously, the singular focus on computer science as the only relevant major has led to siloed organizations (Jacob et al., 2018). Today, however, it is generally accepted that the discipline of cybersecurity is broader than computer science. In fact, multiple majors contribute to cybersecurity enterprises and are key to the mission of cybersecurity. For example, in preparing military cadets, other technical academic majors include information technology, information systems and security, and mathematics and data science (Mack et al., 2019; Spidalieri and McArdle, 2016).
For a specialized field such as cybersecurity, a variety of educational approaches to develop individuals for jobs in the cyber workforce are useful. This can begin rather early in the formal educational process and continue through secondary school, postsecondary programs, college, and beyond. Currently, there are several formal programs that can demonstrate an indication of success for future cyber occupations.
The National Academies’ 2018 report Assessing and Responding to the Computer Science Undergraduate Enrollments points to some ways to build/foster effective partnerships between academia and industry. For example, partnerships between K–12 curriculum specialists are also important to support early and persistent cybersecurity education to expand pathways to cybersecurity professions. Additionally, the report discussed recommendations on the practice of hiring non-degree holders and preparing them for cybersecurity roles. Finally, the report recognized that scalability in individual performance is critical (NASEM, 2018).
For corporations, engagement with institutions of higher education (e.g., universities, 4-year colleges, and community colleges) provides opportunities for branding, research partnerships, and, ultimately, influencing student preferences such that they seek internships and careers in these corporations. Students can develop affinities for corporations who have integrated their efforts across the university through effective partnership strategies. Sponsoring events on campus, such as hack-a-thons, cybersecurity days, digital badges, and seminars have been effective recruiting tools for corporations. In the committee’s judgment, participating in career fairs, alone, does not garner the trust and preferences of students.
Programs such as SFS, discussed above and below, have proven to be an especially effective mechanism to recruit cybersecurity talent into the federal government. Students who participate in the program actively choose to pursue careers in public service and government agencies aggressively compete for the limited number of graduates each year. Agencies with long history of participation in the SFS program, such as the National Security Agency (NSA), have developed strong relationships with many of the universities participating in the SFS program (Cook, 2020). These relationships effectively engage students in the agency mission, culture, and work requirements, and encourage a steady stream of interns and permanent employees.
___________________
18 More information is available at: https://cultureplusconsulting.com/2018/10/16/meaning-metrics-for-diversity-and-inclusion/.
Loyalty to organizations may be fostered through full fellowships, scholarships, and student loan forgiveness. The SFS program provides grants to universities to fund scholarships for students pursuing cybersecurity-related degree programs. These scholarships, along with specialized programming offered by host institutions and opportunities for government internships, strengthen student understanding of the importance and prestige of protecting national security through public service cybersecurity careers. The FAA should consider both expanding its participation in the SFS program and developing stand-alone programs that provide student scholarships and opportunities to engage with students via internships and other experiential learning opportunities. Creating a specialized SFS program for the FAA may not be necessary, but reviewing best practices of other federal agencies in securing cybersecurity talent will be important.
Immersive experiences in cybersecurity do not have to take on the traditional design of summer internships. For example, another useful tool includes cooperative agreements (co-ops), where students work at the agency for one or two semesters, while maintaining enrollment at their respective institutions. The FAA could also take advantage of semester or quarter breaks, using them as mini internships for students. Students are often seeking paid opportunities during these times. For example, semester-structured institutions have “intersessions” between fall semester and spring semester. This time period could be as long as 40 days, providing an opportunity for a student to secure an internship and focus on a cybersecurity project. “May-mesters,” the break between end of the spring semester and beginning of summer sessions, could also be considered. The inter-sessions are important because they can allow students to continue their academic matriculation and take advantage of internship opportunities. In this way, students can graduate within 4 years, minimize student debt, and pursue their career in cybersecurity in the FAA.
Finding 3-7: Many individuals presently in the FAA report an early interest in aviation.
Finding 3-8: Other agencies are able to interview and extend initial offers on-the-spot during relevant cybersecurity conferences and university career fairs; the FAA should follow this example.
Job Listings
To get a better perspective on the advertising methods and techniques used by agencies and departments of the federal government, the committee reviewed more than 100 job postings for cybersecurity-related positions from the USAJobs.gov and Indeed.com websites.
The review revealed there to be almost no job vacancies for entry- or lower-level applicants as determined by the GS classification system. Notably, among the few found, none of the job postings was aimed at any applicant lower than GS-7, with little to no attention to language that appeared to indicate enthusiasm or effort in the promotion of the agency or posting. Aside from basic qualifications and mission descriptions, there was little effort to solicit applicants through use of high-impact language. These basic phrases include, but are not limited to, calls for “Motivated and highly qualified candidates,” mention of a “Strong team environment,” or calls to “Come join this dynamic team using your expertise to make a real impact.” One listing that stood out among the entry-level to experienced positions was a GS-7 Step 1 cyber mitigation engineer at the NSA, which made appeals to the applicant’s potential interest in “securing our nation’s critical infrastructure.”
Most spoke of their history and founding accomplishments regardless of GS level and used similar key phrases to attempt to draw the applicant in. However, the higher or more senior the job and/or title, the more likely the listing was to use impactful language. Essentially, the higher the GS level, the more the agency or department lobbied for the applicant. Alternatively, the lower GS-level postings put forth little to no effort to accomplish more than list the vacancies as described above. All of the job postings have similar education requirements (across the GS level), incentives were nonexistent, and offered benefits followed government boilerplate. Many higher-level postings, especially those affiliated with a military branch of the federal government or office, used language that attempted to “inspire” and/or appeal to a potential applicant’s “patriotism” and sense of duty to their country. Another higher-level posting touted the applicant’s role in developing “technologies and tools” and being “a part of cutting-edge innovations.”
Suggestions to address gaps or deficiencies in postings:
- Put forth as much effort (if not more) into “improving recruiting tactics” for lower-entry-level applicants as in higher/senior level—including language that conveys a vested interest in applicants’ success and future achievements.
- Promote agency/department incentives, that will pay for continued education; training and certifications; more opportunities for merit/step increases.
- Create an achievable/realistic career agenda and path so applicant can see that the agency is thinking about their future goals, aspirations, and growth.
- Promote growth within “career path” plan so that applicant can visualize (from the start) the payoff for their hard work, allegiance, and “stick to it” mindset.
- A list of nonconfidential but exciting projects that the FAA cybersecurity group is engaged with will help potential applicants have a better understanding of the impact of the position.
In job listings, the FAA would benefit from portraying its public persona as the preeminent organization it is. As discussed above, organizational reputation and branding play a central role in attracting high-quality talent. Recent research continues to demonstrate that organizational reputation is a primary determinant of successful recruitment (Baer et al., 2018; Harris et al., 2020; Lawong et al., 2019).
Taking a haphazard approach to hiring in critical skill occupations is rarely successful. Successful attraction is most likely to occur through targeted recruitment practices, even when using social media to attract passive job seekers (Acikgoz, 2019). Furthermore, Ng and Sears (2017) demonstrate that the targeted approach is highly successful even when attempting to attract high-level individuals based on gender.
Scholarship Opportunities and FAA Recruitment
Several scholarship opportunities offer possibilities for the FAA to increase visibility among young and diverse cyber talent. As discussed in detail above, the National Science Foundation’s SFS program, established in 2000, provides up to 3 years of tuition support for students pursuing a postsecondary degree in cybersecurity. In exchange for tuition assistance, a living stipend, and limited professional development support, graduates of the SFS program pledge to serve in the federal government for a period of time equal to the length of their support. The program has proven successful in bringing cybersecurity talent into the federal government. According to a 2019 survey of SFS graduates, 65 percent of respondents indicated continued employment with the federal government beyond the mandatory period of their scholarship (Piotrowski, 2020).
According to figures provided by the sponsor, the FAA has not received any placements of SFS graduates. While the agency is considering more engagement with SFS, participants in the SFS program are responsible for finding their own employment and can chose where they work within the federal government. This suggests that the FAA will need to focus its efforts on increasing awareness of its mission among SFS participants to enable it to compete for SFS graduates.
Another program is the Cybersecurity Talent Initiative of the Partnership for Public Service, which mandates 2 years of service in the federal government.19 This program works with diversity-oriented groups such as WiCyS to create a pool of cyber talent that better reflects national demographics (Kempinski and Cunningham, 2020). By partnering with the Cybersecurity Talent Initiative, current federal partners such as the Federal Bureau of Investigation and the Department of Homeland Security can simultaneously meet their cybersecurity workforce needs and improve diversity in the workplace (Kempinski and Cunningham, 2020). The FAA should consider deeper partnerships with these programs to achieve the same ends.
Finding 3-9: The FAA has not partnered with the SFS program to effectively recruit cyber talent to the organization.
___________________
19 More information is available at https://cybertalentinitiative.org/.
Finding 3-10: The FAA has not partnered with universities to shape cybersecurity programs and curricula.
Finding 3-11: The FAA might consider developing its own programs outside of SFS to provide fellowships and scholarship to students, as well as find ways to integrate them early via internships and other experiential learning opportunities.
Recruiting for Diversity in the FAA Cybersecurity Workforce
In cybersecurity, vulnerabilities arise from complexities associated with a variety of threat actors, strategies, technologies, and geopolitical conflicts. To prevent or confront cyber attacks, multiple perspectives are needed. A monoculture in a cybersecurity organization is not helpful when exploring cybersecurity risks. Blind spots created by “group think” can cause vulnerabilities to be missed or ignored. As discussed in the above section on diversity in the 21st century workplace and also in Chapter 1, diversity in cultural backgrounds yields diversity of thought.20 Diversity in thought as well as in cultural backgrounds can be an insurance policy against missing vulnerabilities.
Group vulnerability assessments, such as the Flaw Hypothesis methodology and the Delphi method described below, are often employed, especially in larger organizations, to aid in developing a risk management plan for the organization. Both methods stress diversity in experience, in thinking, and in cultural/ethnic background.
As described in depth by Bishop (2004), the Flaw Hypothesis methodology is the system analysis and penetration technique in which the specification and documentation for an information system are analyzed to produce a list of hypothetical flaws (Bishop, 2004). This list is prioritized based on the estimated probability a flaw exists, on the ease of exploiting it, and on the extent of control or compromise it would provide. The prioritized list is used to perform penetration testing of a system, the ultimate investment strategy in cybersecurity mitigations (i.e., policy, administrative processes, technologies, awareness training, continues information assurance process).
The Delphi method is a structured communication technique or method, originally developed as a systematic, interactive, and iterative technique that relies on a panel of experts (Adler and Ziglio, 1996). Delphi is based on the principle that decisions from a structured group of individuals are more accurate than those from unstructured group.
Active and ongoing recruiting is a means to diversifying the workforce. It is not effective to simply participate in career fairs or post a position and hope that diverse candidates see the posting and apply. Employers should actively engage in awareness and recruitment activities year-round to ensure that their organization is visible and trusted to potential candidates. During the committee presentations, we heard from representatives of the Department of Education and United States Coast Guard on how they recruit and the tools they employ to hire a diverse cybersecurity workforce. They acknowledged that they have similar challenges to the FAA in hiring cybersecurity professionals due to salary, benefits, and U.S. citizenship requirements (Embry, 2020; Hernandez, 2020).
Increasing the talent pool available to a cybersecurity workforce may require an emphasis on the recruitment of minorities and women, groups that have traditionally been overlooked (Burrell, 2018). Recognizing barriers reported directly by women and underrepresented minorities is critical to finding authentic, intentional ways to recruit and retain a diverse workforce.
Furthermore, obtaining high-quality, diverse candidates to apply requires active engagement in recruitment where those candidates are being educated and trained. For example, several organizations develop and maintain relationships at historically Black colleges and universities (HBCUs). The FAA could prioritize developing meaningful partnerships with minority-serving institutions, professional societies relevant to cybersecurity, and other groups. In the committee’s judgment, relationships and innovative partnerships yield results that are beneficial to an organization with a growing population of retirement-eligible personnel.
Finally, the military Veteran workforce is highly talented and experienced, yet many Veterans find it difficult to obtain their first career job after the military (Turner, 2021). The FAA would benefit by expanding its options such that Veterans of all ranks, officer and enlisted, are actively recruited. In the committee’s judgment, there are still challenges with officer corps diversity across all military branches, but enlisted personnel are also highly qualified and should be explored as a source of talent in cybersecurity.
___________________
20 More information is available at: https://www.diversitywoman.com/diversity-of-thought/.
Finding 3-12: The committee acknowledges that the FAA has similar challenges as other federal agencies to recruit a diverse cybersecurity workforce.
Finding 3-13: The FAA does not take advantage of programs that other agencies use to recruit cybersecurity professionals.
The FAA has had success recruiting people from military backgrounds, both in terms of mission-driven alignment and drawing from a pool that more accurately reflects the demographics of the overall population.21 In the committee’s judgement, the FAA might benefit from enhanced recruiting of people from mission-driven backgrounds such as military Veterans (individuals often seeking continued mission-driven employment). However, it is important that the agency does not rely too much on the military as a way of increasing diversity in the cybersecurity workforce so as to avoid diminishing diversity of thought by hiring too many workers from a single source.
DEVELOPMENT AND ADVANCEMENT
The ELC model includes talent development and advancement. This is the next step after an organization has successfully identified, recruited, and hired the employee. Employee development can include training and performance management. Training has been adopted as an approach by which employers can adapt their current workforce to evolving challenges and skill requirements of the job. Traditional approaches to training as well as emergent trends, such as serious games and simulations of varying levels of fidelity, can provide levels of customization for employee needs. Key activities in this stage of the cycle include reskilling and training, educational conferences, certification, performance management, and organizational culture. Finally, the committee explores performance management and strategies to cultivate cyber competencies in the workforce.
Reskilling and Training
Hiring employees with the right skill set and then growing them as the job requirements change is optimal. However, when organizations are unable to recruit the talent needed to meet new needs, reskilling can empower the existing workforce to adapt to new challenges. In a field such as cybersecurity, marked by rapid changes in skill sets and high demand for talent, reskilling is a valuable tool for employers. Reskilling is overall very promising, and opportunities exist to help transition reskilled employees to positions relevant to their training; over time, reskilling should grow beyond technical skills to include managerial and operational skills (Hernandez, 2020). Many organizations have developed retaining and reskilling programs to help manage the scarcity of new talent in a competitive labor market by training existing staff to take on cybersecurity roles. Large companies such as Amazon, AT&T, and JP Morgan and Chase have developed reskilling programs, sometimes in partnership with universities (Weber, 2019). In considering reskilling programs, it should be noted that in the committee’s judgement their long-term utility has not yet been established.
Those entering the cybersecurity field require ongoing training and education to learn about new technologies and possible threats and to stay adept. A 2014 survey of cyber workers found that 84 percent of participants disclosed informal education supplementation to be a requirement for job success (Champion et al., 2014). Many participants also reported that individuals who had on-the-job training had higher performance.
Finding 3-14: Reskilling is overall very promising, and opportunities exist to help transition reskilled employees to positions relevant to their training.
Online training systems are changing the delivery landscape for training, with training occurring at nearly any time and location. This allows employees to participate in training regardless of location (at work or non--
___________________
21 Focus group discussion with FAA employees and committee members, August 20, 2020. All discussions were conducted in confidentiality, and the names of the participants are withheld by mutual agreement.
work location). The FAA presently has a learning management system it utilizes to deliver training,22 and this type of training, especially courses targeted at cyber, should be encouraged across all levels of the organization. Online training is often organized into learning roadmaps, and if not already targeted for cybersecurity, it would be most helpful to do so.
Training platforms provide an excellent option for certain types of training, especially in situations where it would be beneficial to employ a digital sandbox for individuals to work with specific devices and realistic models of intrusions and attacks. The advantages of this approach are described by Urias and colleagues (2017). Acosta and colleagues (2017) provide further examples, including an emulation sandbox suitable for small to medium scenarios and a logger for capturing and recording evaluator data. Domínguez and colleagues (2017) also demonstrate the efficacy of using real equipment for the training of control systems in security and critical infrastructure protection. Virtual labs can be created via training environments such as RunLabs (Justice and Vyas, 2017), which allow for the rapid configuration of virtual machines with specific network configurations tailored to adaptable training scenarios and scripts.
Serious games (games used for a purpose other than mere entertainment) are being developed for cybersecurity awareness training (Gestwicki and Strumbaugh, 2015; Huynh et al., 2017). The advantages of serious games are that they can be played in the normal work environment and can be constructed to force the player to engage in the material at a deeper level than that required for rote memorization. Storylines can be developed and constructed to help players understand the cybersecurity problems and the advantages of alternative resolutions. It is essential, however, that the serious game employ models of game-based learning to be successful (Coovert et al., 2017; Katsantonis et al., 2017). A survey of serious games in cybersecurity training can be found in Tioh and colleagues (2017).
Gamification (the application of typical elements of gameplay) has established a foothold in the training of first responders focusing on cybercrime (Coull et al., 2017). According to the authors, the gamification approach for training large numbers of police officers holds promise. Gamification has also been used with traditional hands-on skills, such as using capture the flag to foster cybersecurity skills (Li and Kulkarni, 2016).
Due to the fast pace of changes in technology and the fact that security is largely dependent on the environment and context of the work domain, no single training program can cover all the specific technologies, tools, and threats that a cybersecurity professional needs to master to be effective. Training programs that focus on teaching specific technical skills and tools (Caulkins et al., 2016) can leave the learner unprepared for handling new problems. Extensive research in cybersecurity education (McGettrick et al., 2014; Schneider, 2013) has come to the same conclusion—that how a practitioner thinks about problems, rather than the specific technical skills and knowledge, is the key component in the education of effective cybersecurity professionals. In the committee’s judgement, effective training should focus on fundamentals and help develop the necessary problem solving and critical thinking skills needed to adapt to the ever-changing world of cybersecurity. The largest gap in the cybersecurity workforce is professionals who have the technical skills in information security and other skills such as communication, management, and can-do integrated thinking about the systems that they are securing (Crumpler and Lewis, 2019; Vogel, 2016). Technical tools and training have been widely and even freely available for decades; however, some of these other, fundamental aspects of education relating to computer security are still lacking, even within the NICE program (Caulkins et al., 2016).
Educational Conferences
Educational conferences, which often contain practical exercises or competitions, also are good opportunities to contact individuals interested in cyber occupations (e.g., DEF CON, Black Hat). These conferences serve multiple purposes, including the continuing education of professionals, the testing of abilities against new cyber challenges, and social networking and teaming throughout. One example of an organization focused on gender is
___________________
22 Focus group discussion with FAA managers and committee members, August 21, 2020. All discussions were conducted in confidentiality, and the names of the participants are withheld by mutual agreement.
WiCyS,23 which assembles women in cybersecurity from academia, research, and industry to share knowledge, and experience, and take part in networking and mentoring. The WiCyS Conference is held annually, and offers companies a chance to connect with students and candidates. The conference is both a career and graduate school fair with a favorable student to nonstudent ratio and content focused on education, research, outreach, and industry opportunities. It is currently the largest security conference in the nation (Siraj, 2020). WiCyS also includes a Veteran Assistance Program to help female Veterans transition into careers in cybersecurity.
With the demand increasing for cybersecurity professionals, effective cybersecurity education is essential to have a qualified workforce. There are numerous formal and informal education efforts under way including professional certifications, college-level internships and scholarships, high school efforts, and earlier school efforts, all discussed below. Early talent investment starting in elementary school can help develop an interest in the cybersecurity field.
Certification
According to NIST, cybersecurity professionals protect the data, systems, and operations of an organization by providing a variety of security-related tasks (Newhouse et al., 2017). In the realm of federal employment, possession of a relevant educational credential or professional certification has played a large role in defining the profession of cybersecurity (see Box 3-2 for the definition used in this report). Figure 3-2 shows a cybersecurity career pathway for an employee.
The broad range of cybersecurity-relevant certifications reflects the variety of tasks and responsibilities that comprise cybersecurity work. It can be difficult to use certifications as a marker of experience because the field is so broad that certifications can be applicable to all parts of the field. That said, while some common certifications reflect competency in a general set of skills, such as the popular CISSP (Certified Information Systems Security Professional) credential, others are tailored to more specific areas and job tasks. For instance, a PenTest+ certification can be useful in identifying individuals with the necessary skills to perform vulnerability analysis and discovery.
There are numerous cybersecurity degrees and certificates offered by educational institutions as well as skill-based certifications. Credentials are granted by professional organizations, educational institutions, and training agencies, all with a range of levels of requirements. The 2020 Global Knowledge IT Skills and Salary Report publishes data from more than 9,500 survey participants; it found that almost 9 out of 10 IT professionals have at least one certification, with almost 4 out of 10 reporting that they are already pursuing another one.24
Cybersecurity certificates are typically associated with training or education courses that have a testing component (NRC, 2013). These certificates are often “good for life;” while their relevance decreases over time, they are an indicator of knowledge at a certain point of time (NRC, 2013, p. 17). Other types of certificates need to be renewed; in these cases, “certification is a formal procedure by an authorized or accredited body” based on factors that predict job success (NRC, 2013, p. 18). These credentials require testing and recertification and can be revoked.
The National Initiative for Cybersecurity Careers and Studies (NICCS) website has a list of “well-known industry certifications.” Some are meant to be for those entering the cybersecurity field, while others are for those looking to increase their knowledge of potential career opportunities.25 These include professional certifications, which offer an opportunity to develop applied knowledge and skills aligned with the needs of various sectors such as industry and government. Some of these certifications include the Global Information Assurance Certification (GIAC) Security Essentials (GSEC). The globally recognized CISSP certification is a cybersecurity credential and confirmation of qualifications that is held by 56 percent of cybersecurity professionals (Nessi, 2020). Studies have found that CISSP is a credential many employers are seeking (Wang and D’Cruze, 2019).
Other certifications target specific tasks to be conducted by cybersecurity specialists to prepare for certain types of threats such as the Certified Ethical Hacker (CEH) and the Certified Expert Penetration Tester (CEPT). Other certifications target areas within which the professional should operate. The HealthCare Information Security
___________________
23 Additional information on WiCyS is available at: https://www.wicys.org/.
24 More information is available at: https://www.globalknowledge.com/us-en/content/salary-report/it-skills-and-salary-report/.
25 More information is available at: https://niccs.us-cert.gov/about-niccs/featured-stories/cybersecurity-certifications.
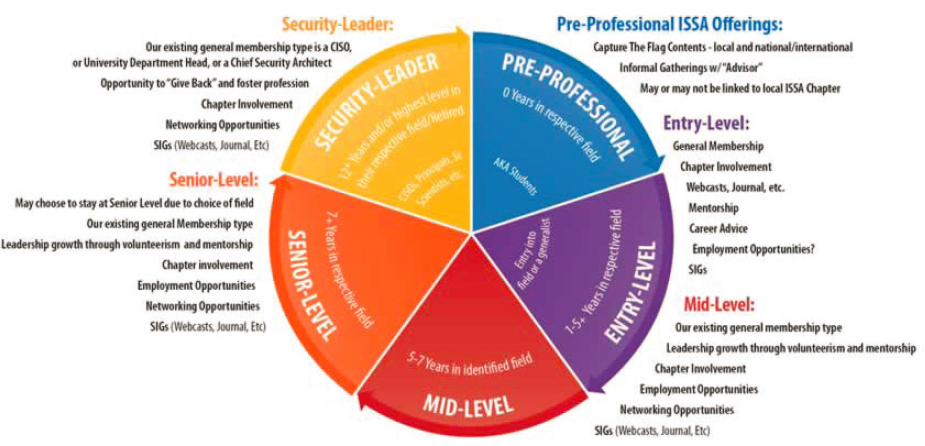
SOURCE: ISSA. Available at: https://www.issa.org/cybersecurity-career-lifecycle/.
and Privacy Practitioner (HISPP) and the Master Mobile Applications Developer (MMAD) will support the development of expertise in application domains with specialized technology, regulations, standards, and operations applicable to those domains of operation.
Those that administer professional certifications are compelled to keep their own certifications active and updated in a competitive market (Knapp et al., 2017). Continuing education is important for certifications, especially in a field that is quickly changing. Many employers are also looking for these certifications to help evaluate the skills and knowledge of applicants, especially among those that lack cybersecurity expertise themselves. Aside from showing an employer evidence of competence, these “may be useful indicators of interest and commitment to work in a field and provide a useful complement or supplement to academic degrees in establishing knowledge and commitment” (NRC, 2013, p. 18). However, earning these credentials and learning the associated skills often come at a financial and time cost to employees.
Non-credential offering organizations, such as the International Consortium of Minority Cybersecurity Professionals (ICMCP), offer annual conferences, partnerships on employment events, and scholarships.26 Academic scholarships are provided at multiple degree levels, including graduate degrees. The ICMCP tracks workforce and market characteristics in the cybersecurity sector. The organization provides training and certifications to members. Students and professionals have access to publications and resources to prepare for certification examinations and expand knowledge and credentials.
A goal of certifications is to help ensure that the individual who holds the certificate is competent in the area(s) covered by the certification. For the most part, this tends to be the case, as seen in many of the presentations and discussions the committee heard from corporations, who used certifications as a means to identify employee skill sets. It should be noted, however, that some high-performing security teams in the private sector and the government reject this emphasis on certification, preferring to assess candidates and employees directly on practical knowledge of security topics. These groups even claim to observe a negative correlation between certification and real-world skills.
Finding 3-15: Cybersecurity certifications do not necessarily indicate equal aptitude for the myriad of job tasks that constitute cybersecurity work. Specific certifications may indicate high suitability for specialized roles within the cybersecurity workforce.
Finding 3-16: Employers who cannot provide professional certification training and compensation for certification and professional development will likely struggle to attract talent. This challenge and especially the financial burden may deter interested individuals who might otherwise have pursued the necessary credentials.
Performance Management
Performance management within organizations has evolved from older traditional approaches to performance appraisal (Pulakos et al., 2019). In these older approaches, appraisals typically took place in organizations annually and focused on administrative needs, such as who should receive a raise, be promoted, let go, and so forth. The individual performing the assessment (typically one’s boss) judged and evaluated the effectiveness of the individual in meeting job and organizational needs over the year. A second approach (split role) evolved and eventually became widespread; proposed by Meyer, Kay, and French (1981), in this approach, the individual is not only judged, but also receives developmental feedback (Pulakos et al., 2019).
Today, performance management in many organizations is a continuous process, no longer performed once or twice a year, but as often as necessary (e.g., weekly). It focuses on identifying, measuring, and developing individuals’ strengths and weaknesses. Performance management covers the administrative and developmental roles and includes four additional purposes: information, documentation, organizational maintenance, and strategy (Smither and London, 2009). A Lithuanian study found that the informational component keeps the employees up to date on the supervisor’s, organization’s, and when appropriate, the organization’s customer’s expectations and their
___________________
26 More information about ICMCP is available at: https://www.icmcp.org/.
performance relative to those expectations (Martinaityte et al., 2019). The documentation role codifies information used for various purposes (e.g., promotion, termination). Moving up the level of analysis hierarchy, organization maintenance defines and maintains a talent and competency inventory, which often feeds into a workforce planning system. Finally, the strategic component helps upper and top management achieve business objectives and goals.
An effective performance management system can help ensure there are no surprises to individuals in that they are continually informed of their performance and are provided feedback regarding their performance. As with the developmental component in the original split role approach, there is two-way communication between the ratee and the rater (Meyer et al., 1981). The discussion always should be open, honest, and factual, where performance standards are made clear and effectively communicated. This ensures the ongoing feedback focused on job performance is understood and accepted. Without acceptance, it is unlikely deficient behavior will be modified or changed or that exemplary behavior will emerge (Erez and Kanfer, 1983).
Key aspects of a performance management system are that it needs to be valid, reliable, and acceptable (Ilgen and Feldman, 1983; Murphy and Cleveland, 1991; Tippins et al., 2018). When considering validity, measures need to be relevant to the person/job. This relevance is best developed through a job analysis where the job is described as well as the personal characteristics of individuals who are competent in the job (DeNisi and Murphy, 2017). Reliable and valid measures are relevant to the job, as defined through job analysis. Both structured ratings and rater training help ensure two or more supervisors rating the same individual would have the same ratings when rating the same aspects of an incumbent’s performance (DeNisi and Pritchard, 2006). Reliable and valid job analysis also allows for specificity in the performance management system. This allows for a process whereby, when an employee is deficient, the deficiency is communicated along with clear and tangible guidance for remediation and improvement.
Built in this way (based on a reliable and valid job analysis), and when standardized (consistent evaluation over time and across individuals), both effective and ineffective behaviors can be identified and employed in the performance management system. Furthermore, levels of performance can be specified. For example, at each of the following levels, typical behaviors are specified for employees in the 40th percentile, 50th percentile, 85th percentile, and 95th percentile.
Beginning with a reliable and valid job analysis also ensures meaningfulness (face valid) to the employee. Each employee can be assured they are being evaluated on only those aspects of the job relevant to their position and within their control. Other factors that help ensure meaningfulness include measuring performance at an appropriate frequency (e.g., bi-weekly/monthly) and communicating to the individual how the results are used in administrative decisions. Individual employees need to also be kept abreast of training completed by evaluators, which helps ensure evaluators are sampling the behavior of those rated at an appropriate rate, and their ratings are reliable and free from errors, contamination, and biases (Inderrieden et al., 1988; Kim and Holzer, 2016). Furthermore, in an effective performance management system, there needs to be a clear and objective approach for appeals for cases where the ratee feels a mistake has been made, and when appropriate, the error is corrected.
It is important that employees are made aware that the performance management system applies to all employees, including supervisors and managers. This ensures the system is thorough as it reaches throughout the organization. Thoroughness is also ensured by building from an effective job analysis in that all major job duties and responsibilities are identified and included in the performance measurement and management system. This helps make certain that the employee receives feedback not only on areas needing improvement but also on areas done well. The sources of feedback should be any relevant individual or group the individual interacts with during their work. These sources include supervisor, peers, and customers (historically referred to as a 360-degree review), as relevant to each individual.
Finally, for a performance management system to be accepted, it needs to be perceived as fair by all those in the organization it impacts. Fairness is often assessed via three different types of organizational justice: procedural, distributive, and interactional (Cropanzano et al., 2007). Each is subjective and deals with perceptions. The focus on interactional justice can be broken down into interpersonal and informational justice (Cropanzano et al., 2007). Informational justice centers on expectations of performance, feedback, and the justification for administrative decisions. Interpersonal justice deals with perceptions of the design of the performance management system itself and the effectiveness of the implementation. Procedural justice is concerned with how ratings are determined
and the relationships between ratings and rewards (as well as negative consequences) (Cropanzano et al., 2007). In the case of distributive justice, perceptions of evaluation are assessed relative to the relationship and linkages between ratings and rewards received. It is important to monitor the advancement of diverse employees through the organization. It should be understood that low representation at higher management levels may discourage lower-level candidates from remaining in the organization. Similarly, engagement programs to maintain the interest of new employees may help improve retention rates (e.g., community service, hackathons, etc.)
In summary, today’s performance management system is an evolution of early performance appraisal systems. Performance management is concerned with several essential elements, including describing the job effectively (via a job analysis), ensuring criterion relevance without contamination and deficiency in job duties and responsibilities and the associated ratings by relevant sources (supervisor, peers, customers), providing feedback to the employee in an open, clear and objective manner, and doing everything to facilitate positive perceptions of justice relative to the performance management system.
Diversity and Inclusion in Organizational Culture
Maintaining an inclusive workplace culture is important in attracting and retaining a skilled workforce. It is important to understand how an organization is perceived by current and prospective employees and to take steps to improve the workplace culture so prospective employees feel they will be welcome.
One way that some employers try to improve inclusion is through employee resource groups. Employee resource groups are employee-led groups with shared characteristics or experiences that are designed to foster a sense of belonging and inclusion. These groups are formed around diversity attributes such as ethnic minorities, Veterans, employees with disabilities, and those who identify as LGBTQ+. Resource groups serve as an important tool in developing a workplace culture where members of underrepresented groups feel welcome and represented (Welbourne et al., 2017). That said, forming these affinity groups, while effective from a psychosocial and workplace sense of belongingness, are merely one approach to attract and retain diverse employees.
In the committee’s judgment, organizations tend to focus more on reporting diversity than integrating and building organizational climates that support diversity and inclusion. An organization requires a process of adaptation and maturity over time to create an effective culture and climate reflective of diversity and inclusion. Where a climate of diversity and inclusion does not exist, a dedication to change is required at all levels of leadership, requiring each to buy into the commitment to foster diversity and inclusion. For instance, Liggans and colleagues (2018) described the importance of leadership for understanding the perceptions and attitudes unique to this diverse group to retain and maximize the benefit of Veterans’ in federal jobs. Leadership buy-in is of singular importance in effecting cultural change within the organization.
In the white paper Innovation Through Inclusion: The Multicultural Cybersecurity Workforce (Reed and Acosta-Rubio, 2018), the authors discussed the importance of diversity and culture. Their paper argues that while minority professionals comprise a considerable part of the cybersecurity workforce, they are underrepresented in senior leadership positions. As the authors also reiterated, studies of organizations with racially and ethnically diverse leadership teams demonstrate improved company culture, bottom-line revenues, and confidence in security posture. Additionally, they offered several methods to promote and nurture the success of the group, including “mentorship and training programs, executive leadership programs to promote the advancement of the multicultural workforce, and company-wide recognition programs and events” (p. 8). In the committee’s judgment, diversity of leadership will improve the FAA’s overall cybersecurity performance.
FAA TALENT DEVELOPMENT AND ADVANCEMENT
Reskilling and Training
The FAA should anticipate the need to significantly and continually retool the cybersecurity skills of its workforce given the rapidly changing nature of the challenge—that is, it should not assume that today’s cyber knowledge, skills, and aptitudes are a good predictor of what will be needed in the future.
For example, AI and other automation tools are likely to absorb lower-level tasks, which will place a higher premium on higher-level technical skills such as critical thinking and decision-making skills. These AI automation tools might pose additional cybersecurity threats to the very professionals who are trying to assist. Although the FAA already provides a fair amount of internal training (in person and online), internal courses will not be sufficient where it lags other agencies.
Reskilling options in areas that cannot be met through standard, commercially available training range from leveraging conference workshops and similar sources of up-to-date knowledge to more intensive options such as placing staff (exchange program) at other agencies or federally funded research and development centers (FFRDCs) that are further along. An example of such leading-edge cybersecurity practice is the transition toward “zero-trust network” models.
Finding 3-17: The future FAA cyber workforce will need skills and competencies, certifications, credentials, qualifications, career entry points, and career development pathways to achieve and sustain the mission of the FAA.
Workforce Strategies and Best Practices
Like many organizations, the FAA is facing an increasing challenge of managing and expanding the set of skills required in its cybersecurity workforce. Both industry and government recognize the need for a cybersecurity skill taxonomy using specific position descriptions, training requirements and associated career paths. The FAA’s adoption of the NIST NICE Framework is a cybersecurity best practice, resulting in an industry-recognized lexicon for the many disciplines in cybersecurity. The Framework divides these specializations into the categories depicted in Figure 3-3.
The multidisciplinary nature of cybersecurity is demonstrated in the above categories and is explicitly called out in the definition of cybersecurity provided by the Association for Computing Machinery (ACM)27 Joint Task Force on Cybersecurity Education:
A computing-based discipline involving technology, people, information, and processes to enable assured operations in the context of adversaries. It involves the creation, operation, analysis, and testing of secure computer systems. It is an interdisciplinary course of study, including aspects of law, policy, human factors, ethics, and risk management (JTF, 2017, p. 16).28
Since the implementation of this definition, the NICE Framework (Pub 800-181) has been updated to simplify the creation of work roles using specific building blocks. The new method to identify work roles is more flexible and modularized.29
Development of Cybersecurity Awareness in Organizations
Taking an organizational view of cybersecurity from the CISO’s vantage point, a model should identify the major elements of a cybersecurity program within an organization and the academic disciplines that support each element, emphasizing the multidisciplinary nature of cybersecurity operations. Based on the model, to develop an efficient cybersecurity program, the CISO would begin with a thorough understanding of the goals of the organization seeking protection. This would guide prioritization of cybersecurity investments. Understanding the organization’s goals supports policy development (i.e., this information set will warrant rigorous protection; this one will not). Having established priorities, mitigations would be selected to implement cybersecurity policy—(i.e., will technologies be applied or procedures, or some combination to protect this particular data asset).
___________________
27 ACM is a nonprofit trade group based around computing technologies. Founded in 1947, the ACM is an international organization of more than 100,000 members and based in New York City.
28 In 2017 ACM became the first professional organization to publish curricular guidelines for cybersecurity in which this definition is presented. Prior, NIST in collaboration with NSA had been the primary source for curricular guidance for U.S. universities.
29 More information is available at: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-181r1.pdf.

SOURCE: Adapted from https://niccs.cisa.gov/workforce-development/cybersecurity-workforce-framework.
The organization with a digital footprint needs to create a cybersecurity-conscious environment through effective security awareness training so that individuals at all levels have the appropriate knowledge to keep information secure. It takes one individual to deliberately or inadvertently create a vulnerability that could be exploited. Cybersecurity is the responsibility of everyone in the organization.
Finally, cybersecurity is not a static state, but an ever-evolving set of strategies and protocols. Regular (annual or more frequent) audits provide insight into the effectiveness of achieving the goals of the implemented cybersecurity policy. Corrections can be made to reflect audit findings and technology change. As attackers improve their knowledge and skills, defensive cybersecurity must improve and do so using future-oriented and predictive strategies and use an implementation cycle that scales iteratively and toward continuous improvement. The cyber profession also evolves, spawning new specializations that must be understood in order to recruit appropriately.
Academic cybersecurity curricula can be developed for any academic discipline (e.g., business, computer science, information science, library science, and urban planning programs, psychology [resistance to social engineering]), with each curriculum drawing from the same organizational/operational view of cybersecurity and each taking a relevant slice through the model that aligns with its discipline. For example, recognizing that elements ranging from policy to technology keep information secure, curriculum designers might use the model to develop a business curriculum module that would emphasize management aspects of cybersecurity—policy, compliance procedures, developing an organizational culture of security through awareness training.
Coordination with Human Resources
The above view runs counter to the view that many in the general public have that cybersecurity is purely a technical discipline. However, it is not so simple. One of the challenges in closing the talent gap is to provide tools for managers and human resources (HR) to appropriately describe and recruit individuals for required jobs. NICE serves as one of these tools. Beginning with federal agencies, NICE has been used to write job descriptions that effectively communicate requirements to applicants. Creating a common lexicon for describing employment eliminates confusion and wasted effort. Many large employers (e.g., T-Mobile30) are now adopting the NICE Framework in their HR processes.
Using the NICE Framework as a Guide to Identify Intense Personal Interest
Using a sports analogue to training cybersecurity experts, an athlete’s passion for their chosen sport is accompanied by a desire, almost a craving, to work enthusiastically hard on self-improvement, allowing them to succeed and flourish in their field. The committee members share the opinion of some researchers that a person’s commitment to persevere, despite obstacles, and their resilience to overcome setbacks in order to strive for their dreams are a reflection of their internal nature. In other words, intensity to succeed works from the inside out, leveraging passion, and predisposition to a preferred activity and/or outcome.
___________________
30 More information is available at: https://www.nist.gov/system/files/documents/2017/08/04/t-mobile.pdf.
In cybersecurity education programs at the Center for Information Assurance and Cybersecurity (CIAC), students are offered a wide array of outside professional activities to assist in finding their passion in cybersecurity. They are encouraged to take multidimensional career assessment tests that measure interests, skills, and work styles to help identify what they like to do and what they are good at. These activities focus students on finding their ideal pathway in cybersecurity using NICE as a guide. In the committee’s judgment, when a student is passionate about their choice, they become dedicated to learning—a basis for becoming a lifelong learner that is essential for success in this fast-moving field. Passionate students often join cyber competitions, spend extra time on homework, and seek mentors—all of which accelerates their learning and growth. Application of NICE is useful beyond graduation; graduates may use the NICE Framework to make decisions about their first destination for employment, thus making more informed decisions about the right environment for their own aspirations.
Other tools have been released that may serve as effective career guides. One such tool is the Cyber Career Pathways Tool, which is meant to help individuals identify, build, and navigate a potential cyber career pathway by increasing understanding of the knowledge, skills, and abilities needed to begin, transition, or advance in a cyber career. In the committee’s judgment, the Cyber Career Pathways Tool should be shared with individuals looking to start a career in cybersecurity, considering a change within the cyber field, college students, managers, and workforce development specialists interested in the cyber ecosystem. The Cyber Career Pathways Tool resource presents a new and interactive way to explore Work Roles within the NICE Framework. It depicts the cyber workforce as five distinct, yet complementary, skill communities. It also highlights core attributes among each of the 52 Work Roles and offers actionable insights for employers, professionals, and individuals considering a career in cyber.31
SUMMARY
This chapter has provided a discussion of human resource and management approaches relative to the cybersecurity workforce, using the ELC model. The chapter began by considering how organizations recruit and hire talent, and how cybersecurity and federal employers specifically can attract the needed talent. In the section on talent advancement and development, the chapter examined training, certifications, conferences, and organizational culture.
Throughout this chapter, the committee considered aspects related to retention, the third level of the ELC model. This comprises both organizational characteristics that drive employee turnover and the role of compensation, including information on current compensation for cybersecurity talent. One aspect of retention addressed at length at various points in the chapter is compensation, which is an important component of talent management and retention for the FAA to consider. While it may be difficult for the FAA to directly compete with salaries from the private sector, the chapter reviews certain monetary incentives within their discretion that can be utilized. The committee also discussed cybersecurity talent retention and provides strategies not directly tied to compensation.
The committee also explored performance management strategies to cultivate cybersecurity competencies in the workforce. The section on talent development examined long-term initiatives that seek to support the growth of the cybersecurity workforce through the development of a hiring pipeline that involves cultivating cybersecurity talent in educational institutions. Finally, diversity is a necessary and integral part of any HR and management program. Throughout the chapter the committee considered special issues and challenges targeting diversity.
___________________
31 This tool was created and is maintained in partnership with the Interagency Federal Cyber Career Pathways Working Group, led by CISA, the Department of Defense, and the Department of Veterans Affairs. Other tools and resources for current and future cybersecurity professionals can be found on CISA’s National Initiative for Cybersecurity Careers and Studies website: https://niccs.cisa.gov/workforce-development/cyber-career-pathways.
Conclusions and Recommendations
CONCLUSION 3-1: The Federal Aviation Administration would benefit from engaging more robustly with recruitment fairs and college programs to bolster the hiring pipeline for cybersecurity positions.
CONCLUSION 3-2: “Early interest” is a notion that can be identified and then leveraged in recruitment. In the case of the Federal Aviation Administration, this includes not just an early interest in aviation, but also an early interest in cyber.
CONCLUSION 3-3: Long-term university partnerships using such activities as scholars-in-residence and fellowships from the Federal Aviation Administration might enhance the agency’s ability to recruit talented recent college graduates.
CONCLUSION 3-4: In the case of the Federal Aviation Administration (FAA), there is a lack of clarity around what the marketing and branding are for promoting cybersecurity occupations, and there is a need for further identifying what the FAA could do to promote itself as an attractive/fulfilling/rewarding place for cybersecurity work.
CONCLUSION 3-5: The committee concludes that the use of numerical targets, such as number of the Scholarship for Service Program program graduates recruited and/or hired to internships and permanent employment, would be a useful mechanism for engaging additional interns with this program.
CONCLUSION 3-6: An optimal way of improving the cybersecurity workforce involves hiring employees with the right skill set and then reskilling them as the job requirements change. Two promising options for improving the cyber workforce in this fashion include programs such as the Scholarship for Service program or reskilling current employees.
The future FAA workforce will need skills and competencies, certifications, credentials, qualifications, career entry points, and career development pathways to achieve and sustain the mission of the FAA. In working to achieve and sustain such a workforce, the FAA will benefit from focused efforts in collaboration with educational institutions and the private sector, engagement in a wide variety of student and career development, and a well-rounded marketing effort that promotes the FAA as a desirable employer. Implementation of the following recommendations would help the FAA achieve its cybersecurity workforce goals.
RECOMMENDATION 3-1: The Federal Aviation Administration should evaluate the use of existing and future internship programs as valuable tools to create a more diverse cybersecurity workforce.
RECOMMENDATION 3-2: At the organizational level, promoting and marketing the agency as an attractive/fulfilling/rewarding place for cybersecurity would facilitate recruiting. However, there is a lack of clarity on what the Federal Aviation Administration’s (FAA’s) current marketing strategy and branding are for cybersecurity. While any FAA marketing approach needs to conform with the larger context of the brand of the federal government, actions to develop a strong FAA-specific marketing presence in cybersecurity should be implemented. To do so, the FAA should identify priority targets for recruitment (and identify their characteristics) and tailor their marketing to reach those targets effectively.
RECOMMENDATION 3-3: The Federal Aviation Administration (FAA) would benefit from engaging more robustly with recruitment fairs and college programs to bolster the hiring pipeline for cybersecurity positions. Moreover, long-term university partnerships using such activities as scholars-in-residence from the FAA might enhance the FAA’s ability to recruit talented recent college graduates.
The FAA should organize and expand its reach and partnerships with universities around cybersecurity preparation efforts in academic and research areas to assist in the development of a talented cybersecurity workforce. Among these partnerships, the FAA should explore opportunities to develop meaningful and sustainable relationships with minority serving institutions32 to access upcoming cybersecurity graduates via internships and employment opportunities.
RECOMMENDATION 3-4: Hiring employees with the right skill set and then growing them as the job requirements change is optimal. This is possible through programs such as the Scholarship for Service (SFS) program or reskilling current employees, which are two approaches for improving the cyber workforce. So far, the Federal Aviation Administration (FAA) has not partnered with the SFS program to effectively recruit cybersecurity talent to the organization; this is a missed opportunity and a partnership should be pursued. In this and other ways, the FAA should explore a wide range of options for meeting future reskilling needs, including internal, outside commercial, industry conference workshops, and outside rotations in agencies and industry.
RECOMMENDATION 3-5: Reskilling the existing workforce can be an important component of developing the needed future cybersecurity workforce for the Federal Aviation Administration and over time worker reskilling should grow beyond technical skills to include managerial and operational skills.
RECOMMENDATION 3-6: The Federal Aviation Administration should continue to use the National Initiative Cybersecurity Education tool to develop work roles that fit into a larger, well-designed organizational structure.
RECOMMENDATION 3-7: The Federal Aviation Administration should train its cyber leadership on best practices in building a diverse and inclusive organizational culture and should customize these best practices to implement a more contemporary culture.
RECOMMENDATION 3-8: When comparing nonsalary monetary incentives, the Federal Aviation Administration (FAA) cannot compete with industry pay scales. The FAA should leverage nonsalary monetary incentives (e.g., career development reimbursements, performance bonuses, etc.) as part of the overall compensation package.
RECOMMENDATION 3-9: “Early interest” in cybersecurity and in aviation by young students is a notion that can be identified and then leveraged in Federal Aviation Administration (FAA) recruitment. Two targeted actions are recommended here to foster and capitalize on FAA related “early interest”:
- The FAA should review its past experience with effective fellowship and internship programs and also look to other federal agencies for proven models, such as the Department of Defense SMART scholarship program.
- The FAA should sponsor and leverage postsecondary-level cyber competitions.
REFERENCES
Acikgoz, Y. 2019. Employee recruitment and job search: Towards a multi-level integration. Human Resource Management Review, 29(1), 1–13.
___________________
32 The U.S. Department of Education’s Minority-Serving Institutions Program includes the following organizations: Historically Black Colleges and Universities (HBCUs); Hispanic-Serving Institutions (HSIs); Tribal Colleges and Universities (TCUs); and Asian American and Pacific Islander Serving Institutions (AAPISIs).
Acosta, J.C., McKee, J., Fielder, A., and Salamah, S. 2017. A Platform for Evaluator-Centric Cybersecurity Training and Data Acquisition. MILCOM 2017—2017 IEEE Military Communications Conference (MILCOM), Baltimore, MD, pp. 393–399. doi: 10.1109/MILCOM.2017.8170768.
Adler, M., and Ziglio, E. 1996. Gazing into the Oracle: The Delphi Method and Its Application to Social Policy and Public Health. London: Kingsley Publishers.
Amankwah-Amoah, J. 2015. An integrative review of the antecedents and consequences of lateral hiring. Journal of Management Development, 34(7), 754–772.
Baer, M.D., Bundy, J., Garud, N., and Kim, J.K. 2018. The benefits and burdens of organizational reputation for employee well-being: A conservation of resources approach. Personnel Psychology, 71(4), 571–595.
Bishop, M. 2004. Introduction to Computer Security. Boston, MA: Pearson Education, Inc.
Burrell, D.N. 2018. An exploration of the cybersecurity workforce shortage. International Journal of Hyperconnectivity and the Internet of Things, 2(1), 29–41. doi: 10.4018/IJHIoT.2018010103.
Burke, M. ND. Six Stages to Success with the Employee Lifecycle. 6Q. Available: https://inside.6q.io/six-stages-to-success-with-the-employee-lifecycle/.
Caulkins, B.D., Badillo-Urquiola, K., Bockelman, P., and Leis, R. 2016. Cyber Workforce Development Using a Behavioral Cybersecurity Paradigm. 2016 International Conference on Cyber Conflict (CyCon U.S.), Washington, DC, pp. 1–6. doi: 10.1109/CYCONUS.2016.7836614.
Champion, M., Jariwala, S., Ward, P., and Cooke, N.J. 2014. Using Cognitive Task Analysis to Investigate the Contribution of Informational Education to Developing Cyber Security Expertise. Proceedings of the Human Factors and Ergonomics Society Annual Meeting, 58, Philadelphia, PA, pp. 310–314.
Chapman, D.S., Uggerslev, K.L., Carroll, S.A., Piasentin, K.A., and Jones, D.A. 2005. Applicant attraction to organizations and job choice: A meta-analytic review of the correlates of recruiting outcomes. Journal of Applied Psychology, 90(5), 928.
CISA (Cybersecurity and Infrastructure Security Agency). 2019. Cybersecurity Talent Identification and Assessment. January. Available: https://niccs.cisa.gov/sites/default/files/documents/pdf/cybersecurity%20talent%20identification%20and%20assessment.pdf?trackDocs=cybersecurity%20talent%20identification%20and%20assessment.pdf.
Collins, C.J., and Stevens, C.K. 2002. The relationship between early recruitment-related activities and the application decisions of new labor-market entrants: A brand equity approach to recruitment. Journal of Applied Psychology, 87(6), 1121.
Cook. S. 2020. “The Cybersecurity Imperative.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. April 23, 2020. Virtual meeting.
Coovert, M.D., Wiernik, B., and Martin, J. 2020. Use of Technology-Enhanced Simulations for Cyber Aptitude Assessment: Phase II Prototype Development. Technical Report, Accession Number: AD1107016. Fort Belvoir, VA: Defense Technical Information Center.
Coovert, M.D., Wiernik, B., and Martin, J. 2019. Use of Technology-Enhanced Simulations for Cyber Aptitude Assessment. Technical Report. Plant City, FL: MDC & Associates.
Coovert, M.D., Winner, J., Bennett, W., and Howard, D.J. 2017. Serious games are a serious tool for team research. International Journal of Serious Games, 4(1). doi: 10.17083/ijsg.v4i1.141.
Coull, N., Donald, I., Ferguson, I., Keane, E., Mitchell, T. Smith, O.V., Stevenson, E., and Tomkins, P. 2017. The gamification of cybersecurity training. International conference on technologies for e-learning and digital entertainment. Edutainment 2017. Lecture Notes in Computer Science, 10345, 108–111. doi: 10.1007/978-3-319-65849-0_13.
Cropanzano, R., Bowen, D.E., and Gilliland, S.W. 2007. The management of organizational justice. Academy of Management Perspectives, 21(4), 24–48.
Crumpler, W., and Lewis, J.A. 2019. Cybersecurity Workforce Gap. Washington, DC: Center for Strategic and International Studies.
Darnold, T.C., and Rynes, S.L. 2013. Recruitment and Job Choice Research: Same as It Ever Was? Pp. 103–143 in Handbook of Psychology: Volume 12 Industrial and Organizational Psychology (I.B. Weiner, N.W. Schmitt, and S. Highhouse, eds.). Hoboken, NJ: John Wiley and Sons, Inc.
DeNisi, A.S., and Murphy, K.R. 2017. Performance appraisal and performance management: 100 years of progress? Journal of Applied Psychology, 102(3), 421.
DeNisi, A.S., and Pritchard, R.D. 2006. Performance appraisal, performance management and improving individual performance: A motivational framework. Management and Organization Review, 2(2), 253–277.
DHS (Department of Homeland Security). 2016. Cybersecurity Workforce Development Toolkit: How to Build a Strong Cybersecurity Workforce. Available: https://niccs.cisa.gov/sites/default/files/documents/pdf/cybersecurity_workforce_development_toolkit.pdf?trackDocs=cybersecurity_workforce_development_toolkit.pdf.7/978-3-319-77028-4_20.
Domínguez, M., Prada, M.A., Reguera, P., Fuertes, J.J., Alonso, S., and Morán, A. 2017. Cybersecurity training in control systems using real equipment. IFAC-PapersOnLine, 50(1), 12179–12184.
Dreibelbis, R.C., Martin, J., Coovert, M.D., and Dorsey, D.W. 2018. The looming cybersecurity crisis and what it means for the practice of industrial and organizational psychology. Industrial and Organizational Psychology, 11(2), 346–365.
Embry, J. 2020. “U.S. Coast Guard.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. June 29, 2020. Virtual meeting.
Erez, M., and Kanfer, F.H.. 1983. The role of goal acceptance in goal setting and task performance. Academy of Management Review, 8(3), 454–463.
Gestwicki, P., and Stumbaugh, K. 2015. Observations and opportunities in cybersecurity education game design. 2015 Computer Games: AI, Animation, Mobile, Multimedia, Educational and Serious Games (CGAMES), Louisville, KY, pp. 131–137. doi: 10.1109/CGames.2015.7272970.
Harris, C., Brown, L.W., and Wright, P. 2020. If You Spend It, They Will Come: Recruiting Expenses, Reputation, and Human Capital Acquisition. P. 13282 In Academy of Management Proceedings (Vol. 2020, No. 1). Briarcliff Manor, NY: Academy of Management.
Hernandez, S. 2020. “Government Cyber Workforce Challenges.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. February 20, 2020. Washington, DC.
Huynh D., Luong P., Iida H., and Beuran, R. 2017. Design and Evaluation of a Cybersecurity Awareness Training Game. Pp. 183–188 in Entertainment Computing – ICEC 2017. Lecture Notes in Computer Science, vol 10507 (N. Munekata, I. Kunita, and J. Hoshino, eds.). Cham: Springer. doi: 10.1007/978-3-319-66715-7_19.
Ilgen, D.R., and Feldman, J.M. 1983. Performance appraisal: A process focus. Research in Organizational Behavior, 5, 141–197.
Inderrieden, E.J., Keaveny, T.J., and Allen, R.E. 1988. Predictors of employee satisfaction with the performance appraisal process. Journal of Business and Psychology, 2(4), 306–310.
Jackson, S.E., and Joshi, A. 2004. Diversity is social context: A multi-attribute, multilevel analysis of team diversity and sales performance. Diversity and the Workplace, 25(6), 675–702.
Jacob, J., Wei, W. Sha, K., Davari, S., and Yang, T.A. 2018. Is the NICE Cybersecurity Workforce Framework (NCWF) Effective for a Workforce Comprising of Interdisciplinary Majors? Proceedings of the 16th International Conference on Scientific Computing (CSC’18), Las Vegas, NV, pp. 124–130.
JTF (Joint Task Force on Cybersecurity Education). 2017. Cybersecurity Curricula 2017 Curriculum Guidelines for Post-Secondary Degree Programs in Cybersecurity. A Report in the Computing Curricula Series Joint Task Force on Cybersecurity Education. Available: https://www.acm.org/binaries/content/assets/education/curricula-recommendations/csec2017.pdf.
Justice, C., and Vyas, R. 2017. Cybersecurity Education: Runlabs Rapidly Create Virtualized Labs Based on a Simple Configuration File. American Society for Engineering Education Annual Conference and Exposition, Conference Proceedings, Columbus, OH, paper ID 18888.
Katsantonis, M.N., Fouliras, P., and Mavridis, J. 2017. Conceptualization of Game Based Approaches for Learning and Training on Cyber Security. PCI 2017: Proceedings of the 21st Pan-Hellenic Conference on Informatics, 36, Larissa, Greece, pp. 1–2. doi: 10.1145/3139367.3139415.
Kempinksi, R., and Cunningham, L. 2020. “Recruiting Mission-Critical Cyber Personnel.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. September 16, 2020. Virtual meeting.
Kim, T., and Holzer, M. 2016. Public employees and performance appraisal: A study of antecedents to employees’ perception of the process. Review of Public Personnel Administration, 36(1), 31–56.
Knapp, K.J., Maurer, C., and Planchkinova, M. 2017. Maintaining a cybersecurity curriculum: professional certifications as valuable guidance. Journal of Information Systems Education, 28(2), 101–114.
Kristof-Brown, A.L., Zimmerman, R.D., and Johnson, E.C. 2005. Consequences of individuals’ fit at work: A meta-analysis of person-job, person-organization, person-group, and person-supervisor fit. Personnel Psychology, 58, 643–672.
Lawong, D., Ferris, G.R., Hochwarter, W., and Maher, L. 2019. Recruiter Political Skill and Organization Reputation Effects on Job Applicant Attraction in the Recruitment Process. Career Development International. Available: https://www.researchgate.net/publication/335267146_Recruiter_political_skill_and_organization_reputation_effects_on_job_applicant_attraction_in_the_recruitment_process_A_multi-study_investigation.
Le Blanc, K., and Freeman, S. 2016. Investigating the Relationship between Need for Cognition and Skill in Ethical Hackers. Pp. 223–228 in Advances in Human Factors in Cybersecurity. Advances in Intelligent Systems and Computing, vol 501 (D. Nicholson, ed.). Cham: Springer.
Lewis, A. 2020. “Industry Cyber Workforce Challenges.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. February 20, 2020. Washington, DC.
Li, C., and Kulkarni, R. 2016. Survey of Cybersecurity Education through Gamification. 2016 American Society for Engineering Education Annual Conference and Exposition, New Orleans, LA, paper ID 16728.
Liggans, G., Attoh, P., Gong, T., Chase, T., Clark, P., and Russell, M. 2018. Diversity and inclusion efforts in federal agencies: A context for exploring perceptions of military veterans. Journal of Veterans Studies, 3(1), 139–151. doi: 10.21061/jvs. v3i1.48.
Lowenstein, M.W. 2017. Employee Ambassadorship: Optimizing Customer-Centric Behavior from the Inside-Out and Outside-In. New York: Business Expert Press.
Mack, N.A., Cummings, R., Womack, K., Dowling, N., Huff, Jr., E.W., and Gosha, K. 2019. From Midshipmen to Cyber Pros: Training Minority Naval Reserve Officer Training Corp Students for Cybersecurity. Proceedings of the 50th ACM Technical Symposium on Computer Science Education, Minneapolis, MN, pp. 726–730.
Mannix, E., and Neale, M.A. 2005. What differences make a difference?: The promise and reality of diverse teams in organizations. Psychological Science in the Public Interest, 6(2), 31–55.
Marinos, N. 2017. Cybersecurity: Federal Efforts are Underway That May Address Workforce Challenges. Washington, DC: United States Government Accountability Office.
Martinaityte, I., Sacramento, C., and Aryee, S. 2019. Delighting the customer: Creativity-oriented high-performance work systems, frontline employee creative performance, and customer satisfaction. Journal of Management, 45(2), 728–751.
McGettrick, A., Cassel, L.N., Dark, M., Hawthorne, E.K., and Impagliazzo, J. 2014. Toward Curricular Guidelines for Cybersecurity. Proceedings of the 45th ACM Technical Symposium on Computer Science Education (SIGCSE ‘14), New York, NY, pp. 81–82. doi: 10.1145/2538862.2538990.
Mendelberg, T., Karpowitz, C., and Oliphant, J. 2014. Gender inequality in deliberation: Unpacking the black box of interaction. Perspectives on Politics, 12(1), 18–44. doi: 10.1017/S1537592713003691.
Meyer, H.H., Kay, E., and French, J.R. 1981. Split Roles in Performance Appraisal. Pp. 70–84 in Psychology and Industrial Productivity (M.M. Gruneberg, and D.J. Oborne, eds.). London: Palgrave Macmillan.
Morgan, S. 2017. Cybersecurity Labor Crunch to Hit 3.5 Million Unfilled Jobs by 2021. Cybersecurity Business Report. Available: https://www.csoonline.com/article/3200024/cybersecurity-labor-crunch-to-hit-35-million-unfilled-jobs-by-2021.html.
Murphy, K.R., and Cleveland, J.N. 1991. Performance Appraisal: An Organizational Perspective. Boston, MA: Allyn & Bacon.
NASEM (National Academies of Sciences, Engineering, and Medicine). 2019. Minority Serving Institutions: America’s Underutilized Resource for Strengthening the STEM Workforce. Washington, DC: The National Academies Press.
NASEM. 2018. Assessing and Responding to the Computer Science Undergraduate Enrollments. Washington, DC: The National Academies Press.
NASEM. 2017. Foundational Cybersecurity Research: Improving Science, Engineering, and Institutions. Washington, DC: The National Academies Press. doi: 10.17226/24676.
NRC (National Research Council). 2013. Professionalizing the Nation’s Cybersecurity Workforce? Criteria for Decision-Making. Washington, DC: The National Academies Press.
Nessi, D. 2020. “Building a Cybersecurity Team: The Airport Perspective.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. June 30, 2020. Virtual meeting.
Newhouse, W. Keith, S., Scribner, B., and Witte, G. 2017. National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework. NIST Special Publication 800-181. Gaithersburg, MD: National Institute of Standards and Technology. doi: 10.6028/NIST.SP.800-181.
Ng, E.S., and Sears, G.J. 2017. The glass ceiling in context: The influence of CEO gender, recruitment practices and firm internationalization on the representation of women in management. Human Resource Management Journal, 27(1), 133–151.
Oltsik, J. 2017. Research Report: The Life and Times of Cybersecurity Professionals. The Enterprise Strategy Group, Inc., and Information Systems Security Association International. Available: https://www.esg-global.com/hubfs/issa/ESG-ISSA-Research-Report-Life-of-Cybersecurity-Professionals-Nov-2017.pdf.
OMB (Office of Management and Budget). 2016. Memorandum for Heads of Executive Department and Agencies M-16-15: Federal Cybersecurity Workforce Strategy. Available: https://www.whitehouse.gov/sites/whitehouse.gov/files/omb/memoranda/2016/m-16-15.pdf.
Page, S. 2019. The Diversity Bonus: How Great Teams Pay Off in the Knowledge Economy. Princeton, NJ: Princeton University Press.
Pelt, D.H.M., van der Linden, D., Dunkel, C.S., and Born, M.P. 2017. The general factor of personality and job performance: Revisiting previous meta-analyses. International Journal Selection and Assessment, 25, 333–346. doi: 10.1111/ijsa.12188.
Perez, J. 2020. “UPS Cybersecurity Defense In-Depth Strategy.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. June 29, 2020. Virtual meeting.
Piotrowski, V. 2020. “CyberCorps® Scholarship for Service Program (SFS).” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. April 22, 2020. Virtual meeting.
Pulakos, E.D., Mueller-Hanson, R., and Arad, S. 2019. The evolution of performance management: Searching for value. Annual Review of Organizational Psychology and Organizational Behavior, 6, 249–271. doi: 10.1146/annurev-org-psych-012218-015009.
Reed, J., and Acosta-Rubio, J. 2018. Innovation Through Inclusion: The Multicultural Cybersecurity Workforce. An (ISC)2 Global Information Security Workforce Study. (ISC)2. Available: https://www.isc2.org/-/media/Files/Research/InnovationThrough-Inclusion-Report.ashx.
Resick, C.J., Baltes, B.B., and Shantz, C.W. 2007. Person-organization fit and work-related attitudes and decisions: Examining interactive effects with job fit and conscientiousness. Journal of Applied Psychology, 92(5), 1446–1455. doi: 10.1037/0021-9010.92.5.1446.
Reynolds, D., and Dickter, D.N. 2017. Technology and Employee Selection: An Overview. Pp. 855–873 in Handbook of Employee Selection (2nd ed.) (J.L. Farr, and N.T. Tippins, eds.). New York: Routledge.
Santos, O. 2019. Developing Cybersecurity Programs and Policies. London, UK: Pearson Education, Inc.
Santos, D., Goel, S., Costanzo, J., Sagan, D., and Buddelmeyer, P. 2020. A Roadmap for Successful Regional Alliances and Multistakeholder Partnerships to Build the Cybersecurity Workforce. NISTIR 8287. Gaithersburg, MD: National Institute of Standards and Technology.
Schneider, F.B. 2013. Cybersecurity education in universities. IEEE Security & Privacy, 11(4), 3–4. doi: 10.1109/MSP.2013.84.
Siraj, A. 2020. “Towards Gender Balance CyberSecurity Workforce.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. April 23, 2020. Virtual meeting.
Smith-Doerr, L., Alegria, S.N., and Sacco, T. 2017. How diversity matters in the US science and engineering workforce: A critical review considering integration in teams, fields, and organizational contexts. Engaging Science, Technology, and Society, 3, 139–153.
Smither, J.W., and London, M. 2009. Performance Management: Putting Research into Action. Vol. 21. San Francisco, CA: Josey-Bass.
Spidalieri, F., and McArdle, J. 2016. Transforming the next generation of military leaders into cyber-strategic leaders: The role of cybersecurity education in US service academies. The Cyber Defense Review, Spring, 141–163.
Tadmor, C.T., Satterstrom, P., Jang, S., and Polzer, J.T. 2012. Beyond individual creativity: The superadditive benefits of multicultural experience for collective creativity in culturally diverse teams. Journal of Cross-Cultural Psychology, 43(3), 383–392.
Tioh, J.-N., Mina, M., and Jacobson, D. 2017. Cyber Security Training: A Survey of Serious Games in Cyber Security. Institute of Electrical and Electronics Engineers Frontiers in Education Conference, 1, Indianapolis, IN, pp. 1–5.
Tippins, N., Sackett, P., and Oswald, F. 2018. Principles for the validation and use of personnel selection procedures. Industrial and Organizational Psychology, 11(S1), 1–97.
Tisu, L., Lupșa, D., Vîrgă, D., and Rusu, A. 2020. Personality characteristics, job performance and mental health: The mediating role of work engagement. Personality and Individual Differences, 153. doi: 10.1016/j.paid.2019.109644.
Turner, D. 2021. Vets facing difficult transition to civilian jobs. Stars and Stripes. Available: https://www.military.com/veteranjobs/career-advice/job-hunting/vets-facing-difficult-transition-to-civilian-jobs.html.
Urias, V.E., Van Leeuwen, B., Stout W.M.S., and Lin, H.W. 2017. Dynamic Cybersecurity Training Environments for an Evolving Cyber Workforce. In 2017 IEEE International Symposium on Technologies for Homeland Security (HST), Waltham, MA, pp. 1–6. doi: 10.1109/THS.2017.7943509.
Vogel, R. 2016. Closing the cybersecurity skills gap. Salus Journal, 4(2), 32–46. doi: 10.3316/informit.093144667545339.
Wang, P., and D’Cruze, H. 2019. Certification in cybersecurity workforce development: A case study. International Journal of Hyperconnectivity and the Internet of Things (IJHIoT), 3(2), 38–57.
Wang, J., Cheng, G.H.L., Chen, T., and Leung, K. 2019. Team creativity/innovation in culturally diverse teams: A meta-analysis. Journal of Organizational Behavior, 40(6), 693–708.
Weber, L. 2019. Why Companies are Failing at Reskilling. Wall Street Journal, April 19.
Welbourne, T.M., Rolf, S., and Schlachter, S. 2017. The case for employee resource groups: A review and social identify theory-based research agenda. Personnel Review, 46(8), 1816–1834. doi: 10.1108/PR-01-2016-0004.
Worden, M., and Romero, H. 2020. “Raytheon Cyber and Aviation Security.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. April 23, 2020. Virtual meeting.
Wright, M. 2015. Improving cybersecurity workforce capacity and capability. Information Systems Security Association International Journal, 13(10), 13–20.
Yang, L-Q., Levine, E.L., Smith, M.A., Ispas, D., and Rossi, M.E. 2008. Person-environment fit or person plus environment: A meta-analysis of studies using polynomial regression analysis. Human Resources Management Review, 18(4), 311–321.






























