3
Methodology
The statement of task directs the committee to “identify potential scenarios for the balance during the next 10 to 20 years between encryption and decryption (and other data and communications protection and exploitation capabilities) and assess the national security and intelligence implications of each scenario.” In particular, the committee is required to:
- Identify the drivers of the future, design and select scenarios for exploration, and consider the implications for the application of encryption and decryption capabilities, as well as the possible pace and effects of the adoption of post-quantum cryptology.
- Assess the national security, intelligence, and broad societal implications of each scenario determined by the committee to be most worthy of attention; identify and assess options for responding to these scenarios; and assess the implications for future Intelligence Community science and technology and security investments.
For the purposes of this study, the committee used a tailored mix of approaches based on the work of futures and strategic foresight firms, such as Toffler Associates and academic researchers such as Steven Weber at the Center for Long-Term Cybersecurity.1,2 The committee followed a five-step process:
- Develop the focal question.
- Scan the environment.
- Identify the drivers of change.
- Design and select the scenarios.
- Identify and explore strategically salient issues.
___________________
1 G.S. Parnell, J.A. Jackson, R.C. Burk, L.J. Lehmkuhl, and J.A. Engelbrecht, Jr., 1999, R&D concept decision analysis: Using alternate futures for sensitivity analysis, Journal of Multi-Criteria Decision Analysis 8(3):119–127.
2 J.A. Englebrecht, R.L. Bivens, P.M. Condray, M.D. Fecteau, J.P. Geis II, and K.C. Smith, 1996, Alternate Futures for 2025, Air University Press, Maxwell Air Force Base, AL.
DEVELOP THE FOCAL QUESTION
The focal question establishes foundation and context for the study and provides key insights into the required analysis. It is important to note that, in following the methodologies selected by the committee, the focal question that guides the effort may not necessarily be the same as what is found in the statement of task. In this case, while the sponsor outlined its objectives and supporting tasks, there was no single overarching question that would scope and guide the committee’s efforts. For any investigation of future scenarios, a focal question is critical to ensure both an efficient use of resources and a valuable outcome. Every experiment must start with a question, and this effort is no different; getting the question “right” is a critical first step in ensuring a valuable outcome for any futures and foresight effort.
The committee began by reviewing the questions and considerations identified by the sponsor in the statement of task (see Chapter 1) and determining if there was a way to aggregate them into a single, overarching question. After internal deliberation and research, the committee settled on the following focal question to guide the effort: What opportunities and risks associated with encryption and decryption will emerge over the next 10 to 20 years, and how can the Intelligence Community prepare itself?
As the committee began the task, the sponsor provided additional questions to help focus the work. These are presented in Box 3.1.
SCAN THE ENVIRONMENT
Although scenario development involves some imagination, scenarios must be grounded in data. Once the committee identified the focal question, it was able to identify primary and secondary sources and receive presentations from leading experts across relevant fields related to cryptography to ensure a broad understanding of the issues at play. This environmental scan allowed the committee to start identifying the features that would influence the future operating environment in its scenarios. The identification of a feature aims to answer the question, What might be out there?—features are attributes or characteristics of the future operating environment, or the material objects expected to be present in it, based on the information available (because, when looking to 2030 and 2040, it is difficult to find “reliable” forecast data). Features are considered data, but at their foundation they are the effects of human invention and behavior from the environment.
Having identified the potential features of the future operating environment, the committee could begin to explore their implications—that is, to ask the question, “Given the features, what is likely to emerge in the future?” More than cursory trends, the exploration of how features will evolve and emerge in the explored future allowed the committee to identify extrapolated, and linear (or faster) change in various categories subject to quantification or qualification when considered by themselves. The implications of the features are effects or results, and they need not be physical or tangible, allowing a more nuanced approach to imagining potential future scenarios.
Although the question focused on encryption, it was important for the committee to consider the global societal and political context in which encryption would be applied. This necessitated exploring such features as culture, economics, industry, intelligence, law, politics, regulatory environment, and society.
IDENTIFY THE DRIVERS OF CHANGE
What Are “Drivers”?
Following the Toffler Associates’ process,3 the committee assigned its observations to three drivers of the future operating environment. Drivers are defined as material or immaterial forces or vectors expected to be a significant cause of or contributor to change. Each of the three drivers is multi-dimensional and wide-ranging in its application within the scope of the focal question. Box 3.2 highlights important points using drivers.
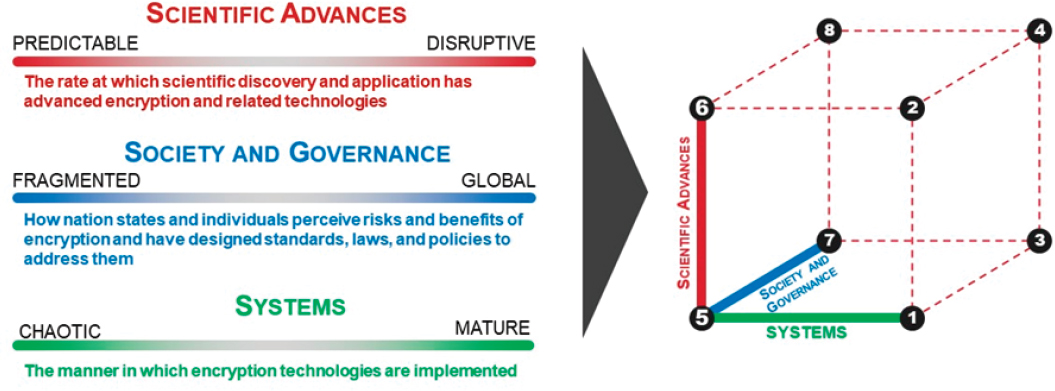
Each of the three drivers is framed by two endpoints—they are the extreme values at each end of the driver, and they bound the range of possibility of each driver. With each of the three drivers defining an orthogonal axis, one can envision the three-dimensional “decision space” defined by the drivers and bounded by the endpoints. The extremes of the three drivers define eight corners of a cube, creating eight unique potential scenarios for exploration.
Creating and Naming Drivers and Endpoints
To develop the drivers, the committee reviewed the data from the environmental scan, the members’ understanding of encryption and related policy and technology issues, and the issues raised by the statement of task, and discussed the features and implications that emerged. Through a series of facilitated discussions, the committee
___________________
3 The Toffler Associates’ process identifies three drivers that encompass the decision space for the future operating environment. Three drivers is a process/methodology goal that defines a cube representing the decision space of outcomes along each axis.
arrayed the information it had collected from the previous environmental scan, introduced additional relevant information, and identified three groupings. While exploring the logic for each grouping, the committee worked to identify the major forces that the groupings represented—these forces would then serve as natural names for the drivers. Naming drivers can be difficult, because one word or phrase may not capture the breadth of features and implications, but the committee sought to select names for the drivers and endpoints that would enable the reader to understand their intent quickly. In the process of developing and exploring the drivers, the committee also identified a set of findings and actions that would be broadly beneficial that appeared to be consequences of the drivers themselves rather than their interactions in scenarios. The latter are not being presented as formal recommendations, however.
For the purposes of this report, the committee identified and named the three drivers as follows: Scientific Advances, Society and Governance, and Systems. Figure 3.1 provides a short description of the drivers and how they bound the decision space.
DESIGN AND SELECT SCENARIOS
To design the scenarios, the committee first sketched a narrative for each of the eight scenarios, leveraging data from the environmental scan and making inferences from the interactions of the drivers. Like the creation of the drivers and endpoints, the narrative for each of the eight scenarios involves a mixture of imagination and analytical rigor—although they might not necessarily be probable, they must be both possible and plausible. Possible because no scenario should necessarily break the accepted laws of physics; plausible because they should allow decision makers to see themselves (or a future version of themselves) in the scenario to maximize immersion and learning.
Selecting the Scenarios
Based on the convergence of the endpoints for the drivers (see Appendix C), the committee discussed what each scenario might look and feel like in the world of 2040 and how each might be relevant to the discussion. After the committee created a thumbnail sketch of each of the eight scenarios, it set out to select the scenarios that it believed would be most interesting to explore the focal question and drive results for the sponsor.
The objective of the committee was to select three scenarios that would be stressful for planning and pose a wide range of situations, as well as meet criteria derived from the focal question. Other criteria the committee used in selecting the scenario:
- One future should be similar to the world in which we find ourselves today—that is, the result of extrapolating established trends. This scenario is not intended to be today—rather, it is a future state when many things have changed, but this scenario will be perceived as like today.
- One future should be considered the most stressful and challenging world to explore, given the focal question. This future may be the one farthest away in the cube from the status quo.
- One future should fall between those two extremes, allowing for the exploration of different alternatives.
Developing the Narratives
Based on its discussions and the criteria, the committee selected three scenarios that are defined and discussed in Chapter 5. Each of the scenarios selected by the committee presents varying degrees of complexity to explore the future of encryption and the impacts on the Intelligence Community. Once the committee selected the three scenarios that it would explore, it set out to design detailed narratives that would help to capture the relevant aspects of each. The descriptions sought to capture the most salient aspects of the future and answer questions such as, What nations are allies and adversaries? How do nations interact? How do people use the Internet? What is the role of the government in daily life? What about crime levels, education, technological advances, economy, and the regulatory environment?” The purpose of each narrative is to provide enough detail to provide a reader with a clear picture of the scenario, to tell a compelling story, and to help explore the questions, What is the sponsor’s biggest challenge or concern in this scenario? What is its biggest opportunity?
IDENTIFY AND EXPLORE STRATEGICALLY SALIENT ISSUES
The selected scenarios should identify and elevate issues for consideration. Some issues seem like imperatives and will need to be addressed because they are vital to the sponsor’s success in all or most of the scenarios; some will be important, but relevant in only one or two scenarios. Conversely, some future scenarios suggest alternative eventualities whose occurrence (or failure to occur) should be assessed at some point in the future.
The committee documented risks, opportunities, and actions associated with each scenario. In addition, the committee assembled consolidated findings and observations associated with the drivers that, in the committee’s view, applied no matter which scenario or individual developments occur in the future.





