2
Architecture and Data
The capabilities that we’re building and using, we’re actually designing into it the capability to snap together like LEGO blocks, both our Air Force capabilities, as well as our sister services and international partners.… The power of this architecture is unlocked by services, allies and partners working together to connect networks and share information at machine speed. That’s all-domain superiority.
—Preston Dunlap, Chief Architect, U.S. Department of the Air Force1
ARCHITECTURE OVERVIEW
The architecture of the Advanced Battle Management System (ABMS) refers to the relationships and interconnections between individual system components and capabilities. The granularity of the architecture is typically described at the system and sub-system level, with multiple capabilities represented within each sub-system component. These sub-components are modularized and interconnected through a variety of technologies, including wired and wireless communications, interconnect frameworks within a single platform, satellite communication (SATCOM) systems, and commercial telecommunications. The intent is to integrate all components and
___________________
1 S. Freedberg, Jr., 2019, “Air Force ABMS: One Architecture to Rule Them All?” Breaking Defense, https://breakingdefense.com/2019/11/air-force-abms-one-architecture-to-rule-them-all, November 8, and J. Lacdan, 2020, “Army, Air Force Form Partnership, Lay Foundation for CJADC2 Interoperability,” Army News Service, October 1.
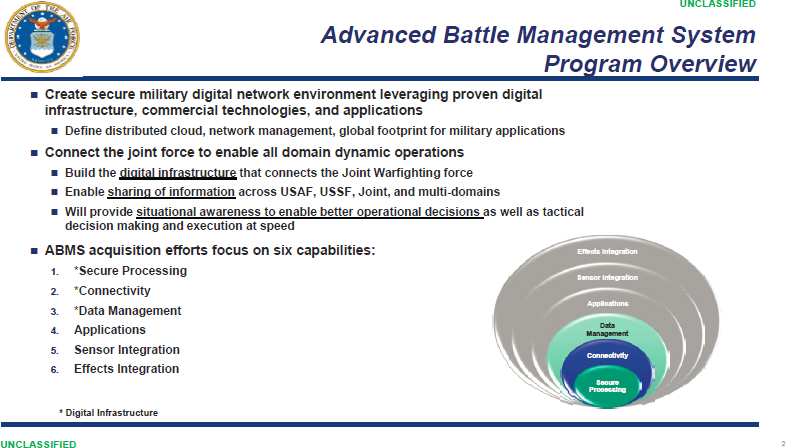
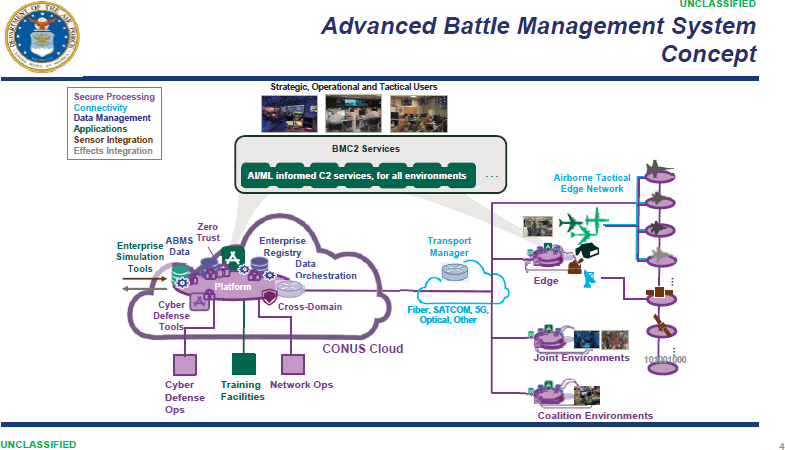
interconnections to achieve the larger system objectives—in this case, the coordinated command and control (C2) across all Department of the Air Force (DAF) sensors, network components, and weapon systems, as well as connections to the larger Joint All-Domain Command and Control (JADC2) enterprise architecture. Figure 2.1 provides an overview of ABMS and Figure 2.2 details the ABMS concept.
As a C2 family of systems, ABMS involves both data processing and communication that support computation, sensing, and actuation, defined as the application of weapons effects.2 Under the current construct, each C2 node has the ability to provide autonomous computation in the use of sensors, data, and actuation. The success of this architecture fundamentally depends on the rigorous adherence to Application Programming Interface (API) and data standards that provide a common application environment and a set of flexible protocols.
ABMS architecture is also intended to closely link to elements of JADC2, although the committee saw little evidence of this. The focus appears to be largely on defining ABMS-specific platforms, components, and interconnections that are native to the DAF. The committee strongly encourages developing ABMS architecture at the Joint level to achieve interoperability with other Services and multinational partners.
___________________
2 R. Walden, 2021, “ABMS Perspectives from the Air Force Rapid Capabilities Office,” Presentation to the Air Force ABMS Committee, January 22.
A standard that is open, modular, and (most importantly) scalable also needs to be defined to ensure that Army, Navy, Marine Corps, DoD agencies, and multinational partner assets (or their portion of the JADC2 system) can effectively integrate with the ABMS architecture as envisioned by the JWC. Innovative and “smart” systems will also need to integrate and/or interoperate with legacy systems. Additionally, because the majority of U.S. weapons systems are designed and supplied by prime system integrators in the defense industrial base, they should be engaged throughout the development process.
FINDING 1: To support the JWC, the ABMS architecture must be considered integral to JADC2, which needs to be clearly defined.
FINDING 2: An open, modular design is needed to support evolution of ABMS and JADC2.
RECOMMENDATION 1: The Department of the Air Force Chief Architect’s Office and the Department of the Air Force Rapid Capabilities Office should define the Advanced Battle Management System (ABMS) architecture at the Joint All-Domain Command and Control level to ensure interoperability with other ABMS-like systems being developed.
RECOMMENDATION 2: The Joint Staff J6 or a designated U.S. Department of Defense executive agent should establish interoperability requirements and performance metrics for all participants in Joint All-Domain Command and Control to allow for eventual integration of all capabilities.
RECOMMENDATION 3: The Department of the Air Force Chief Architect’s Office and the Department of the Air Force Rapid Capabilities Office should design the Advanced Battle Management System architecture to be modular and include open standards and interfaces that would enable configuration with other Service variants.
The ABMS architecture should include the ability to achieve integrity, availability, and confidentiality for all communications, data, and computation across all applications. The goal is to establish not only a common operating picture (COP), but a representation of the totality of data that could be used for any strategic or tactical decision at the edge. If the tactical edge is sufficiently served with relevant data, velocity of commanders’ intent can be maintained at some level. If the tactical edge is not serviced, but the strategic level is, relevant actions and its resultant effects will be limited at best, and ineffective at worst.
Emphasis should also be given to communications, data, and computation operating in degraded or denied environments, where a level of autonomy for disconnected or high-latency components need to operate uninterrupted. More importantly, protecting ABMS—both systems and data—against cyber vulnerabilities and adversarial attacks requires that cybersecurity be included as part of the overall architecture design.
FINDING 3: The ABMS architecture requires integrity, availability, and confidentiality for all communications, data, and computation elements.
RECOMMENDATION 4: The Department of the Air Force Chief Architect’s Office and the Department of the Air Force Rapid Capabilities Office should design the Advanced Battle Management System’s architecture with specific technical requirements and solutions for ensuring that communications, data, and computation may continue to operate in degraded or denied access environments.
Architecture and Technology Status
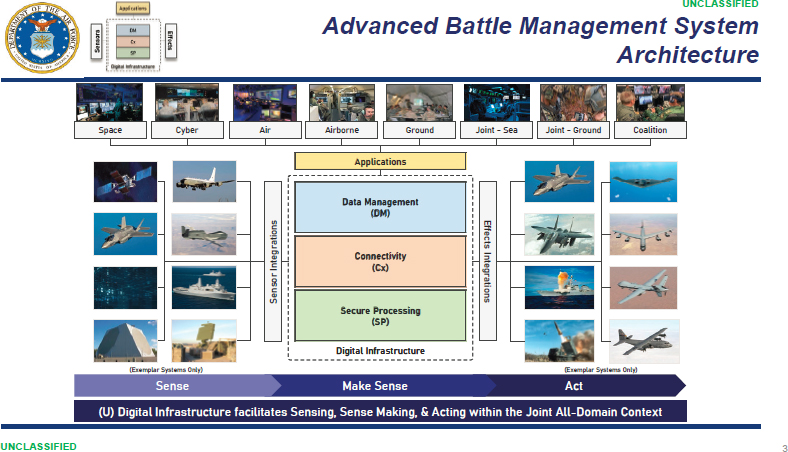
In rudimentary terms, the ABMS architecture consists of an array of platforms, sensors, networks, and datalinks interconnected through a secure cloud3 to facilitate sensing, sense-making, and acting within the Joint All-Domain context. Figure 2.3 depicts the ABMS architecture.
ABMS is a family of systems that includes both hardware and software supported by technologies to input and connect with the JADC2 network. Under the original governance by the DAF’s Chief Architect, it comprises six product (i.e., technologies and capabilities) categories:4
- Sensor integration, including sensors on satellites and aircraft, ground-based radar, among others;
- Data and data management;
- Secure processing that involves both cybersecurity and the ability to transmit and process data across all classifications while allowing broad access to data products;
___________________
3 For more on the Air Force cloud, see Assistant Secretary for Acquisition, Technology, and Logistics, 2019, “Memorandum for Acquisition Workforce: Cloud One and DevSecOps,” September 13.
4 D. Mayer, 2021, “ABMS Aims to Revolutionize Data Flow, Speed Decisions,” Air Force News, https://www.af.mil/News/Article-Display/Article/2559022/abms-aims-to-revolutionize-data-flow-speed-decisions/, April 1.
- Connectivity, from both military and commercial networks, including artificial intelligence (AI) and machine-to-machine links across both legacy and new weapons platforms;
- Applications; and
- Effects integration.
Each of these original product categories or capabilities was developed through iterative 4-month “demonstration sprints” conducted during on-ramp experiments.5 At the time of presentation by the DAF’s Chief Architect to the committee, they are supported by multiple software product lines to include:
- cloudONE, the secure cloud that supports multi-level classifications across the ABMS enterprise;
- edgeONE, a local cloud backup in the event that datalinks are disconnected from cloudONE;
- dataONE, a database that builds on the Unified Data Library (UDL);6
- crossDomainONE, which enables the transmission of data across classification levels;
- omniaONE, a common operating picture of the all-domain battlefield using multiple feeds merged through a system called fuseONE, which is a cloud-based fusion environment;
- AI/smartONE, which layers on top of omniaONE and uses artificial intelligence to cue the user to potentially useful information;
- feedONE, cloud-based data feeds from all sources;
- commandONE, a battle management command and control system using the Link16e network;7 and
- gatewayONE, a communications gateway designed to secure two-way data path across multiple platforms and domains.8
___________________
5W. Roper, 2020, “Advanced Battle Management System Management Construct.”
6 UDL is “a collection of space objects that integrates data from commercial and government sources.” See S. Erwin, 2021, “Bluestaq Wins $280 Million Space Force Contract to Expand Space Data Catalog,” Space News, https://spacenews.com/bluestaq-wins-280-million-space-force-contract-to-expand-space-data-catalog/, March 23. See also F. Wolfe, 2021, “Unified Data Library to Be Significant Part of U.S. Space Force Contribution to ABMS,” Defense Daily, https://www.defensedaily.com/unified-data-library-significant-part-u-s-space-force-contribution-abms/space/, May 24.
7 Link 16 is “the DOD’s primary tactical data link for all military service and defense agency command, control and intelligence systems.” See B.E. White, 1999, “Tactical Data Links, Air Traffic Management, and Software Programmable Radios,” Proceedings of the IEEE, https://www.mitre.org/sites/default/files/publications/white_tactical_data_links.pdf. Linked16e is the enhanced Link 16.
8 P. Dunlap, 2020, “ABMS Overview,” Presentation to the Air Force ABMS Committee, October 30.
ABMS is also supported by a variety of hardware product lines to include:
- radioONE, a new radio frequency antenna for receiving SATCOM data;
- apertureONE, a common aperture for communications and radar;
- boxONE, the workstation used to access cloudONE or edgeONE;
- phoneONE, a smartphone that accesses cloudONE or edgeONE; and others.9
The goal is to connect all of these elements into a holistic data-integration and command decision enabler to accelerate the find, fix, target, track, engage, and assess (FFTTEA) kill chain. The committee makes no determination regarding each of these product categories, because it was not provided with information regarding their overall performance.
The ABMS architecture remains nascent and continuously evolving. It is difficult to comprehend the totality of the ABMS architecture without examining each component, which is being constructed from the bottom-up. “When we say ‘build bottom-up,’ we mean that this process of iterative experimentation should occur at the tactical level. The end users of ABMS—joint sensors and shooters—should be the ones cycling through new techniques and technologies that will come to form ABMS.”10 It is important to note that while each component is developed as a building block, ABMS is designed to be a vast ecosystem that integrates each block into its core architecture. As new technologies and capabilities emerge and are experimented in on-ramp exercises, proven technologies will be fielded in capability releases. As such, the ABMS architecture is evolving and in the early stages of definition.
As a possible connective framework, a time-triggered architecture (TTA) may be a viable option.11 TTA is an integration framework that provides an environment for integrating components into a system, where certain properties of the system are guaranteed for the system by the framework independently of the components.12
___________________
9 Ibid.
10 P. Birch, R. Reeves, and B. DeWees, 2020, “Build ABMS from Bottom-Up, for the Joint Force,” Breaking Defense, https://breakingdefense.com/2020/05/build-abms-from-bottom-up-for-the-joint-force/, May 13.
11 J. Valenzia, 2020, “JADC2 and ABMS,” Presentation to the Air Force ABMS Committee, December 18. For more on TTA, see H. Kopetz, 1997, “Why a Distributed Solution?,” p. 34, in Real-Time Systems: Design Principles for Distributed Embedded Applications, Springer. See also H. Kopetz and G. Bauer, 2002, “The Time-Triggered Architecture,” Proceedings of the IEEE Special Issue on Modeling and Design of Embedded Software, October.
12 J. Rushby, undated, “An Overview of the Time Triggered Architecture (TTA) and Its Formal Verification,” http://www.csl.sri.com/users/rushby/slides/kestrel05.pdf, Computer Science Laboratory, SRI International.
Within this framework is the capability to rapidly adapt to changing conditions, mission requirements, technology improvements, and threats.13 The advantages of using TTA are “to precisely specify the interfaces among the nodes, to simplify the communication and agreement protocols, to perform prompt error detection, and to guarantee the timeliness of real-time applications.”14 It has been used in automobile applications (Audi, Peugeot S.A., and others), but also for aircraft applications (Honeywell Aerospace).15
Furthermore, to support the aims of JADC2, the ABMS architecture needs to remain evolvable, allowing for continuous development, deployment, testing, refinement, and improvement over time. While DAF leaders have embraced flexibility in developing ABMS, Congress’s decision to reduce the ABMS FY 2021 budget by nearly one-half may hamper the department’s ability to continue with this approach.16 According to the Acting Assistant Secretary of the Air Force for Acquisition, Technology, and Logistics, “We’re doing everything in our power to keep efforts going … with a cut of that magnitude, it will have an impact.”17
The ABMS architecture must focus on protecting data, computations, and communications from adversary access or manipulation; providing high-bandwidth communications with significant redundancy and resiliency; deploying advanced computational platforms with surplus or expanding capacity to handle thousands of parallel C2 tasks simultaneously; providing large data curation and storage for near-real-time data accessibility to all decision-support nodes; and allowing for interoperability with both legacy platforms and inter-Service systems and networks. Furthermore, the architecture should remain modular with standardized, open interfaces based on practicality, and ideally, a track record of successful implementation, so as technology progresses, new components may be easily incorporated into ABMS to improve realization of all mission requirements. The use of open standards and APIs would facilitate ready and rapid adoption of new technologies that are critical for enabling the integration of future communications, computation, data, and software improvements.
FINDING 4: The ABMS architecture must be adaptive to enable continuous development, deployment, testing, refinement, and improvement over time.
___________________
13 E. Bryant, 2021, “Cybersecurity in JADC2 and Contested Environments,” Presentation to the Air Force ABMS Committee, April 16.
14 H. Kopetz and G. Bauer, 2002, “The Time-Triggered Architecture,” p. 1.
15 Rushby, TTA Overview 4.
16 See T. Hitchens, 2021, “Air Force Working to Minimize Damage from ABMS Budget Cut,” Breaking Defense, https://breakingdefense.com/2021/02/air-force-working-to-minimize-damage-from-abms-budget-cut/, February 24.
17 Ibid.
FINDING 5: Under current plans, the ABMS architecture is likely to face interoperability challenges if it is to fully realize the JADC2 JWC.
Technology for Data-Centric Operations
Current DoD communications are primarily point-to-point.18 Advancing the command, control, communications, computers, intelligence, surveillance, and reconnaissance (C4ISR) architecture across a complex and dispersed DoD enterprise to take advantage of newer, more agile networked communication solutions at both strategic and tactical levels will require a significant amount of time, resources, and commitment. As increasing numbers of operations shift to data-centricity, it is critical that data—more specifically, the access, storage, transmission, validation, and protection of data—be considered in the enterprise architecture design.
There are an increasing number of modern tools to support data-centric operations. These range from tools to support application-to-application interfaces to the use of clouds to provide on-demand computing, storage, and sharing.19 Others include predictive analytics, data virtualization, stream analytics, distributed storage, data preprocessing, and others.20 While the work on capabilities such as DARPA’s data translation and rapid software integration tool known as system of systems technology integration tool chain for heterogeneous electronic systems (STITCHES) could support architectural transitions and facilitate tactical operations, ABMS must also support data and computing needs for highly sensitive strategic missions to include nuclear command, control, and communications (NC3) operations. Adopting an array of data-exchange technologies that could support the spectrum of capabilities should remain a central objective of ABMS’s architecture design.
Furthermore, as AI/machine learning (ML) technologies become ever more pervasive and capable, machine-to-machine data sharing—at scale within accept-
___________________
18 J.C. Stenbit, 2021, “DoD C3I Perspectives,” Presentation to the Air Force ABMS Committee, February 24.
19 A good example of application-to-application interfaces is DARPA’s System of Systems Technology Integration Tool Chain for Heterogeneous Electronic Systems (STICHES). See DARPA (Defense Advanced Research Projects Agency), 2020, “Creating Cross-Domain Kill Webs in Real Time,” Defense Advanced Research Project Agency website, https://www.darpa.mil/news-events/2020-09-18a, September 18.
20 See Maruti Techlabs, 2017, “10 Key Technologies That Enable Big Data Analytics for Businesses,” Toward Data Science, https://towardsdatascience.com/10-key-technologies-that-enable-big-data-analytics-for-businesses-d82703891e2f, September 26, and R. Sheldon, 2021, “Why and How to Adopt a Data-Centric Architecture,” TechTarget, https://searchconvergedinfrastructure.techtarget.com/tip/Why-and-how-to-adopt-a-data-centric-architecture, January 28.
able timelines for both planned and unanticipated mission requirements—will become increasingly important and must be fully integrated into the ABMS and JADC2 architecture design. Present-day machine-to-machine data sharing is primarily point-to-point and utilized in support of planned and anticipated missions with predetermined data feeds. However, as adversaries rapidly advance their own use of AI/ML, the DoD and the DAF need to implement advanced AI capabilities that would improve C2 and time-sensitive decision-making from the range of tactical operations to the strategic planning level.21 Implementing a robust machine-to-machine data sharing capability will require, at a minimum:
- Appropriate placement of data storage and computing to facilitate timely access to—and availability of—data to support military operations;
- Security and synchronization of data storage; and
- Redundancy to support operations in degraded environments and to enable reconstitution; among others.
RECOMMENDATION 5: The Department of the Air Force Rapid Capabilities Office should adopt an array of data-exchange technologies that could support the entire spectrum of capabilities, from tactical to strategic.
Highly Capable Processing: AI and ML
Communications must not only be networked, but also enable direct connections and relays—both with and between—humans and machines. As a C2 network, ABMS requires rapid, accurate, secure, and resilient data processing. This will involve a large volume of complex data and event processing and will increase the time sensitivity and demand for quality of services, particularly in contested areas with jamming and poor communications. Without the aid of machines, process-
___________________
21 For examples, see Y. Tadjdeh, 2021, “Algorithmic Warfare: Russia Expanding Fleet of AI-Enabled Weapons,” National Defense Magazine, https://www.nationaldefensemagazine.org/articles/2021/7/20/russia-expanding-fleet-of-ai-enabled-weapons, July 20, and A. Eversden, 2021, “A Warning to DoD: Russia Advances Quicker Than Expected on AI, Battlefield Tech,” C4ISRNet, https://www.c4isrnet.com/artificial-intelligence/2021/05/24/a-warning-to-dod-russia-advances-quicker-than-expectedon-ai-battlefield-tech/, May 24. See also S. Bendett, 2019, “Russia’s AI Quest Is State-Driven—Even More Than China’s. Can It Work?” DefenseOne, https://www.defenseone.com/ideas/2019/11/russias-ai-quest-state-driven-even-more-chinas-can-it-work/161519/, November 25, and Y. Tadjdeh, 2020, “China Threatens U.S. Primacy in Artificial Intelligence,” National Defense Magazine, https://www.nationaldefensemagazine.org/articles/2020/10/30/china-threatens-us-primacy-in-artificial-intelligence, October 30.
ing, validating, and interpreting the sheer volume of data would be delayed and overwhelm users.
According to the National Security Commission on Artificial Intelligence, “AI is the quintessential ‘dual-use’ technology. The ability of a machine to perceive, evaluate, and act more quickly and accurately than a human represents a competitive advantage in any field—civilian or military.”22 As adversaries compete (and surpass) the U.S. military in this space, the adoption of AI/ML to expedite data transmission and decision-making will be increasingly vital.
Currently, decision-making involves operators manually watching data feeds, taking notes on paper, making phone calls to correlate information with other operators monitoring different data feeds, walking between computer hubs to discuss critical information, and using their own (human) analyses to provide visual and oral updates to convey this information to decision-makers. Accordingly, this approach requires massive manpower, is prone to human error, and significantly delays decisions owing to the sheer volume of complex data being communicated.23
To address this deficiency, the DAF Chief Architect and the Air Force Rapid Capabilities Office are using AI as an enabler and have recruited commercial companies to provide AI/ML-based analytics to transform ABMS’s C2 capabilities. They have incorporated AI as part of ABMS’s smartONE capability to develop algorithms for sensing and synthesizing data. In ABMS’s on-ramp 2 exercise, users were able to leverage smartONE in concert with omniaONE, a common operating picture, to cue users to potentially useful information regarding an adversary’s strategic assets.24 AI was also tested and employed in on-ramp 4, where it was incorporated as part of the kill chain. Users were able to rapidly relay data between different platforms through cloudONE, the tactical-edge cloud and dataONE, ABMS’s common data standardization repository. Additionally, the demonstration used AI to dial in targets to fire upon.
The eventual goal is to leverage AI/ML to provide more automation and predictive analytics to expedite data transport and decision-making even faster. The Director for Joint Force Integration in the Air Force’s Strategy, Integration, and Requirements Directorate explained, “Where we are going, is to identify ways in
___________________
22NSCAI (National Security Commission on Artificial Intelligence), 2021, National Security Commission on Artificial Intelligence Final Report, p. 9, https://www.nscai.gov/wp-content/uploads/2021/03/Full-Report-Digital-1.pdf.
23 See J. Eddins, 2021, “Valenzia: ABMS Will Deliver the ‘Decision Advantage,’” Airman Magazine, https://www.macdill.af.mil/News/Features/Display/Article/2647112/valenzia-abms-will-deliver-the-decision-advantage/, May 26.
24 M.D. Strohmeyer, 2021, “United States Northern Command Support to ABMS,” Presentation to the Air Force ABMS Committee, February 24. See also V. Insinna, 2020, “Behind the Scenes of the US Air Force’s Second Test of Its Game-Changing Battle Management System.”
which we can take that same information and move it through the system machine to machine. So, an automated process … to help make sense or otherwise connect the dots in a way that maybe weren’t connected in the past. This is so that when that information shows up to the decision-maker, they’re able to make a highly informed and fast decision.”25
The committee views these efforts as a notable first step in incorporating AI/ML into ABMS. However, a more comprehensive expansion of AI across ABMS is needed. A commercial capability that may be considered for use is highly capable processing technologies, such as hyperautomation or intelligent process automation. Hyperautomation is “a business-driven, disciplined approach that organizations use to rapidly identify, vet and automate as many business and IT processes as possible. [It] involves the orchestrated use of multiple technologies, tools or platforms,” including the following:
- AI;
- ML;
- Event-driven software architecture;
- Robotic process automation (RPA);
- Business process management (BPM) and intelligent business process management suites (iBPMS);
- Integration platform as a service (iPaaS);
- Low-code/no-code tools;
- Packaged software; and
- Other types of decision, process, and task automation tools.26
While intended primarily for business systems, in the context of ABMS, hyperautomation could potentially improve the accuracy of information processed and accelerate decision-making by further automating advanced C2 functions and data processing. Within the commercial sector, companies are using hyperautomation to reduce burdens on operators and increase the accuracy of predictive analytics by as much as 95 percent when trained with multiple, high-quality data sets.27
___________________
25 J. Eddins, 2021, “Valenzia: ABMS Will Deliver the ‘Decision Advantage.’”
26 Gartner, “Hyperautomation,” Gartner Glossary, https://www.gartner.com/en/information-technology/glossary/hyperautomation. For more on hyperautomation, see IBM Cloud Education, “What Is Hyperautomation?” IBMCloudLearn Hub, https://www.ibm.com/cloud/learn/hyperautomation, April 15, 2021, and D. Wright, “Hyperautomation: The Next Digital Frontier,” Forbes, https://www.forbes.com/sites/servicenow/2021/03/26/hyperautomation-the-next-digital-frontier/?sh=50b4919273fd, March 26.
27 “Trends in Machine Learning to Know for 2021,” Business World Innovative Technologies, https://www.businessworldit.com/ai/machine-learning-trends/, March 23.
To improve and maintain the quality of data collected, the process of automated machine learning (AutoML) may also be considered for adoption. AutoML is “the process of automating the time-consuming iterative task of ML model development. It allows data scientists, analysts, and developers to build ML models with high scale, efficiency, and productivity all while sustaining model quality.”28 These combined processes would enable ABMS developers and users to increase both the efficiency and efficacy of data processing; thereby, contributing to the nation’s information advantage.
RECOMMENDATION 6: To the maximum extent possible, the Department of the Air Force Chief Architect’s Office and the Department of the Air Force Rapid Capabilities Office should design and execute a comprehensive artificial intelligence strategy that would encompass all elements, to include doctrine, chain of command, policy, authorization for weapon release in a joint environment, interfaces to Joint All-Domain Command and Control, and not just select capabilities of the Advanced Battle Management System.
Data and Data Standards
As highlighted in the DoD’s Data Strategy, data is a strategic asset.29 Within ABMS, data constitutes the intelligence, indications, warnings, signals, status, situation, commands, controls, and other multimodal information needed to understand the situation and command, control, and operate military forces. As such, “data in the DoD is a high-interest commodity and must be leveraged in a way that brings both immediate and lasting military advantage.”30
The recognition of data as a strategic asset requires that data pedigree and security be maintained at all times. Original source and combined data should be tagged, catalogued, and securely stored immediately. “In a data-dependent and data-saturated world, victory belongs to the side with decision superiority—the ability to sense, make sense of a complex and adaptive environment, and act smarter, faster, and better.”31
However, without a set of enterprise-level data standards, particularly as each military Service and DoD agency establishes its own contribution to JADC2, information sharing at scale will not be possible. The DoD’s Data Strategy provides
___________________
28 “What Is Automated Machine Learning (AutoML)?” Microsoft Research, https://docs.microsoft.com/en-us/azure/machine-learning/concept-automated-ml, July 1.
29DoD (U.S. Department of Defense), 2020, DoD Data Strategy, https://media.defense.gov/2020/Oct/08/2002514180/-1/-1/0/DOD-DATA-STRATEGY.PDF.
30DoD (U.S. Department of Defense), 2020, DoD Data Strategy, https://media.defense.gov/2020/Oct/08/2002514180/-1/-1/0/DOD-DATA-STRATEGY.PDF, p. 3.
31 C. Pope, 2021, “With Its Promise and Performance Confirmed, ABMS Moves to a New Phase.”
the “overarching vision, focus areas, guiding principles, essential capabilities, and goals necessary to transform the Department into a data-centric enterprise.”32 But it directs each military Service and DoD component/agency to develop its own data strategy implementation plan. This could potentially lead to misalignments and unnecessary redundancies.
The Joint Staff J6 is the DoD’s lead organization for establishing common data standards for JADC2. J6 has hosted monthly meetings through its JADC2 cross functional team (CFT), composed of members from DoD agencies, military Services, the U.S. Department of Homeland Security, and NATO. The CFT held a multi-day data summit in January 2021 with the aim of developing a common data fabric33 for JADC2 that incorporates a standard lexicon, performance metrics, and requirements for setting common data standards.34 To date, the CFT has developed a common vocabulary and identified components of the data fabric definition that will be turned into objectives to direct subsequent work in support of JADC2. These components include metadata tagging, common data interfaces, data access control, data security, and data infrastructure.35 Still, the common data fabric has yet to be completed owing to the challenge of establishing a standard that is neither too prescriptive, nor too open.
Additionally, in June 2021 the J6 released a classified JADC2 Strategy that “provides the governance and framework necessary to enable rapid integration of artificial intelligence, ML, predictive analytics and other emerging technologies.”36 It focuses on five specific lines of effort (LOEs) to include data, human enterprise, technology, nuclear command and control, and the mission partner environment.37 More recently, the J6 is finalizing details on a classified JADC2 Implementation
___________________
32DoD (U.S. Department of Defense), 2020, DoD Data Strategy.
33 A common data fabric refers to a set of standards and IT services that allow data to be shared among different weapon systems, different C2 networks, different organizations and services and across different levels of security. T. Hitchens, 2021, “Exclusive: ‘Do-or-Die’ JADC2 Summit to Crunch Common Data Standards,” Breaking Defense, https://breakingdefense.com/2021/01/exclusive-do-or-die-jadc2-summit-to-crunch-common-data-standards/, January 12.
34 D. Crall, 2021, “Joint All Domain Command and Control,” Presentation to the Air Force ABMS Committee, March 3.
35 A. Eversden, 2021, “Getting Away from ‘Anything Goes’: Military Leaders Set Data Standards for Joint War Fighting,” C4ISRNet, https://www.c4isrnet.com/battlefield-tech/it-networks/2021/01/27/getting-away-from-anything-goes-military-leaders-set-data-standards-for-joint-war-fighting/, January 27. See also S.A. Whitehead and J.S. Wellman, 2021, “Joint All Domain Command and Control (JADC2),” Presentation to the Air Force ABMS Committee, February 5.
36 D. Vergun, 2021, “DoD Looking for Advanced Command, Control Solution,” DoD News, https://www.defense.gov/News/News-Stories/Article/Article/2646822/dod-looking-for-advanced-command-control-solution/, June 4.
37 A. Eversden, 2021, “With Austin’s Signature on JADC2 Strategy, Top General Says It’s ‘Delivery Time,’” C4ISRNet, https://www.c4isrnet.com/battlefield-tech/it-networks/2021/06/04/with-austins-signature-on-jadc2-strategy-top-general-says-its-delivery-time/, June 4.
Strategy that includes objectives, task transactions, milestones, service contributions (to include ABMS) and other efforts being undertaken by combatant commands and other DoD agencies. The near-term (FY 2022) focus will be on developing minimally viable products and enhancing capabilities such as DevSecOps, identity, credential, and access management (ICAM), zero trust (ZT), transport layer, and cloud.38 To ensure common software standards, the J6 is also working with the Joint Requirements Oversight Council (JROC) to mandate open software standards for ensuring cross-Service and cross-domain compatibility and interoperability across sub-systems through the use of common software interfaces.39 These collective efforts provide ABMS (along with Project Convergence and Project Overmatch) with a guiding foundation to support their respective development activities.
RECOMMENDATION 7: The Joint All-Domain Command and Control cross functional team should reach immediate agreement on a common data fabric and security levels of the data with data standards and tools defined at the Joint level. Without a common set of agreed upon open standards with known interface exchange requirements that do not limit innovation, the military Services risk developing incompatible and stove-piped solutions.
Containerization and Kubernetes
To enable agile development in a continuous integration/continuous delivery and deployment (CI/CD)40 environment, containerization is the optimal solution. Containers refer to a lightweight virtual machine that can be preconfigured and uploaded to a cloud or on-premises (on-prem) environment to immediately provide both the software capability and supporting operating system libraries and dependencies necessary to entirely support the capability.41 Expensive and time-consuming integration with different operating systems and hardware platforms are
___________________
38 L.C. Williams, 2021, “Pentagon Preps JADC2 Implementation Plan,” FCW, https://fcw.com/articles/2021/09/08/dod-jadc2-plan-implementation.aspx, September 8.
39 T. Hitchens, 2021, “Exclusive: ‘Do-or-Die’ JADC2 Summit to Crunch Common Data Standards.”
40 CI/CD is a method to frequently deliver apps by introducing automation into the stages of app development. The main concepts attributed to CI/CD are continuous integration, continuous delivery, and continuous deployment. See “What is CI/CD?” Red Hat, https://www.redhat.com/en/topics/devops/what-is-ci-cd, 2018. See also D. Samant, 2021, “7 Rules for Faster Releases with Containerized CI/CD,” Container Journal, https://containerjournal.com/features/7-rules-for-faster-releases-with-containerized-ci-cd/, March 29.
41 See IBM Cloud Education, 2021, “Containerization,” IBM Cloud Learn Hub, https://www.ibm.com/cloud/learn/containerization, June 23.
avoided by encapsulating all dependencies within the container. The production of a container with the software for CI/CD is referred to as containerization. Containerization is a well-established commercial practice and is supported by a number of government and commercial software packages that enable the construction, test and evaluation, and deployment of containers in an operational environment. This level of flexibility dramatically increases the confidence that an upgrade to specific capabilities within the context of a larger system such as ABMS can be achieved with less risk to overall mission requirements.
Within the DAF, open-source Kubernetes42 has been widely adopted to avoid vendor lock-in and to provide resilience, security, adaptability, automation, auto-scaling, and an abstraction layer. It has been successfully employed on the F-16 fighter jet and the U-2 reconnaissance aircraft to enable available on-board computing power to meet advanced system and software needs on demand.43 According to the former DAF’s Chief Software Officer (CSO), in the instance of the U-2 experimentation, “The successful combination of the U-2’s legacy computer system with the modern Kubernetes software was a critical milestone for the development of software containerization on existing Air Force weapon systems.”44
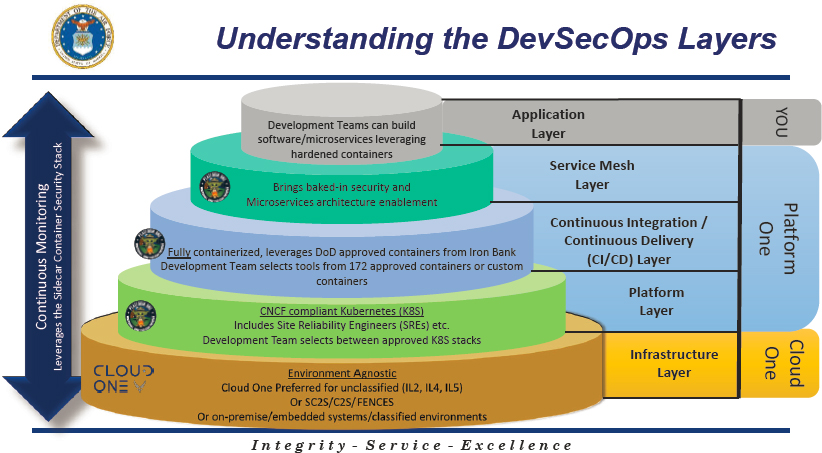
To achieve these experiments, the DAF had to create a portable technology stack that included (1) the Cloud One infrastructure layer, which provided a stable and secure common development, test, and production environment; (2) Platform One, which provided software enterprise services and hardened containers, CI/CD options, and the Istio45 service mesh layer that provided integrated, ZT security
___________________
42 Kubernetes is a portable, extensible open-source platform for managing containerized workloads and services that facilitates both declarative configuration and automation. See the Office of the Department of the U.S. Air Force Chief Software Officer, “Kubernetes,” https://software.af.mil/training/kubernetes/. The key difference between containers and Kubernetes is that containers are designed to code once and run anywhere, while Kubernetes provides the potential to orchestrate and manage all container resources from a single control plane. See Microsoft, “Kubernetes vs. Docker,” https://azure.microsoft.com/en-us/topic/kubernetes-vs-docker/.
43 See S. Miller, 2020, “Why the Air Force Put Kubernetes in an F-16,” https://gcn.com/articles/2020/01/07/af-kubernetes-f16.aspx, GCN, January 7, and K. Reichman, 2020, “In a First for the DoD, Kubernetes Installed on U-2 Dragon Lady,” Aviation Today, https://www.aviationtoday.com/2020/10/09/first-dod-kubernetes-installed-u-2-dragon-lady/, October 9.
44 Air Combat Command Public Affairs, 2020, “U-2 Federal Lab Achieves Flight with Kubernetes,” Air Force News, https://www.af.mil/News/Article-Display/Article/2375297/u-2-federal-lab-achieves-flight-with-kubernetes/, October 7.
45 Istio is a service mesh—a modernized service networking layer that provides a transparent and language-independent way to flexibly and easily automate application network functions. See Google Cloud, “What Is Istio?” https://cloud.google.com/learn/what-is-istio.
and the architecture to enable microservices;46 and (3) an application layer, which allowed development teams to easily construct reusable modular software or microservices that leveraged hardened containers to be used across teams.47Figure 2.4 illustrates the layers of this technology stack.
For ABMS, more specifically, Kubernetes is used to automate security and data analysis in development. During the February 2021 multi-nation on-ramp 4 experimentation that took place in Ramstein Air Base in Germany, the combination of a Kubernetes cluster, DevSecOps (development, security, and operations), deployment of an AI/ML application at the edge, and the ability to transfer development
___________________
46 Microservices (or microservices architecture) are a cloud native architectural approach in which a single application is composed of many loosely coupled and independently deployable smaller components or services. These services typically have their own technology stack, communicate with one another over a combination of REST APIs, event streaming, and message brokers; and are organized by business capability. See IBM Cloud Education, 2021, “Microservices,” IBM Cloud Learn Hub, https://www.ibm.com/cloud/learn/microservices, March 30, and Amazon Web Services, “What Are Microservices?” https://aws.amazon.com/microservices/.
47 S. Miller, 2020, “Why the Air Force Put Kubernetes in an F-16,” GCN, https://gcn.com/articles/2020/01/07/af-kubernetes-f16.aspx, January 7.
code from unclassified to classified networks was successfully demonstrated.48 The goal is to use Kubernetes to automate security by constantly scanning for anomalies and potential breaking points within ABMS. Once an anomaly or breaking point have been detected through Kubernetes, they may then be integrated within the container and deployed as any other capability advance. This obviates the need for a separate and distinct security mitigation process and fully integrates system security requirements into the DevSecOps development process. Furthermore, this approach would reduce the need for manual testing and minimize the potential for human error.
FINDING 6: Containerization and Kubernetes are mature open-source orchestration systems for enabling and securing agile development within a CI/CD environment.
RECOMMENDATION 8: In coordination with the Department of the Air Force Chief Software Officer, the Department of the Air Force Chief Architect’s Office and the Department of the Air Force Rapid Capabilities Office should expand the use of containerization and Kubernetes for continuous Advanced Battle Management System development and for detecting and mitigating security vulnerabilities.
SOFTWARE CONSIDERATIONS
ABMS requires the complex integration of various independently evolving, customized weapon-specific software elements. Together, they are envisioned to support a highly distributed framework of sensing, timely aggregation, and analysis functions to provide enhanced decision-making capabilities to fight and defend with agility and resilience. Shared information with heterogeneous physical, technical, and temporal characteristics must be standardized, or at least translatable and interoperable, to facilitate timely and accurate decision-making. Coordinated and distributed actuation, defined as the application of weapons effects, are also needed to produce coherent lethal effects. Moreover, legacy systems will have to be integrated in a coherent, phased, and cost-effective manner.
The software needed to support such an integrated and multi-layered C2 framework will likely evolve as new operational challenges and adversarial strategies change over time. This will require the software to be agile, adaptable, modifiable,
___________________
48 See AWS (Amazon Web Services), 2021, “Bringing Cloud Capability to the Air Force at the ‘Speed of Mission Need,’”AWS Public Sector Blog, https://aws.amazon.com/blogs/publicsector/bringing-cloud-air-force-speed-of-mission-need/, May 7.
and secure. Rigorous testing to evaluate, verify, and improve software performance and reduce development costs will also be critical.
Application Software and DevSecOps
Modern day applications require the most up-to-date development, security, and operations (DevSecOps)49 process, including automated security tools and automated test and deployment. Rapid advances in handheld digital devices (with integrated communication, computation capabilities, and impressive storage encrypted with biometrics and other means) have ushered in an explosive growth in innovative tools with low barriers to transform insights to prototypes and to process data at the tactical edge. Harvesting this collection of viable ideas into workable products is possible with the DevSecOps methodology, where innovators, developers, integrators, and end users all interact in frequent cycles that build upon each other.
The goal of the application environment would then be to create a model-based software engineering system that steadily combines evolving innovation, acquisition, and sustainment processes; provides telemetry and feedback from deployed code that updates the model; generates code automatically; provides automated testing and integration; and deploys the code. Any automated code development without in-depth human participation during the development process is likely to result in limited operational latitude and increased vulnerabilities. Knowledge engineering tools do exist, but must be incorporated in the software development process.
The complexity and evolving nature of ABMS requires a software development approach that is open, agile, secure, and adaptive. The DAF’s CSO has taken steps to shift the department from a traditional waterfall software development approach, which typically takes anywhere from 3 to 10 years to execute, toward more agile and secure software development methodologies. In coordination with the Office of the Under Secretary of Defense for Acquisition and Sustainment (OUSD[A&S]), the DoD’s Chief Information Officer (CIO), the Defense Information Systems Agency (DISA), and the other military Services, the DAF CSO has implemented the DoD Enterprise DevSecOps Initiative (DSOP) that detailed “a combination of
___________________
49 DevSecOps—short for development, security, and operations—automates the integration of security at every phase of the software development life cycle, from initial design through integration, testing, deployment, and software delivery. IBM Cloud Education, 2020, “DevSecOps,” IBM Cloud Learn Hub, https://www.ibm.com/cloud/learn/devsecops, July 30.
Kubernetes, Istio, knative,50 and an internally developed specification for ‘hardening’ containers with a strict set of security requirements as the default software development platform across the military.”51Figure 2.5 describes this initiative.
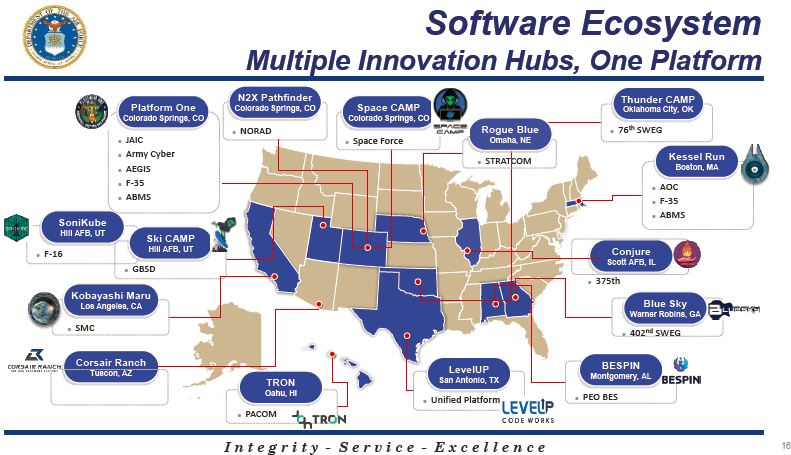
By transitioning to this enterprise approach, the DAF is able to deploy hardened software factories on existing or new environments (to include classified, disconnected, and clouds) within days instead of years; establish multiple DevSecOps pipelines with various options; enable rapid prototyping and faster deployment for weapons, C4ISR, and business systems; provide continuous learning and feedback from end users and warfighters; aid in security repairs within minutes; generate a holistic and integrated cybersecurity stack to allow complete visibility of all assets, software security state, and infrastructure as code; and facilitate adoption of microservices by using the Microservices Architecture.52 The objective is to establish a software ecosystem with multiple innovation hubs through the CloudOne infrastructure that undergirds ABMS.53Figure 2.6 depicts the locations of these innovation centers that comprise the current DAF software ecosystem.
The Shadow Operations Center (ShOC-N) at Nellis Air Force Base has been designated as the lead agency responsible for creating and testing information technology applications for the ABMS.54 The use of DevSecOps is central to ABMS’s development by assembling software developers, operators, and end users in a “virtual and physical playground for information collection and sense-making using data.”55 This integration will enable quick delivery of operationally relevant and cyber secure software to troops. In June 2021, ShOC-N hosted the JADC2 21-1, J6 campaign, which convened experts from all domains and connected 17 different DoD battle laboratories to exchange operationally relevant data. Using a
___________________
50 Knative is an extension of the Kubernetes container orchestration platform that enables server-less workloads to run on Kubernetes clusters, and provides tools and utilities that make building, deploying, and managing containerized applications within Kubernetes a simpler and more “native-to-Kubernetes” experience. See IBM Cloud Education, 2021, “Knative,” IBM Cloud Learn Hub, https://www.ibm.com/cloud/learn/knative, June 17.
51 T. Krazit, 2019, “How the U.S. Air Force Deployed Kubernetes and Istio on an F-16 in 45 Days,” The New Stack, https://thenewstack.io/how-the-u-s-air-force-deployed-kubernetes-and-istio-on-an-f-16-in-45-days/, December 24.
52 Office of the DAF Chief Software Officer, “DoD Enterprise DevSecOps Initiative (DSOP),” https://software.af.mil/dsop/#valuefordod.
53 For more on Cloud One, see Office of the DAF Chief Software Officer, “Cloud One,” https://software.af.mil/team/cloud-one/, and 2021, “Cloud One: Enabling Cloud for Almost Any Department of Defense Use Case,” Air Force Magazine, https://www.airforcemag.com/cloud-one-enabling-cloud-for-almost-any-department-of-defense-use-case/, July 2.
54 See C. Collins, 2021, “Air Force Laboratory Applies DevSecOps to Support Battle Management System Development,” ExecutiveGov Daily, https://www.executivegov.com/2021/06/air-force-laboratory-applies-devsecops-to-support-battle-management-system-development/, June 24.
55 “ShOC-N at Nellis Air Force Base Supports ABMS Development,” Air Force Technology, https://www.airforce-technology.com/news/shoc-n-nellis-air-force-base-abms-development/, June 24.

combination of DevSecOps and experimental software applications,56 developers were able to assist “warfighters [to] visualize and make sense of the cyber domain and gain decision advantage over the adversary … and to enable better understanding of the cyber domain from all branches’ perspectives.”57 By leveraging emerging and experimental technologies to provide real-time feedback to software engineers, this allowed them to make rapid adjustments and improvements and shorten the timeline for development.
The next step is to integrate AI/ML to enable big data processing and predictive analytics. According to the Commander, U.S. Northern Command (USNORTHCOM), the key to ensuring victory in the future all-domain battlespace is through predictive analysis. “We see JADC2 as absolutely core to the way we’re
___________________
56 Project IKE is a prototyping effort that is used to map networks, assess the readiness of cyber teams, and command forces in cyberspace. The project began in 2013 at DARPA under the name Plan X and was moved to the DoD’s Strategic Capabilities Office (SCO) in 2019 and officially transitioned as a program under the Joint Cyber Command and Control (JCC2) program management office. See M. Pomerleau, 2021, “A Cyber Tool That Started at DARPA Moves to Cyber Command,” C4ISRNet, https://www.c4isrnet.com/cyber/2021/04/20/a-cyber-tool-that-started-at-darpa-moves-to-cyber-command/, April 20.
57 N. Mathison, 2021, “Nellis AFB Empowers Warfighters via DevSecOps,” Air Force News, https://www.af.mil/News/Article-Display/Article/2668568/nellis-afb-empowers-warfighters-via-devsecops/, June 23.
going defend the homeland … and the part that I think is going to be so incredibly game-changing is the ability for us to really use predictive analysis and inform our decisions going into the future.”58 More specifically within ABMS, predictive analytics will enable developers to “get digital feedback on where the information is going, where the data’s being corrupted, where are we having problems getting enough information through, and how is that impacting the decision making.”59
FINDING 7: The use of DevSecOps within the existing software factories has been effective at creating a CI/CD environment for some ABMS development.
RECOMMENDATION 9: The Department of the Air Force Chief Architect’s Office and the Department of the Air Force Rapid Capabilities Office should adopt development, security, and operations as the common development environment using containerization and continuous integration/continuous delivery across all of the Advanced Battle Management System.
___________________
58 T. Hitchens, 2020, “The Key to All-Domain Warfare Is ‘Predictive Analysis;’ Gen. O’Shaughnessy,” Breaking Defense, https://breakingdefense.com/2020/05/the-key-to-all-domain-warfare-is-predictive-analysis-gen-oshaughnessy/, May 5.
59 N. Mathison, 2020, “Nellis AFB Empowers Warfighters via DevSecOps.”
Data Rights
In defense acquisition, the tendency is for the government to ask industry for access to all data rights to include both technical and computer software data. Technical data includes “any recorded information of a scientific or technical nature (e.g., product design or maintenance data, computer databases, and computer software documentation”).60 Computer software includes the “executable code, source code, code listing, design details, processes, flow charts, and related material that would enable the software to be reproduced, recreated, or recompiled.”61 Industry commonly retains title to technical data and computer software, but conveys a licensing arrangement for government agencies to use such data through one of three categories: unlimited rights, limited rights (technical data) or restricted rights (computer software), and government purpose rights.62
For ABMS, where the architecture is comprised of an amalgam of hardware, software, legacy systems, and other C2 infrastructure, owning or accessing data rights may not be feasible nor sustainable. Instead, focus should be given to owning the rights (instead of all intellectual property rights) to the interfaces that connect these various components.63 This is particularly relevant for systems using open system architectures (OSA). “A major benefit of the modular/open systems approach from a data rights perspective is that the performance and interface information should meet the DFARS [Defense Federal Acquisition Regulation Supplement] criteria of form, fit, and function data and thereby have no government data rights restrictions.”64
By acquiring and maintaining the performance and interface requirements, the government would be able to use them to procure and support modular solutions
___________________
60 DISA (Defense Information Systems Agency), “Data Rights,” https://disa.mil/about/legal-and-regulatory/datarights-ip/datarights, accessed September 18, 2021.
61 DISA (Defense Information Systems Agency), “Data Rights,” https://disa.mil/about/legal-and-regulatory/datarights-ip/datarights, accessed September 18, 2021. See also Carnegie Mellon University, “Governing Rights in Technical Data and Computer Software,” https://www.cmu.edu/osp/contracts/contracts-process/rights.html, accessed September 18, 2021.
62 See W.J. DeVecchio, 2018, “Taking the Mystery Out of Data Rights,” Thomson Reuters, Issue 18-8, https://media2.mofo.com/documents/180700-mystery-data-rights.pdf, July, and S.B. Cassidy, A.B. Hastings, and J.L. Plitsch, 2017, “What Every Company Should Know About IP Rights When Selling to the US Government,” Landslide, 9(6), July–August.
63 See U.S. Department of Defense Instruction 5010.44, 2019, “Intellectual Property (IP) Acquisition and Licensing,” Office of the Under Secretary of Defense for Acquisition and Sustainment, https://www.esd.whs.mil/Portals/54/Documents/DD/issuances/dodi/501044p.PDF, accessed November 26, 2021.
64 Office of the Assistant Secretary of the Army for Acquisition, Technology, and Logistics, 2015, “Army Data and Data Rights (D&DR) Guide,” p. 35, https://www.acq.osd.mil/dpap/cpic/cp/docs/Army_Data_and_Data_Rights_Guide_1st_Edition_4_Aug_2015.pdf, August.
from multiple vendors. This would in turn reduce the dependency on sole source acquisitions or costly procurements of licensing rights to privately developed technology or computer software. “While any weapon system can potentially benefit from an OSA approach, sub-systems expected to contain proprietary technology, have frequent technology updates, or are available from multiple sources, are particularly strong candidates. Another reason to consider the modular/open system approach would be if the sub-system were expected to have data rights restrictions, which are not likely to be mitigated through the acquisition of additional data rights.”65
RECOMMENDATION 10: For modular open system designs with robust interface specifications, the Department of the Air Force Rapid Capabilities Office should acquire performance and interface requirements instead of all intellectual property rights.
SECURITY
Network Reliability, Resiliency, and Fault Tolerance
The success of ABMS during any engagement relies on the communications infrastructure. Much of this infrastructure consists of data networks that are responsible for transporting essential data from sensors to computation, decision-making, execution, and data storage nodes. As a critical element of ABMS, it is important to monitor real-time status of the state and resilience of the entire network infrastructure at all times. Should there be any disruption or degradation of network performance, redundant and resilient systems must automatically reroute and reconstitute network communications to maintain ABMS capabilities. The ability to operate with little or no communication connectivity or bandwidth is also important and should be considered as part of ABMS’s overall security design.
The defined performance of the network is often structured around real-time measures of bandwidth and latency—both within individual point-to-point links of the network and across end-to-end communications. The specific acceptable metrics for bandwidth and latency are defined in the context of the tactical status of ABMS capabilities. During lower-level engagements, some degradation of bandwidth and latency may be acceptable. However, during higher-level engagements, where cyberattacks are more likely, bandwidth must be elevated and latency reduced, or at a minimal, maintained. Thus, the question of when the network can no longer support volume and timeliness of priority traffic is a dynamic question.
___________________
65 Ibid.
It must also reflect the degree to which it serves the overall ABMS goal of enabling the DAF to operate within the adversary’s observe-orient-decide-act (OODA) loop.
The dynamic nature of the network’s minimum performance requirements creates a new set of challenges for when redundant and resilient communications structures are employed. Although the minimum performance is dynamic, it is not ad hoc, but predefined based on the C2 requirements of ABMS during engagement. Once defined, ABMS capabilities will be able to automatically adjust network capabilities (e.g., using software defined networks and network functions virtualization) to maintain a minimum performance profile at all times.
Defining minimum performance characteristics for each operational scenario will define how the network breaks and what the contingency will be for each scenario. It is important to note that the source of network failure may be forced by the adversary and resilient and redundant capabilities may be anticipated by the adversary, as well. Any contingency must therefore realistically address the threat model, where the adversary will directly attack the network and communications infrastructure necessary to enable ABMS.
As a contributor to both JADC2 and the nation’s NC3 capability, security, reliability, and resiliency should be essential attributes of ABMS. According to Representative Adam Smith (D-WA), Chairman of the House Armed Services Committee, “We have to be able to protect [our command and control] systems and ideally we have to be able to build a system so that we can make our adversary systems more vulnerable. That really needs to be the focus.”66 The Vice Chairman of the Joint Chiefs of Staff added, “It’s important to realize that JADC2 and NC3 are intertwined because … NC3 will operate in significant elements of JADC2. Therefore, NC3 has to inform JADC2 and JADC2 has to inform NC3. You have to have that interface back and forth, and that’s been recognized.”67 As a C2 system that is able to bridge different security classifications through crossdomainONE,68 ABMS will need to provide the secure, reliable, and resilient interfaces to connect JADC2 and NC3. This will require the participation of the U.S. Strategic Command (USSTRATCOM).
As detailed in Chapter 1, current Air Operations Center (AOC) modules were designed and based on now-dated technologies—including those used for cybersecurity. The incremental development and evolution of safeguarding AOC compo-
___________________
66 L.C. Williams, 2021, “JADC2 Needs to Be Pentagon’s ‘Big Bet,’ Flournoy Says,” FCW, https://fcw.com/articles/2021/03/30/jadc2-big-bet-flournoy.aspx, March 30.
67 C. Clark, 2020, “Nuclear C3 Goes All Domain: Gen. Hyten,” Breaking Defense, https://breakingdefense.com/2020/02/nuclear-c3-goes-all-domain-gen-hyten/, February 20.
68 CrossdomainONE is a platform that would seamlessly and securely move data up and down security classification boundaries. See T. Hitchens, 2019, “First Multi Domain C2 Exercise Planned: ‘ABMS Onramp,’” Breaking Defense, https://breakingdefense.com/2019/12/first-multi-domain-c2-exercise-planned-cross-domain-one/, December 6.
nents resulted in a patchwork of varying constructs, processes, and completeness. Furthermore, the design and development of the current AOC were executed in the context of a former threat environment—one far different from what operators encounter today. The battlespaces of today and the future are highly complex and will engage all domains at the strategic, operational, and tactical levels. What is most difficult to anticipate and prepare for is competition conducted in the “gray zone” between peace and war.69 The unpredictability and complexity of all-domain warfare require confidentiality, integrity, and availability of the operational environment in which ABMS supports.
To accomplish this, a security engineering construct and associated implementation strategy from a multi-pronged approach to consider the operational, technical, and risk assessment (based on a realistic assessment of the threat environment and technical limitations) perspectives should be developed. The security construct should identify vulnerabilities and support:
- Security: ABMS must provide secure and accurate data and be trusted by operators across all domains;
- Reliability: ABMS capabilities must perform as advertised and made available, when needed, and;
- Resilience: ABMS must be able to perform in anti-access and degraded environments and be able to rapidly reconstitute, as needed.
Ultimately, security engineering must be designed, implemented, and evaluated against the current operational and technical baseline. It cannot be solely a technical evaluation.
FINDING 8: ABMS—and the operational forces that use it—must be resilient to technical failures and limitations plus against adversarial attacks.
FINDING 9: ABMS bandwidth and latency capacities need to adjust to changing operating conditions and demands. For example, during high-level engagements, where cyberattacks are more likely, bandwidth must be elevated and latency reduced or at least maintained or in support of critical functions,
___________________
69 “Gray zone” refers to competitive interactions among and within state and non-state actors that fall between traditional war and peace. It is characterized by ambiguity about the nature of the conflict, opacity of the parties involved, or uncertainty about the relevant policy and legal frameworks. Adversaries seek competitive advantages through military, diplomatic, information, and economic tactics. See J.L. Votel, C.T. Cleveland, C.T. Connett, and W. Irwin, 2016, “Unconventional Warfare in the Gray Zone,” Joint Forces Quarterly, 80(1st quarter) 101–109. See also L.J. Morris, M.J. Mazarr, J.W. Hornung, S. Pezard, A. Binnendijk, and M. Kepe, 2019, “Gaining Competitive Advantage in the Gray Zone,” RAND Corporation, https://www.rand.org/pubs/research_reports/RR2942.html.
associated data transfer need to be prioritized, where bandwidth availability is challenged.
RECOMMENDATION 11: The Department of the Air Force Chief Architect’s Office and the Department of the Air Force Rapid Capabilities Office should design resilience into the Advanced Battle Management System architecture and specify dynamic criteria for needed performance.
Multi-Level Security
Multi-level security (MLS) refers to “processing information with different classifications and categories that simultaneously permits access by users with different security clearances and denies access to users who lack authorization.”70 Such systems would enable individual platforms to process information at different security levels and move data between these levels, as appropriate.71 The advantages of MLS are to store and share data of mixed classification and to provide secure access to multiple classifications of data to those who have the proper authorizations.
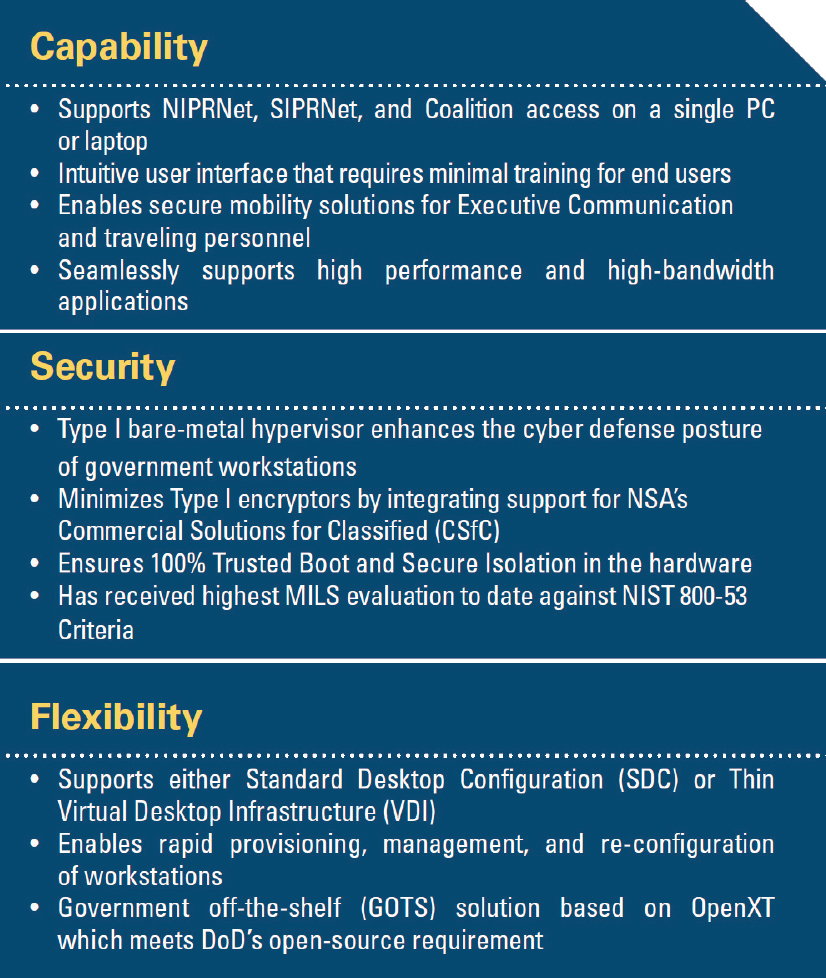
ABMS has incorporated this MLS approach through CrossDomainONE, the platform that enables data to move across classification levels and the ABMS DeviceOne SecureView (ADSV) established by the Air Force Research Laboratory (AFRL).72 ADSV supports ABMS and JADC2 by connecting sensors and shooters and enabling data transfer and/or access to both multi- and cross-domain data. Figure 2.7 summarizes the key features of ADSV.
The committee views CrossDomainONE and ADSV as notable first steps in enhancing MLS protection for ABMS. However, ADSV’s use of hypervisor—a virtual machine monitor—for security enhancement may expose ABMS to potential vulnerabilities and risks. A critical next step is to automate data transfer and integration. Data from sensors and platforms, particularly for highly classified intelligence and sensor data, are rarely meta-tagged (labeled) to allow a MLS system
___________________
70 Information Technology Laboratory Computer Security Resource Center, “Multi-Level Security (MLS),” National Institute of Standards and Technology (NIST), https://csrc.nist.gov/glossary/term/multi_level_security.
71 For more on MLS, see E. Boebert, 2008, “Multilevel Security,” pp. 239–273 in Security Engineering: A Guide to Building Dependable Distributed Systems, Second Edition (R. Anderson, ed.), Wiley, http://www.cse.psu.edu/~pdm12/cse597g-f15/readings/cse597g-mls_reading.pdf.
72 SecureView® cross domain access solution allows users access to multiple independent levels of security (MILS) on a single workstation and provides immediate access to mission critical data. It was developed by the Air Force Research Laboratory to provide the Intelligence Community (IC) with unparalleled security and protection against data exfiltration. See AFRL (Air Force Research Laboratory), “Advanced Battle Management System (ABMS) DeviceOne SecureView,” https://afresearchlab.com/technology/successstories/advanced-battle-management-system-abms-deviceone-secureview/.
to effectively evaluate a machine-to-machine transport and integration of data. To address this technical gap, platforms and systems should be able to operate at different classification levels to ensure both compatibility with other Services and multi-national partners and allies operating in the JADC2 framework. Sanitizing subsets of highly classified information for release to operational users should also be addressed in MLS design.
Cybersecurity and Zero Trust
Security is critical to ABMS. As such, the storage, processing, and communication of data must be equally secure and reliable, and communication must be enabled and timely across the enterprise. Designing a holistic cybersecurity architecture for all of ABMS and its supporting components is essential; piecemeal development will only result in security gaps and seams that could (and will) be exploited by our adversaries. According to the Deputy Commander of the 16th Air Force/Air Forces Cyber (the Air Force’s information warfare command), “The only way we’re going to be able to really conduct JADC2 is through a defended, resilient, fully capable fabric, warfighting communication fabric … we’re going to have to not just enable that and design it and operate it, we’re going to have to defend it because the adversary is going to try to take that away from us.”73
To address this security challenge, ABMS developers are moving toward the adoption of zero trust (ZT), an architecture that provides authenticated and authorized access between services without relying on the location of those services within a network infrastructure.74 ZT is not a specific set of technologies, but rather an architectural construct that requires authentication and authorization for all interactions between individual nodes in a distributed system. Most commonly, ZT relates to deperimeterization (also, de-perimeterization), the ability to protect an organization’s systems and data on multiple levels through a mix of encryption, secure computer protocols, secure computer systems, and data-level authentication. Deperimeterization reduces or removes the need to operate within an enterprise
___________________
73 M. Pomerleau, 2020, “Air Force Looking at How to Defend JADC2 Systems,” DefenseNews, https://www.defensenews.com/digital-show-dailies/air-force-association/2020/09/16/air-force-looking-at-how-to-defend-jadc2-systems/, September 16.
74 See S. Rose, O. Borchert, S. Mitchell, and S. Connelly, 2020, “Zero Trust Architecture,” NIST Special Publication 800-207, https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf,August. For more on zero trust in the federal government, see S. Vetter and A. Stewart, 2020, “Zero Trust: Evolving the Federal Government’s Security Model!” PSC Magazine, https://www.pscouncil.org/a/Content/2020/Zero_Trust__Evolving_the_Federal_Government_s_Security_Model.aspx. See also, C. Clark, 2020, “Dunlap on Zero Trust, Agility, and ADO Cybersecurity,” Breaking Defense, https://breakingdefense.com/2020/11/dunlap-on-zero-trust-agility-ado-cybersecurity/, November 24.
network by providing access between a user and distributed services such as data, specialized computing, sensors, and location services.75
For ABMS, ZT is being used on deviceONE, which certifies credentials are checked at every layer of the system. It is important for the DAF Chief Architect and the Air Force Rapid Capabilities Office to expand the use of ZT and other cybersecurity protections across all ABMS capabilities to ensure maximum safeguards against cyber vulnerabilities.
While the concept of ZT has been in existence for a while, recent improvements in support technologies to connect a wide variety of services through multi-factor authentication (MFA), authorization services, and other security capabilities have enabled wider adoption of ZT. ZT provides authenticated and authorized access between dispersed platforms and users to enable command, control, and communications within a dynamic network environment. It is also frequently used in cloud computing environments, which is suitable for ABMS’s Internet of Military Things, to provide trusted access from endpoints in untrustworthy network environments to a cloud computing and data environment.
However, adopting ZT architecture not only for ABMS, but across the entire DoD JADC2 enterprise may be fraught with challenges. ZT technology that is able to address the enormity of DoD-wide C4ISR in support of the spectrum of military operations has not been proven sufficiently robust. Moreover, the wide variety of capabilities and requirements that necessitate coordination across the JWC demands creating an authorization service that would remain current while connecting all users, data, and technical platforms. The forthcoming JADC2 Implementation Strategy does encourage focusing greater attention on ZT, but it falls short in addressing the technical and logistics challenges of adopting ZT across disjointed and disconnected users and systems that comprise the DoD enterprise. The strategy also does not address specific authorities needed to access and actuate systems in JADC, which is essential in human-machine communications. Thus, while ZT should remain an integral component of ABMS, the overall ABMS (and JADC2) security architecture will require well-defined authentication and authorization requirements between platforms and the human-computer interface (HCI).
Another consideration is establishing cybersecurity for legacy systems that possess varying and irregular degrees of vulnerabilities owing to their outdated hardware, software, and operating technologies. These systems are generally incompatible with security features surrounding access, including MFA, single-sign
___________________
75 For more on deperimeterization, see SC Staff, 2004, “Jericho Forum Brings Its Deperimeter Concept to U.S.,” SC Media, https://www.scmagazine.com/news/-/jericho-forum-brings-its-deperimeterization-concept-to-u-s, July 30, and J. Kindervag, 2016, “No More Chewy Centers: The Zero Trust Model of Information Security,” Forrester, https://crystaltechnologies.com/wp-content/uploads/2017/12/forrester-zero-trust-model-information-security.pdf, March 23.
on, and role-based access. They also lack sufficient encryption techniques necessary for protecting digital data confidentiality. Establishing connections with these legacy systems through the rubric of ABMS will require at a minimum, performing vulnerability scans to identify and address all vulnerability gaps, adopting cybersecurity controls for systems that are networked with ABMS components, and updating the latest system patches to minimize exposure.76
It is important to recognize that while ZT provides one layer of security protection, a comprehensive cybersecurity plan for the entire ABMS architecture is warranted.77 This requires both offensive and defense planning to include red teaming ABMS’s cyber defenses to ensure their resiliency to protect against adversarial penetrations and attacks. The Air Force’s Mission Defense Teams, specialized defensive cyber teams tasked to protect critical Air Force missions and installations, should be leveraged.78 Additionally, Congress has recently directed and authorized defense cyber personnel to operate outside of U.S. networks. This measure will enable U.S. Cyber Command (USCYBERCOM) to better understand the types of malware adversaries are employing and the types of operations they might be planning against U.S. networks through its Hunt Forward missions.79 According to the Commander of USCYBERCOM, “We cannot afford to wait for cyberattacks
___________________
76 See S. Crozier Cox and H. Levinson, 2019, “Cybersecurity Engineering for Legacy Systems: 6 Recommendations,” Carnegie Mellon University Software Engineering Institute, https://insights.sei.cmu.edu/blog/cybersecurity-engineering-for-legacy-systems-6-recommendations/, August 26, and D. Snyder, J.D. Powers, E. Bodine-Baron, B. Fox, L. Kendrick, and M.H. Powell, 2015, “Improving the Cybersecurity of U.S. Air Force Military Systems Throughout Their Life Cycles,” RAND Corporation, https://www.rand.org/content/dam/rand/pubs/research_reports/RR1000/RR1007/RAND_RR1007.pdf.
77 See D. Snyder, J.D. Powers, E. Bodine-Baron, B. Fox, L. Kendrick, and M.H. Powell, 2015, “Improving the Cybersecurity of U.S. Air Force Military Systems Throughout Their Life Cycles,” and 2021, “Top 11 Most Powerful Cybersecurity Software Tools in 2021,” Software Testing Help, https://www.softwaretestinghelp.com/cybersecurity-software-tools/, October 4.
78 See H. Stevens, 2019, “Mission Defense Team: Defending the RPA network,” Air Combat Command News, https://www.acc.af.mil/News/Article-Display/Article/1986201/mission-defense-team-defending-the-rpa-network/, October 10, and M. Pomerleau, 2019, “When Malware Hits an F-16, Call These New Air Force Cyber Teams,” C4ISRNet, https://www.c4isrnet.com/dod/air-force/2019/04/17/when-malware-hits-an-f-16-call-these-new-air-force-cyber-teams/, April 17.
79 Hunt Forward missions are U.S. cyber protection teams, who operate at the request of host nations to partner with them in conducting defensive cyber operations on their (host nation) networks. See E. Tucker, 2020, “Military’s Top Cyber Official Defends More Aggressive Stance,” Military Times, https://www.militarytimes.com/news/your-military/2020/08/25/militarys-top-cyber-official-defends-more-aggressive-stance/, August 25. See also U.S. Cyber Command, 2020, “United States Cyber Command Technical Challenge Problem Set,” https://www.cybercom.mil/Portals/56/Documents/2020%20Tech%20Challenge%20Problems%20UNCLASS%20CAO-PAO%20FINAL.pdf?ver=2020-08-18-160721-850.
to affect our military networks. We learned that defending our military networks requires executing operations outside our military networks. The threat evolved, and we evolved to meet it.”80
FINDING 10: Offensive and defensive cybersecurity protection is essential for ABMS and must be holistically and seamlessly integrated into the entire system architecture from the start. Approaching cybersecurity in a fragmented approach or as an afterthought will only generate vulnerability gaps that will be exploited by malicious actors.
FINDING 11: ZT holds promise, but is not currently sufficiently mature to be the singular security protection in military C2 systems like ABMS.
RECOMMENDATION 12: The Joint Staff’s J6, the Department of the Air Force, and the broader U.S. Department of Defense community should establish and implement a robust enterprise-wide offensive and defensive cybersecurity strategy for Joint All-Domain Command and Control (JADC2) and the Advanced Battle Management System. Security is a fundamental requirement that must be designed and fully integrated into the all JADC2-supporting systems’ architecture from the start.
RECOMMENDATION 13: The Department of the Air Force Rapid Capabilities Office should apply zero trust (ZT) in stages as technologies mature and integrate ZT services to include the use of multi-factor authentication across all of the Advanced Battle Management System.
RECOMMENDATION 14: In addition to adopting zero trust, the Department of the Air Force Rapid Capabilities Office should leverage the best available mature cybersecurity practices and capabilities, including multi-factor authentication; identity, credential, and access management; encryption; penetration testing; managed detection services; behavior monitoring applications; among others.
RECOMMENDATION 15: The Department of the Air Force Rapid Capabilities Office (DAF RCO) should employ the Air Force’s Mission Defense Teams to red team the Advanced Battle Management System’s cyber defenses against attacks from malicious actors. Based on these red team
___________________
80 P.M. Nakasone and M. Sulmeyer, 2020, “How to Compete in Cyberspace,” Foreign Affairs, https://www.foreignaffairs.com/articles/united-states/2020-08-25/cybersecurity, August 25.
exercises, the DAF RCO should address vulnerabilities by bolstering and enhancing cyber defenses accordingly.
RECOMMENDATION 16: The Department of the Air Force Chief Architect’s Office and the Department of the Air Force Rapid Capabilities Office should work in partnership with the U.S. Cyber Command to address Internet of Things defense and other cyber vulnerabilities and exploits that are highlighted in the “United States Cyber Command Technical Challenge Problem Set” document.
TESTING AND MODELING
Test and Evaluation
Risk reduction is the primary objective for testing and evaluation (T&E). By assessing system performance against warfighter and operator requirements, early detection and mitigation of system vulnerabilities, deficiencies, and performance issues may be accomplished. As part of the broader systems engineering process (SEP), the committee deems T&E as essential and should be conducted throughout ABMS development and deployment cycles, particularly as new products and services are introduced into the overall ecosystem.
According to the Chief Architect of the DAF, ABMS is designed to be evolving to incorporate and utilize new technologies as they emerge. Developmental testing is thus integrated into the broader DevSecOps process, while operational testing is conducted through large scale on-ramp demonstrations and exercises.81 The first field test of ABMS took place from December 16–18, 2019, and involved the Air Force, Navy, and Army operating under a homeland defense scenario. The on-ramp exercise tested new software, communications equipment, and a mesh network to transmit time-sensitive information between fighters, destroyers, ground forces, and command centers. “Today’s demo is our first time demonstrating internet-of-things connectivity across the joint force. Cloud, mesh networking and software-defined systems were the stars of the show, all developed at commercial Internet speeds … the goal is to move quickly and deliver quickly.”82
Subsequent operational field tests occurred from August 31 to September 3, 2020 (on-ramp 2 that focused on classified and unclassified communications and testing of 28 ABMS “ONE” product lines to connect sensors to weapons through
___________________
81 P. Dunlap, 2020, “ABMS Overview,” Presentation to the Air Force ABMS Committee, October 30.
82 See C. Bousie and C. Pope, 2019, “Military Conducts First Test of Advanced Battle Management System,” Air Force News, https://www.eglin.af.mil/News/Article-Display/Article/2047058/military-conducts-first-test-of-advanced-battle-management-system/, December 26.
a secure data network);83 September 15 to September 25, 2020 (on-ramp 3 that tested integrating non-traditional battle management C2 nodes, such as the KC-46 tanker, with ABMS to provide seamless detection, tracking, and engagement in all domains);84 and late February 2021 (on-ramp 4 that tested and observed the ability of the joint force, allies and multi-national partners to integrate and provide command and control across multiple networks to multiple force capabilities).85 An on-ramp 5 was originally planned for the Pacific Theater, but was canceled in March 2021 owing to budget constraints.86
Additionally, Air Force and Army leaders signed a 2-year inter-Service agreement in September 2020 to work jointly to establish mutual standards for data sharing and service interfacing for ensuring all new communication equipment, networks, and AI are compatible with one another. The agreement also impacts joint force training, exercises, and demonstrations.87
While these activities are noteworthy, recent reductions in the ABMS budget are hampering the DAF’s ability to continue with large scale live exercises and capability demonstrations. Additionally, the Secretary of the Air Force has directed focusing more attention on making “true” operational improvements vice prototyping and experimentation.88 For these reasons, the committee determines that ABMS may need to retailor future testing through a combination of model-based systems engineering (MBSE), modeling and simulation (M&S), and the use of digital twins.
FINDING 12: Developmental testing should be focused on detecting and remedying errors in designing or implementing a system; operational testing
___________________
83 D. Henley, 2020, “Advanced Battle Management System OnRamp #2, Accelerating Data-Sharing and Decision-Making,” Air Force News, https://www.acc.af.mil/News/Article-Display/Article/2358597/advanced-battle-management-system-onramp-2-accelerating-data-sharing-and-decisi/, September 22.
84 D. Henley, 2020, “KC-46 Tests Command and Control During ABMS Onramp 3,” Air Force News, https://www.acc.af.mil/News/Article-Display/Article/2413971/kc-46-tests-command-and-control-during-abms-onramp-3/, November 12.
85 B.W. Everstine, 2021, “USAFE’s ABMS On-Ramp Included Partner Nations, Base Defense Scenario,” Air Force Magazine, https://www.airforcemag.com/usafes-abms-on-ramp-included-partner-nations-base-defense-scenario/, March 1, and U.S. Air Forces in Europe and Air Force Africa, 2021, “USAFE Completes CJADC2 Demonstration,” USAFE Press Release, https://www.usafe.af.mil/News/Press-Releases/Article/2518755/usafe-completes-cjadc2-demonstration/, March 1.
86 B.W. Everstine, 2021, “Pacific ABMS On-Ramp Canceled Due to Budget Cuts,” Air Force Magazine, https://www.airforcemag.com/pacific-abms-on-ramp-cancelled-due-to-budget-cuts/, March 17.
87 G. Reim, 2020, “US Army and USAF to Jointly Develop Battlefield Network, Called, called CJADC2,” Flight Global, https://www.flightglobal.com/defence/us-army-and-usaf-to-jointly-develop-battlefield-network-called-cjadc2/140450.article, October 2.
88 See T. Hitchens, 2021, “Air Force ABMS Refocus: Capabilities and Kit, Not Experiments,” Breaking Defense, https://breakingdefense.com/2021/09/air-force-abms-refocus-capabilities-and-kit-not-experiments/, September 20.
should be focused on the ability of the system to meet the user’s requirements. Both developmental and operational testing—augmented with digital and MBSE, M&S, and digital twins—must be continuously executed and evaluated across ABMS to maintain the DAF’s technological advantage in an increasingly sophisticated threat environment.
Model-Based Systems Engineering
In 2016, the DoD introduced “Systems Engineering Digital Engineering Fundamentals” to encourage the use of MBSE practices within a digital ecosystem.89 MBSE is defined as the “formalized application of modeling to support system requirements, design, analysis, verification and validation activities beginning in the conceptual design phase and continuing throughout development and later life cycle phases.”90 More simply, MBSE is used to support requirements, design, analysis, verification, and validation associated with the development of complex systems.91 The advantages of using this methodology are to reduce development risk, improve system performance, institutionalize rigor and precision into the design process, and enhance knowledge transfer. Unlike traditional systems engineering methods that focus primarily on design documentation (Document-Intensive Systems Engineering), MBSE instead focuses complex systems like ABMS that are suitable in digital-modeling environments.
As a multi-disciplinary approach, MBSE combines modeling, systems thinking, and systems engineering into a holistic framework. It covers four essential systems engineering domains to include requirements/capabilities; behavior; architecture/structure; and verification and validation. If applied to ABMS, MBSE would enable DAF engineering teams to better understand design change impacts; communicate design intent; verify, change, accept, and sustain functional capabilities; and analyze a system’s design before it is constructed. Moreover, as the methodology continues to mature, MBSE may extend beyond basic engineering models to support cross-domain model integration and complex predictive and effects-based modeling.92
___________________
89 See DoD Digital Engineering Working Group, 2016, “Systems Engineering Digital Engineering Fundamentals,” https://ac.cto.mil/wp-content/uploads/2019/06/DE-Fundamentals.pdf.
90 INCOSE (International Council on Systems Engineering Technical Operations), 2007, “Systems Engineering Vision 2020,” International Council on Systems Engineering, p. 15, September.
91 See N. Shevchenko, 2020, “An Introduction to Model-Based Systems Engineering (MBSE),” Carnegie Mellon University Software Engineering Institute, https://insights.sei.cmu.edu/blog/introduction-model-based-systems-engineering-mbse/, December 21, and K. Henderson and A. Salado, 2020, “Value and Benefits of Model-Based Systems Engineering (MBSE): Evidence from the Literature,” Wiley Periodicals LLC, 2021(24):51–66, https://onlinelibrary.wiley.com/doi/epdf/10.1002/sys.21566, December 15.
92 INCOSE, “Systems Engineering Vision 2020,” p. 24.
Within the DAF, there has been a strong push to move toward enterprise adoption of digital engineering (DE), of which MBSE is a subset.93 The former Assistant Secretary of the Air Force for Acquisition, Technology, and Logistics (SAF/AQ) encouraged the application of digital engineering to facilitate ownership of the technical baseline through “owning the technical stack.”94 The objectives are to:
- Achieve dominant capabilities while controlling life cycle costs;
- Increase the use of prototyping and experimentation;
- Improve requirements definition;
- Strengthen the DAF’s organic engineering capability; and
- Improve DAF leaders’ ability to understand and mitigate technical risk.95
The former SAF/AQ states that digital engineering has enabled the DAF to embrace computer-centric design and testing to expedite prototyping and reduce costs on new systems like next generation air dominance (NGAD) fighters.96 DE is also being employed in the ground-based strategic deterrent (GBSD) system, which is pursuing a flexible design based on intelligence assessments and technology forecasts, and in Space and Missile Systems Command’s protected anti-jam tactical satellite communications (PATS) family of systems that is leveraging both static and dynamic models in testing, integration, and design.97
Additionally in June 2021, the DAF stood up a Digital Transformation Office (DTO) headquartered at Air Force Materiel Command (AFMC) that is responsible for developing a digital governance structure and managing current and new digital
___________________
93 See R. Tsui, D. Davis, and J. Sahlin, 2018, “Digital Engineering Models of Complex Systems Using Model-Based Systems Engineering (MBSE) from Enterprise Architecture (EA) to Systems of Systems (SoS) Architectures and Systems Development Life Cycle (SDLC),” 28th INCOSE International Symposium, July 7–12.
94W. Roper, 2020, “There Is No Spoon: The New Digital Acquisition Strategy,” p. 5, https://software.af.mil/wp-content/uploads/2020/10/There-Is-No-Spoon-Digital-Acquisition-7-Oct-2020-digital-version.pdf, October 7.
95 AFMC (Air Force Materiel Command), “Benefits of Digital Engineering,” Air Force Digital Campaign, https://wss.apan.org/af/aflcmc/Benefits%20of%20DE%20Page/Home.aspx, accessed September 15.
96 See R.S. Cohen, 2021, “ABMS, Digital Engineering Decisions on Roper’s Final To-Do List,” Air Force Magazine, https://www.airforcemag.com/abms-digital-engineering-decisions-on-ropers-final-to-do-list/, January 14.
97 AFMC, 2020, “AF Digital Campaign Industry Exchange Day,” Air Force Digital Campaign, https://youtu.be/26lot6gv3Xk, accessed September 15, 2021. For more on GBSD, see CRS, 2020, “Defense Primer: Ground Based Strategic Deterrent (GBSD) Capabilities,” Congressional Research Service In Focus, https://sgp.fas.org/crs/natsec/IF11681.pdf, November 10. For more on PATS, see F. Wolfe, 2021, “Protected Anti-jam Tactical SATCOM Marquee Effort for SMC,” https://www.defensedaily.com/protected-anti-jam-tactical-satcom-marquee-effort-smc/space/, February 26.
transformation activities. The DTO director is also dual-hatted as the director of the DAF’s Digital Engineering Enterprise Office, responsible for:
- Providing traceability of system requirements across the system’s life cycle;
- Creating an environment that fosters innovation, experimentation, and demonstration from concept development to fielding;
- Enabling rapid prototyping to deliver capabilities faster and quickly respond to changing threats and requirements;
- Facilitating collaboration to improve integration of system of systems to meet mission needs; and
- Developing a platform and process to support DAF modernization efforts across multiple functional areas to include agile development and modular open systems architecture (MOSA).98
Collectively, the DTO and the Digital Engineering Enterprise Office seek to accelerate digital modernization and transformation across the DAF enterprise.99
FINDING 13: MBSE and digital engineering methodologies reduce development risk and improve system design and performance.
RECOMMENDATION 17: The Department of the Air Force Chief Architect’s Office and the Department of the Air Force Rapid Capabilities Office should work with the Department of the Air Force’s Digital Engineering Enterprise Office to apply model-based systems engineering (MBSE) methods across Advanced Battle Management System engineering and sustainment activities and to enable MBSE to serve as a bridge between operator requirements and development teams.
___________________
98 R. Jones, 2019, “USAF Digital Engineering Strategy to Implementation,” Office of the Deputy Assistant Secretary of the Air Force for Science, Technology, and Engineering, https://www.nist.gov/system/files/documents/2019/04/05/11-5_jones_usaf_mbse_implementation.pdf, April 5.
99 For more on the DAF’s digital transformation, see Air Force Materiel Command, “Digital Campaign,” https://www.afmc.af.mil/digital/, and W. Cooley, 2021, “Digital Campaign Overview,” Presentation to the Air Force Studies Board, August 6. See also Air Force Studies Board, 2021, “Digital Strategy for the Department of the Air Force: A Workshop Series,” https://www.nationalacademies.org/our-work/digital-strategy-for-the-department-of-the-air-force-a-workshop-series.
M&S and VV&A
Modeling is the process of producing a representation of the construction and working of a system; simulation is the operation of a model of the system.100 Together, M&S is a tool used in systems engineering to inform decisions. Verification, validation, and accreditation (VV&A) refers to three inter-related but unique processes that collect and evaluate evidence to determine whether a model’s or simulation’s capabilities, accuracy correctness, and usability are sufficient to support its intended uses.101 In concert with MBSE, M&S and VV&A provides options for trade-space analysis to inform design decisions and to quantify performance during system development. When overlaid with T&E, M&S and VV&A allow systems engineers the opportunity to evaluate with confidence that design implementation is performing according to expectations.102
In support of these processes, the DAF has established the Common Simulation Training Environment (CSTE) at the Air Force Life Cycle Management Center’s Architecture and Integration Directorate, Wright-Patterson Air Force Base. The role of the CSTE is to create a collaborative environment where training systems and simulators may be better linked to support operators and warfighters. Additionally, the DAF is working to standardize training platform requirements by establishing in 2016 simulator common architecture requirements and standards (SCARS) that implement a modular open system architecture (MOSA) approach and a set of universal standards for DAF simulators.103 The intent of these activities is to rapidly update technologies on a continual basis, while supporting ABMS and JADC2.
___________________
100 See A. Maria, 1997, “Introduction to Modeling and Simulation,” in Proceedings of the 1997 Winter Simulation Conference, S. Andradottir, K.J. Healy, D.H. Withers, and B.L. Nelson, eds., pp. 7–13, https://ieeexplore.ieee.org/stamp/stamp.jsp?arnumber=640369.
101 See DoD (U.S. Department of Defense), 2008, “Department of Defense Standard Practice Document of Verification, Validation, and Accreditation (VV&A) for Models and Simulations,” MIL-STD-3022, p. 2, January 28.
102 MITRE Corporation, “Verification and Validation of Simulation Models,” MITRE Systems Engineering Guide, https://www.mitre.org/publications/systems-engineering-guide/se-lifecycle-building-blocks/other-se-lifecycle-building-blocks-articles/verification-and-validation-of-simulation-models.
103 See M. Roaten, 2021, “Air Force Looking to Boost Connectivity for Simulators,” National Defense Magazine, https://www.nationaldefensemagazine.org/articles/2021/7/22/air-force-looking-to-boost-connectivity-for-simulators, July 22.
Digital Twin
A digital twin is a “virtual representation of an object or system that spans its life cycle, is updated from real-time data, and uses simulation, ML, and reasoning to help decision-making.”104 Classes of models include the system model, product model, and process model. A digital twin and digital thread connect these models together in a model-based environment.105 As an engineering tool, a digital twin provides insights regarding how a system or connected sensors will perform in the future.
Within the DAF, several programs and systems are already adopting digital twins in their engineering plans. For example, the PATS family of systems is using a digital twin for early system modeling to reduce risk and as a built model for system integration and operational support.106 A digital twin was also used in the design and initial testing for the Air Force’s new advanced aircraft trainer jet, the eT-7 Red Hawk, where design, construction, and test flights were all conducted before the first trainer jet was even manufactured and delivered.107 Similarly, digital twins were used in lieu of flight tests to evaluate competing proposals for the B-52 engine replacement.108 The DAF also announced plans to create a digital twin for the F-16 to improve sustainment and modernization of its current fleet.109 The goal
___________________
104 M.M. Armstrong, 2020, “Cheat Sheet: What Is Digital Twin?” IBM Business Operations Blog, https://www.ibm.com/blogs/internet-of-things/iot-cheat-sheet-digital-twin/, December 4. See also M. Grieves and J. Vickers, 2017, “Digital Twin: Mitigating Unpredictable, Undesirable Emergent Behavior in Complex Systems,” pp. 85–113 in Transdisciplinary Perspectives on Complex Systems, (F-J. Kahlen, S. Flumerfelt, and A. Alves, eds.), Springer, Switzerland, https://link.springer.com/book/10.1007/978-3-319-38756-7.
105 NASEM (National Academies of Sciences, Engineering, and Medicine), 2021, Adapting to Shorter Time Cycles in the United States Air Force: Proceedings of a Workshop Series, p. 18, The National Academies Press, Washington, DC. Digital thread is defined as “an integrated information flow that connects all the phases of the product life cycle using an accepted authoritative data source.” NASEM, 2021, “Adapting to Shorter Time Cycles in the United States Air Force: Proceedings of a Workshop Series,” p. 18.
106 See T. Hitchens, 2021, “Space Force Digital Vision Focuses on Speedy Decisions,” Breaking Defense, https://breakingdefense.com/2021/05/space-force-digital-vision-focuses-on-speedy-decisions/, May 6, and S. Erwin, 2020, “Space Force Developing a Digital Strategy for Designing and Producing Future Satellites,” Space News, https://spacenews.com/space-force-developing-a-digital-strategy-for-designing-and-producing-future-satellites/, October 21.
107 R.S. Cohen, 2020, “Air Force Introduces e-Planes for the Digital Era,” Air Force Magazine, https://www.airforcemag.com/air-force-introduces-e-planes-for-the-digital-era/, September 14.
108 S. Waterman, 2020, “Digital Twins Proliferate as Smart Way to Test Tech,” Air Force Magazine, https://www.airforcemag.com/digital-twins-proliferate-as-smart-way-to-test-tech/, March 15.
109 B. Brackens, 2021, “Air Force to Develop F-16 ‘Digital Twin,’” Air Force Life Cycle Management Center News, https://www.aflcmc.af.mil/News/Article-Display/Article/2677215/air-force-to-develop-f-16-digital-twin/, June 30.
is to create a “full scale 3D model of the aircraft … to help address future parts obsolescence, and mitigate supply chain risks … [to reduce reliance] on legacy manufacturing sources and processes.”110
For ABMS, the Air Force Research Laboratory’s (AFRL’s) Munitions Directorate is using digital twins aided by high-performance computing systems and AI/ML in the Digital Enterprise WeaponONE (W1) program to collect data from weapons in-flight, combine that information with data fed from the battlefield, and transmit the aggregated data seamlessly through ABMS back to the digital twin.111 The goal is to improve accuracy and utility of the digital models. AFRL demonstrated this capability in January 2021 using the Gray Wolf prototype. Gray Wolf is an experimental cruise missile intended to provide clustered deployment against enemy air defenses.112 During the exercise, Gray Wolf executed a 24-hour air tasking order that enabled missiles to collaborate. W1 collected in-flight data and cross referenced it with information about the battlefield, then used ABMS network to securely transport the information back to the digital twin for analysis. “The all-encompassing, digital, agile, open ecosystem program unites best practices and standards from across government, industry, and academia and applies them to weapons development.”113 Going forward, the W1 program will further advance its digital twin prototypes to enable bi-directional data exchanges with their physical counterparts.
To encourage competition in leveraging even greater use of digital twins, the AFRL is building an online colosseum where commercial vendors’ systems are able to compete. “Each vendor could submit a digital twin of a proposed weapons platform for evaluation in ‘a kind of Gladiator showdown … across that particular technology area,’”114 according to the head of AFRL’s Munitions Directorate. Vendors are directed to build their digital twins using the Government’s Reference
___________________
110 Ibid.
111 See Air Force Research Laboratory Public Affairs, 2021, “WeaponONE Demonstrates Digital Twin Technologies That Deliver Software-Defined Weapon Capabilities to the Battlefield,” Air Force Life Cycle Management Center News, https://www.aflcmc.af.mil/News/Article-Display/Article/2478391/weaponone-demonstrates-digital-twin-technologies-that-deliver-software-defined/, January 21.
112 T. Hitchens, 2021, “AFRL’s WeaponONE Aims to Rapidly Build Digital Design, Engineering Tools,” Breaking Defense, https://breakingdefense.com/2021/02/afrls-weaponone-aims-to-rapidly-build-digital-design-engineering-tools/, February 5.
113 T. Hitchens, 2021, “AFRL’s WeaponONE Aims to Rapidly Build Digital Design, Engineering Tools,” Breaking Defense, https://breakingdefense.com/2021/02/afrls-weaponone-aims-to-rapidly-build-digital-design-engineering-tools/, February 5.
114 S. Waterman, 2021, “Air Force Goes All in on Digital Twinning—for Bombs as Well as Planes,” Air Force Magazine, https://www.airforcemag.com/air-force-goes-all-in-on-digital-twinning-for-bombs-as-well-as-planes/, March 26.
Architecture that provides standards and defines the interfaces the digital model needs to use.
FINDING 14: Significant initiatives are under way across the DAF to encourage the use of digital twins for both legacy platforms and emerging systems.
RECOMMENDATION 18: Building on existing activities in digital engineering and modeling and simulations, the Department of the Air Force Chief Architect’s Office and the Department of the Air Force Rapid Capabilities Office should expand the use of digital twins in Advanced Battle Management System development, particularly as new capabilities and technologies are introduced.
COMMON MISSION COMMAND CENTER
An example of a complex architecture and systems integration has been the Family of Systems (FOS) that was initiated in 2010 by the former Under Secretary of Defense for Acquisition, Technology, and Logistics, the former Principal Deputy Under Secretary of Defense for Acquisition, Technology, and Logistics, and the former Air Force SAE. Pulling together a large number of existing and newly developing programs in the FOS, five major elements resulted in a fusion of new technologies and synthesis of major program elements.
That proven process led to a recognition that there is a strong requirement for integrating command, control, communications, and intelligence (C3I) to different program components. Resulting from this need, a government and industry team under the auspices of the DAF RCO has successfully established a prototype capability to support ABMS elements. This prototype, the Common Mission Control Center (CMCC), is a software, hardware, and human machine interface that directs, tasks, and combines multiple missions, to include a large number of weapon systems within a complex C2 framework. The focus is on providing interoperability, mission management, planning and tasking, data fusion from multiple information sources, geo-location status and situational awareness, product management and dissemination, and machine-to-machine data exchange in a secure C2 environment.115 It has been developed with a well-established open architecture framework using open mission systems/universal command and control interface (OMS/UCI) applications. Additionally, the DAF RCO has led a major effort in protected com-
___________________
115 P. Host, 2016, “Air Force, Contractors Working Together on Common Mission Control Center,” Defense Daily, https://www.defensedaily.com/air-force-contractors-working-together-on-common-mission-control-center/air-force/, June 21.
munications and indications and warnings, which would enhance the multi-layer security of the CMCC.
The 2019–2020 Defense Science Board study on 21st Century Multi-Domain Effects recommended the establishment of an open architecture base in a Joint C3I system that would combine command and control functionalities across the military Services to support complex operations across all domains.116 The CMCC provides this type of integrated command and control construct and may be scalable to support ABMS functions and JADC2 mission requirements going forward. If CMCC serves as phase zero for ABMS, then future upgrades would be refreshed every year or two to fully integrate with new capability releases in a disciplined and symbiotic way. The capability upgrades would be continuous to prevent obsolescence and to ensure that ABMS is equipped to address evolving adversarial threats.
RECOMMENDATION 19: The Department of the Air Force Rapid Capabilities Office should consider scaling the Common Mission Control Center and designate it as phase zero for the Advanced Battle Management System.
___________________
116DoD, 2020, “21st Century Multi-Domain Effects Executive Summary,” Defense Science Board, https://dsb.cto.mil/reports/2020s/FINALMDEExecutiveSummary.pdf, September.










































