4
Additional Employee and Organizational Considerations
INTRODUCTION
A diverse cybersecurity workforce has become an increasingly critical component of public and private organizations, including the Federal Aviation Administration (FAA). This chapter continues the discussion begun in Chapter 3 of the employee lifecycle (ELC) model by turning to a consideration of the third and fourth stages of the ELC: Retention and Retirement. The committee first describes opportunities for the FAA’s talent retention, talent pipeline development, and retirement. The chapter concludes by highlighting public and private best practices in cybersecurity organizational structure, cybersecurity skill taxonomies, cybersecurity sourcing, and inclusion in the cybersecurity program.
RETENTION
The retention stage of the ELC model addresses how organizations can ensure their workplace remains attractive to their skilled employees. This includes looking at the factors driving employee turnover, among them the role of compensation in either retaining current employees or incentivizing them to leave for other opportunities. Employee turnover is a major concern for nearly half of the managers who belong to the Society for Human Resource Management (SHRM), the primary professional organization for human resource professionals (SHRM, 2018). This focus on turnover is due at least in part to the cost associated with hiring replacement employees. The replacement cost can be estimated between 90 and 200 percent of annual salary (Allen et al., 2010).
One of the first research-based models to explain employee turnover was developed by Mobley (1977). Mobley established a linkage between psychological withdrawal (e.g., thinking of quitting), behavioral indicators (e.g., increased absenteeism, tardiness), and the turnover behavior itself. External factors, such as the availability of alternative jobs, also influence an employee’s decision to leave an organization. Subsequent research on turnover led to the identification of other important attitudes held by employees, including organizational commitment, engagement, perception of being treated fairly by the organization (Narayanan et al., 2019), and empowerment.
An unfolding model of turnover was developed by Lee and Mitchell (1994). According to this model, turnover is characterized by four distinct paths, each with distinct foci, psychological processes, and external influences. These authors make a case that turnover can be triggered by critical events, such as an unexpected job offer, spouse or family influence, and social abuse (e.g., bullying from supervision or peers) on the job. Fit models (introduced in Chapter 3) are also useful in explaining the accumulation (or lack) of dissatisfaction on the part
of the employee. The better an individual’s knowledge, skills, abilities, and other characteristics (KSAOs) fit the requirements of the job, the work team, and organization, the more satisfied (less dissatisfied) the individual is (Lee and Mitchell, 1994; Subramony, 2009; Wolfson and Mathieu, 2018). As retention is influenced by each of these factors, each factor needs to be monitored and appropriately neutralized or countered (e.g., an outside job offer receives a counteroffer).
The process of managing employee retention in the committee’s judgment needs to be evidence-based. Surveys are often useful in capturing attitudinal measures such as job satisfaction and organizational commitment. Similarly, job, team, and organizational fit can be measured via surveys and/or during the developmental phase of an annual (or more frequent) performance appraisal (Borman et al., 1997; Krumm and Hertel, 2013; Levy et al., 2011). To the extent possible, it is advisable that job satisfaction, organizational commitment, fit, and alternative job availability be monitored as frequently as possible (e.g., 3–4 times per year) using analytics and statistical analysis to model individual and group trends, and acting when necessary to counter or neutralize pressures that tend to increase turnover. The organization also needs to be sensitive to generational differences as certain groups, such as millennials, are often motivated by and hold different values than other generations. Generational differences need to be identified and managed along with traditional constructs associated with retention or turnover, such as satisfaction, commitment, and fit measures (including P-O, or person-organization fit; P-J, or person-job fit; P-T, or person-team fit).
Based on a meta-analysis of the turnover literature, Lee and colleagues (2018) developed a typology of four classes of individuals who stay/turnover. The four types of individuals described below should receive different targeted interventions as retention strategies. Some stay in the organization because they want to and can stay (enthusiastic stayers—job is fulfilling and has good fit indices); and those who want to leave the organization and have the ability to do so (enthusiastic leavers—have other jobs available to them). A third group wants to stay but they must leave (reluctant leavers—for example are let go during a downturn in the economy), and those who want to leave but must stay (reluctant stayers—e.g., family/spouse constraints inhibit leaving). It is straightforward to see how individuals in each group would require and respond to alternative internal and external motivation and retention strategies. Similarly, a close examination of satisfaction and embeddedness surveys for each group might reveal important issues relative to turnover. For example, the organization might ascertain it is top-heavy in reluctant stayers, resulting in productivity issues. In the committee interviews with FAA employees, there were discussions of losing younger cyber talent during government furloughs.1 These employees were reluctant to leave but needed to as they had to support themselves and their families.2
Compensation
According to salary.com,3 the average information security (IS) and cybersecurity salary is $106,972 as of July 2020.4 The 2020 Cybersecurity Salary Survey looks at five positions: Security Analyst/Threat Intelligence Specialist, Security Architect/Cloud Security Architect, Penetration Tester, Network Security Engineering, and Security Director/Manager (Cynet, 2020). The survey looks at salaries, relative organizational impacts (e.g., geolocation, industry, etc.), and individual factors (e.g., gender, experience, certification). According to the survey, location matters with salaries being higher in the United States than in other continents. Bonuses were also common except among Security Analysts, ranging between 1 and 10 percent per year. Another finding was that a degree does not guarantee a higher salary; among those surveys, similar salary ranges were found for those with and without a college degree.
In addition to salary, other benefits cybersecurity employees are looking for can be hard to measure; these include the ability to learn on the job; access to a senior person/being a senior person; training resources; potential for contribution/change; organizational culture, organizational fit, and organizational support to retain cybersecurity talent; a cybersecurity vision or strategy; rewards for employees; and leadership for good cybersecurity (Zurko, 2020).
___________________
1 Focus group discussion with FAA managers and committee members, August 21, 2020. All discussions were conducted in confidentiality, and the names of the participants are withheld by mutual agreement.
2 Focus group discussion with FAA managers and committee members, August 21, 2020.
3 More information is available at: https://www.salary.com/research/salary/posting/information-systems-and-cybersecurity-salary.
4 More information is also available at the U.S. Bureau of Labor Statistics for Occupational Employment and Wage statistics. Data can be found at http://www.bls.org.
Raw pay gaps are driven mainly by compensable factors, with a smaller portion driven by unexplained pay inequities (Greenfield, 2020). From Greenfield’s presentation, the committee learned that the single most important factor determining an employee’s pay is their career level or salary grade (i.e., where they sit in an organization’s hierarchy). Thus, closing raw pay gaps will require organizations to ensure women and people of color gain access to more senior, higher-paying roles. However, even small, unexplained pay gaps deserve attention. A back-of-the-envelope calculation suggests that a 1¢ unexplained pay gap translates into lost wages for women in the U.S. economy of roughly $500 million each week (Greenfield, 2020). Best practices for pay equity include using a robust statistical approach to assess pay equity; having a formalized remediation process to address identified pay equity risks; having an assigned team responsible for conducting pay equity assessment; and enforcing pay equity policies and practices (Greenfield, 2020).
Finding 4-1: Compensation is an important component of talent management and retention for the FAA to consider. While it may be difficult for the FAA to directly compete with salaries from the private sector, certain monetary incentives can be utilized. Aligned with compensation, cyber talent retention and strategies not directly tied to compensation can be attractive to the cyber employee.
In her presentation to the committee, Jamie Embry described how the Coast Guard provides substantial hiring bonuses and retention bonuses to ensure they can attract and retain a sufficient cyber workforce (Embry, 2020). Another tool described by Embry is the ability to gain certifications on the job, which helps train the workforce and serves as an incentive because it supports career development.
There are many constructs5 an organization should be aware of and monitor to keep employees retained. It is important to monitor these via surveys, interviews, and other strategies to gather attitudinal and behavioral data (Lee and Mitchell, 2003). The data should be gathered and statistically analyzed so both long-term and short-term trends are identified at the individual and group levels (Hom et al., 1992). When negative trends (e.g., a rising level of dissatisfaction) emerge, action should be taken to mitigate factors leading to dissatisfaction. Similarly, if an enthusiastic leaver receives a job offer, efforts should be made to counter (Li et al., 2016a).
Workplace flexibility is a powerful tool for talent retention, and changes in telecommuting opportunities related to the COVID-19 pandemic have become an increasingly important issue for employees. Work-life balance is an important factor for many younger employees and is increasingly important for all employees (Singh, 2019). Flexible work schedules and flexibility in work location may be a way to bring talent to less desirable locations. Organizations experiencing difficulty recruiting employees due to work locations should consider allowing telecommuting for job roles that do not require employees to be on site.
Career Advancement and Development
Several of the presenters in the data-gathering sessions indicated the importance of perceived merit in hiring and retention practices. For example, technical cybersecurity professionals may not be motivated in an environment where seniority guides career development. In addition to favoring merit-based advancement, other factors that are important to technical professionals in the cybersecurity fields are that they find their work challenging and interesting, they have sufficient resources to do their work well, and they have career advancement opportunities. In the committee’s conversations with cybersecurity professionals in the FAA, the individuals indicated that they often feel that, due to a lack of resources, the issues they find in the security of their systems cannot be resolved.6 Additionally, the professionals expressed that they felt that sometimes management listened more to contractors than the full-time employees and involved contractors in decision making while excluding FAA employees.7
___________________
5 Per https://dictionary.apa.org, a construct is a complex idea or concept formed from a synthesis of simpler ideas.
6 Focus group discussion with FAA employees and committee members, August 20, 2020. All discussions were conducted in confidentiality, and the names of the participants are withheld by mutual agreement. Focus group discussion with FAA managers and committee members, August 21, 2020.
7 Focus group discussion with FAA employees and committee members, August 20, 2020.
Appreciation
As reviewed above, several factors impact the retention of individuals in an organization. External and motivational factors are differentially important, depending on why an individual is considering leaving an organization (e.g., reluctant stayers/leavers). One motivational factor of increasing research importance is appreciation. Simply stated, individuals who feel appreciated are less likely to turn over than those to whom the organization does not convey the same information about the person’s worth to the organization and its goals. This importance is likely due to appreciation and recognition being considered innate human needs (Abdullah et al., 2016).
Research examining the role of appreciation at work and its importance to outcomes such as increased job satisfaction and decreased turnover is growing. For example, a longitudinal design covering six Swiss organizations found appreciation to be central in employees’ feelings of success in the organization, satisfaction with the job, and overall satisfaction with the organization (Pfister et al., 2020). Similarly, Abdulla and colleagues (2016) demonstrate appreciation (along with recognition) to be central in job satisfaction for Malaysian IT workers. Even in situations where a worker might believe a work task is unnecessary, unreasonable, or outside the scope of their responsibilities (termed illegitimate task in the research literature), an individual is more likely to complete the task if they feel appreciated. Muntz and Dormann (2020) demonstrate this in a longitudinal study of nurses. Their conclusions highlight that nurses who felt appreciated were less likely to perceive a task as illegitimate; it generally costs organizations little to create an environment of appreciation and it is “highly powerful” (p. 391).
But what is appreciation? At one level, appreciation is something we all know. A person can both feel appreciated and also rationally consider whether they are appreciated by an organization. Researchers such as Fagley (2012, 2016) and Fagley and Adler (2012) are more clearly defining the construct space of appreciation by arguing it has eight specific facets. Fagley (2016) defines these aspects as:
- “Have” focus: Focusing on, and valuing, what one has.
- Awe: Feeling awe or wonder in response to nature, beauty, or life itself.
- Ritual: Using routines or practices to foster noticing and valuing something (appreciation).
- Present Moment: Focusing on the present moment and valuing it.
- Self or Social Comparison: Using self or social comparisons to promote appreciation.
- Gratitude: Feeling grateful to a benefactor for help, support, or opportunities.
- Loss or Adversity: Appreciation (noticing and valuing something) triggered by experiences of loss or adversity.
- Interpersonal: Noticing and valuing the people in one’s life.
Identifying particular aspects of appreciation and the importance each plays in an individual’s work life offers opportunities for the FAA to foster a sense of appreciation in its cyber employees. For example, the FAA could communicate to individuals the “Haves” in their job (e.g., access to cutting-edge technology, tools, and training), or the “Awe” or “Social Comparison” aspects of being able to work for the premier aviation organization in the world. Of course any of the other aspects of appreciation could be utilized by the FAA as well. The outcome for the FAA of increasing perceptions of appreciation would include increased job satisfaction and less turnover among its cybersecurity workforce.
FAA RETENTION
Due to the shortage of qualified cybersecurity talent, unemployment rates for this workforce population are low to non-existent. Thus, recruitment remains a challenge. However, forward-thinking organizations, in the midst of a recruitment battle, have begun to use more systems-level approaches to both recruit and better retain cybersecurity talent. Without effective retention practices, recruitment becomes a revolving door, and cost management becomes an issue due to the need to continue to orient and train new talent. Retention is a challenge faced by the FAA cybersecurity workforce, and in the committee meetings the FAA personnel discussed several barriers to retention, including (FAA, 2020):
- A growing proportion of retirement eligible personnel;
- Fast-paced changes in cybersecurity threats and vulnerabilities that require employees to acquire new knowledge on a consistent basis;
- Competition with private industry, the Department of Defense, and intelligence agencies;
- Preferences of workers to go to contract positions due to salary limitations (the general schedule grades and steps) in FAA jobs;
- Noncompetitiveness of salaries; and
- Limited opportunities for advancement because of policies around time-in-rank.
Based on discussions with the sponsor and the committee, the turnover rate of FAA employees is lower than other agencies, but the rising need for cybersecurity talent, and more so, a diverse and talented workforce intensifies the need to focus on retention. Often, organizations separate recruitment efforts from retention efforts, yet a systems view reveals that they are highly interdependent and that it is important to integrate the two (Schweyer, 2004). Every recruitment initiative should be strongly integrated with retention initiatives, and prospective employees should be provided with retention incentives.
The committee’s literature review found that experts in the field of employee retention have grounded forward-thinking best practices for retention in three primary areas: (1) ensuring employees can build human capital in the workplace; (2) focusing on management practices and attitudes as leading indicators of employee intent to depart from an organization; and (3) advancing workplace culture to enhance the attractiveness of the organization for both recruitment and retention. Many of these scholars mention the need to increase workforce diversity simply due to the changing demographics of the United States. Likewise, there is a strong need to increase the heterogeneity of talent, skills, and knowledge to address complex problems, especially in cybersecurity. Thus, best practices provided here assume an integrated systems approach to recruitment and retention, as well as an authentic commitment to diversity and inclusion within the FAA.
Human Capital in the Workplace
Fundamentally, retention of employees rests on their perceptions of the likelihood of moving to higher and suitable positions within the workplace. This often involves human capital development, which is an expanding practice in organizations to attract and retain talented workers. Alnachef and Alhajjar (2015) define the practice as “helping people to acquire expertise” (p. 1154). Effective human capital development is grounded in a systematic, strategic plan to grow employees’ professional capabilities and to understand employees’ current needs and future aspirations within the organization (Alnachef and Alhajjar, 2015).
Human capital development has also been conceptualized as a social capital development process. Etti (2020) posits a human capital model to attract and retain women and ethnic minorities in the U.S. Federal Civil Service. The model is adapted from several scholars focusing on the role of social capital in organizations (Bourdieu, 1989; Coleman, 1988; Cross and Cummings, 2004; Granovetter, 1973). The model posits several interconnected factors necessary for organizations to assist employees in developing human capital. In this regard, the leader-member exchange between managers and employees can be strengthened and ultimately result in positive impacts on retention. The model has been adapted in Figure 4-1 to include more concepts specific to the FAA and cybersecurity.
Etti builds on work by Alnachef and Alhajjar (2015), who proposed an initial model to address many of the same human capital concepts depicted in Figure 4-1 (Etti, 2020). In their initial model, Alnachef and Alhajjar identified three actions any employer can build into the organizational culture to grow and retain strong talent: (1) provide employees with relevant opportunities for learning and education; (2) consistently support the development of experience and expertise; and (3) create and implement opportunities to grow employees’ innovation and creativity (p. 1156).
Naff (1994) highlighted the limited advancement of women in civil service positions. Lack of human capital due to formal education or experiential learning opportunities as well as limited participation in workplace networks serve as barriers to promotion and advancement. Additionally, women and underrepresented minorities are less likely to be assigned to key tasks and initiatives that grow experience and knowledge in emerging and
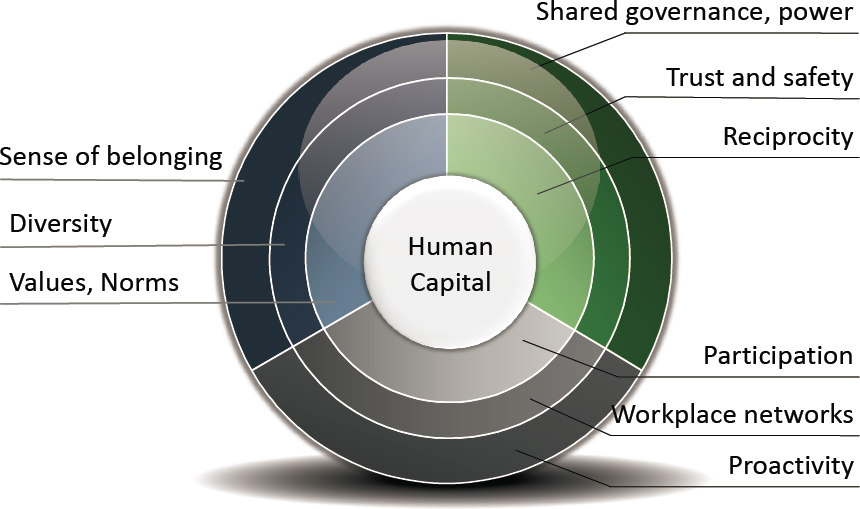
SOURCE: Committee adapted from Etti (2020).
competitive areas. Another challenge to retention and advancement is associated with unfair performance evaluations and lack of feedback.
These issues identified by Naff (1994) and others map to the Etti concepts of workplace networks, participation, proactivity, sense of belonging, and reciprocity. In the aforementioned retention barriers identified by the FAA, implementation of a human capital development process would be impactful. Particularly, if salary competition threatens retention, then proactive methods to create clear paths to advancement and higher salaries within the FAA would reduce this threat. Similarly, success at retention early in an employee’s FAA career could provide opportunities to grow and develop expertise in systems thinking around cybersecurity, such that an employee may be cross-trained to understand interdependencies across all relevant components. This form of joint optimization within human capital development advances the personal growth of the employee and their readiness and productivity within the organization, each of which lead to advancements consistent with organizational values.
Focusing on Management Practices and Attitudes as Leading Indicators of Employee Intent to Depart from an Organization
To be effective, human capital development must be led by management practices that support the advancement of employees. Part of leadership development for managers should involve an understanding of the urgency to recruit and retain strong cybersecurity talent. The FAA identified an increasing challenge of balancing permanent cybersecurity employees with contractors, many of whom are former FAA employees (FAA, 2020). It is prudent to connect the dots in this case. A contributor to effective human capital development is shared governance or a perceived sense of power in the workplace. Managers play a significant role in employee perceived power (Schrage et al., 2020). Thus, management styles must be continuously assessed and developed to determine the extent to which a management style is conducive to an effective human capital development strategy.
One indicator on management performance evaluations would be a demonstrated ability to be proactive and inclusive in identifying talent in the workplace that could benefit from high levels of human capital development. In meeting its own Goal 4 in the 2020–2025 FAA Cybersecurity Strategy, the agency’s employees and management are key to co-designing and implementing human capital development processes that build and maintain a competitive workforce (FAA, 2020). As mentioned, the objectives of Goal 4 included providing more cybersecurity training and experiential learning (exercises). In combination, achieving the objective of role-based training to help employees better understand their roles and how their roles fit within a larger structure was deemed important in the strategy (Goal 4 objective). Management’s ability to execute this objective is another performance indicator for strong leadership in human capital development. Great managers focus on making people better at what they do.
Another practice in the development of managers and other leaders in the FAA is the capability to recognize factors that may impact turnover rates. Many studies focus on the intention to turnover (or leave) an organization, but there are fewer studies focusing on actual turnover rates. A study by Cohen, Blake, and Goodman (2016) did apply a linear regression model to identify factors that correlated with actual turnover rates. They found that workload satisfaction was strongly correlated with actual turnover rates. Higher workload and perceived unfairness in workload distribution led to more dissatisfaction and turnover. Also, lower satisfaction with advancement opportunities in the organization led to higher turnover rates. When employees saw limited opportunities to move to higher positions, they were more likely to leave for better opportunities. Not surprisingly, pay satisfaction also correlated strongly with turnover rates. The fourth contributor was flexibility in work schedules, such that more set and rigid work schedules were associated with higher turnover rates.
Advancing Workplace Culture to Enhance Attractiveness of the Organization to Recruit and Retain Employees
Although the FAA has suggested that retention is not as great a challenge as recruitment, continued challenges with recruitment amidst an existing experienced workforce may be a leading indicator of an organizational culture that may not be evolving to the degree necessary to attract and retain younger workers (FAA, 2020). Additionally, the loss of employees to private industry and other government agencies might very well signal the need for examination of organizational culture at least as a negative contributor to retention.
Organizational culture defines the proper way to behave within the organization. This culture consists of shared beliefs and values established by leaders and then communicated and reinforced through various methods, ultimately shaping employee perceptions, behaviors, and understanding.8 Organizational culture is a key factor in the success of an organization as it can make or break any enterprise.
A study by Opengart and Ison (2016) focusing on personnel shortages in aviation collected factors from interviews of women in aviation, one of the most difficult populations to recruit and retain. Based on interviews, barriers were identified that relate to workplace practices. For example, a lack of open communication was a persistent annoyance for women in aviation, because women did not feel comfortable expressing needs that might be different from those assumed by the predominantly male leadership. This inability to openly communicate influenced decisions to leave aviation, regardless of talent, expertise, and passion for the job.
Opengart and Ison (2016) also found that fair distribution of work was another factor. Workload and fairness in workload distribution should be a value embedded in the organizational culture; one that values employees as the greatest resource. In the Opengart and Ison study, the perception of unequal distribution, either through overload or through which assignments were given to which aviation employees, was considered a contributor to dissatisfaction in the workplace. Other factors identified by women included a sense that the fight for equality in a male-dominated aviation culture was cognitively exhausting, leading to distractions in their ability to focus on critical tasks. Finally, self-efficacy was undermined by a workplace culture that valued men over women and stereotyped women as being less capable. These stereotypes may also have been reinforced through the exclusion of women in key networks and group activities. These practices, shaped by a specific organizational culture, undermine almost every concept identified in the Etti model for human capital. In essence, women who wanted higher
___________________
8 More information is available at: https://www.shrm.org/resourcesandtools/tools-and-samples/toolkits/pages/understandinganddevelopingorganizationalculture.aspx.
or better compensation, reported being blocked from building human capital in the aviation workplace, and, consequently, they made the decision to go elsewhere to pursue opportunities perceived to be more fair and lucrative.
As the Opengart and Ison (2016) study illustrates, retention is associated with organizational culture, and in particular, building an organization where employees perceive opportunities to develop human capital while also working within an organization that offers opportunity and flexibility. Newer generations with tendencies toward higher career mobility will not easily be retained without future-oriented best practices for retention. To avoid a revolving door and keep the best talent to meet increasingly complex and rapidly changing cybersecurity threats, a strong focus on organizational culture must be central to any organization’s priorities and strategic goals. But an intentional plan and process to facilitate retention also needs to be focused on cybersecurity positions in particular.
One way to focus the effort is to conduct a barrier analysis specific to the cybersecurity workforce. This barrier analysis, in the committee’s judgment should be comprehensive and should involve diverse employees, including early-career employees, women, different generations, and underrepresented minorities. There is a need to build a culture of cybersecurity across all facets of an organization. A better positioned workforce will be the first line of defense. The goal is to have workers do what you would have them do to protect systems on their own. By better training the staff on the threats and making it more competitive this will inspire some employees to pursue cyber careers. A “women in technology” program in collaboration with the Women in Technology organization9 can help demonstrate the value and importance an organization or agency is placing on recruiting and advancing women in cybersecurity.
TALENT PIPELINE DEVELOPMENT
Addressing the gap in the cybersecurity workforce requires programs that help employers identify the required skills and education programs that develop those skills at all levels of education (i.e., early, mid, and late career). There are several programs and initiatives specifically focused on developing the cybersecurity workforces at the general education, university, and professional levels. Some initiatives are designed to develop a talented cybersecurity workforce and attract them to work in government agencies (Piotrowski, 2020).
Some of these initiatives are designed to characterize cybersecurity knowledge, skills, and abilities to improve understanding of what is required in various cybersecurity roles. The National Initiative Cybersecurity Education (NICE) Framework was developed to provide a common frame of reference and common language to describe cybersecurity roles and the knowledge, skills, and abilities needed to perform work in those roles (Newhouse et al., 2017). Mapping existing and future job roles to knowledge, skills, and job tasks like those in the NICE Framework is a crucial step in establishing a cybersecurity workforce. It is important to understand what skills are required for each job role so that recruitment and training efforts ensure the required skills in the cybersecurity workforce, and using a common framework may help standardize within different lines of business within the FAA and across organizations. It is also important to recognize that lacking current knowledge and skills in the cyber realm need not be a barrier to pursuing training or a career in cyber, as having requisite aptitudes and traits (e.g., systems thinking, need for cognition) serve as a sufficient predictor for future competency in cyber occupations (Coovert, Wiernik, and Martin, 2019, 2020).
In the committee’s judgment, there may be resistance to investments in the talent pipeline because these investments are for the long term and do not fill current positions, may be viewed as a distraction, and may divert resources from other needs. However, such investments are in the national interest and in a governmental organizations’ long-term interests.
Early Training Talent Pipeline Development
There has been focus in recent years on developing skills and interest in cybersecurity at the K–12 level. For example, the United States Department of Homeland Security (DHS) Cybersecurity Education Training Assistance Program (CETAP) and the Air Force Association’s CyberPatriot National Youth Cyber Education Program are
___________________
9 More information is available at: https://www.womenintechnology.org.
intended to give K–12 teachers cybersecurity education tools to develop an awareness of cybersecurity issues and career fields.10 Government agencies may help ensure the long-term workforce needs are met by actively supporting and visibly participating in these programs. There are increasing efforts and studies aimed at high school students to attract future talent and increase the perceived value of cyber science (Turner et al., 2014).
The largest high school cyber defense competition is the Air Force Association’s CyberPatriot competition program.11 This program was created to inspire K–12 students toward cybersecurity or STEM careers and gives teams the task of managing a network for a small company. The competition is at the core of the program and involves middle and high school students.
Another organization making high-quality computer science an integral part of the K–12 educational experience is CSforALL.12 The CSforALL initiative connects providers, schools, funders, and researchers to equip students with computational thinking skills.
Other programs for younger elementary (K–6) school children include the Air Force Association’s CyberCamps, which teach the basics of cybersecurity, and the Cyber Education Literature series for early elementary students.13 Other organizations have also implemented programs aimed at younger children, such as the Girl Scouts of USA’s Cyber Challenge. In 2019, a national computer science program was sponsored by Raytheon to help close the gender gap in STEM fields by preparing girls to pursue careers in fields such as cybersecurity, computer science, artificial intelligence, and robotics. Finally, universities are beginning to develop programs to engage students beginning in grade school. At the University of South Florida for example, there are special coding camps targeted at several specific grade groups, including Grades 3–5 “Elementary CyberCamp”; grades 4–6 “Everyone Can Code Camp”; grades 6–8 “Middle School CyberCamp”; and grades 9–12 “High School CyberCamp.”14
Finding 4-2: Continuing through college, groups such as the National Collegiate Cyber Defense Competition bring together highly skilled individuals about to enter the cyber workforce. Groups and activities such as these provide opportunities for an organization to contact and recruit developing cyber talent.
College-Level Talent Pipeline Development
Programs directed at training university students and recruiting them to government agencies have been successful in providing high-quality graduates of programs to federal agencies. The Scholarship for Service (SFS) program15 is the most well-known of the internship programs for cybersecurity. SFS students receive fellowships in exchange for 2 years of service in a federal agency. As discussed in Chapter 3, the majority of employees hired through the SFS program stay in the position beyond the required service time. Because there are a limited number of SFS graduates, and graduates can choose which government agency in which to serve their required time, competition for these graduates is keen. To take full advantage of the SFS program, employers need to actively recruit SFS graduates and ensure their workplace is perceived as desirable.
The National Security Agency (NSA) and the DHS sponsor the National Centers of Academic Excellence in Cyber Defense Education (CAE-CDE) program.16 This program aims to decrease vulnerability in the nation’s infrastructure through cyber defense education and research. The program includes the CAE-CDE program for Associate, Bachelor, Masters, and Doctoral programs; and the Centers of Academic Excellence in Cyber Research (CAE-R). The CAE-CDE is a “national quality standard for certifying and maintaining high quality of cybersecurity education with rigorous and consistent requirements for program evaluation and close alignment to specific
___________________
10 More information is available at: https://niccs.us-cert.gov/formal-education/integrating-cybersecurity-classroom.
11 More information about the Air Force Association’s CyberPatriot program is available at: https://www.uscyberpatriot.org/.
12 More information about CSforALL is available at: https://www.csforall.org/.
13 More information is available at: https://www.uscyberpatriot.org/afa-cybercamps/getting-started/afa-cybercamp-overview and https://www.uscyberpatriot.org/Pages/Special%20Initiatives/CELS-Overview.aspx
14 More information is available at: https://www.usf.edu/education/about-us/summer-programs.aspx.
15 More information is available at: https://www.sfs.opm.gov/.
16 More information about the history and management of the CAE-CDE is available at: https://www.nsa.gov/resources/students-educators/centers-academic-excellence/.
cybersecurity knowledge units” (Dawson et al., 2018, p. 127). Dawson and colleagues note that “[o]ut of over 5300 colleges and universities in the U.S., only about 200 of them have achieved the CAE-CDE designation status” (p. 127).
Currently, education for cybersecurity is available at 2- and 4-year academic institutions, with varying courses, programs, and degrees. These may be focused on cybersecurity, computer science and engineering, management information systems, and other information technology-related areas (NRC, 2013). Cybersecurity education is also available as part of other fields of study such as business.
There is a current push for universities to establish centers to advance cybersecurity education and workforce development programs, such as the Virginia Tech program to help Amazon’s new headquarters staffing.17 Their roles vary, including curriculum development, co-curricular initiatives, building of the K–12 pipeline, and so forth. Another example is the Center for Infrastructure Assurance and Security (CIAS) at The University of Texas at San Antonio, which created the Collegiate Cyber Defense Competition (CCDC)18 along with several other competition programs. CCDC is similar to other competitions in many ways; however, it is the only one that focuses on managing and protecting an existing network infrastructure. The competition, especially the top performers, routinely attracts recruiters for hiring.
Diversity Through College-Level Talent Pipeline Development
One path to increasing the talent pool available to a cyber workforce would be to emphasize the recruitment of minorities and women, groups that have traditionally been overlooked in this field (Burrell, 2018). As discussed above, programs in higher education can be an effective component of an organization’s recruitment and selection strategy; this includes efforts to increase the diversity of the cyber workforce. As recently pointed out (NASEM, 2019), a great pool of potential STEM talent can be found at the more than 700 minority-serving institutions (MSIs) across the United States.
Finding 4-3: Institutional partnerships with MSIs can both expand the talent pool for high-demand positions and ensure diversity in the workforce for the long term.
Student-Level Talent Pipeline Development
Beyond institution-level initiatives to promote cybersecurity, interventions with individual students can also bolster the cybersecurity talent pipeline. Scholarship programs, such as those administered through the Center for Cyber Safety and Education (Center), formerly (ISC)2 Foundation, provide scholarship opportunities for undergraduate, graduate, minorities, women, and Veterans.19 The 2020 KnowBe4 Scholarship for Black Americans in Cybersecurity is a $10,000 scholarship that can be used for tuition, fees, books, electronics, and housing, while the 2020 (ISC)2 Women’s Scholarship provides $1,000 to $6,000 to individual women pursuing or planning to pursue a degree in the field of cybersecurity or information assurance.
FAA TALENT PIPELINE DEVELOPMENT
There are well-established models for MSI student internships at other federal agencies that the FAA might consider adopting or adapting. The National Geospatial-Intelligence Agency and NSA are good examples. In the committee’s judgment, the most effective internship programs are centered around the student experience, such as supporting mentorship and other engagement with students throughout the academic year.
A spectrum of opportunities for broader engagement exists that runs from informal interactions with faculty to support for campus visits by FAA employees, and providing support for scholars-in-residence. Such activi-
___________________
17 More information is available at: https://vt.edu/innovationcampus/News/2019/June/innovation-campus-location.html.
18 More information on competition details is available at: https://www.nationalccdc.org/.
19 More information about all the scholarship opportunities is available at: https://iamcybersafe.org/s/scholarships.
ties would represent a change in practice and culture from what the committee understands to be the norm in cybersecurity at the FAA. The FAA does this in other areas of the organization, and both NSA and CIA support scholars-in-residence programs at MSIs for this purpose. FAA technical staff and managers can both proactively reach out to faculty and use research with universities as an opportunity to develop relationships with faculty who will create talent pipelines.
There may be a need to create new programs to meet unique or specific FAA cyber workforce needs. For example, there may not currently be education and training programs targeted at detailed government technical oversight of industry technical programs (i.e., aircraft manufacturers).
To formalize a human-centric cyber-education curriculum, Caulkins and colleagues (2016) analyzed the NICE, the National Cybersecurity Workforce Framework, and the DHS National Initiative for Cybersecurity Careers and Studies (NICCS) educational framework. After a gap-analysis, the human-centric educational training curriculum was developed and implemented in a pilot educational program at a large university. Important elements of this work include the integration of three overarching frameworks, a gap analysis, and the focus on human-centric training for behavioral cybersecurity.
How might we conceptualize training for a cybersecurity workforce? And how might these be applied to the FAA’s situation in particular? One proposed model is to utilize a framework associated with military strategy (Church, 2016). There are several flavors proposed, but the author argues that we can leverage what we do well in the military and apply it as a framework for dealing with cyber issues. Another strategy often advocated is that the focus of cyber awareness training should be to try to “get into the attacker’s head.” Many training programs to thwart attackers focus only on the explicit—that which is observable. Martiny and colleagues (2015) believe a more successful approach would be to try and understand the belief states and goals of the attacker. This argues for training a cognitive understanding of the attacker.
Training
Training is an essential part of a cyber aware workforce. Key elements include training regarding social engineering and that the fact any part of the cyber-physical system can be attacked. Developments in the training area include the fact that individuals with different personality factors are more or less likely to succumb to threats of social engineering (Cusack and Adedokun, 2018; SEI, 2014). Cloud-based training has developed the capability of providing training at both the worksite and off worksite of the employee. Additionally, developments of training strategies employing serious games, gamification, and digital sandboxes of different types are increasing the capability to provide realistic training under realistic conditions for a variety of cyber-related occupations.
Formal training methods are employed by the FAA where individuals are sent to universities for specialized cyber training for short periods.20 Other less formal training approaches include peer mentoring (Janeja et al., 2016) and peer influence (Li et al., 2016b) to improve cybersecurity behavior in organizations. Zafar (2016) advocates for the use of behavioral training, having found correlations between habit creation and security threats (e.g., password sharing, phishing, unauthorized cloud computing).
Below are three examples of what the committee means by personnel practices that could support professional development and motivate the cyber workforce. These are not intended as mandates, but illustrations of policies and procedures that likely would benefit the FAA.
- Allow time away and expensing of registration fees for security workshops.
- Strategically and fairly use temporary duty assignments to other agencies or FFRDCs so that staff can assess and import security practices that have proven to work well elsewhere.
- Make broader use of, and publicize internally, short-term “red teams” that allow security-minded technical staff, even those without NICE security job titles, to research new attack techniques on FAA systems,
___________________
20 Focus group discussion with FAA employees and committee members, August 20, 2020. All discussions were conducted in confidentiality, and the names of the participants are withheld by mutual agreement. Focus group discussion with FAA managers and committee members, August 21, 2020.
whether in Atlantic City test facilities or elsewhere. Perhaps more important than the budget outlay is the management skill in creating “blameless post-mortems” (i.e., after action reviews of lessons learned) that widely spread the knowledge gained through the FAA without creating embarrassment or hard feelings.
Skill Development and Training Through Certification
Along with formalized academic training, certification programs can be used to complement and expand cybersecurity knowledge, skills, and abilities. Organizations providing certifications have the advantage of frequently updating information and competencies while also being more responsive to emerging threats in the cybersecurity landscape (Knapp et al., 2017). Other programs such as the U.S. Cyber Challenge (USCC) have identified strategies to train and assess students to fulfill cybersecurity roles.
Workplace Flexibility
Workplace flexibility is a powerful tool to apply in retention as well as recruiting (as discussed in Chapter 3). Changes in telecommuting perspectives related to the COVID-19 pandemic are becoming increasingly cited as an important issue for employees. Work-life balance is an important factor for many younger employees and is increasingly important for all employees (Singh, 2019). Flexible work schedules and flexibility in work location may be a way to bring talent to less desirable locations. Organizations having difficulty retraining or keeping employees because of the work locations should consider allowing telecommuting for job roles that do not require employees to be on site.
RETIREMENT
As discussed in Chapter 2 of this report, the FAA has an experienced workforce with many employees getting closer to retirement-eligible age or having accumulated the years necessary to retire from the organization. For years, experts have been predicting a wave of retirements in the federal government, and urging federal agencies to prepare for the inevitable “tsunami” of retirement-eligible employees leaving the workforce (Lewis and Cho, 2011). This anticipated shift has prompted focus on how to recruit and retain the numbers needed to maintain the workforce and how to capture knowledge from these highly skilled employees. In its interviews, the committee heard about employees staying on past their retirement because they enjoy the mission and experience a sense of fulfillment working in their current positions, but this is not a long-term or comprehensive solution. It is critical that an organization develop strategies to ensure that specialized knowledge related to its mission and operation is captured and transferred effectively to new employees. One strategy would be to establish a list of critical positions within the cybersecurity workforce and track the succession plans for each position on a regular basis.
Such a large wave of retirements also presents any organization with an opportunity to identify shifts in the needed skills and knowledge and recruit employees to fill gaps. The fast pace of changes in cybersecurity affects the skills and knowledge needed to effectively perform cybersecurity, which means that job functions may change equally rapidly (Vasileiou and Furnell, 2019). On-the-job training and reskilling can support the development of these skills but in limited ways, and some job functions may require recruiting new individuals with unique skillsets and experiences (Burrell, 2018). Taking advantage of openings due to retirements may allow the opportunity to evaluate emergent needs and refresh the workforce with those new skills (Dawson and Thomson, 2018). As workers retire, it is important for managers and recruiters to avoid replicating the position description of the outgoing employee and rushing to hire workers with identical skillsets. Instead, they might take the time to look at where the cybersecurity workforce is moving and recast the position for the future, critically evaluating what new skills might be required. Though this takes additional time, it is likely well worth the effort to thoroughly understand present organizational needs, project future needs, and how to further the diversity of skills through a conceptualization of these positions. This may be an effective strategy particularly for agencies that tend to have low turnover and fewer open cybersecurity positions, such as the FAA.
CYBERSECURITY ORGANIZATIONAL STRUCTURE AND DESIGN
Organizational design is a strategic management approach that considers people, system complexity, and organizational aspirations. Other factors such as emerging behaviors and needs, core business priorities, geopolitical requirements, and the external environment are also considered (Auernhammer and Leifer, 2019; Hendrick, 2009). Part of any business strategy that impacts organizational design relates to the use of assets and tools to advance the goals of the organization (Moşteanu, 2020). Tagarev (2020) has identified important considerations for organizational design in collaborative cybersecurity organizations; these include a governance structure within the overall organization design with a focus on trust, security risk, knowledge sharing, and inter-operability. While there are numerous models for structuring an organization, including hierarchical, matrixed, and functional structures and others, the distributed nature and breadth of missions at the FAA has resulted in an organization that incorporates aspects of each of these.
The FAA cybersecurity workforce alignment presently supports two functional areas, the enterprise role and the mission systems. The enterprise role includes support of the internal infrastructure and processes, cyber operations, security awareness training and application, and network enterprise services. Mission functions encompass the air traffic systems, unmanned systems, other platforms, and system of systems to support the FAA missions. The mission-facing cybersecurity workforce performs acquisition duties as well as design, testing, and oversight for specific programs. In the committee’s judgment, organizations benefit from including organizational design as a part of continuous improvement to ensure that the structure and processes are optimized to align the workforce with the mission.
In the committee’s judgment, organizational design is not simply an effort to assert functional and cross-functional capabilities, but also a means of communicating the values of an organization and its outward-facing commitment to the mission (it should be noted this could be tied to how the FAA markets itself). Training and communication are important aspects of the human-centered approach and are enabled by both organizational structure and culture. These aspects of organizational design have become an industry best practice, as discussed in relation to the United Postal Service (UPS) (Perez, 2020) and summarized in McKinsey & Company research (Lewis, 2020).
Further information-gathering briefings during this study provided more information relevant to organizational design and the success of the FAA cybersecurity workforce initiative. According to Juan Perez, UPS Chief Information and Engineering Officer, organizational design should establish a solid network with the appropriate technologies, the right people, the right attitude, and the appropriate planning to be able to manage events (Perez, 2020). The right people and leadership have to be in place to protect the privacy and security of a company’s information (Perez, 2020). Additionally, the design of a cybersecurity organization should also be a reflection of the cybersecurity risk management governance model that the organization wants to have in place.
From Perez’s perspective, UPS Chief Information Officers (CIOs) and Chief Information Security Officers (CISOs) must have six capabilities concerning cybersecurity:
- Know the company;
- Know the customer;
- Understand security and information breaches;
- Prioritize what is most critical and important to protect;
- Establish a well-defined response mechanism to any potential incident; and
- Apply these capabilities consistently.
According to Perez, cybersecurity requires collective efforts. Similar to Hendrick (2009), Perez observed that the complexity of the system will influence the effectiveness of organizational design and the capabilities of those assigned in leadership roles in specific organizational units. In the committee’s judgement, simplifying the complexity of the system through technology, automation, and better processes and controls is critical.
The FAA cybersecurity workforce efforts will benefit from best practices, such as those forged by UPS and similar organizations, which include a people-centric perspective on the workforce. UPS focuses on socializing employees to facilitate a security-minded enterprise, and this socialization is done through teaching, training, standardizing risk management, and communicating to foster a security culture and individual awareness (Perez,
2020). Agility is a critical benefit of this people-centric perspective. Based on organizational theory, too much centralization may restrict the agility of an organization, especially those that rely on knowledge-based roles (as opposed to routinized or skill-based roles) (Hendrick, 2009; Moşteanu, 2020).
Charlie Lewis, Expert Associate Partner at McKinsey & Company, provided information on organizational design from the perspective of strategic management. Trends in how organizations are changing include challenges with organizational leadership, talent acquisition and retention, risk-based investment, business enablement, cyber hygiene, and regulatory compliance. According to Lewis, when thinking about how an organization should be structured, organizational leadership needs to be empowered to influence the business. CISO units should not be perceived as a wall or impediment. They should be seen as innovation enablers.
It is important for cybersecurity in any organization to fit within the structure and the operating model of the broader business and to be a part of the broader business or the broader organization in a way that allows it to support the achievement of the business strategic goals and understand what to secure, why to secure, and where their focus should be in both how they operate to support delivering value and determining the competencies needed (Lewis, 2020). Additionally, the processes, integration, and linkages required with existing governance structures need to be considered across the entire business. Finally, in thinking about how to structure the organization, Lewis suggested bringing in new people, and take the processes and the operating models decided upon to structure the organization as a whole (Lewis, 2020).
Lewis explained that when looking at the operating model as a cyber-specific operating model, there are key design choices to consider. These design choices include the service catalog (what are the services provided and where do they go), risk ownership (clarifying the division of stakeholders who are accountable, responsible, consulted, and/or informed in the cyber risk management process), and lines of defense (as they pertain to cybersecurity and risk are discussed in more detail below). In his presentation, Lewis outlined three lines of defense for cybersecurity:
- The first line typically includes the IS department and business units.
- The second line of defense is composed of risk managers looking at aggregate risks at an enterprise level.
- The third line evaluates the overall process of cyber risk governance.21
For the most part, these are fairly standard operating model design considerations that would be applied. Cybersecurity should be no different from any other part of the organization. It just serves a different, newer function. Close coordination across these three independent lines of defense is enabled by five foundational elements that are the keys to success: (1) lifecycle understanding of controls; (2) strong process definition; (3) clear definition of roles and responsibilities; (4) talent distribution; and (5) enterprise-wide agreement between roles and responsibilities (Lewis, 2020). The key takeaway is that there should be close coordination across these independent lines. They may be independent, but they need to work together.
Peter Cooper, CEO of Pavisade, discussed cybersecurity challenges in the aviation workforce. Leadership coordination, accountability, and expertise in aerospace safety are fairly well understood throughout the entire organization in aerospace, all the way up to the CEO (Cooper, 2020). For example, there are dedicated flight safety chains and a well-established culture of flight safety. But for aviation and aerospace cybersecurity, the challenge is finding the balance between leadership, coordination, accountability, and expertise.
Cooper noted it is critical to understand workforce push and pull factors to attract, develop, and retain a cybersecurity workforce. The future workforce will need to:
“develop new regulations; understand complex cyber/physical systems at the edge of innovation; understand complex failure modes and resiliency; have the confidence to question and challenge; have the ability to objectively test/audit and demonstrate; and to make and communicate, objective, evidential, risk-based decisions; and defend those decisions” (Cooper, 2020).
___________________
21 More information is available at: https://securityintelligence.com/take-a-load-off-delegate-cyber-risk-management-using-the-three-linesof-defense-model/.
The CISO as a Senior Executive
Given the critical nature of cybersecurity to the FAA’s mission, the reporting lines for the CISO need to respect the role as senior within the organization. Every operational and technology decision carries risks to the cyber enterprise and can impact FAA operations and thus impact flight safety. In the committee’s judgement, to manage the risk appropriately, the CISO must be included, irrespective of human resource reporting structures.
To better illustrate the degree to which the significance of the CISO role has been elevated in the private sector, the committee points to the National Association of Corporate Directors (NACD) and Internet Security Alliance, who made clear “directors need to understand and approach cybersecurity as a strategic, enterprise risk—not just as an IT risk” (Clinton et al., 2020, p. 12). As a result, the NACD suggests that Boards of Directors build a personal relationship with their CISOs. From the discussions with various presenters the committee found that the most effective CISOs operate at multiple levels and believe it is important for the FAA’s CISO to be able to develop a comprehensive cybersecurity strategy that crosses multiple complex domains.
Given the highly complex nature of the FAA and the potential for life-threatening cyber events, the FAA needs to build plans around recruitment, development, and retention of highly skilled, knowledgeable, and innovative CISOs.
Finding 4-4: The FAA cybersecurity employees and the cybersecurity program as a whole will benefit from a CISO that can develop a comprehensive cybersecurity strategy that crosses multiple complex domains in the FAA.
CISO Independence
In the committee’s judgment, it is critical that the CISO have a high degree of independence in order to challenge failures to execute key security controls. The most common historical failures have resulted from CISOs reporting to CIOs. This often creates conflicts of interest in areas such as vulnerability and patch management, technology choices, and outsourcing decisions. The emerging best practice in many private-sector organizations that have had CISOs reporting to CIOs has been to elevate the role to become a peer of the CIO. In some cases, this also involves expanding the typical scope of the CISO to include other risk disciplines, most frequently business continuity and technology resilience. In the private sector, another best practice is to allow the CISO to have direct access to the Board of Directors.
Three Lines of Defense
In the financial services industry, an emerging best practice in cyberecurity risk management is the idea of multiple lines of defense. These are:
- The business and the IS operational teams that own the risks and execute the security program;
- An independent function to challenge the appropriateness of risk management decisions; and
- An audit or control validation function.
The three-lines-of-defense model originated in banking and was focused on credit risk, market risk, and counter-party risk. In the early 2010s, banking regulators began to extend the concept to operational risk, most visibly cybersecurity risk. In 2013, the Institute of Internal Auditors published a position paper, “The Three Lines of Defense in Effective Risk Management and Control,” that introduced and extended the best practice outside of banking to other large enterprises (IIA, 2013).
In an organization, the CISO is the functional leader for the first line of defense, and the Inspector General is the functional leader for the third line of defense. There is no leader of the second line today. The role of the second line is not to create a second audit organization. While auditors need to be focused on the controls and whether or not they are being operated effectively, the new second line is not “controls” focused. The second line’s role is at a higher level and includes examining the risk management decisions being made and,
when necessary, questioning whether those decisions will force the organization to operate outside of its risk tolerances.
Hybrid/Federate First Line CISO Teams
Based on private-sector best practices, neither a fully centralized nor a fully decentralized model for a first-line cybersecurity program can be effective in a large complex organization. To best deliver on the mission, the cybersecurity organization itself is ideally, in the committee’s judgement, a hybrid organization composed of two basic types of teams: (1) a cybersecurity organization-wide team and (2) a vertically integrated specialized team.
Ideally, one core set of teams would support the entire FAA in a shared and horizontally integrated fashion. These teams would directly report to the FAA’s CISO, and their budgets, in the committee’s judgement, should be centrally managed. These teams would focus on governance functions as well as the development and operations of critical capabilities that need to operate across the enterprise to be operationally and economically effective.
These core teams would be augmented by a set of highly specialized teams that are vertically integrated with the different units they support within the FAA ecosystem even as they remain connected to the core. These teams could be matrix managed by both the CISO as well as the lead role of the group with which they are aligned. The budget for these groups should be managed by the CISO as agreed with the relevant department heads.
The key first line horizontal functions are:22
- Strategy and governance
- Policy writing
- Cyber tech strategy
- Risk measurement and reporting
- Risk identification/risk acceptance or policy exception management
- Information security operations
- Identity and access management
- Vulnerability and threat management inclusive of red team
- Data protection
- Supply-chain IS risk management
- Cybersecurity operations
- Security operations center
- Threat hunting
- Incident response
- Cyber threat intelligence
- Cybersecurity fusion center
- Core security technology engineering and architecture standards
- Network, data center, cloud, and end point security engineering
- Application security architecture and engineering
- Cyber innovation
As the first-line security engineering and operations teams are built, another private-sector best practice should be, in the committee’s judgment, overlaid on the previous model; this is the idea of organizing around the concept of Plan, Build, and Operate (PBO). Under the PBO rubric, one function would excel at strategy, one at engineering, and one at execution, with all tied together through the shared services delivery goal.
Examples of vertical/local functions are:
- FAA Internal Applications Security Specialists;
- FAA External Applications Security Specialists;
___________________
22 This is meant to be an illustration of one such model; many variations will exist.
- FAA External Airframe Security Specialists; and
- FAA Airport Security Specialists.
Concluding Thoughts on Organizational Structure and Design
In the above sections, best practices associated with organizational design have been enumerated along with examples. Given the changing demographics of the United States, best practices, in the committee’s judgement, would ideally align with future cybersecurity needs and would include the populations that have not been equitably considered as contributors of their talent, skills, and knowledge to the FAA. Intentional efforts to apply these workforce best practices are integral to recruiting, developing, and retaining a robust cybersecurity workforce.
SUMMARY
This chapter has examined how the FAA should retain the talent needed for a diverse cybersecurity organization. Using the ELC model as guidance, the committee has made findings and recommendations in the areas of retention, development and advancement, and retirement. At every point, the committee has also considered issues of diversity. With these as a path forward, the committee believes that the FAA will be able to over time become a high-performing and diverse cybersecurity organization.
Conclusions and Recommendations
Difficulty competing with commercial entities that have higher compensation packages is one of the current challenges faced by the FAA in building its cybersecurity workforce. While one of the biggest benefits of working in the private sector is the higher salary potential, organizational reputation and positioning are critical components of recruitment and talent attraction efforts. The FAA relies on its staff to be mission focused and supports their cybersecurity workforce to complete their tasks.
As described in Chapter 3, managing an employee’s success and thus the organization’s success, takes place across multiple stages: attraction, recruitment and hiring (onboarding), development, advancement, retention, and retirement (separation). These are critical components that the FAA can and should pursue as indicated in the recommendations below.
CONCLUSION 4-1: It is critical that the Federal Aviation Administration develop strategies to ensure that specialized knowledge related to the FAA mission and operation is captured and transferred effectively to new employees.
RECOMMENDATION 4-1: The Federal Aviation Administration should monitor, and revise if necessary, its personnel practices to support the development of the necessary skills to meet the ever-changing demand in the current and future cybersecurity workforce.
RECOMMENDATION 4-2: The Federal Aviation Administration should provide professional development opportunities to refresh skill sets of current cybersecurity employees and ensure sharing of key institutional and mission-specific knowledge with newer cybersecurity staff.
RECOMMENDATION 4-3: The Federal Aviation Administration (FAA) cybersecurity employees and the cybersecurity program as a whole will benefit from a Chief Information Security Officer (CISO) that can develop a comprehensive cybersecurity strategy that crosses multiple complex domains in the FAA. The CISO’s reporting structure needs to support a strong governance model, which ensures that the CISO has both the independence and the access required to effectively manage the FAA’s cyber risk posture. In support of such leadership responsibility, the FAA should position the CISO role at the most senior level of the non-political appointees within the organization. Given the scarcity of qualified
people, the FAA should consider variances from current pay-scale limitations in order to be a competitive employer.
RECOMMENDATION 4-4: Employee retirement, at the end of the lifecycle model, offers organizations the opportunity to rethink organizational needs and required skill sets, which in turn helps refocus talent recruitment and the next iteration of the employee lifecycle. The Federal Aviation Administration should ensure that all efforts to upskill and evolve the cyber workforce include the agency’s risk management, cybersecurity compliance, and independent assurance capabilities.
RECOMMENDATION 4-5: The Federal Aviation Administration should enable the success of the cybersecurity program and the Chief Information Security Officer by designing a hybrid organizational model leveraging private-sector best practices such as blending core and edge (vertically integrated) functions as well as the plan, build, operate model.
REFERENCES
Abdullah, N., Shonubi, O.A., Hashim, R., and Hamid, N. 2016. Recognition and appreciation and its psychological effect on job satisfaction and performance in a Malaysia IT company: systematic review. IOSR Journal of Humanities and Social Science, 21(9), 47–55.
Allen, D.G., Bryant, P.C., and Vardaman, J.M. 2010. Retaining talent: Replacing misconceptions with evidence-based strategies. Academy of Management Perspectives, 48–64.
Alnachef, T., and Alhajjar, A. 2015. Effect of human capital on organizational performance: A literature review. International Journal of Science and Research, 6, 1154–1158.
Auernhammer, J.M.K., and Leifer, L. 2019. Is Organizational Design a Human-Centered Design Practice? Proceedings of the 22nd International Conference on Engineering Design (ICED19), Delft, The Netherlands. doi: 10.1017/dsi.2019.126.
Borman, W.C., Hanson, M.A., and Hedge, J.W. 1997. Personnel selection. Annual Review of Psychology, 48(1), 299–337.
Bourdieu, P. 1989. Social space and symbolic power. Sociological Theory, 7, 14–15.
Burrell, D.N. 2018. An exploration of the cybersecurity workforce shortage. International Journal of Hyperconnectivity and the Internet of Things, 2(1), 29–41. doi: 10.4018/IJHIoT.2018010103.
Caulkins, B.D., Badillo-Urquiola, K., Bockelman, P., and Leis, R. 2016. Cyber Workforce Development Using a Behavioral Cybersecurity Paradigm. 2016 International Conference on Cyber Conflict (CyCon U.S.), Washington, DC, pp. 1–6, doi: 10.1109/CYCONUS.2016.7836614.
Church, A. 2016. Military Strategy as a Guide for Cybersecurity. Proceedings of the 15th European Conference on Cyber Warfare and Security (ECCWS 2016), Munich, Germany, p. 58.
Clinton, L., Higgins, J., and van der Oord, F. 2020. Cyber-Risk Oversight 2020: Key Principles and Practical Guidance for Corporate Boards. National Association of Corporate Directors and the Internet Security Alliance. Available: https://www.casede.org/index.php/biblioteca-casede-2-0/seguridad/ciberseguridad/537-cyber-risk-oversight-2020/file.
Cohen, G., Blake, R., and Goodman, D. 2016. Does turnover intention matter? Evaluating the usefulness of turnover intention rate as a predictor of actual turnover rate. Review of Public Personnel Administration, 36, 240–263.
Coleman, J.S. 1988. Social capital in the creation of human capital. American Journal of Sociology, 94, 95–120.
Cooper, P. 2020. “Cybersecurity Challenges in Aviation – Workforce.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. April 22, 2020. Virtual meeting.
Coovert, M.D., Wiernik, B., and Martin, J. 2019. Use of Technology-Enhanced Simulations for Cyber Aptitude Assessment. Technical Report. Plant City, FL: MDC & Associates.
Coovert, M.D., Wiernik, B., and Martin, J. 2020. Use of Technology-Enhanced Simulations for Cyber Aptitude Assessment: Phase II Prototype Development. Technical Report, Accession Number: AD1107016. Fort Belvoir, VA: Defense Technical Information Center.
Cross, R. and Cummings, J.N. 2004. Ties and network correlates of individual performance in knowledge-intensive work. Academy of Management Journal, 47, 928–937.
Cusack, B., and Adedokun, K. 2018. The impact of personality traits on user’s susceptibility to social engineering attacks. In proceedings of the 16th Australian Information Security Management Conference (pp. 83-89). Perth, Australia: Edith Cowan University. Available: https://ro.ecu.edu.au/ism/228.
Cynet. 2020. 2020 Cybersecurity Salary Survey Results. Available: https://go.cynet.com/hubfs/2020-Salary-Survey-Report.pdf.
Dawson, J., and Thomson, R. 2018. The future cybersecurity workforce: Going beyond technical skills for successful cyber performance. Frontiers in Psychology, 9, 744. doi: 10.3389/fpsyg.2018.00744.
Dawson M., Wang P., and Williams, K. 2018. The Role of CAE-CDE in Cybersecurity Education for Workforce Development. Pp. 127–132 in Information Technology—New Generations. Part of Advances in Intelligent Systems and Computing, vol. 738 (S. Latifi, ed.). Cham, Switzerland: Springer. doi: 10.1007/978-3-319-77028-4_20.
Embry, J. 2020. “U.S. Coast Guard.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. June 29, 2020. Virtual meeting.
Etti, W.H.M. 2020. A case study of women and ethnic minority manager leadership advancement in general schedule 13-15 pay scale within the U.S. Federal Civil Services. Dissertation: University of Maryland – Eastern Shore. Proquest: 28002115.
FAA (Federal Aviation Administration). 2020. “The FAA Cybersecurity Workforce Overview.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration by FAA Cybersecurity Steering Committee (CSC) and FAA AHR Representatives. February 19, 2020. Washington, DC.
Fagley, N S. 2016. The Construct of Appreciation: It is So Much More Than Gratitude. Pp. 70–84 in Perspectives on Gratitude: An Interdisciplinary Approach (D. Carr, ed.). New York: Routledge.
Fagley, N.S. 2012. Appreciation uniquely predicts life satisfaction above demographics, the Big 5 personality factors, and gratitude. Personality and individual Differences, 53(1), 59–63.
Fagley, N.S., and Adler, M.G. 2012. Appreciation: A spiritual path to finding value and meaning in the workplace. Journal of Management, Spirituality & Religion, 9(2), 167–187.
Granovetter, M.S. 1973. The strength of weak ties. American Journal of Sociology, 78, 1360–1380.
Greenfield, G. 2020. “Building an Evidence-Based Diversity and Inclusion Strategy.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. June 29, 2020.Virtual meeting.
Hendrick, H.W. 2009. A Sociotechnical Systems Model of Organizational Complexity and Design and Its Relation to Employee Cognitive Complexity. In Proceedings of the Human Factors and Ergonomics Society 53rd Annual Meeting, San Antonio, TX, pp. 1028–1032.
Hom, P.W., Caranikas-Walker, F., Prussia, G.E., and Griffeth, R.W. 1992. A meta-analytical structural equations analysis of a model of employee turnover. Journal of Applied Psychology, 77(6), 890.
IIA (Institute of Internal Auditors). 2013. IIA Position Paper: The Three Lines of Defense in Effective Risk Management and Control. Available: https://na.theiia.org/standards-guidance/Public%20Documents/PP%20The%20Three%20Lines%20of%20Defense%20in%20Effective%20Risk%20Management%20and%20Control.pdf.
Janeja, V.P., Seaman, C., Kephart, K., Gangopadhyay, A., and Everhart, A. 2016. Cybersecurity Workforce Development: A Peer Mentoring Approach. 2016 IEEE Conference on Intelligence and Security Informatics (ISI), pp. 267–272, doi: 10.1109/ISI.2016.7745487.
Knapp, K.J., Maurer, C., and Planchkinova, M. 2017. Maintaining a cybersecurity curriculum: Professional certifications as valuable guidance. Journal of Information Systems Education, 28(2), 101–14.
Krumm, S., and Hertel, G. 2013. Knowledge, Skills, Abilities and Other Characteristics (KSAOs) for Virtual Teamwork. pp. 80–99. The Psychology of Digital Media at Work. Psychology Press.
Lee, T.W., Hom, P., Eberly, M., and Li, J. 2018. Managing employee retention and turnover with 21st century ideas. Organizational Dynamics, 47(2), 88–98.
Lee, T.W., and Mitchell, T.R. 2003. Control turnover by understanding its causes. The Blackwell Handbook of Principles of Organizational Behaviour, 93–107.
Lee, T.W., and Mitchell, T.R. 1994. An alternative approach: The unfolding model of voluntary employee turnover. Academy of Management Review, 19(1), 51–89.
Levy, J.J., Richardson, J.D., Lounsbury, J.W., Stewart, D., Gibson, L.W., and Drost, A.W. 2011. Personality traits and career satisfaction of accounting professionals. Individual Differences Research, 9(4).
Lewis, C. 2020. “Designing Business and Cybersecurity Strategy into Cybersecurity Operating and Organizational Models.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. July 30, 2020. Virtual meeting.
Lewis, G.B., and Cho, Y.J. 2011. The aging of the state government workforce: Trends and implications. The American Review of Public Administration, 41(1), 48–60. doi: 10.1177/0275074009359308.
Li, J.J., Lee, T.W., Mitchell, T.R., Hom, P.W., and Griffeth, R.W. 2016a. The effects of proximal withdrawal states on job attitudes, job searching, intent to leave, and employee turnover. Journal of Applied Psychology, 101(10), 1436.
Li, L., Xu, L., He, W., Chen, Y., and Chen, H. 2016b. Cyber Security Awareness and Its Impact on Employee’s Behavior. International Conference on Research and Practical Issues of Enterprise Information Systems, Vienna, Austria, pp. 103–111. Lecture Notes in Business Information Processing, vol. 268. doi: 10.1007/978-3-319-49944-4_8.
Martiny, K., Motzek, A., and Möller, R., 2015. Formalizing Agents’ Beliefs for Cybersecurity Defense Strategy Planning. Computational Intelligence in Security for Information Systems Conference, Burgos, Spain, pp. 15–25.
Mobley, W.H. 1977. Intermediate linkages in the relationship between job satisfaction and employee turnover. Journal of Applied Psychology, 62(2), 237–240. doi: 10.1037/0021-9010.62.2.237.
Moşteanu, N.R. 2020. Challenges for organizational structure and design as a result of digitalization and cybersecurity. The Business & Management Review, 11(1), 278–286.
Muntz, J., and Dormann, C. 2020. Moderating effects of appreciation on relationships between illegitimate tasks and intrinsic motivation: A two-wave shortitudinal study. European Journal of Work and Organizational Psychology, 29(3), 391–404.
Naff, K. 1994. Through the glass ceiling: Advancement of women in federal civil service. Public Administration Review, 54, 507–514.
Narayanan, A., Rajithakumar, S., and Menon, M. 2019. Talent management and employee retention: An integrative research framework. Human Resource Development Review, 18(2), 228–247.
NASEM. (National Academies of Sciences, Engineering, and Medicine). 2018. Assessing and Responding to the Computer Science Undergraduate Enrollments. Washington, DC: The National Academies Press.
NASEM. 2019. Minority Serving Institutions: America’s Underutilized Resource for Strengthening the STEM Workforce. Washington, DC: The National Academies Press.
Newhouse, W. Keith, S., Scribner, B., and Witte, G. 2017. National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework. NIST Special Publication 800-181. Gaithersburg, MD: National Institute of Standards and Technology. doi: 10.6028/NIST.SP.800-181.
NRC (National Research Council). 2013. Professionalizing the Nation’s Cybersecurity Workforce? Criteria for Decision-Making. Washington, DC: The National Academies Press.
Opengart, R., and Ison, D. 2016. A strategy for alleviating aviation shortages through recruitment of women. International Journal of Aviation Management, 3, 200–219.
Perez, J. 2020. “UPS Cybersecurity Defense In-Depth Strategy.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. June 29, 2020. Virtual meeting.
Pfister, I.B., Jacobshagen, N., Kälin, W., and Semmer, N.K. 2020. How does appreciation lead to higher job satisfaction? Journal of Managerial Psychology, 25(6), 465–479.
Piotrowski, V. 2020. “CyberCorps® Scholarship for Service Program (SFS).” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. April 22, 2020. Virtual meeting.
Schrage, M., Schwartz, M., Jones, R., Kiron, D., and Buckley, N. 2020. Opportunity marketplaces: Aligning workforce investment and value creation in the enterprise. Deloitte Insights. April, 28, 2020. Available at: https://www2.deloitte.com/us/en/insights/focus/technology-and-the-future-of-work/importance-of-investing-in-employees.html.
Schweyer, A. 2004. Talent Management Systems: Best Practices in Technology Solutions for Recruitment, Retention and Workforce Planning. Toronto: John Wiley & Sons Canada, Ltd.
SEI (Software Engineering Institute). 2014. Unintentional Insider Threats: Social Engineering. The CERT® Insider Threat Center, Carnegie Mellon University. Available: https://resources.sei.cmu.edu/asset_files/TechnicalNote/2014_004_001_77459.pdf.
SHRM (Society for Human Resource Management). 2018. Using Recognition and Other Workplace Efforts to Engage Employees: SHRM Survey Findings. Available: https://www.shrm.org/hr-today/trends-and-forecasting/research-and-surveys/Pages/employee-recognition-2018.aspx.
Singh, D. 2019. A literature review on employee retention with focus on recent trends. International Journal of Scientific Research in Science and Technology, 6(1), 425–431.
Subramony, M. 2009. A meta-analytic investigation of the relationship between HRM bundles and firm performance. Human Resource Management, 48(5), 745–768.
Tagarev, T., 2020. Towards the design of a collaborative cybersecurity networked organisation: Identification and prioritisation of governance needs and objectives. Future Internet, 12(4), 62. doi: 10.3390/fi12040062.
Turner, G.E., Deemer, E.D., Tims, H.E., Corbett, K., and Mhire, J. 2014. Cyber value and interest development: Assessment of a STEM career intervention for high school students. Electronic Journal of Science Education, 18(1), 1–15.
Vasileiou, I., and Furnell, S. 2019. Cybersecurity Education for Awareness and Compliance. Hershey, PA: IGI Global. doi: 10.4018/978-1-5225-7847-5.
Wolfson, M.A., and Mathieu, J.E. 2018. Sprinting to the finish: Toward a theory of human capital resource complementarity. Journal of Applied Psychology, 103(11), 1165.
Zafar, H. 2016. Cybersecurity: Role of Behavioral Training in Healthcare. Twenty-second Americas Conference on Information Systems, San Diego, CA, p. 1760.
Zurko, M.E. 2020. “Cybersecurity Workforce Impacts of Technical Transition.” Presentation to Committee on Cybersecurity Workforce of the Federal Aviation Administration. July 29, 2020. Virtual meeting.




















