4
Drivers
The interactions among society, technology, and cryptography have continually evolved, driven by such trends as the move to cloud computing, networked utilities, and the Internet of Things (IoT). There is no reason to believe that such evolution will cease in coming decades. This section describes the three drivers whose state the committee assessed would largely determine the future of encryption and as appropriate explores their interaction with current and foreseeable future technological and societal trends. The description of each driver begins with a summary chart that identifies the endpoints for that driver and lists some of the most significant developments in or attributes of a future that is driven by that extreme. For each driver, the summary chart is followed by an in-depth discussion of the driver and the characteristics and implications of its extremes.
As discussed in Chapter 3, each of the drivers deals with a different aspect of the future being explored. The committee determined that it was most appropriate to describe each driver in a format that seemed best aligned with the components and variables that make up that driver. Thus, although the summary charts for the three drivers have a common style and format, the detailed descriptions of the drivers and their endpoints vary depending on the nature and components of that driver.
SCIENTIFIC ADVANCES DRIVERS: DISRUPTIVE VERSUS PREDICTABLE
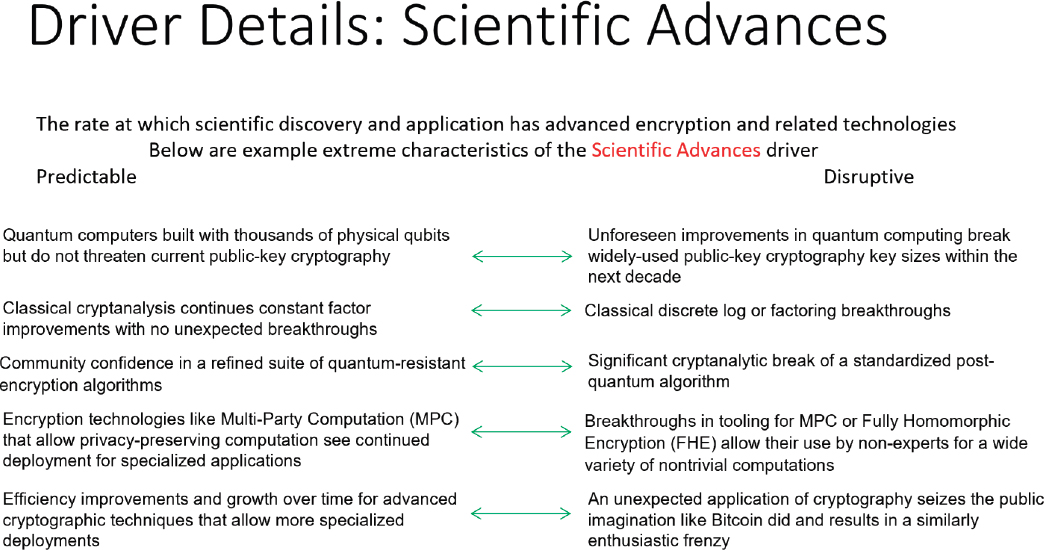
Scientific Advances deals with the emergence of new theoretical breakthroughs or significant technologies that impact cryptography. The creation of a large-scale fault-tolerant quantum computer would be one such advance, but new mathematical attacks on asymmetric encryption, advances that enable efficient computation on encrypted data, and technologies that use quantum properties for encryption also fall into this category. At two extremes, the state of future scientific advances could be either predictable or disruptive (see Figure 4.1).
The Scientific Advances driver measures the rate at which scientific discovery and application advance encryption and related technologies.
Scientific advances are a necessary precursor for technology to have impact in practice, but they are not sufficient on their own. As in all scientific fields, only a relatively small fraction of research results in cryptography are ultimately practical. It can often take years and additional discoveries to figure out what is useful and for ideas to be developed enough to have impact in the real world. At a very high level, a path to practicality for a scientific advance might begin with work giving the theoretical foundations for an idea, followed by work that fleshes out the idea more concretely, a series of academic-scale, proof-of-concept implementations to demonstrate real-world
practicality, limited use in special-purpose applications by industrial research, standardization, incorporation into widely used devices or libraries, and use in general-purpose applications. Scientific advances can also follow practice, as when real-world discoveries of new classes of vulnerabilities (weaknesses) spur research in the underlying causes, or the development and deployment of new technologies (like graphics processing units [GPUs], secure enclaves, or cryptocurrencies) can motivate researchers to develop new theories about the security strengths and weaknesses of technologies and systems.
The other two drivers attempt to capture the conditions that might promote or discourage the transfer of research progress into practice. Research and development often proceed at an uneven pace: ideas can be introduced and languish unnoticed for years, fads and fashionable areas can produce large quantities of publications in niche areas all at once, and there can be communication gaps between the research community and practitioners.
The cryptography research community is broad and spans a range from purely theoretical computer science and mathematics to applied security and privacy work with an implementation focus. As in many academic fields, the vast majority of published papers are theoretical, and it is often hard to predict if a given work will have an impact in practice. There are also research areas that, despite large amounts of research investment and large numbers of academic publications, may never become practical enough to have impact on the real world (e.g., theoretical work on provable software obfuscation), and appear destined to remain of theoretical or only academic interest for the foreseeable future.
The endpoints of the Scientific Advances driver are “predictable” at one extreme, and “disruptive” at the other. “Predictable” scientific advances means that the committee envisions progress to continue at the current pace, with no great surprises to researchers working in the field. “Disruptive” advances would include some kind of major scientific development that is both unexpected given the pace and direction of current results and likely to have a significant impact on either theory or practice.
The committee includes both offensive and defensive advances under this umbrella. Cryptography is somewhat unusual among mathematical and scientific fields in that a “scientific advance” can be offensive or destructive and show that a construction or an idea is in fact insecure, even if it was previously believed to be secure. This is because the security of a cryptographic scheme usually relies on the assumption that a particular computational
problem is hard for an adversary to solve in a feasible amount of time. For problems useful for cryptography, it is rare and typically applies only in limited circumstances to be able to specify fully rigorous lower bounds for the computational hardness of problems. Confidence in the hardness of problems is typically gained after years of public analysis has failed to produce improved algorithms for solving them.
The following sections describe the endpoints of “predictable” and “disruptive” advances by laying them out in several relevant areas.
Quantum Computing and Cryptanalysis
The 2019 National Academies’ report Quantum Computing: Progress and Prospects is a detailed study of the past, present, and future of quantum computing.1 The authors did not give explicit predictions for a timeline for the development of quantum computing technology. They stated in their summary:
Predicting the future is always risky, but it can be attempted when the product of interest is an extrapolation of current devices that does not span too many orders of magnitude. However, to create a quantum computer that can run Shor’s algorithm to find the private key in a 1024-bit RSA encrypted message requires building a machine that is more than five orders of magnitude larger and has error rates that are about two orders of magnitude better than current machines, as well as developing the software development environment to support this machine.
The progress required to bridge this gap makes it impossible to project the time frame for a large error-corrected quantum computer, and while significant progress in these areas continues, there is no guarantee that all of these challenges will be overcome. The process of bridging this gap might expose unanticipated challenges, require techniques that are not yet invented, or shift owing to new results of foundational scientific research that change our understanding of the quantum world. Rather than speculating on a specific time frame, the committee identified factors that will affect the rate of technology innovation and proposed two metrics and several milestones for monitoring progress in the field moving forward.
The conclusions of that report are still valid as the committee writes this report 2 years later.
Predictable
According to the Global Risk Institute’s Quantum Threat Timeline Report 2020, around half of the polled experts think there is a 5 percent or less chance of a “significant quantum threat to public-key” cryptography within the next 10 years, but 85 percent of the experts believed there was a 50 percent or greater chance of a threat to public-key cryptography within 20 years. A useful quantum computer would implement logical “qubits” (see Chapter 2) as the basis of its computational power. In the cited survey, most respondents believed that construction of a single logical qubit (a qubit with reliable error correction) would be demonstrated within 1 to 3 years. In order to threaten current public-key cryptography, a quantum computer with thousands of logical qubits would need to be constructed. Current quantum computers have been built with under a hundred physical qubits (“noisy” qubits without error correction), and an extrapolation of this progress would have research prototypes built with thousands of physical qubits by the end of the decade. At current estimates, a quantum computer would need 10 million to 20 million physical qubits to factor 2048-bit RSA.2,3 Consistent progress in scaling quantum computers may encounter yet unknown engineering challenges, and expert opinion currently differs on precisely when such a quantum computer would be built. The authors of the Quantum Computing report identified the constant average
___________________
1 National Academies of Sciences, Engineering, and Medicine (NASEM), 2019, Quantum Computing: Progress and Prospects, Washington, DC: The National Academies Press, https://doi.org/10.17226/25196.
2 V. Gheorghiu and M. Mosca, 2019, “Benchmarking the Quantum Cryptanalysis of Symmetric, Public-Key and Hash-Based Cryptographic Schemes,” Institute for Quantum Computing, University of Waterloo, February 7, https://arxiv.org/pdf/1902.02332.pdf.
3 M. Roetteler, M. Naehrig, K.M. Svore, and K. Lauter, 2017, “Quantum Resource Estimates for Computing Elliptic Curve Discrete Logarithms,” Cryptology ePrint Archive, https://eprint.iacr.org/2017/598.
gate error rate for physical qubits as a short-term metric and the effective number of logical error-corrected qubits of a system as a long-term metric to monitor the scaling progress of quantum computers.4
Disruptive
In the area of quantum cryptanalysis, a disruptive scientific advance would be experimental construction within the next decade of a quantum computer capable of threatening widely used public-key cryptography. This would likely involve the development of physical qubits with a sufficiently low error rate and the ability to build and connect these together at scale.5 A similar disruptive effect might be achieved by an algorithmic improvement that threatens public-key cryptography without requiring an enormous number of error-corrected qubits.
The authors of the Quantum Computing report conclude that disruptive scientific advance in quantum computing is more likely if there is a virtuous cycle of research and development investment from industry. In such a cycle, initial scientific advances in quantum computing might attract large amounts of capital, which in turn could result in new rounds of significant scientific progress. An important advance that would enable such a virtuous cycle to fund the enormous engineering effort required would be the development of a currently unknown but compelling commercial application for noisy intermediate-scale quantum (NISQ) computers. Such a commercial application of NISQ computers would likely not be related to cryptography or security at all: machine learning or chemistry simulations are probably more lucrative and of broader interest. However, a virtuous cycle that defines a path to commercially relevant quantum computing at scale would likely bring about improvements speeding cryptographically relevant quantum computers as a side effect.
Last, there is the possibility of a scientific advance that conclusively rules out the possibility of scalable general purpose quantum computing under some set of conditions relevant to public-key cryptography. For example, there may be a proof of a lower bound on achievable error rates at levels incompatible with effective quantum computation. Such an advance would eliminate the potential threat to encryption from quantum computers.
Classical Cryptanalysis
Improvements to classical cryptanalysis will continue to be a factor in choice of security parameters and cryptographic algorithms going forward. History can be a guide for what these improvements and transitions may look like. There are several recent examples of cryptographic algorithm transitions that took place owing to improvements in classical cryptanalysis. These include the moves from the MD5 hash function to SHA-1 and from SHA-1 to SHA-2 after a progression of weaknesses and finally practical attacks were found on the MD5 and SHA-1 algorithms and the move from 1024-bit RSA to 2048-bit RSA (or larger) owing to expected improvements from Moore’s law bringing 1024-bit factoring within feasible range.
Predictable
The current record for factoring the product of large prime numbers, set in 2020, is an attack on an 829-bit RSA modulus that took 2,700 core-years on a few academic clusters.6 A back-of-the-envelope extrapolation from this running time suggests that a 1024-bit factorization would require around 500,000 core-years without any
___________________
4 From NASEM, 2019, Quantum Computing: Progress and Prospects (Washington, DC: The National Academies Press, https://doi.org/10.17226/25196):
5 X.-C. Yao, T.-X. Wang, H.-Z. Chen, W.-B. Gao, A.G. Fowler, R. Raussendorf, Z.-B. Chen, et al., 2012, Experimental demonstration of topological error correction, Nature 482(7386):489–494, https://doi.org/10.1038/nature10770.
6 F. Boudot, P. Gaudry, A. Guillevic, N. Heninger, E. Thomé, and P. Zimmermann, 2020, “Comparing the Difficulty of Factoring and Discrete Logarithm: A 240-Digit Experiment,” Cryptology ePrint Archive, Report 2020/697, https://eprint.iacr.org/2020/697.
further algorithmic or implementation improvements. The largest supercomputers in the world currently have millions of cores. The public literature has suggested that 1024-bit factorization has been within reach for large organizations since 2010 at the latest. A public demonstration of 1024-bit factoring or computation of a prime-field discrete logarithm (believed to be a few times harder than factoring) would not be surprising: the main difficulty would be convincing an organization with sufficient computing power that this would be a good use of hardware. Progress on the elliptic curve discrete logarithm problem—the basis for the elliptic curve variants Elliptic Curve Diffie-Hellman (ECDH) and Elliptic Curve Digital Signature Algorithm (ECDSA)—has mostly consisted of taking advantage of hardware improvements; records within the past decade have ranged from 113-bit to 118-bit curves; in principle, a few more bits above that would be feasible.7
Disruptive
Even a modest-seeming algorithmic improvement to asymmetric cryptanalysis algorithms could have a potentially high impact, because the key sizes in current use are based upon the running times of the current best attacks. The best cryptanalytic algorithms for RSA and Diffie-Hellman are the “number field sieve” algorithms for factoring and discrete logarithm for large characteristic finite fields, respectively. In 2013, a series of breakthroughs for a closely related algorithm, the function field sieve for discrete logarithm in small characteristic finite fields, produced the first algorithmic improvements for this problem after more than two decades and a series of impressive new computational records.8 These improvements did not turn out to threaten widely deployed cryptography, but even a much more modest improvement in this direction for the general number field sieve would have the potential to threaten the 2048-bit RSA and Diffie-Hellman key sizes in current use and would require either increasing the key sizes or replacing with schemes based on alternative cryptographic assumptions.
An improvement in the algorithms that are the best classical cryptanalysis of elliptic curve discrete logarithm would be similarly impactful: the security of 256-bit curves could be threatened by any algorithm that improves upon the current algorithms for elliptic curves. Such an improvement would be more surprising than an improvement for factoring or finite-field discrete logarithm given the existing lack of progress in this area.
Based on current understanding, the classical improvements that jeopardize the security of major standardized symmetric cryptographic algorithms (Advanced Encryption Standard [AES], the SHA-2 and SHA-3 hash functions) seem much less within the realm of possibility. In particular, AES has a comfortable security margin against all known families of attacks;9 the discovery of an entirely new and practical family of attacks that applies to AES would be both disruptive and surprising. (This is in contrast to the situation with factoring and discrete log mentioned above, in which usable key sizes have little security margin against any improvement in a known class of attacks.) However, flaws would still be expected to be found in other symmetric algorithms used in more niche applications, such as proprietary or low-power algorithms, which typically receive less public scrutiny or must accommodate challenging constraints.
Most of the scientific expertise in the open research community in cryptanalysis is outside of the United States, primarily in Europe, so any improvements would be expected to come from international researchers. While the Internet has enabled broader dissemination of knowledge about cryptography and security, the high-level research training and careers required to understand and contribute to the state of the art require real investment in research infrastructure from government and industry.
___________________
7 D.J. Bernstein, S. Engels, T. Lange, R. Niederhagen, C. Paar, P. Schwabe, and R. Zimmermann, 2016, “Faster Elliptic-Curve Discrete Logarithms on FPGAs,” Cryptology ePrint Archive, Report 2016/382, https://eprint.iacr.org/2016/382.
8 R. Barbulescu, P. Razvan, P. Gaudry, A. Joux, and E. Thomé. “A heuristic quasi-polynomial algorithm for discrete logarithm in finite fields of small characteristic.” In Annual International Conference on the Theory and Applications of Cryptographic Techniques, pp. 1–16. Springer, Berlin, Heidelberg, 2014. https://link.springer.com/chapter/10.1007/978-3-642-55220-5_1.
9 See A. Bogdanov, D. Khovratovich, and C. Rechberger, 2011, “Biclique Cryptanalysis of the Full AES,” in Advances in Cryptology—ASIACRYPT 2011 (D.H. Lee and X. Wang, eds.), ASIACRYPT 2011, Lecture Notes in Computer Science, Volume 7073, Berlin, Heidelberg: Springer, https://doi.org/10.1007/978-3-642-25385-0_19, and P. Derbez, P.-A. Fouque, and J. Jean, 2012, “Improved Key Recovery Attacks on Reduced-Round AES in the Single-Key Setting,” Cryptology ePrint Archive 2012/477, https://eprint.iacr.org/2012/477.pdf.
FINDING 4.1: Most of the current public scientific expertise in algorithm design, cryptanalysis, and other areas of applied cryptography is outside the United States, largely in Europe. In contrast, within the United States, cryptography is taught as an area of theoretical computer science. The specific areas of expertise necessary to guide and facilitate the transition to post-quantum cryptography are relatively new and will require a more robust educational pipeline to train new talent.10 Public research investment, through the National Science Foundation and other organizations, would encourage this process, while strict U.S. export control regulations have historically discouraged talent from locating in the United States.
FINDING 4.2: An improvement in asymmetric cryptanalysis algorithms could have a significant effect on the security of public key encryption algorithms that are in wide use today. Such an improvement would enable more efficient attacks on encrypted information using conventional computers rather than requiring the construction of a quantum computer. Furthermore, it could potentially be exploited in secret and with little or no advance notice.
Post-Quantum Algorithms
The current candidates for post-quantum public key encryption and signature algorithms (lattices, structured lattices, supersingular isogeny Diffie-Hellman, hash-based signatures, etc.) all have downsides in the form of larger keys, ciphertext/signature size, and/or longer computation time than elliptic curve cryptography. Furthermore, the relative quantum resistance of each of the algorithm candidates under consideration for standardization is an area of active research. The cryptographic community continues to study the security assumptions underlying the candidates. The more public analysis and scrutiny a candidate receives, the more confidence the community gains in its presumed resistance to attack by a quantum-aided adversary. (See Chapter 2 for more details.)
Predictable
At a predictable rate of scientific advances, within the decade the committee would expect to see increased confidence in the resistance to classical and quantum cryptanalysis of these schemes, and better optimizations and instruction-level support in major central processing units (CPUs) to improve the performance of these algorithms, as well as support in transport layer security (TLS) and other major protocols. Some weaknesses in some special case parameter settings for these algorithms might be found, but it is reasonable to expect that the community will agree on a suite of implementable, post-quantum secure algorithms.
Disruptive
In this realm, the committee can foresee both constructive and destructive scientific advances. On the constructive side, a new quantum-secure construction might be found that does not have any key length or computational downsides compared to elliptic curve cryptography: this could greatly increase the speed of adoption. On the destructive side, an efficient quantum or classical algorithm for solving the shortest vector problem in algebraically structured lattices (or another post-quantum construction that the community currently has a lot of confidence in) would seriously disrupt the standardization and deployment process. The committee views significant cryptanalytic attacks against hash-based signatures as very unlikely because the security of these constructions relies on several hardness assumptions of the underlying hash functions. (See the related finding in Chapter 2.)
___________________
10 To understand the cryptographic landscape, one must receive a Ph.D. in cryptography with at least 3–5 years of highly specialized training in graduate school. Even though the information is freely available on the Internet, the sheer volume of information and high degree of specialization means that without hands-on advising, it is nearly impossible to learn the skillset necessary to become proficient in cryptography.
Computing on Encrypted Data
There are several cryptographic technologies that accomplish tasks related to the general goal of computing on encrypted data in an untrusted environment without decryption. These include multi-party computation (MPC), searchable encryption, private set intersection, and partially and fully homomorphic encryption. (These were introduced in Chapter 2.) Currently, the use of these technologies requires the support of expert cryptographers.
Predictable
There have already been several deployed and widely used applications (and many proofs-of-concept) of MPC and searchable encryption. The predictable future, driven especially by system implementers’ need to protect users’ privacy, is for more MPC applications to be deployed, but without breakthroughs each will continue to require specialized expertise. Fully homomorphic encryption is less efficient than MPC. The other techniques will also see some applications but will remain niche technologies. There is substantial uncertainty in the use of zero knowledge (ZK) tied to blockchain techniques, as it is hard to foresee how the tension between blockchains and trusted third parties will evolve.
Disruptive
Advances in tooling, or in technology that makes it practical for non-experts to deploy new multiparty applications, would result in wider use of this form of confidential computing. On the other hand, if these techniques have to be made quantum-resistant their spread will be slowed. Algorithmic breakthroughs could make any of these techniques more efficient, and so more widely used. Regulations could limit or motivate the development and use of computation on encrypted data.
Anonymous Communication and Metadata Protection
In many existing communication systems, encryption is used to protect only the data considered to be the “content” of communications, while leaving metadata about sender and receiver, time, length, or other properties unencrypted. For example, Hypertext Transfer Protocol Secure (HTTPS) encrypts the contents of websites, but a passive observer of the network traffic can see the network IP (Internet protocol) addresses of the sender and receiver, the timing, length, and order of network requests, and other metadata that can reveal significant information about the likely encrypted content.
There are a number of cryptographic tools and ideas that can be used to build privacy-enhancing technologies by allowing systems to function while concealing information from some or all parties. For example, the Tor network uses cryptography to route network connections through volunteers in order to keep an eavesdropper from linking the connection’s origin and destination network address together. The Apple/Google COVID-19 exposure notification system uses cryptographic ideas to maintain the participants’ privacy while still reporting their contact status.11,12
In addition to the concepts of encryption, MPC, and FHE discussed above, a number of advanced cryptographic constructions that are not currently widely used can achieve more advanced privacy goals; these include zero-knowledge proof and its variants, function secret sharing, Oblivious RAM, and Private Information Retrieval. These ideas are discussed in Chapter 2.13,14
___________________
11 There is some leakage in the Apple/Google COVID-19 solution, which is addressed in additional proposals.
12 Apple, 2020, “Apple and Google Partner on COVID-19 Contact Tracing Technology,” Newsroom, April 10, https://www.apple.com/newsroom/archive.
13 K. Yang, P. Sarkar, C. Weng, and X. Wang, 2021, “Quicksilver: Efficient and Affordable Zero-Knowledge Proofs for Circuits and Polynomials over Any Field,” Cryptology ePrint Archive, https://eprint.iacr.org/2021/076.
14 N. Franzese, J. Katz, S. Lu, R. Ostrovsky, X. Wang, and C. Weng, 2021, “Constant-Overhead Zero-Knowledge for RAM Programs,” Cryptology ePrint Archive, https://eprint.iacr.org/2021/979.
Predictable
Recent years have brought real-world deployments of these ideas, such as the use of ZK to build cryptographically untraceable anonymous transactions in the cryptocurrency Zcash, and deployment of MPC by Google and Apple for applications like computation on sensitive data and making assertions about private data without disclosing the underlying data.15,16 Predictable scientific advances in these areas would include efficiency improvements across the board. A predictable course of development would also see companies deploying more sophisticated cryptographic schemes to protect aspects of privacy and verifiability for their users and data. As these applications broaden, this will drive a cycle of increased interest and investment in efficient cryptographic privacy-preserving techniques and implementations in both industry and government applications.17 A predictable counter-trend is that relying parties will struggle to understand the protocols or be (perhaps rightly) skeptical of the security of implementations, limiting the benefits that these technologies can ultimately provide.
Disruptive
Disruptive advances in this area may come from transitioning technologies into practice. For example, a completely anonymous low-latency network communication mechanism that produces no metadata and sees wide adoption would likely be disruptive. A second example of a disruptive development might be government initiatives to use ideas from privacy-enhancing technologies to build more sophisticated or privacy-preserving mechanisms for law enforcement search or tracking of encrypted communications and data. As a positive development, such initiatives could have the potential to provide more transparency or accountability for government agencies if implementations are rigorous and transparent. They may also spur development and refinement of privacy-enhancing technologies. On the other hand, such deployments risk public backlash, misunderstandings over the technical guarantees provided by these technologies, misuse, or loss of trust owing to implementations being vulnerable to the same types of vulnerabilities and bugs common to any implementation.
Lightweight Cryptography
The AES cipher is near ubiquitous for symmetric encryption, and no flaws are expected to be found that might call its security into question. It was designed to be well suited to hardware implementation, and many microprocessors have high-speed AES hardware support.18,19 However, there have been calls to develop and standardize new “lightweight” symmetric encryption algorithms that would be suitable for extremely small and low-resource sensors expected to be part of the coming IoT, and the National Institute of Standards and Technology (NIST) is currently in the process of selecting lightweight cryptographic algorithms for standardization.20
Predictable
There are already a number of candidate lightweight cryptographic algorithms proposed to NIST for standardization. Predictable scientific advances in this area would include successful conclusion of the NIST activity and
___________________
15 E. Ben Sasson, A. Chiesa, C. Garman, M. Green, I. Miers, E. Tromer, and M. Virza, 2014, “Zerocash: Decentralized Anonymous Payments from Bitcoin,” 2014 IEEE Symposium on Security and Privacy, https://doi.org/10.1109/sp.2014.36.
16 M. Ion et al., 2020, “On Deploying Secure Computing: Private Intersection-Sum-with-Cardinality,” pp. 370–389 in 2020 IEEE European Symposium on Security and Privacy (EuroS&P), https://doi.org/10.1109/EuroSP48549.2020.00031.
17 For example, see the proposed “H.R.4479—Student Right to Know Before You Go Act,” which would use MPC to compute information about college student outcomes.
18 Wikipedia, “Trusted Platform Module,” Wikimedia Foundation, https://en.wikipedia.org/wiki/Trusted_Platform_Module, accessed October 14, 2021.
19 Intel, “Intel® Software Guard Extensions,” https://software.intel.com/content/www/us/en/develop/topics/software-guard-extensions.html, accessed October 12, 2021.
20 NIST, “Lightweight Cryptography,” Computer Security Resource Center, Information Technology Laboratory, https://csrc.nist.gov/Projects/Lightweight-Cryptography, accessed October 15, 2021.
publication of a Federal Information Processing Standard (FIPS) for lightweight cryptography along with guidelines for appropriate use scenarios, followed by some deployment in real-world systems with those characteristics.
Disruptive
A disruptive scientific advance in this area might include a catastrophic break of an algorithm after its standardization and large-scale deployment.
Standards for Cryptography
A number of different international and national organizations publish standards and recommendations for cryptographic algorithms and protocols. Examples of organizations publishing influential cryptographic standards include NIST, which publishes algorithm recommendations that vendors must follow in order to be FIPS certified and sell their products to the U.S. government, the Internet Engineering Task Force (IETF), which publishes standards for network protocols including TLS, SSH, S/MIME, IPsec, and many others, and the International Organization for Standardization (ISO), which publishes international standards.
These organizations use different processes for creating and approving standards. For several major cryptographic algorithm recommendations (AES, SHA-3, and the post-quantum cryptography algorithms), NIST has run open international competitions in which researchers submit their algorithm designs and those designs go through several rounds of vetting, including attempts at cryptanalysis, by the open research community and NIST before NIST chooses and publishes the final candidates. NIST also publishes recommendations written through an internal process that involves workshops and public comment periods.
Protocols standardized and published by the IETF are the result of open processes and the work of individuals within the IETF’s various working groups (WGs). Anyone can join an IETF WG and propose or contribute to the development of a draft standard, and only individuals can be members of a WG. Although the character of individual WGs vary, common processes are used across the IETF to develop their standards. The resulting Requests for Comments (RFCs) document most of the protocols upon which the Internet operates today. Recently, the IETF has begun collaborating more closely with academia on the development of new security standards; the TLS 1.3 RFC is an example of a particularly open collaboration among academic and industry contributors.
ISO committees are composed of representatives from different countries’ national standards bodies such as the American National Standards Institute (ANSI) in the United States. Industry, academic, and individual contributions to ISO standards and the participation of subject matter experts are channeled through the national bodies.
In addition to the organizations listed above, sometimes cryptographic standards are developed by industry groups or consortia as part of an effort to standardize new technology. For example, both the 3rd Generation Partnership Project (3GPP), which developed mobile telecommunications standards such as Global System for Mobile Communications (GSM) and LTE, and the Bluetooth Special Interest Group, which developed the various Bluetooth short-range wireless specifications, designed and specified their own encryption algorithms as part of their specification suites.
There are multiple technical and non-technical factors that drive the development of new standards and recommendations. Some of these include desire for new functionality, performance, desire to obtain patent royalties or impose licensing restrictions, desire for backdoors or other mechanisms that could enable government access to encrypted data, desire to advantage national industries and economies, and nations’ preference for relying on their own standards and technologies. The costs in time and effort of participating in standards bodies can limit participation to individuals or organizations who seek a commercial or reputational benefit from the integration of a particular idea or technology in a standard or from blocking an idea or technology.
Predictable
NIST is expected to produce post-quantum encryption and digital signature algorithm recommendations starting in early 2022 and continuing for the next few years with multiple waves of selections. All of the final
candidates were produced by researchers working in the open community. Owing to the open process and NIST’s history of past successful competitions (e.g., AES, SHA-3), the predictable path of development and deployment is for NIST’s selections to be adopted into updated security standards and protocols over the next 5 to 10 years.
However, because the structure of these algorithms is new, the committee also expects continued research and development of newer post-quantum algorithms and variants of NIST’s selections. A predictable path of development for these variants, if they offer measurable performance or security advances over NIST’s selections, would see them potentially adopted by major implementations with sufficient cryptographic agility in parallel with NIST’s selections. Eventually, these variants might themselves be included in updates to NIST’s standards.
Disruptive
A potential disruptive development might involve the U.S. government’s dilemma upon the discovery of a weakness in an algorithm that had been proposed to be standardized. Although an Executive Branch policy process known as the Vulnerabilities Equities Process exists to enable a decision either to disclose fully the details of the weakness or to “retain the vulnerability” for the Intelligence Community’s possible use, neither option might be attractive. The government might have to disclose classified details to convince a mistrusting, skeptical public, influenced by the memories of the Dual Elliptic Curve incident detailed in Chapter 2, that the algorithm was indeed deficient; but if that were unacceptable, it would withhold such information, thus allowing use for public and commercial purposes of the weak algorithm.
Other disruptive developments might include wildly divergent algorithm recommendations coming from Chinese or European government standards bodies, or the standardization at a national level of an algorithm suspected to be backdoored by a government agency that large technology companies are forced to implement in order to sell products in that country.
Program Obfuscation
There has been considerable interest in cryptographic methods for program obfuscation, but it remains an open question whether an efficient general approach can be built for practical applications, despite a considerable output of research publications on the topic.21
Predictable
Cryptographic software obfuscation may never be feasible even in principle. An alternative to software-based cryptographic program obfuscation is to use hardware security mechanisms to protect the execution of sensitive programs. Examples of such hardware mechanisms in use today include Apple’s Secure Enclave technology and trusted execution environments like Intel’s SGX.22,23 The current state of the art is that there is a cat-and-mouse game between security researchers and hardware developers to discover methods to circumvent these mechanisms and patch the flaws.24 The predictable course of development in this area is that secure hardware technology will steadily improve over time through this process, and hardware-enforced security will become even more practical and widely used. See the discussion of tamper-resistant hardware in the Systems Driver section below for more details.
___________________
21 S. Garg, C. Gentry, S. Halevi, M. Raykova, A. Sahai, and B. Waters, 2016, Candidate indistinguishability obfuscation and functional encryption for all circuits, SIAM Journal on Computing 45(3):882–929, https://doi.org/10.1137/14095772x.
22 Apple, “Secure Enclave,” Support, https://support.apple.com/en-gb/guide/security/sec59b0b31ff/web, accessed October 12, 2021.
23 Intel, “Intel® Software Guard Extensions,” https://software.intel.com/content/www/us/en/develop/topics/software-guard-extensions.html, accessed October 12, 2021.
24 S. Van Schalik, A. Kwong, D. Genkin, and Y. Yarom, “SGAxe: How SGX Fails in Practice,” https://sgaxe.com/files/SGAxe.pdf, accessed October 13, 2021.
Disruptive
There are recent scientific results showing that some types of program obfuscation can be built with security based on plausible hardness assumptions. However, even if the security of these proposed schemes and hardness assumptions holds up to scrutiny, there is a long road to practicality: the initial proposals are too slow for any practical application. A fundamental breakthrough or series of breakthroughs would be needed to make a provably secure program obfuscation scheme based on well-accepted hardness assumptions practical; such a fortuitous series of developments happening within 10 to 20 years would be unexpected.
Cryptocurrencies
Predictable
The level of interest and funding around cryptocurrencies has already begun to spur scientific development of related technologies, including consensus protocols, short zero-knowledge proofs, advanced digital signatures, time-lock puzzles, cryptographic protocols, and verifiable computation. Cryptocurrencies face some major barriers to more widespread adoption, notably the possibility of widespread government regulation to limit untraceable transactions. Other barriers may include environmental impact for proof-of-work based schemes, transaction delay, transaction traceability, and security considerations including fraud and irreversible transactions. The scientific tools necessary to solve the computational problems are getting better understood.
There is considerable hype around applications of blockchains, but the so-called permissionless (typically proof-of-work or proof-of-stake based) blockchains that are used to back the most common cryptocurrencies, as well as the underlying data structure of a blockchain itself, seem poorly suited to many applications. Permission-less blockchains involve serious additional barriers to broad adoption owing to environmental impact, security challenges, and inefficiency. In a predictable sequence of events, the use of such permissionless blockchains would largely be a symbolic and minor detail in what are effectively centralized applications. Developers of distributed systems may also continue to use the word “blockchain” to apply to the more sophisticated consensus algorithms, multiparty computation, and more advanced distributed data structures that would be a better match for bona fide distributed applications.
A predictable course of development over the next 10 to 20 years would see cryptocurrencies and related technologies gain somewhat broader adoption and continue to serve as inspiration, funding source, and proving ground for an increasing variety of advanced cryptographic techniques. It is also predictable that cryptocurrencies currently based on classical cryptography (e.g., ECDSA) will begin to migrate to post-quantum algorithms along with other industries on similar time scales. Predictable developments could also include the rapid migration from the existing proof-of-work scheme (e.g., Bitcoin mining uses proof of work) to alternative schemes (such as proof of stake; Ethereum plans to transition within this year) that have much lower environmental costs and impacts.
Disruptive
It is possible that disruptions could emerge toward growth or contraction with respect to cryptocurrencies. Disruptive growth might see sufficiently broad deployment that one or more cryptocurrencies become the de facto fiat currency in large parts of the world. Disruptive contraction could come largely from the policy arena discussed below under “Society and Governance” rather than technical developments, but possible developments are listed here to provide a complete picture. Disruptive contractions could occur if cryptocurrencies featuring privacy and anonymity wither and eventually die under a barrage of strict government regulations related to money laundering, sanctions evasion, terrorist financing, fraud, cyberattacks, and similar concerns. Cryptocurrencies—Bitcoin in particular—facilitated the monetization of international ransomware attacks, and continued attacks could lead to significant regulatory changes. The investment bubble surrounding cryptocurrencies is large enough that a catastrophic crash could have measurable economic impact; such a crash could result in loss of interest, excitement, and funding in the general area.
Applications of Cryptography
Cryptocurrencies are an application of cryptography that futurists envisioned in the 1980s, and became a reality decades later with the first release of Bitcoin in 2009. Cryptocurrencies began to drive cryptographic and systems advances when they took off during the 2010s, as well as enabling additional chaos by facilitating the evolution of ransomware. There are numerous other potential applications of cryptography that could be developed to the point of practicality, including privacy-preserving collection and search methods for law enforcement and intelligence, cryptographically verified supply chains, cryptographically verified voting receipts,25 or using the cryptographic techniques described above to allow privacy-preserving data sharing in business contexts.26
Predictable
Other applications of cryptography that were predicted by the “cypherpunks” and other enthusiasts and have since seen real-world use include anonymized web browsing, hidden services and the “dark web,” dark markets, prediction markets, steganographic techniques, and ubiquitous end-to-end encrypted messaging.27 A predictable rate of scientific advances would see incremental improvements to the efficiency and usability of these technologies by non-experts that would enable more widespread deployment. These new applications can have powerful effects, often simultaneously for good and bad, with controversy attached. This is already true for secure communications and cryptocurrencies; other applications of cryptographic technologies would likely also be seen to be used for both good and bad.
Disruptive
A disruptive advance in this category would be an idea like Bitcoin that goes from a not fully realized intention to proof of concept to mainstream at a rapid pace and spurs a cycle of investment, further scientific advances, and ultimately societal impact.
Quantum Key Distribution
Quantum key distribution (QKD) systems leverage properties of light quanta to enable parties to negotiate a secret key that an eavesdropper cannot determine except through an exceptional stroke of luck. (Despite sharing the term “quantum” and sometimes being referred to as “quantum cryptography,” QKD is entirely unrelated to quantum computing or post-quantum cryptography.) Current QKD designs perform only key agreement; authentication would need to be done using standard cryptographic algorithms, although someday long-term quantum memories could perhaps support authentication via unclonable shared, secret keys. Although QKD systems are often described as implementing one-time pads, at present they cannot generate key material fast enough to protect high-speed traffic; hence they may be used to generate key material for classic algorithms such as AES, enabling changes of the symmetric key very often (e.g., many times per second).
The security properties of real QKD systems are somewhat murky at present, and because they require transmission and reception of exceptionally dim light (“single photons”) they need specialized optical equipment and an unencumbered optical channel through fiber or the atmosphere. Although such systems may have niche applications, they are unlikely to become pervasive within the next 20 years.
___________________
25 An example of one such system is the ElectionGuard end-to-end verifiable election technology by Microsoft (T. Burt, 2019, “Protecting Democratic Elections Through Secure, Verifiable Voting,” Microsoft on the Issues (blog), May 6, https://blogs.microsoft.com/on-the-issues/2019/05/06/protecting-democratic-elections-through-secure-verifiable-voting). Recently, Hart InterCivic (one of the “big 3” voting equipment manufacturers in the United States) announced that it would start incorporating ElectionGuard into its systems (Microsoft News Center, 2021, “Hart and Microsoft Announce Partnership to Make Elections More Secure, Verifiable,” June 3, https://news.microsoft.com/2021/06/03/hart-and-microsoft-announce-partnership-to-make-elections-more-secure-verifiable).
26 Microsoft News Center, 2021, “Hart and Microsoft Announce Partnership to Make Elections More Secure, Verifiable,” June 3, https://news.microsoft.com/2021/06/03/hart-and-microsoft-announce-partnership-to-make-elections-more-secure-verifiable.
27 Cryptoanarchy.wiki, “Cypherpunks Mailing List Archive,” https://mailing-list-archive.cryptoanarchy.wiki, accessed October 15, 2021.
Predictable
A predictable course of advancement might see existing proof-of-concept networks in China, Japan, Europe, and perhaps the United States grow through the addition of further links over hundreds of kilometers. Further demonstrations of satellite QKD may happen, and perhaps small proof-of-concept satellite networks. Commercial systems may find niche markets.
Disruptive
Convincing demonstrations of QKD implementations that provide high security in practice may lead to adoption in some specialized systems. Real-world demonstrations of quantum repeaters and quantum networks would be a significant technical achievement and could enable somewhat broader use. However, even a major technical advance would not be expected to have an overall disruptive impact owing to the underlying limitations of QKD.
Artificial Intelligence and Machine Learning
The fields of artificial intelligence (AI) and machine learning have made significant progress in recent years and are receiving an enormous amount of attention in the research community as well as growing real-world use. There are multiple ways that cryptography interacts with machine learning. A major one is the use of encryption to protect the privacy of potentially sensitive data used to train machine learning models. Cryptographic tools for computing on encrypted data like homomorphic encryption and multiparty computation can be used to train machine learning models on encrypted data, or to encrypt the models themselves.28 In applied security research, there has been significant recent work on adversarial machine learning, including attacks that fool machine learning models into making incorrect choices, or invert machine learning models to learn sensitive information about training data. Machine learning has been used in applied security applications, such as in anomaly detection for network data. Current applications to core areas of cryptography are more limited. Machine learning has been used to analyze side-channel traces, and a handful of works have explored using machine learning techniques to design or analyze ciphers.29
Predictable
A predictable set of advances would see the proof-of-concept demonstrations of privacy-preserving machine learning using cryptography to protect training data or the model becoming more sophisticated. It is unlikely but not impossible that machine learning would lead to significant new attacks on deployed cryptography. There may be academic proof-of-concept works using machine learning to optimize fast implementations, discover new side channels, or improve upon existing work learning differential paths or other areas of classical cryptanalysis.
There are also numerous cryptography-adjacent applications of machine learning to security more generally. For example, analyzing metadata, analyzing data decrypted owing to flawed cryptography or implementations, correlating unencrypted data sources with encrypted sources, optimizing computational clusters for cryptanalysis or data analysis, and so on. A predictable set of advances would see all of these applications grow more sophisticated and may also inspire additional work on cryptographic techniques to protect against these techniques.
Disruptive
A disruptive advance might be the development of an entirely new field of cryptanalysis based on machine learning that is able to find subtle flaws and biases in published cryptographic algorithms much more effectively
___________________
28 C. Juvekar, V. Vaikuntanathan, and A. Chandrakasan, 2018, “Gazelle: A Low Latency Framework for Secure Neural Network Inference,” arXiv.org, January 16, https://arxiv.org/abs/1801.05507.
29 A. Gohr, S. Jacob, and W. Schindler, 2019, “CHES 2018 Side Channel Contest CTF: Solution of AES Challenges,” Bundesamt für Sicherheit in der Informationstechnik (BSI), https://eprint.iacr.org/2019/094.pdf.
than the statistical/computational methods or human-driven mathematical analysis tools that are used to analyze algorithms today. A significant flaw or bias discovered in a deployed algorithm that could not be found by human analysis would be disruptive to the cryptographic community, because it would mean that a new set of analysis tools would need to be added to the analyst’s toolkit before a new algorithm could be trusted.
Dramatic advances in the ability of AI systems to write or analyze code, or to test systems, could make a mature systems future much more likely, by making it economically feasible to generate new and more reliable systems, or to find the flaws in existing systems.
SOCIETY AND GOVERNANCE DRIVER: GLOBALIZATION VERSUS FRAGMENTATION
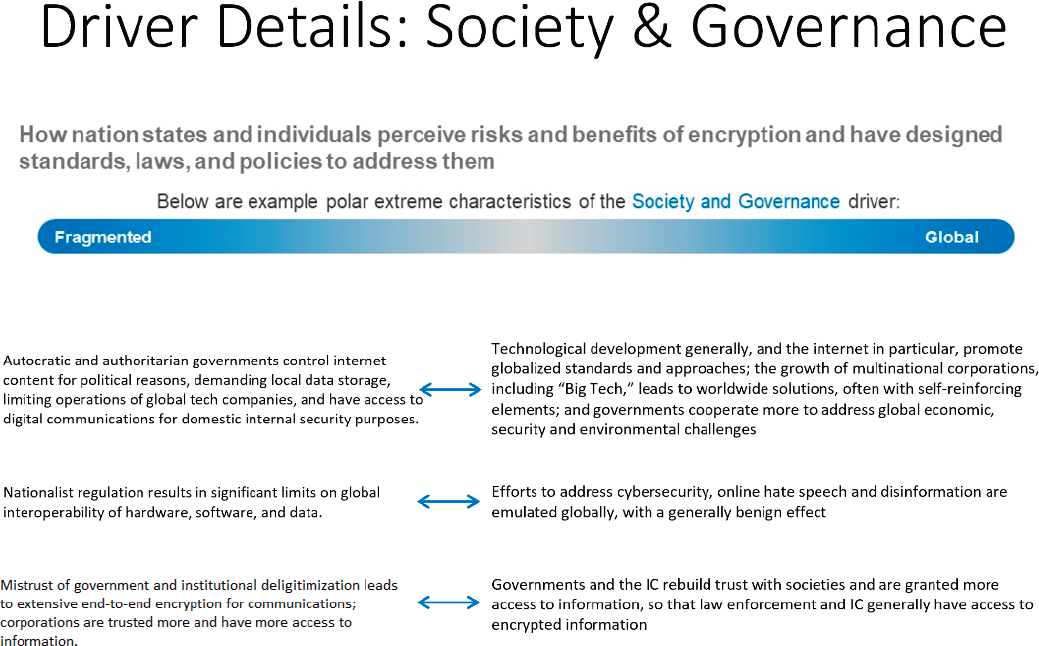
Figure 4.2 defines what is meant by the Society and Governance driver, and how a future would look if it existed at either extreme.
How countries and their citizens will perceive risks and benefits of encryption, and how in response they will choose to protect cultural values and develop local laws and policies, will obviously affect the future of encryption in both direct and diffuse ways. Although there are many facets to the Society and Governance driver, the committee believes that a critical differentiating feature will be the extent to which this driver leads to global convergence—resulting in countries around the globe taking similar approaches to the relevant issues—or fragment along national, cultural, or other geopolitical lines.
As a threshold matter, the Society and Governance driver presents three analytic challenges to a greater degree than some of the other, more technical drivers the committee considered:
- The Society and Governance driver tends to be inherently subjective, ambivalent, diffuse, and non-quantitative.
- This driver is often interrelated and does not operate in a mutually exclusive manner—for example, even in an extreme case of globalization, powerful countervailing trends for fragmentation will still be present. The very factor propelling one outcome may readily trigger the opposite result. (For example, disintegration of a country’s political structures might lead to a weak national government with local powers predominating and competing, but might also lead to a stronger, perhaps authoritarian national regime.)
- Even when a particular driver manifests itself strongly, the consequence for intelligence collection or defense might not necessarily be correspondingly clear. (For example, a globally common approach to technology regulation might mean that the Intelligence Community would need to devote fewer resources to solving access problems, because one success could presumably be easily replicated elsewhere; but it could also mean that all targets are similarly problematic and by definition there would be fewer weaker individual targets.) In other words, the relative strength of a particular aspect of the Society and Governance driver may not translate directly into a particular result for encryption or an unalloyed positive or negative outcome for the Intelligence Community.
The committee arrived at the decision to use the Society and Governance driver for its scenario planning, and within that, to explore globalization versus fragmentation, prior to the publication of the Global Trends 2040 report.30 Nonetheless, the committee believes that report presciently outlines the major themes and trends warranting consideration.31 Most significantly, it is worth noting that three out of the five themes expressly outlined in the report—fragmentation, disequilibrium, and contestation—all tend toward worldwide differentiation in a wide array of areas. Every one of the five scenarios examined by the report has strong, and in most cases, dominating elements of fragmentation and differentiation. Given the thorough discussion of broad societal drivers contained in Global Trends, the committee does not repeat that analysis, but instead supplements it here with a particular focus on how those drivers might manifest themselves in specific topics particularly relevant to encryption.
This section identifies and discusses what the committee believes to be the most salient drivers for globalization or fragmentation, which arise from a variety of sources. One dynamic, however, affects almost every part of the discussion: the rise of China as an economic, military, technological, and geopolitical power. Although China’s development is going to have a profound effect on the drivers discussed below, and the velocity of that rise is uncertain (and possibly unequal in various sectors), it is not clear whether the force of an ever-more potent China, and the rest of the world’s reaction, will automatically lead to globalization or fragmentation (although the latter seems more likely). Both globalization and fragmentation are discussed in depth below, but the committee nonetheless believed that the role of China in driving each of these two trends to be of such overriding potency that it warrants specific mention.
Last, the committee recognized that many of the factors tending toward globalization are offset by other factors pushing in the opposite direction even where both arise in the same context. The committee decided that it was better to organize this discussion by exploring the factors favoring globalization in one section and favoring fragmentation in another. Another option would have been to organize by subject area, and explore each area’s effects toward globalization or fragmentation, but this would have led to a more cumbersome presentation. The committee appreciates that presenting the factors separately is artificial because it is often the case that forces for both globalization and fragmentation are present at the same time in a single situation but believes that this approach may be more useful for the reader. Given that many of the concepts favoring globalization are straightforward and easily apprehended, the committee’s discussion starts with those concepts, and then separately considers fragmenting forces.
___________________
30 National Intelligence Council, 2021, Global Trends 2040: A More Contested World, Office of the Director of National Intelligence, March, https://www.dni.gov/index.php/gt2040-home, accessed October 21, 2021.
31Appendix D summarizes relevant points from the Global Trends 2040 report.
Factors Favoring Globalization
The Role of the Internet
The Internet—arguably the most transformational manifestation of the Digital Revolution—has directly fostered globalization, owing to its inherently open and interoperable nature. It has propelled the free and easy flow of information, ideas, and communications without regard to sovereign boundaries. Thus, everything from news to pop culture to products and services to political concepts (including democracy, populism, and authoritarianism) has the potential to reach a worldwide audience instantly. The resulting shared experience is itself a powerful cause of international commonality.
Many of the applications available via the Internet are expressly intended to operate across borders, with easy adaptation to multiple languages and services ranging from purchasing to messaging designed for multinational users. Although technically possible, it is difficult for a nation-state to filter Internet traffic selectively at its border, and the political, cultural, and economic downsides of blocking all or significant portions of Internet traffic for a country are substantial. As those cross-border factors are sustained, the Internet will continue to be a force for globalization.
More broadly, the fact that the Internet is a manifestation of global adoption of technical standards itself facilitates global approaches to electronic communications generally. Although the Internet was initially the product of U.S. national security research, its evolution and technical workings owe relatively little to direct government efforts, and far more to those of the private sector. Governmental involvement has consisted mostly of promoting global connectivity and interoperability—in the case of the latter, principally by supporting various international professional bodies that set technical standards, and by adopting the resulting standards in national regulation.
Moreover, many countries have not stopped encrypted communications at their borders—the Internet grew to its current scale without most national governments governing the technical workings of Internet traffic that transits, originates, or terminates in a particular nation. In addition, multiple telecommunication modes such as voice, video, data, and text messaging are highly interconnected, providing users additional channels for cross-border communication. By contrast, in the early days of telephony, countries imposed effective technical, geographical, and substantive limits—the communications of the Soviet Union and its Warsaw Pact allies, for instance, existed largely separate from communications networks of the United States and its allies.
Other Technological Developments
Although the Internet may be a particularly visible cause and effect of modern globalization, technological developments have also led to the globalization of trade in goods and services generally. Diverse sectors including financing, manufacturing, logistics and shipping rely on the ease and lower cost of cross-border communications (voice, video, and data). Many industry sectors have increasingly adopted common standards around the world. Although protectionist pressures exist in many settings, the broad trend has been for governments to support (or at least not oppose) expanding cross-border flow of goods and services.
In particular, supply chains for many hardware and electronics products have become highly global, especially since China entered the World Trade Organization in 2001. So, for example, owing to the Internet and global communications, as well as standardization, a product sold in the United States might be designed in Europe, manufactured in Asia with parts from various countries, shipped around the globe, and subsequently supported by a customer call center in India. Common standards in all these areas are likely to be more successful where there are unified approaches to communications (including encryption). Indeed, the adoption of English as the principal language of commerce, finance, and certain other endeavors (such as aviation) itself promotes worldwide commonality to a significant extent.
All of this globalization is principally the result of private sector endeavors; it is that sector, not the governmental one, that is mostly leading technological innovation because of economic motivation. As major corporations with worldwide operations dominate this innovation and associated delivery of products and services, this
contributes powerfully to globalization, and is likely to have an associated effect on encryption issues. By contrast, in an era in which individual governments lead or substantially regulate technological development, there is a greater likelihood of nationalistic approaches to such development.
As a corollary to the evolution of the worldwide Internet, there have been powerful trends toward global approaches to software and online services. U.S.-based companies have achieved widespread adoption globally for important categories of software, such as operating systems from Microsoft, Apple, and Google and social media platforms. In addition to proprietary software, which is now sold worldwide, open-source software is and will be important for a wide range of uses, and open-source software by its nature can be created or adopted anywhere in the world. Another important globalizing force is cloud computing, in which large processing and storage providers such as Amazon, Microsoft, Google, Salesforce, SAP, and many others afford customers around the globe the ability to store and use data in uniform ways. With software and cloud computing so often operating across borders, the advantages of interoperability create additional reasons to adopt international, and perhaps global, approaches for encryption, including for data in transit across borders.
Increasing reliance on satellites for communications and processing, including for remote monitoring for purposes ranging from climate change to agricultural production, will also propel the globalizing trends. Depending on whether adequate bandwidth can be available and transmitted and on the size of receiving antennas and the economics of low Earth orbit satellite constellations, it is possible that widespread Internet availability from satellites could sidestep or at least complicate national regulation of Internet access and could consequently promote globalization. While significant portions of satellite communications (both satellite to satellite as well as Earth connections) are currently not encrypted, in the future more elements of such communications might be encrypted; given the nature of those communications, there would be strong incentives to have globally common schemes.
Political Factors
There are, of course, numerous political institutions—mostly an outgrowth of World War II and partially in response to the Cold War—that expressly promote global and regional cooperation in matters ranging from security to trade, public health, and transportation, and to the extent those institutions continue to be effective, globalization will tend to predominate. In particular, as it relates to encryption, the “Five Eyes” intelligence sharing arrangement of English-speaking nations (i.e., the United States, the United Kingdom, Canada, Australia, and New Zealand), and their corresponding coordination in law enforcement, are also drivers toward greater emphasis on common approaches to encryption and intelligence collection generally.
More broadly, as nations seek to deal with common problems, they have historically pursued coordinated approaches, at least where consistent with national interests. Thus, global problems such as climate change, international terrorism, nuclear proliferation, and control of outer space might all elicit global approaches in a wider range of areas. The national security mission of the Intelligence Community appears to be expanding beyond traditional political and military adversaries to a greater array of such threats and vulnerabilities. The resulting increased responsibility might be made less onerous by reliance not only on the Five Eyes relationship (which itself could expand) but also on potentially numerous other like-minded nations seeking to address these global problems.
Self-Reinforcing Elements
Last, virtually all of the factors noted above as propelling globalization have strong reinforcing elements that deepen and expand the trend. On a simple level, the more a particular technology or standard is widely adopted, the more difficult or expensive it is for “holdouts” to persist with alternatives, and for competing approaches to arise and take hold. To some extent, this characteristic is true even of ideas and societal approaches; the past few decades have seen expansion of legal rules that protect human rights, including the rights of women and historically marginalized groups. Such protections suggest the possibility of globalization of world public opinion on important matters.
Factors Favoring Fragmentation
Even a casual reader of the preceding paragraphs would be quick to point out that there frequently is a countervailing trend for every factor tending to globalization. The committee does not attempt to detail every such trend, but again notes that this inherent duality or ambivalence is present in most aspects of the Society and Governance driver.
Potential for Misuse
Perhaps this duality, with its latent potential for abuse, is an aspect of the human condition and the way societies organize—but it is thrown into sharp relief by technology itself, which lends itself to later malicious use or reveals risks not fully appreciated at the time the technology was introduced. For example, when radio became common around the world in the 1920s, many observers thought that it would lead to world peace and initially viewed the invention as purely a benefit. Yet within a matter of years, totalitarian regimes in the Soviet Union and Germany used radio for propaganda. The same pattern is of course playing out today with the advent of (mostly previously underappreciated) cybersecurity risks and online maliciousness, as well as disinformation on the Internet.
The result of this greater appreciation of the inherent risks and the potential for misuse of modern communications systems supported by the Internet is in many cases a cause for national or local regulation. This is especially the case where there is a perception that effective global safeguards either do not exist, or are not tailored to support the country’s political, economic, or cultural concerns. At least at this point in the evolution of the Internet and given the current situation of global political competition and a rise in nationalism and populism, it seems that the forces arrayed against globalization and furthering national regulation are gathering strength. The extent of the recent different approaches taken by China and to a lesser extent even the European Union to a wide array of U.S. technology is illustrative of the strength of these forces.
Regulation
In their most benign manifestation, these anti-globalization forces take the form of national regulations to promote online competition, enhance cybersecurity, curtail hate speech, and protect citizens’ data privacy. The result can be a multiplicity of complex regulatory schemes that vary from nation to nation, which offset the predisposition of the multinational corporations that control the major online platforms (such as marketplaces, search engines, social media, payment systems) to operate in a uniform manner around the world.
There might, however, be some natural limiting element to this apparently benign regulation, because governments will be somewhat hesitant to curtail commercial enterprises that perform a useful and desired service. Consequently, regulation might turn out to be a somewhat weaker fragmenting force. On the other hand, to the extent that U.S. companies dominate social media, marketplace and communications aspects of the Internet, there could be a political backlash against perceived U.S. hegemony, and that might add fuel to the fragmenting forces. Both China and the European Union have separately sought to regulate U.S. social media, hardware and device manufacturers and online service providers in ways that require conformity to local rather than global rules.
Factionalism Fomented by Authoritarian and Autocratic Governments
By contrast, in its more nefarious form, the impetus for national control is a far more potent cause of fragmentation. The efforts on the part of regimes such as Russia, China, Iran, and Turkey to control content on social media platforms and to impose email censorship (along with extensive user surveillance) are the most visible manifestation of governmental pushback against the open and unregulated nature of the Internet.32 To the extent that this trend intensifies, it could entail the end of the World Wide Web, and the development of the “splinternet”—with individual countries or blocs of like-minded countries imposing substantive content requirements enabled by technological distinctions at national levels. This could include, for example, prohibiting or regulating virtual
___________________
32 Freedom House, 2021, “New Report: Global Battle Over Internet Regulation Has Major Implications for Human Rights,” press release, September 21, https://freedomhouse.org/article/new-report-global-battle-over-internet-regulation-has-major-implications-human-rights.
private networks (VPNs), banning end-to-end encryption (so as to permit government surveillance), or mandating a variety of governmental access to otherwise encrypted communications (perhaps through required turnover of encryption keys to authorities or insisting on the use of specified encryption schemes).
In the case of China in particular, it can be difficult to isolate the relative strengths of the various drivers that propel development of their own unique systems, including nationalism, the push for use of Mandarin throughout the nation, the strategic and economic goals of the Chinese Communist Party for China’s technological superiority, and the sheer mass of the country in terms of both geographic size and population. These are all factors that cause China to stand apart from the rest of the world. This is seen most readily with social media and online payment systems, where uniquely Chinese systems are extraordinarily pervasive within that country (e.g., WeChat has more than 1.2 billion users in China), and yet are not significant elsewhere (except among the Chinese diaspora). In any case, these drivers in one form or another are precipitating a fragmentation involving a fifth of the world’s population.
Indeed, to the extent China remains a rising, if not yet dominant, power, its sheer presence on the world stage is itself a fragmenting element. Seeking to control the internal communications of its own population, China is in the process of developing its own approach to communications, separate from the U.S.-dominated international system. Internationally, by promoting its own hardware, encryption, and software systems—often with financial incentives—China will have increasing influence over significant parts of the international system. For example, China started its own post-quantum cryptography algorithm standardization after NIST began its process. Limited to domestic submissions, China ultimately selected as winners one algorithm that had been submitted by a Chinese group to the NIST process but did not advance and two algorithms that are modifications of NIST submissions by an international consortium of researchers. China’s future success in this regard will probably be a function of geopolitical factors rather than purely technological or economic ones—but it is possible (if not probable) that large portions of neighboring Asia as well as Africa and Latin America might well use Chinese communications systems in addition to or in lieu of U.S. or European ones.
China’s emphasis on the development of its own technology and systems is principally the result of the country’s political and strategic goals, and to a lesser extent of the reluctance of Western nations to rely on Chinese technology generally on the basis of security concerns. For example, the recent rejection by the United States. and some of its allies of Huawei’s 5G telecom equipment may well be a harbinger of the type of global divisions that will arise over Chinese technology. Similarly, recent efforts to strengthen integrated circuit production in the United States, although not aimed exclusively at China, are illustrative of efforts intended to preclude eventual Chinese dominance in a critical technology and could lead to China and the United States utilizing different electronic components.
Mistrust of Governments
Negative aspects of the Internet—the presence of disinformation, the absence of uniformly recognized curated news sources, and the resulting de-legitimization of institutions—all reflect and lead to increasing distrust of authorities, whether democratic or otherwise. In particular, Western democracies have themselves been grappling with a rise in the mistrust of governments (including in the area of surveillance) and a corresponding growth in the use of encrypted communications (both to avoid government surveillance and in response to general privacy and security concerns).
In large part as a result of social media, many nations, whether democratic or not, have been coping with an apparent rise in domestic extremism, with a seeming prevalence of conspiracy theories. In this regard, the availability of encryption affords extremist citizens’ groups the ability to organize quickly and effectively, posing a threat to domestic order. A few agencies within the Intelligence Community that have a law enforcement function do have specific responsibility for collecting certain types of domestic intelligence within the United States; in addition, any ensuing increase in civil unrest among our allies and even adversaries might complicate or increase intelligence collection demands.
In the case of more authoritarian regimes, the potential for more encrypted communications is likely to lead a government mistrustful of its own citizens to ban or curtail effective encryption. Even in the case of democratic
nations, the rise in the average citizen’s use of encrypted communications increasingly has an effect on government’s access, subject to applicable legal process (“exceptional access”), to the content of (and, in some cases, metadata about) communications. In general, such access could be expanded either because authoritarian regimes seek greater surveillance over their citizens, or because a more trusting or complacent citizenry is willing to accept such access as a price of greater perceived security and safety.
It is not clear that there is even a unified approach to the issue of exceptional access among the Five Eyes countries; at least some of the non-U.S. members have either adopted or are contemplating approaches to exceptional access which mandate that communications and device providers make available non-encrypted content upon relevant legal process. Indeed, it is possible, if not likely, that an increasingly fragmented outcome on this point could result. The implications for intelligence collection range from complexity and demands for greater resources to cope with more variegated targets, to possible ease of intelligence collection to the extent exceptional access schemes can be exploited. (See Box 4.3 for a further discussion of exceptional access and metadata.)
Economic and Security Concerns
Nations worry about not only content control but also perceived invidious economic advantages relative to other nations and their own national security risks arising from technology. The COVID-19 pandemic and recent cyber hacks from foreign sources have produced an increasing recognition in the United States that the country’s well-being is more profoundly than ever dependent on the actions of other nations. There are now significant and growing policy debates about the extent to which nations and their allies should seek their own rules nationally—in opposition or at least without regard to those of other nations—to govern hardware, software, and data.
Economic competition and protectionism are likely to be factors promoting nationalistic solutions to communications technology, including encryption. These solutions could be seen especially as the United States and China seek economic hegemony, but also as the European Union seeks through antitrust and privacy regulation to limit U.S. technological dominance.
Another product of technology, cryptocurrency, presents additional challenges to governments. In particular, governments’ inability (for technical or political reasons) to regulate cryptocurrencies could promote illegal activity generally, undermine taxing efficiency and support fragmenting forces throughout the global economy.
As to the national security concern, the U.S. reaction to Huawei’s central involvement in 5G rollouts throughout the world—raising fears of Chinese government surveillance and collection of data—is a recent and highly visible example of how nations might address “supply chain risk” presented by hardware and software. That surveillance risk, augmented by general cybersecurity concerns arising from foreign cyber malefactors (as seen in the Solar Winds and Colonial Pipeline hacks of late 2020 and early 2021), are likely to solidify nationalist approaches in the United States and Western nations to cybersecurity risk management and encryption.
Apart from the effects of diverging developments in technology and the international standards that guide those developments, traditional economic and geopolitical forces might inevitably lead to a more fragmented world. Just how potent, and possibly irreversible, these forces of fragmentation might be is highlighted by the speed and scope of Russia’s expulsion from much of the Western economy following the Ukrainian invasion and the extent of Russia’s significant internal disengagement from Western news and social media. At the time of this report, it may be too soon to make a definitive judgment, but the profound international reaction to the Ukraine crisis may be a harbinger of future fragmentation. More broadly, traditional economic and geopolitical forces, coupled with the rise of China, could lead to the realignment of the 70-year-old postwar international system, and the concurrent diminution (for both domestic and international reasons) of U.S. leadership. The effect of this on encryption could be diffuse but pervasive. For example, political changes within the Five Eyes, as was the case with New Zealand nuclear policy in the 1980s, might weaken the alliance. Differing views on privacy and intrusion might also create future friction. The growth of regional blocs that join in taking different approaches to trade and regulation might also increase fragmentation.
Such a realignment could yield an international situation governed less by largely unchanging common interests than by ad hoc, transactional considerations—which in turn could make planning for the Intelligence Community more problematic. This could present novel challenges—in management, resource availability and
allocation, and recruiting, among other things—for the Intelligence Community, which since its inception at the end of World War II has been focused for decades on a single critical problem set during the Cold War and, for the past two decades, on counterterrorism. Moreover, a significant component of the Intelligence Community’s mission in the future will entail open-source information, requiring significantly greater involvement of the private sector that both holds much of that information and has the expertise to analyze it.
The increasing calls, notably from Europe and India, and more recently China, for nations to have protective ownership interest in the data of their citizens and businesses based on national security, privacy concerns and other grounds—so-called data sovereignty—are likely to have an effect on encryption and lead to more local control. Especially in Europe, notions about privacy and marketplace competition that differ from U.S. views are behind significant proposed restrictions on cross-border data flow and the regulation of online services.
It is easy to see how this could produce different approaches to encryption as well as data transmission and storage—but the effects on the Intelligence Community are mixed. For example, a requirement banning cross-border transfer of certain data and requiring in-country storage and processing might produce fewer opportunities for surveillance by interception in transit; on the other hand, it might facilitate surveillance because of the consolidation of target information in potentially accessible cloud or server storage controlled in the relevant nation. That might be offset, however, by requirements for local data storage that are often coupled with elevated cybersecurity standards, which could frustrate U.S. Intelligence Community access.
Cryptocurrencies potentially may create large disruptions in what information is available to governments, including intelligence agencies. The section above on Scientific Advances discusses technological developments related to cryptocurrencies and provides a brief discussion of policy-related issues. A full analysis of the possible regulations concerning cryptocurrencies is beyond the scope of the current study, but this report will briefly discuss possible impacts from low or high levels of such regulation.
If there is a low level of government regulation of cryptocurrencies, then many payments will be difficult or impossible to track by intelligence agencies or government agencies generally. Scientific advances might disable a particular cryptocurrency, but as long as cryptography works at all there will be ways to use it for payments that may be difficult or impossible to track. In the absence of financial records accessible to government, cryptocurrencies can be used to enable ransomware, money laundering, terrorist financing, financial sanctions evasion, and other criminal activities. Historically, regulatory regimes such as anti-money laundering efforts have tended to expand their coverage over time, as criminals have used unregulated cash-like instruments in place of regulated instruments such as cash or checking accounts.33 Cryptocurrencies may also be used to place income and assets outside of the tax reporting system, potentially substantially reducing compliance with national taxation requirements. To the extent that cryptocurrencies evade such regulatory efforts, then intelligence agencies will have reduced access to financial information and finance-related illegal activity may increase significantly.
In the low-regulation scenario, there are market and technological factors that may lead to varying levels of growth in cryptocurrencies. In financial markets, enthusiasm about growth in cryptocurrencies has spurred rapid growth in investments in the sector, with total market capitalization above $2 trillion in early 2022.34 In contrast to this scenario of rapid and sustained growth, government officials and others have expressed the view that cryptocurrencies are Ponzi schemes,35 where early investors get high returns as total investment grows, but later investors lose their funds as the number of new investors diminishes. If the risk of such losses becomes large enough, then investment in cryptocurrencies may flatten or even decline over time. Along with these market unknowns, there are technological unknowns. As the sector grows, so does the incentive for attackers to steal or otherwise attack existing cryptocurrencies. Such attacks may be on the algorithms at heart of cryptocurrencies; in addition, as with cryptosystems generally, attacks may be possible even if the algorithms themselves remain resistant to attacks. In
___________________
33 For example, casino chips were transported across national borders and cashed in a different jurisdiction, and so money laundering laws expanded to cover casino chips. P. Swire, 1999, “Financial Privacy and the Theory of High-Tech Government Surveillance,” 77 Washington University Law Quarterly 461.
34 C. Morris, 2022 “Crypto Market Cap Is Once Again Above $2 Trillion,” Fortune, March 2, https://fortune.com/2022/03/02/crypto-market-cap-2-trillion.
35 M. Singh, 2022, “Cryptocurrency Is Akin to ‘Ponzi Scheme’ and Banning It Is ‘Perhaps the Most Advisable Choice,’ Says India’s Central Bank,” TechCrunch+, February 15, https://techcrunch.com/2022/02/15/india-central-bank-cryptocurrency-ponzi-banning.
many settings there are weaknesses in the implementation of cryptosystems, so that attacks can succeed even if the encryption algorithm remains strong. The technological risk of successful attacks means there is uncertainty about future growth in cryptosystems, similar to the market risks if fraud grows too high or new investors shun the sector.
High government regulation may limit the growth and use of cryptocurrencies, in addition to possible limits on growth owing to market and technological factors. Governments have at least two regulatory strategies available to limit growth of cryptocurrencies outside of the traditional banking system. First, governments may make it expensive or illegal to convert from a cryptocurrency to the national currency, such as by prohibiting payments in cryptocurrencies to banks and other significant economic actors. Second, governments may issue and support (such as by regulation) a government-issued cryptocurrency. Under either approach, a larger fraction of transactions would remain visible to intelligence and other government agencies, and thus available for investigations into money laundering and other criminal activity. Early examples of government limits on cryptocurrencies include China’s 2021 ban on Bitcoin and Japan’s prohibition on use of anonymous cryptocurrencies.
This high level of government regulation could help combat crime but may also be accompanied by expanded government surveillance generally of financial activity. The multi-decade shift toward electronic financial transactions has already allowed companies and governments to track individuals and transactions at fine granularity. This trend toward financial surveillance may expand considerably with government-issued cryptocurrencies, or prohibition on use of privacy-protecting cryptocurrencies in commerce. High levels of financial surveillance would be contrary to the trend in many countries to provide expanded protection of personal privacy, against both corporate and government access to personal information. Defenders of financial privacy can point to historical abuses, including mandatory reporting in Nazi Germany of Jews’ financial assets, as a step toward eventual seizure of such assets.36
FINDING 4.3: It is difficult to predict what mix will occur of low or high levels of government regulation of cryptocurrencies. Low levels of regulation will be subject to criticism for facilitating criminal activity. High levels of regulation will be subject to criticism for excessive surveillance. Market and technological factors further make it difficult to predict future growth in the sector. Of this uncertainty, it is also uncertain the extent to which intelligence agencies will retain, increase, or decrease their access to financial, transactional information.
Climate Change
Last, on a more diffuse and speculative note, the effects of climate change, such as rising seawater levels and shifts to alternative energy production, might lead to a proclivity for local responses and adaptation. This could include possible reluctance by some countries to fund efforts to mitigate the effects in other countries. Moreover, countries might seek to address the resulting challenges in a national way given that the problem manifests itself in a territorial manner and the fact that effective global solutions are not immediately apparent or within reach.
FINDING 4.4: Forces for both globalization and fragmentation will be present. Even if the committee were in a position to predict whether globalization or fragmentation were more likely to prevail, these trends are complex and interrelated. Some trends reinforce themselves and others prompt opposite reactions. Thus, it is difficult to determine which forces are likely to prevail on any given issue. In theory, this means that the Intelligence Community will need to be prepared for alternative extremes—for example, a world in which authoritarian governments weaken or ban encryption in ordinary communications, and a world in which governments support pervasive use of encryption citing privacy and security concerns. Because that preparation is impossible to sustain over any meaningful period, there will be a premium on accurate detection of trends at the earliest possible stage and managing the risk of an incorrect assessment.
___________________
36 P. Swire, 1999, “Financial Privacy and the Theory of High-Tech Government Surveillance,” 77 Washington University Law Quarterly 461.
FINDING 4.5: The Internet and increasing technological interdependence promotes globalization. The shared experience of individuals around the globe owing to information and communications being instantly and ubiquitously available is a powerful cause of international commonality. That factor, along with convergence of technologies, ever increasing global interdependence on all levels and across economic and political sectors, the continued growth of world trade and the expected increase in the role of the private sector, with its constant drive for efficiency and common standards, will tend to powerfully mold the world in a unified way, increasing the likelihood that nations around the world will take common approaches to issues relevant to encryption.
FINDING 4.6: Governmental regulation, for better or worse, of communications technology may lead to fragmentation on national lines. National security concerns have the effect, whether specifically intended or not, of creating competing national technologies—by limiting the exports of sensitive technology or by curtailing imports of equipment that may permit surreptitious surveillance by a foreign manufacturer or its government. Potent forces are present, for both beneficial and malicious reasons, that could predispose the global arrangement toward individual nationalistic or regional solutions to issues bearing on encryption. In many countries, there is growing support for “digital sovereignty,” a term that can mean various things ranging from having regulatory decisions made nationally instead of by Silicon Valley, and support for protectionist trade policies, to segmenting the Internet by blocking communications with other countries. In addition, national regulations to promote online competition, enhance cybersecurity, curtail hate speech, and protect citizens’ data privacy might well vary significantly around the globe and even in geopolitical regions where there might otherwise be commonality. A rise in citizens’ mistrust of governments (especially in the area of surveillance) might lead to a corresponding growth in the use of encrypted communications (both to avoid government surveillance and in response to general privacy concerns). Moreover, individual countries or blocs of like-minded countries might impose (or continue to impose) substantive communications content requirements enabled by technological distinctions at national levels, including, for example, banning or discouraging end-to-end encryption (so as to permit government surveillance), or mandating a variety of governmental access to otherwise encrypted communications (perhaps through required turnover of encryption keys to authorities or insisting on the use of specified encryption schemes).
FINDING 4.7: In most cases, a common set of security protocols and cryptographic algorithms are used globally, and systems and networks today are largely interoperable. This may not remain the case; the factors that led to this interoperability are weakening, and pressures to create national and regional differences are growing.
Society and Governance Driver Summarized
Box 4.1 presents the considerations for the future of online communication and the two endpoints of globalization and fragmentation.
As will be seen in Box 4.2, increased fragmentation could affect the U.S. Intelligence Community in multiple ways, determined by governmental and societal changes. Box 4.3 expands on a possible future in which drivers create a situation in which communications “go dark.”37
SYSTEMS DRIVERS: CHAOTIC VERSUS MATURE
The systems driver addresses the issues associated with the development and operation of technology products and systems that embed encryption. The extremes of the systems driver are chaotic and mature. Figure 4.3 defines what is meant by the systems driver and how a future would look if it existed at either extreme.
___________________
37 R. Knake, 2020, “2019: The Beginning of the End of the Open Internet Era,” Council on Foreign Relations, January 6, https://www.cfr.org/blog/2019-beginning-end-open-internet-era.
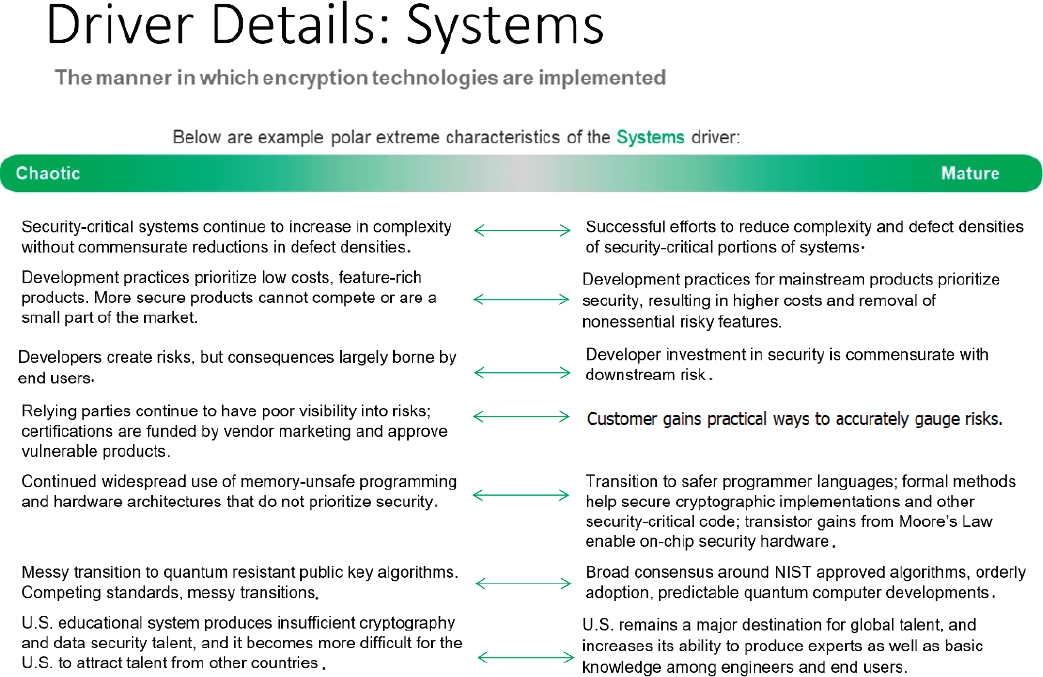
Most attacks that compromise cryptographic systems exploit implementation weaknesses. This is partly owing to the strengths of cryptography; widely used algorithms are typically based on well-researched mathematical problems, designed with large safety margins, and carefully reviewed before gaining trust. In contrast, the security-critical elements of a typical computer system are so large and complex as to virtually ensure the presence of errors that lead to exploitable vulnerabilities.
The balance between systems-related risks and algorithm-related risks has shifted over the past decades. Moore’s law and related advances have enabled a dramatic decrease in the cost of computation and a corresponding increase in the complexity of computation systems. Historically, cryptographic algorithms were severely constrained by the limited computational complexity that was practical during encryption and decryption, and as a result were often breakable. In the 1980s, constraints on computation power started to ease, but export control regulations, the 56-bit key size of the Data Encryption Standard (DES)38 and general unavailability of cryptographic knowledge limited the strength of most commercial implementations.
Today’s systems fail as a result of exactly the opposite problem; the underlying algorithms are extremely robust, but complexity in the systems that use them results in vulnerabilities that adversaries routinely exploit to break or bypass the cryptography. The real-world security properties of systems are typically determined by the weakest link—and there is a lot of room for mistakes. Typical computing devices today comprise billions of transistors and millions of lines of software distributed across operating systems, firmware, device drivers, software
___________________
38 The first encryption algorithm standardized by NIST for use by the private sector and the civil agencies of the U.S. government was called the Data Encryption Standard, commonly referred to as DES.
libraries, and application code. Trends for greater network connectivity, more sharing of resources between tasks, and exposure of more sophisticated programming interfaces enable cost savings and powerful features, but also make vulnerabilities more likely and more exploitable. The complexity and defect densities for typical computing systems today are sufficiently high that vulnerabilities are essentially certain.39 Unless there are reductions of many orders of magnitude in complexity and/or defect densities, vulnerabilities will remain widespread.
Security vulnerabilities are different from other kinds of defects. Normal bugs result in observable misbehavior that motivates remediation efforts. For example, if an important system fails to boot or crashes, people will notice and fix the problem. By contrast, security flaws tend to be invisible to developers, to testers focused on the functioning of system features, and to end users. Excess complexity makes vulnerabilities even harder to find; even vulnerabilities that seem glaringly obvious once highlighted often lie undiscovered for years in neglected parts of a codebase that work well for non-malicious inputs. In addition, fixes for non-security bugs are individually beneficial, and provide benefits that scale with the number of bugs fixed. In contrast, security efforts are more like trying to make a sieve watertight. If a product has thousands of security bugs, a security effort that fixes 75 percent would appear successful in terms of the number of vulnerabilities, yet might make no practical difference if attackers still have plenty of ways in. Security bug responses can also be chaotic, and therefore more prone to introducing new problems, as developers must rush to implement fixes before vulnerabilities are exploited (or to stop an active attack). Information technology (IT) departments receive updates from numerous vendors and face a constant, and often overwhelming, deluge of urgent fixes. Even planned updates to introduce new security measures can impose costs on end users, such as usability challenges associated with extra authentication steps.
Of course, defenders also strive to reduce risk. These efforts include fixes to specific security bugs, broader mitigations for specific categories of attack, and monitoring of operational systems to help detect or block intrusions. This results in an ongoing “tit-for-tat” dynamic, where offensive efforts try to evade defenses, and defensive efforts try to mitigate attacks. While some kinds of defensive responses can occur quickly, others can take many years because new research is needed, hardware has to be replaced, or the vulnerability arises from upstream components in complex supply chains. At a higher level, perceptions of risk and externally imposed requirements determine each organization’s willingness to accept costs, reduced functionality, inconvenience, and other trade-offs in pursuit of security initiatives. In theory, market forces might create some semblance of a balance between offense and defense over longer periods of time, but the level of investment will likely reflect the cost/benefit trade-offs for development organizations—who have traditionally been mostly isolated from the damage that breaches cause to downstream organizations and individuals. Furthermore, unlike risks such as credit card fraud where rates can be monitored and managed over time, attackers exploiting systems vulnerabilities often combine stealth or surprise with speed to make enormous gains before defenders can react. Such issues are especially acute in IoT systems where cyber-physical attacks have the potential to damage real-world equipment such as components of electrical grids or transportation systems.
Chaotic Versus Mature Systems
The Systems driver concerns the security properties of systems using cryptography. These properties include the security logic itself, such as algorithms, protocols, hardware, and software. A great deal of software whose purpose is unrelated to security is also included because it may harbor bugs (such as buffer overflow vulnerabilities) that attackers can use to bypass or break the cryptography or other security mechanisms. The Systems driver also considers the development and operation of systems, including practices and tools such as software engineering, testing, key management infrastructure, operator knowledge and training, monitoring systems, code update/remediation capabilities, and acquisition processes.
The “chaotic” extreme represents hardware/software systems and development methodologies that are likely
___________________
39 O.H. Alhazmi, Y.K. Malaiya, and I. Ray, 2006, “Measuring, Analyzing and Predicting Security Vulnerabilities in Software Systems,” Computers and Security, https://doi.org/10.1016/j.cose.2006.10.002.
to result in exploitable security vulnerabilities. A chaotic scenario may involve development teams making liberal use of third-party hardware and software components without thorough security diligence, programmers working without security experience or guidance, rapid addition of new functionality requested by customers without careful consideration of security implications, and high complexity in security-critical components. The operators and administrators of chaotic systems may be inattentive to security practices or overwhelmed by the task of managing the systems securely. Vendors producing chaotic systems often have poor awareness of risk and may advertise false or misleading security claims out of ignorance or self-interest. Ignoring security, chaotic approaches can offer large benefits for customers, including low costs, rich feature sets, and rapid upgrades.
The “mature” case assumes development processes designed to minimize the likelihood and impact of vulnerabilities. The number of security defects in a system scales with both the complexity of the system (e.g., lines of code) and the defect density (e.g., defects per line of code). As a result, “mature” scenarios require combining technical and human measures to reduce defect densities with a commitment to controlling the complexity of security-critical components. These reductions will invariably involve significant trade-offs, such as omitting desirable features (or disabling them by default), accepting performance overhead from technologies that isolate sensitive computations and data, and spending a lot more time and money on development and testing.
With some notable exceptions, today’s systems are chaotic. Mainstream CPUs, operating systems, and major applications are so complex that even today’s more careful development teams have no realistic chance of producing vulnerability-free designs. The effort required to find vulnerabilities is often within the capabilities of a determined and skillful individual, and probably always within the capabilities of a sophisticated nation state or other advanced persistent threat.40
Factors Leading to Chaotic or Mature Systems
The prevalence of chaotic systems is not owing to malice; technology companies do invest in security and would like to do better. However, the dominant factors driving technology development today strongly favor chaotic systems. Market share and profits are driven by characteristics of chaotic systems, including fast time to market, rich feature sets, and low development costs. The costs of insecurity and the operational burden of security measures that do get adopted largely fall on users rather than developers. Developers’ economic incentives to sacrifice time-to-market and product features for security are comparatively weak, such as the desire to avoid bad publicity and customer complaints. Chaotic vendor-operated services (such as cloud applications) face similar pressures, although customers have a somewhat different mix of burdens and have less visibility into server-side vulnerabilities and operational risks.
Information asymmetries between developers and relying parties also favor chaotic systems. The security risks of technology products are often opaque to end users, so customers cannot easily compare products. Developers have strong commercial incentives to claim trustworthiness, and rarely face penalties for touting the security of vulnerable products. Customers’ pricing expectations reflect the cost required to implement new functionality, not the (potentially far greater) costs of mitigating the risks created by the added complexity. If markets for technology products or government regulations do not place sufficient value on mature systems (or if customers cannot tell the difference or are unable to switch), vendors who produce them will fail or be relegated to high-priced niche offerings.
Technical advances that make mature systems easier to develop could result in significantly different outcomes. In addition, economic, political, and regulatory factors (as might be imposed after a humanitarian disaster caused by a computer security failure or if the number of small disasters becomes large enough that a major government
___________________
40 The Defense Science Board report on Resilient Military Systems provides a useful perspective on adversary capabilities. See Department of Defense, 2013, Task Force Report: Resilient Military Systems and the Advanced Cyber Threat, Defense Science Board, Office of the Under Secretary of Defense for Acquisition, Technology and Logistics, Washington, DC, January, https://dsb.cto.mil/reports/2010s/ResilientMilitarySystemsCyberThreat.pdf.
decides to take dramatic action) could also change the equilibrium; such factors might vary by country because they would likely be defined by national interest, including legislation.
Improving System Security
The following sections discuss potential drivers that could change the status quo and make systems more mature.
Incentives, Transparency, and Development Process
Developer “Skin in the Game”
The direct costs of security breaches today overwhelmingly fall on end users. Although security outcomes can affect technology developers’ reputations, the effects are small enough that security initiatives tend to be very limited in their ability to affect development time, costs, performance, or features. Security investments would likely increase if legal or regulatory changes shifted liability to vendors—but such a shift could also bring enormous downsides, depending on nuances such as how liability is allocated. For example, the consequences of a security vulnerability depend on numerous contributing factors, such as whether (or which) adversaries discover the issue, how quickly it is fixed, end-user actions outside the developer’s control, and so on. Liability obligations would particularly affect low-cost or free/open source software developers as they do not have a revenue source to fund either security efforts or the liability. Still, some countries may impose liability obligations anyway.
Metrics, Transparency, and Disclosure
End users generally cannot accurately assess the security properties of technology products. Even when the source code and design documents are available, it takes substantial effort and expertise to perform a meaningful security evaluation. Optional or mandatory disclosure rules for vendors might help, but it is difficult to design rules that provide meaningful insights and encourage improvements, rather than devolving into paperwork exercises. If disclosures matter (i.e., affect customer behavior), then vendors will try to maximize their competitive advantages, and some will prioritize security resources on efforts that boost their scores over better ways to improve security. Some will be even more aggressive in seeking competitive advantages—for example, undermining competitors’ scores, litigating if they do not like their score, and lobbying for changes in the system itself.
Third-party certifications also face difficult conflicts of interest; evaluations are typically funded by vendors, so evaluation schemes and testing labs survive by minimizing evaluation costs and approving products. If a metric gains enough traction to affect customer behavior, vendors will invariably seek competitive advantages by using the same sorts of tactics that they would use in response to traditional metrics such as performance benchmarks. Still, imperfect approaches may prove beneficial. The Biden administration’s 2021 Executive Order 14028 seeks to make a start by requiring that vendors to the U.S. government implement a relatively specific set of practices during development and be prepared to show artifacts demonstrating their implementation to government customers. Although government efforts to mandate product security have historically met with limited success,41 industry response to the Executive Order has been relatively positive and the Executive Order will likely cause vendors to the government to adopt these practices.42
___________________
41 S.B. Lipner, 2015, “The Birth and Death of the Orange Book,” IEEE Annals of the History of Computing, April–June.
42 See the agenda, summary, and position papers for the NIST workshop in response to the Executive Order at NIST, 2021, “Workshop and Call for Position Papers on Standards and Guidelines to Enhance Software Supply Chain Security,” updated June 11, https://www.nist.gov/itl/executive-order-improving-nations-cybersecurity/workshop-and-call-position-papers.
Secure Development Processes
Many software vendors have sought to improve the security of their products by instituting development processes that specify security-related requirements for development teams.43 Those range from threat modeling to discover design-level vulnerabilities44 to specific requirements, such as tools, coding constructs, and libraries. These processes typically combine human activities (such as code reviews) and automated tools (such as static analysis and fuzzing tools, as discussed below) to detect potential vulnerabilities and to assess whether delivered code meets the process requirements.
Secure development processes aim to help organizations pursue continuous improvement: the root causes of reported vulnerabilities are investigated and, where feasible, process requirements, tools, and developer training are updated to prevent the recurrence of similar vulnerabilities. Over time, the application of secure development processes has enabled organizations to reduce the frequency and severity of reported vulnerabilities.45
There are challenges to the adoption of secure development processes. Organizations with limited resources may not be able to invest in creating a process or acquiring and tailoring the necessary tools. In other cases, projects may not prioritize security or lack the centralized control necessary for consistent adoption of a secure development process. However, adoption of such processes continues to grow in response to customer pressure and U.S. government requirements (see discussion of Executive Order 14028 below).
Technologies for Improved Security
Advances in Formal Methods
Formal methods is the name given to the application of mathematical techniques to prove the correctness and other properties of software. Although proven-correct software requires specialized skills to develop, and far more labor than conventionally developed software, some cryptographic algorithm and protocol implementations are relatively well suited to formal verification. If current progress continues, formally verified high-performance open-source libraries fully implementing protocols such as SSL/TLS (including the cryptographic algorithms, protocol handling, certificate processing, etc.) could be developed.
However, formal verification methods are not currently able to scale to the complexity of today’s typical computing systems. A good example is Sel4—a secure operating system kernel that has been formally verified.46 Although an important effort, Sel4 has less than 0.1 percent as many lines of code as the Linux kernel and lacks much of the functionality found in a typical operating system.
Vulnerabilities can hide in gaps between proofs and reality. Still, a breakthrough that allowed the economical application of formal methods to larger software systems could significantly change the security of the products that people and organizations use. Even incremental progress in the field might lead to improvements that would make attackers’ search for vulnerabilities more difficult.
___________________
43 NIST, 2022, “Secure Software Development Framework,” Computer Security Resource Center, Information Technology Laboratory, updated February 3, https://csrc.nist.gov/Projects/ssdf.
44 A. Shostack, 2014, Threat Modeling: Designing for Security, John Wiley & Sons, Indianapolis, IN.
45 M. Miller, 2019, “Trends, Challenges, and Strategic Shifts in the Software Vulnerability Mitigation Landscape,” presentation at BlueHatIL, February 7, https://github.com/microsoft/MSRC-Security-Research/tree/master/presentations/2019_02_BlueHatIL, accessed October 15, 2021.
46 G. Heiser, 2020, “The SEL4 Microkernel: An Introduction,” Revision 1.2 of 2020-06-10, The sel4 Foundation, https://sel4.systems/About/seL4-whitepaper.pdf.
Memory-Safe Programming Languages and Development Tools
Memory safety bugs cause the majority of vulnerabilities in many large software projects (including Microsoft’s product lines,47 Android,48 Chromium,49,50 iOS, MacOS,51 Ubuntu Linux,52 and Firefox53). Operating systems, device drivers, software libraries, and other critical software are largely written in programming languages that lack memory safety, and memory safety programming errors continue to cause a very significant fraction of product security vulnerabilities. For example, a single missing bounds check on an array access in the C programming language can allow attackers to compromise an entire process (including logic and data never legitimately accessed by the buggy function).54 More modern programming languages have the potential to reduce dramatically the harm of these and many similar software bugs. Today, many software teams are transitioning to the Rust programming language, which can guarantee memory safety at compile time.
Static Analysis and Fuzzing
Static analysis tools identify potentially vulnerable code patterns in software, while fuzzing tools repeatedly execute software with varying inputs to detect memory safety violations or other misbehavior. These tools are used by many software development teams and have identified many vulnerabilities in commercial and open source products. The widely used tools identify suspicious code patterns but can miss some vulnerabilities. In contrast, “sound” static analysis tools are guaranteed to catch all vulnerabilities within the categories addressed by the tool, but for most programming languages they are not widely used today as they tend to find large numbers of false positives that are time consuming for developers to address. Executive Order 14028, mentioned above, effectively requires that developers use static analysis tools and fuzzing as they build software that will be sold to the U.S. government. Improvements in static analysis and fuzzing tools are important, and sound tools in particular could have a large impact if they can be designed with acceptable false positive rates.
Hardware Security Advances
Hardware security plays a major role in many applications of cryptography. For example, tamper-resistant hardware can help protect cryptographic secrets from adversaries who steal or gain access to physical devices. Within complex systems, cryptographic operations can be implemented in enclaves or other hardware that operates independently from more vulnerable elements such as the main CPU, memory, and operating system. In other cases, cryptographic accelerators or specialized CPU instructions may improve performance or power consumption but do not add any extra protection.
Cryptographic hardware can take many physical forms, ranging from tiny logic blocks on a larger semiconductor chip to large appliances. Some technologies also blur lines between hardware and software. For example, the security may appear to be isolated in hardware, but in practice depend on firmware, microcode, FPGA bitstreams, or other externally supplied configuration data. If done well, cryptographic capabilities implemented in dedicated silicon, where security-critical logic is not shared with untrusted operations, can provide the highest levels of security. At the same time, backdoors in hardware are extremely difficult to detect.
___________________
47 MSRC Team, 2019, “A Proactive Approach to More Secure Code,” Microsoft Security Response Center, July 31, https://msrc-blog.microsoft.com/2019/07/16/a-proactive-approach-to-more-secure-code.
48 J. Vander Stoep and C. Zhang, 2019, “Queue the Hardening Enhancements,” Google Security Blog, May 9, https://security.googleblog.com/2019/05/queue-hardening-enhancements.html.
49 K. Serebryany, 2018, “Hardware Memory Tagging to Make C/C++ Memory Safe(r),” Github, December, https://github.com/google/sanitizers/blob/master/hwaddress-sanitizer/MTE-iSecCon-2018.pdf.
50 The Chromium Projects, “Memory Safety,” https://www.chromium.org/Home/chromium-security/memory-safety, accessed October 15, 2021.
51 P. Kehrer, 2019, “Memory Unsafety in Apple’s Operating Systems,” July 23, https://langui.sh/2019/07/23/apple-memory-safety.
52 Ubuntu Security, 2020, “USN-4360-1: json-c Vulnerability,” May 14, https://ubuntu.com/security/notices/USN-4360-1.
53 D. Hosfelt, 2019, “Implications of Rewriting a Browser Component in Rust,” Hacks.Mozilla (blog), Mozilla, February 28, https://hacks.mozilla.org/2019/02/rewriting-a-browser-component-in-rust.
54 MSRC Team, 2019, “A Proactive Approach to More Secure Code,” Microsoft Security Response Center, July 31, https://msrc-blog.microsoft.com/2019/07/16/a-proactive-approach-to-more-secure-code.
Improvements in semiconductor technologies have dramatically reduced the costs of adding security-focused logic into chips. As a result, large chips can combine many processors, some of which may be dedicated to security functions. Discrete devices for tasks such as network encryption, key management, user authentication, and security monitoring would fill a large rack and cost thousands of dollars. Implementing the same logic as isolated on-chip logic blocks adds negligible manufacturing cost—in addition to providing superior power consumption, convenience, and tighter integration.
Semiconductor advances are the most beneficial in areas where security can be improved by adding logic to devices. For example, adding memory encryption can reduce the need to trust external DRAM, and CPU features like CHERI55 can reduce the exploitability of programming errors. Enclaves and related software isolation mechanisms are also an area of active interest, although designs that share large amounts of circuitry between protected and normal modes have struggled with vulnerabilities arising from the large attack surface area. As transistor prices fall, the cost incentive to reuse circuitry will decrease, while allowing chip vendors to add many security blocks optimized for different use cases and customers. The costs of logic implemented in hardware and software will also become more similar, where the up-front engineering costs dominate while the incremental costs of manufacturing and distributing the logic become negligible.
Application-Specific Solutions
Even if the bulk of the market is chaotic, there may be islands of maturity. Security components such as secure enclaves on endpoint devices, cryptographic credentials such as smart cards or tokens, and robust encryption libraries may make it possible for organizations to create assured solutions for specific tasks. Similarly, governments and companies that are at high risk and have large security budgets can also produce or buy custom high-assurance solutions, although these solutions will typically be much more expensive and less attractive because they are much slower to adopt new functionality than mass-market alternatives. Larger countries will continue to invest in customized solutions—for example, to protect sensitive communications, classified data, intelligence operations, and weapons systems.
The success of these application-specific solutions depends on many factors beyond security, including the complexity of the integration and the incentives for adoption. For example, a technology that requires reworking a system’s user interfaces, databases, and so on, is much more challenging than one that connects easily into established hardware or software interfaces. Some of these solutions can be built using relatively straightforward cryptography but could have large implications for the Intelligence Community. For example, a secure remote access system that facilitated a transition to distributed workforce would have major implications for hiring, facilities, culture, and employee oversight.
Integration and Operations
System Architecture
Enterprise information technology systems typically encompass a variety of client and server computers along with networks that interconnect enterprise systems with each other and with outside systems connected via the Internet or private networks. In many cases, enterprises also rely on servers in the “cloud” that provide computing and/or storage services.
The architecture of an enterprise IT system defines the components that make up the system and technical requirements for interconnections. Effective security needs to be central to the architecture. An effective security architecture can help to mitigate (though not eliminate) shortcomings in the security of the individual products that are the components of a system.
___________________
55 R.N.M. Watson, J. Woodruff, P.G. Neumann, S.W. Moore, J. Anderson, D. Chisnall, and N. Dave, 2015, “CHERI: A Hybrid Capability-System Architecture for Scalable Software Compartmentalization” in Proceedings of the 36th IEEE Symposium on Security and Privacy (“Oakland”).
A fundamental principle of security architecture is “least privilege”—the idea that no user, computer program, or component should be granted more access than it requires to perform its function.56 Some designers of modern IT systems have adapted least privilege to a concept called “zero trust,” that aims to build enterprise IT systems that do not make any assumptions about the security of the network. Zero trust eliminates or diminishes reliance on a network firewall to create a trusted network. As a result, users are allowed to use untrusted networks (such as potentially compromised corporate networks or public Wi-Fi access points) to perform sensitive tasks. In this model, applications and servers must carefully ensure that all accesses are authorized.
Implementations of zero trust architectures seek to ensure that every attempt to gain access to a resource (a file, a device, or a communications channel) must be authorized and the user or system attempting access must be strongly authenticated. All resources in transit over a network or in storage must be protected from unauthorized access. Encryption is critical to the implementation of zero trust architectures: authentication relies on encryption to implement digital signatures and data protection relies on encryption to provide secrecy and prevent unauthorized access.
Supply Chain Security
Computer systems and networks bring together products and components created by a worldwide ecosystem of commercial vendors, open-source developers, manufacturers, and integrators. If systems do not take extraordinary efforts to isolate individual components, a vulnerability in an “outsourced” piece of hardware or software can have a devastating effect on the security of the entire system. Such a vulnerability can result from a malicious actor or inadvertent error at any stage in the supply chain or involve misunderstandings across components or layers of abstraction. The “SolarWinds”57 intrusion disclosed in late 2020 is an example of a supply chain attack that was reported to have resulted from a malicious modification.
Governments and vendors have been seeking to establish policies and processes to prevent or defeat supply chain attacks. Executive Order 14028 mentioned above is a recent example. But supply chains are complicated, and the problem is a difficult one that plays a significant role in driving systems in a chaotic direction.
End-User Operational Security and Risk Management
The inevitability of security failures does not mean that defense is pointless. Organizations can raise the bar against successful attacks by adopting mundane practices such as patching and updating software,58 configuring their networks to require strong authentication of users and authorization of access, continuous backup and checkpointing, collecting and protecting logs of users’ and programs’ actions, and rapidly fixing vulnerabilities that are detected. At a minimum, such practices are effective against attackers with limited competence and resources (such as many ransomware perpetrators), while increasing the development cost and reducing the operational lifetime of attacks. Effective defenses against “low end” attackers can also help organizations reserve their best defensive resources and people for use against sophisticated adversaries.
Possible evolutionary paths for risk management include investing heavily in thoroughly verified systems to reduce the number of vulnerabilities, or reducing reliance on higher-risk components, deploying redundancy to combine less reliable systems into something better where failure modes are mostly independent (an approach that the National Security Agency has advocated in its “Commercial Solutions for Classified” program59), and where necessary combining many insecure components with insecure monitoring systems and unreliable people but managing to detect enough attacks to “muddle along.”
Recovery and resilience can be important although they do not work effectively in cases where the secrecy of
___________________
56 J.H. Saltzer and M.D. Schroeder, 1974, The protection of information in computer systems, Communications of the ACM 17(7).
57 Center for Internet Security, “The SolarWinds Cyber-Attack: What You Need to Know,” last updated March 15, 2021, https://www.cisecurity.org/solarwinds.
58 Organizations’ reliance on obsolete information technology products that have not been designed to stand up to new threats or benefited from secure development practices, or even are no longer provided with security patches by their developers, has proven to be a major cause of security incidents and a major concern for information security managers. See https://slate.com/technology/2018/06/why-the-military-cant-quit-windows-xp.html.
59 National Security Agency, “Commercial Solutions for Classified Program (CSfC),” https://www.nsa.gov/csfc/, accessed October 15, 2021.
information is paramount (e.g., it is not possible to “recover” from a leak such as the Office of Personnel Management [OPM] breach60). Movement of computing to the “cloud” is a trend that will continue at least for the near future. Cloud services tend to be better managed and protected than many individual enterprise systems but the consequences of a successful attack on a cloud provider could be extremely serious.
FINDING 4.8: In every scenario, bugs in software and operational errors are the weakest links in security.
FINDING 4.9: Communications and storage depend on a software stack: hypervisor (a program that allows a computer to run several operating systems simultaneously), operating system, libraries, and application. While quantum computers or mathematical advances are important research topics, bugs or operational mistakes in this stack are the biggest source of system insecurity. Exploiting these errors is, and likely will remain, the biggest opportunity for offense, and minimizing them the highest priority for defense and risk management.
Education, Workforce, and Training
People with the right knowledge and expertise are essential for the reliable implementation and operation of cryptographic systems over the long term. Within U.S. universities, “security” is frequently considered a niche specialty or elective, much like graphics or computer games, rather than a cross-cutting issue of fundamental importance to all systems at the same level as algorithms or data structures. Although some self-taught individuals develop significant expertise in security, and some companies invest substantial sums in security education and training for their developers and operational staff, many do not. Some programmers have little enthusiasm for security, such as one survey respondent who commented, “I find the enterprise of security a soul-withering chore and a subject best left for the lawyers and process freaks. I am an application developer,” while another said, “I find security an insufferably boring procedural hindrance.”61
Thus, future U.S. scenarios are likely to lean toward “chaotic” without substantial improvements in our educational system and developers’ full commitment to reliable, trustworthy implementations of hardware and software systems. While the Internet has enabled broader dissemination of knowledge about cryptography and security, the high-level research training and careers required to understand and contribute to the state of the art require real investment in research infrastructure from government and industry.
FINDING 4.10: The United States needs far more data security expertise than is currently available, and these needs are growing substantially. The failure to meet these needs could have significant and widespread ramifications both for national security and the private sector. All software developers and computer scientists require basic competence in computer security. In addition, a growing number of people will require deep expertise in security. The required skills are not easy to teach, as students need both security-focused knowledge and a deep technical knowledge across multiple subjects and layers of abstraction. If the U.S. educational system does not meet these needs, or if the United States becomes a less attractive destination for students, researchers, and entrepreneurs born in other countries, the shortage will be much worse. Technological changes may rapidly increase demand for rare skills or may reduce demand by enabling tasks that currently require exceptionally skilled individuals to be performed by a broader range of people
FINDING 4.11: Practical knowledge about the security of cryptographic systems will continue to be widely disseminated across the globe. Effective work (offensive or defensive) can be performed by a few skilled individuals. As a result, unlike areas where a country can obtain dominant capabilities by incurring costs that
___________________
60 T. Armerding, 2016, “The OPM Breach Report: A Long Time Coming,” CSO Online, October 13, https://www.csoonline.com/article/3130682/the-opm-breach-report-a-long-time-coming.html.
61 F. Nagle, D. Wheeler, H. Lifshitz-Assaf, H. Ham, and J. Hoffman, n.d., Report on the 2020 FOSS Contributor Survey.
other countries cannot afford, many countries will have significant data security capabilities and none will be dominant.
Systems-Related Issues and Trends
The following sections delve into specific issues that will have a significant impact on the security of future systems and their implementation or use of encryption. In particular, some of the potential Scientific Advances discussed previously have significant Systems-related aspects that can influence the overall maturity of the products and services that are deployed to end users.
Post-Quantum Cryptography
Post-quantum cryptography refers to cryptographic algorithms believed to be resistant against adversaries possessing both large-scale quantum computers and classical computers. As discussed in Chapter 2, such algorithms are being developed and standardized today, and can be used on classical (i.e., non-quantum) computers so that systems and data are robust against future quantum computing advances. The process of transitioning to new algorithms is difficult. In mature scenarios, these issues are managed and bounded; chaotic scenarios yield insecure cryptographic implementations. The challenges that need to be addressed include:
- Incompatibility with existing infrastructure and systems: Post-quantum cryptography (PQC) algorithms typically involve larger secret and public keys, longer computation times, and longer message lengths. For constrained devices like the U.S. government Common Access Card (CAC) and readers, these limitations can introduce incompatibilities with existing hardware and performance challenges. Other examples include 5G cellular systems (where existing designs do not include PQC) and cryptocurrencies such as Bitcoin. All of these systems can be changed, but such updates will take time, money, and determination, in some cases to the level of complete replacement.
- Complexity and security risks arising from the need for backward compatibility during transitions: Because today’s cryptography is so pervasive, many different protocols and implementations will need to be transitioned. During the transition phase, many ecosystems will need to run two entirely distinct security protocols or configurations in parallel—a backward-compatible option using traditional public key algorithms, and one with post-quantum algorithms. Many different components may need upgrading, including cryptographic protocols, key management hardware, certificates, and certificate issuance infrastructure. Because many devices will need to interoperate with non-upgraded systems, and some systems may never get upgraded, it may take a very long time before the legacy (non-quantum-resistant) options can be fully disabled. Transitions will likely be especially lengthy in military systems, whose lifespan is often measured in decades.
- The potential for long-term interoperability issues arising from multiple competing systems based on national interests: Today’s Internet standards largely achieve interoperability by predominantly using a small number of NIST-standardized algorithms. In contrast, there may be multiple competing non-interoperable PQC standards—for example, one set advanced by NIST, and others advanced (or mandated) by other nations. This diversity raises a number of distinct issues ranging from technical to sociopolitical—will devices need to implement all of these protocols, will this contribute to Internet fragmentation, will critically important standards be controlled by adversaries? Protocols such as SSL/TLS that support algorithm negotiation may do better in terms of interoperability, but typically the overall protocol security is that of the weakest supported public key option. Thus, today’s commercial cryptographic suites, which are already fairly chaotic, may become even more so as PQC systems are deployed and operated.
FINDING 4.12: The transition to post-quantum cryptography is likely to be prolonged over many years. It may also provide a rationale for replacing obsolete systems that have other security problems.
FINDING 4.13: The complexity of the transition to post-quantum cryptography will likely introduce a range of new security vulnerabilities.
FINDING 4.14: A new classical cryptanalysis algorithm or quantum computing development could result in rushed and disorganized efforts to replace widely used public key algorithms and cryptographic standards that use these algorithms. Such a breakthrough would require mitigation efforts that would be more complex than fixing typical software bugs, such as the coordinated deployment of major protocol updates across implementations and services.
Side Channels
Cryptographic algorithms are defined as mathematical operations. For example, NIST’s standard for AES-256 encryption defines how to transform a 128-bit plaintext block and a 256-bit secret key into a 128-bit ciphertext block. From a mathematical perspective, AES-256 is believed to be extremely strong. For example, even an adversary who captures billions of plaintext/ciphertext pairs encrypted with a single random target key, and who can harness all the computers on Earth for decades, has no significant chance of recovering the key using the best-known attacks.
The situation is completely different if the adversary can gain even a tiny fraction of a bit of additional information from the encryption process. For example, cryptographic devices in practice often emit radio frequency waves, draw varying power,62 or take variable time depending on the operations being performed. These effects are termed “side channels” because they reveal additional information beyond the mathematically defined inputs and outputs. Even very low fidelity measurements of such side channels can be enough to turn the adversary’s problem from a wildly infeasible calculation into a trivial one.
Beginning in 2018 with the discovery of classes of vulnerabilities referred to as Spectre63 and Meltdown,64 side channels in modern processor hardware became a subject of increased interest to vulnerability researchers. As with cross-site scripting errors 10 to 15 years before,65 vulnerability researchers reported an array of new vulnerabilities in a relatively short period. While some of these side-channel vulnerabilities can be mitigated in software or microcode updates, others cannot—and there is a real possibility that even more serious unfixable hardware vulnerabilities will be uncovered in the future.
For security engineers, side-channel attacks are challenging because they involve implementation properties that cross teams and layers of abstraction. For example, a cryptographic algorithm may be implemented in software, which runs on a CPU, which is manufactured from transistors, which are connected by wires that generate RF signals, which ultimately expose the secret key. Software developers generally have little idea of the analog characteristics of the circuits, while circuit designers generally have little understanding of the cryptographic implications of their designs. To exploit the resulting analog side channels, attackers require physical proximity to the device or need some other way to collect the required information. Relatively advanced mitigations are present in some specialized cryptographic chips such as those used in smart cards, but most processors today contain no protections.
___________________
62 J. Kocher, J. Jaffe, and B. Jun, 1999, “Differential Power Analysis,” Advances in Cryptology—Crypto 99 Proceedings (M. Wiener, ed.), Lecture Notes in Computer Science, Vol. 1666, Springer-Verlag.
63 P. Kocher, J. Horn, A. Fogh, D. Genkin, D. Gruss, W. Haas, M. Hamburg, M. Lipp, S. Mangard, T. Prescher, M. Schwarz, and Y. Yarom, 2019, “Spectre Attacks: Exploiting Speculative Execution,” 40th IEEE Symposium on Security and Privacy (S&P’19), https://spectreattack.com/spectre.pdf.
64 M. Lipp, M. Schwarz, D. Gruss, T. Prescher, W. Haas, A. Fogh, J. Horn, S. Mangard, P. Kocher, D. Genkin, Y. Yarom, and M. Hamburg, 2018, “Meltdown: Reading Kernel Memory from User Space,” 27th USENIX Security Symposium (USENIX Security 18), https://meltdownattack.com/meltdown.pdf.
65 Symantec, 2008, “Symantec Internet Security Threat Report Trends for July–December 07,” Volume XIII, April, https://web.archive.org/web/20080625065121/http://eval.symantec.com/mktginfo/enterprise/white_papers/b-whitepaper_exec_summary_internet_security_threat_report_xiii_04-2008.en-us.pdf.
In addition to analog side channels, timing side channels can also expose sensitive information.66 These can result from cryptographic algorithm implementations that, for example, allow secret intermediate values to affect a memory address or conditional branch (enabling Flush+Reload attacks67). In addition, packet timing and sizes can reveal information about network flows as well as messages that cannot be decrypted. Modern microprocessors also have numerous side channels internally that can leak information between processes. In general, optimizations by chipmakers to increase CPU performance tend to introduce new side channel vulnerabilities.68 As a result, new side channel attacks are likely to be discovered.
Although side-channel vulnerabilities and attacks draw academic and media attention, their real-world impact may be less than that of software vulnerabilities that may be easier to discover and exploit. For example, many side channel vulnerabilities are only practical to exploit if adversaries can run software on the target machine, in which case software bugs are probably easier to exploit. Researchers will likely continue to discover side channel vulnerabilities, and end users, including the Intelligence Community will be well advised to assess their potential impact and respond accordingly.
5G Cellular Systems
5G cellular systems are now being built out around the world; although their cryptography is not particularly novel in its approach, 5G systems as a whole deserve considerable attention from the Intelligence Community.69 Most press coverage of 5G systems has emphasized its new radio technology—for example, the increased bandwidth that can be provided via millimeter wave technology. Although such radio issues may have some relevance for the Intelligence Community—for example, radio intercepts will be more difficult with many short-range radio links, distributed beam forming, and so on—they are largely independent of cryptographic considerations.
For many use cases, the 5G network is viewed as untrusted with respect to privacy and integrity of communications. An additional layer of cryptographic protection (such as SSL/TLS for web services or VPNs) provides protection unrelated to the network. However, the network still sees traffic flow metadata, including protocol information, packet sizes and timing, and source and destination addresses. In addition, network vulnerabilities can also result in denial-of-service attacks. These present the greatest systems-level concerns, as they cannot be addressed easily via application layer cryptography. Current networks also collect fine-grained location information about users; the 5G standards aim to provide more privacy.
One of 5G’s more interesting aspects lies within its conversion to a distributed cloud infrastructure, in which services are implemented almost entirely in software. For example, Verizon’s 5G “Mobile Edge Cloud” service is provided by Amazon Web Services hosted within nearby (low-latency) data centers.
Older cellular systems generally provided services (echo cancellation, texting, voicemail, etc.) via suites of specialized hardware and software appliances provided by equipment manufacturers (Huawei, Ericsson, etc.). The 5G vision sees such services provided by chains of virtual machines running within “edge clouds.” The edge cloud vision, sometimes identified by the dense acronym NFV/SDN, for Network Functions Virtualization and Software-Defined Networks, or C-RAN for Cloud Radio Access Networks, moves to an architecture based on software running on commodity servers. In its most extreme form, some of the radio functionality is also envisioned as running in such edge clouds. Some nations envision these software suites as fully open source rather than provided by a traditional vendor.
___________________
66 P.C. Kocher, 1996, “Timing Attacks on Implementations of Diffie-Hellman, RSA, DSS, and Other Systems,” pp. 104–113 in CRYPTO 1996.
67 Y. Yarom and K. Falkner, 2014, “Flush+Reload: A High Resolution, Low Noise, L3 Cache Side-Channel Attack,” pp. 719–732 in Proceedings of the 23rd USENIX Security Symposium, https://www.usenix.org/system/files/conference/usenixsecurity14/sec14-paper-yarom.pdf.
68 P. Kocher, J. Horn, A. Fogh, D. Genkin, D. Gruss, W. Haas, M. Hamburg, M. Lipp, S. Mangard, T. Prescher, M. Schwarz, and Y. Yarom, 2019, “Spectre Attacks: Exploiting Speculative Execution,” 40th IEEE Symposium on Security and Privacy (S&P’19), https://spectreattack.com/spectre.pdf.
69 P. Marsch, Ö. Bulakci, O. Queseth, and M. Boldi, eds., 2018, 5G System Design: Architectural and Functional Considerations and Long Term Research, John Wiley & Sons, Hoboken, NJ.
This evolution is likely to introduce two very significant systems issues in practice. First, the software will likely be highly complex and thus introduce many possibilities for error. In addition, the perceived ease with which software can be updated may result in poor implementation quality, as vendors may prioritize speed in deploying and improving implementations over making them reliable or secure. If so, the rate of software upgrades may accelerate considerably. In such scenarios, when one looks across the world, one might see many different software versions (and bugs) running in the various providers rather than today’s relative uniformity.
Second, telecommunications providers may find it difficult to manage such software-intensive, cloud-based infrastructure, particularly when their infrastructure spans a number of distributed edge-clouds; staffing will likely be an issue. Their difficulty will increase even more to the extent that they migrate to an agile “DevOps” (software development [Dev] and IT operations [Ops]) style of operation, which is radically different from their current cultures. It seems unlikely that cellular providers in most parts of the world will be able to support such infrastructure development and upgrading without considerable help from third parties, thus, in essence outsourcing their operation (and the correct functioning of their cryptographic systems). The combination of new architectures, complex and evolving software, operator inexperience, and perhaps outsourced operation may elevate the chaos, rather than maturity, within many provider networks.
Thus, today’s cellular infrastructure, which is relatively mature, may in coming years become more chaotic for some service providers as they roll out their 5G infrastructure.
FINDING 4.15: 5G may introduce a number of new systems issues in practice, owing to both complex new suites of software and operator inexperience in distributed cloud environments.
Internet of Things
The term “Internet of Things” (IoT) spans an extremely wide variety of devices and systems that range, according to context, from the Supervisory Control and Data Acquisition (SCADA) systems that oversee entire electrical grids through instrumented aircraft fleets all the way down to doorbells and thermostats. The examples in this discussion are concerned primarily with what might be termed “personal” IoT devices, such as smartphones, personal medical devices, household appliances, and automobiles.
Industrial IoT or SCADA systems are well established worldwide and share many cybersecurity considerations with IT systems. SCADA systems do pose significant unique security challenges, especially resulting from the fact that such systems are often performance critical, long-lived, and difficult to update. The cybersecurity of SCADA systems has been the subject of many studies and standards efforts—see, for example, the National Academies’ report Enhancing the Resilience of the Nation’s Electricity System70 or International Electrotechnical Commission (IEC) Standard 62443.71 In contrast to SCADA and industrial IoT systems, emerging consumer IoT devices are becoming ubiquitous and much less likely to be designed with security as a major consideration.
The continuing move to connected devices means that it will soon be almost impossible to live a “normal” life without being surrounded by devices with sensors, multiple communication channels (WiFi, 5G, Bluetooth) all built to be cheap, which implies little security, and opaque supply chains. These devices pose a serious risk of surreptitious data collection. For example, the cryptographic strength of an encrypted telephone system call is irrelevant if a compromised IoT device can record the audio. Likewise, cellular data capabilities in IoT devices can allow attackers to mount attacks and exfiltrate data without being seen by local network monitoring tools. Given such omnipresent, constant surveillance, implemented by poorly secured devices, it may prove extremely difficult to keep many personal matters private in coming years—such as where one has been over the past year, who one might have met, what they look like, and the substance of conversations.
___________________
70 National Academies of Sciences, Engineering, and Medicine, 2017, Enhancing the Resilience of the Nation’s Electricity System, The National Academies Press, Washington, DC, https://doi.org/10.17226/24836.
71 International Electrotechnical Commission, 2021, “Understanding IEC 62443,” blog, February 26, https://www.iec.ch/blog/understanding-iec-62443.
Although robust open-source reference implementations might reduce the amount of security expertise needed by IoT vendors, the pressures for low cost and rapid release of such devices present major challenges. In addition, even if security vulnerabilities are found and subsequently fixed for future devices, it may not be possible to apply patches to devices in the field, or users may decline to update. Even in otherwise well-secured devices, metadata may undesirably leak information.
The fact that IoT devices can kill people is an even bigger challenge. There are many warning signs. For instance, in 2019 the FDA issued an alert on insulin pump security, warning that some devices could be hacked and remotely controlled which “could allow a person to over deliver insulin to a patient, leading to low blood sugar (hypoglycemia), or to stop insulin delivery, leading to high blood sugar and diabetic ketoacidosis (a buildup of acids in the blood).”72 Automobiles can also be very dangerous. As early as 2015, Fiat recalled 1.5 million vehicles after a demonstration of (benign) hackers taking remote control of a Jeep Cherokee through the Internet.73 Self-driving automobiles clearly pose further potential vulnerabilities.
Many IoT issues may have unexpected but significant consequences. As one example taken from industrial IoT, in the 2013 Target breach, the attackers used remotely accessible networked heating, ventilation, and air conditioning (HVAC) equipment as an entry point into the company’s network in order to install malware on point-of-sale terminals. As a second example, security vulnerabilities in poorly secured networked smart meters could potentially be escalated to destabilize the entire electrical grid through surges or blackouts. Last, it is a well-known problem that medical devices often run unpatched versions of ancient software like Windows XP (and installing updates may require FDA approval); ransomware attackers have managed to exploit vulnerabilities in these legacy devices as well as in the remote access and network firewall infrastructure intended to protect networked hospital equipment.
FINDING 4.16: Many IoT components are poorly secured and easy to subvert, with an extremely wide range of consequences that are difficult to predict but potentially very high impact for the Intelligence Community and broader society. Because IoT will likely bring significant improvements to many aspects of life, however, more money and energy may be devoted to securing such devices going forward.
___________________
72 Food and Drug Administration, 2019, “FDA Warns Patients and Health Care Providers About Potential Cybersecurity Concerns with Certain Medtronic Insulin Pumps,” FDA News Release, June 27, https://www.fda.gov/news-events/press-announcements/fda-warns-patients-and-health-care-providers-about-potential-cybersecurity-concerns-certain.
73 A.M. Kessler, 2015, “Fiat Chrysler Issues Recall Over Hacking,” The New York Times, July 24, https://www.nytimes.com/2015/07/25/business/fiat-chrysler-recalls-1-4-million-vehicles-to-fix-hacking-issue.html.









































