5
Workshop Three, Part One
OPENING REMARKS
Workshop series co-chair Ms. Deborah Westphal, chairman of the board, Toffler Associates, explained that this final workshop in the series would identify gaps between what the Air Force is currently doing and what it could consider doing in the future.
THE FUTURE THREAT ENVIRONMENT
Dr. Brendan Mulvaney, director, China Aerospace Studies Institute, National Defense University, discussed China’s progress in digitization and modernization. He explained that China conceptualizes things differently than the United States—for example, the information domain in China includes electronic warfare; cyber; spectrum operations; and intelligence, surveillance, and reconnaissance systems. Because China operates in a different framework, it can be difficult to make comparisons between the two countries for analysis. China does not have many of the same restrictions that the United States has in terms of collaboration and information sharing; thus, it uses information from many inputs for its large information system. This approach is often referred to as “informationization.” As early as 1991, China understood both that information systems were key to modern warfare and that there was a sense of urgency to compete with the United States, which was more advanced at that time. China’s first step of informationization was digitization (i.e., moving away from Cold War-era analog systems that had no cross-platform capability). The next step is “networkization” (i.e., free flow of information up and down the chain). China has begun to create an integrated command platform—a system into which all information could flow, with each user having an appropriate level of network access. At the same time, China is embarking on “smartification.” According to Dr. Mulvaney, China strongly believes that if enough information is collected and analyzed
correctly, any problem can be solved. As a result, China is beginning to dedicate science and technology investments to using machine learning (ML) and high-powered computing to analyze the information, signals, and intelligence emerging from all of its sources (e.g., space, cyber, on the ground, etc.). China also collects and stores encrypted information in vast data centers so that it will have an advantage when the quantum computer becomes operational and the encrypted information can be read. China is working to move the human to be “on-the-loop” (versus “in-the-loop”) and eventually to remove the human completely from the loop. Dr. Mulvaney believes that the Chinese are more likely to turn life-and-death decisions over to artificial intelligence (AI) than the United States.
He explained that China conducts both 5-year and long-term planning, and as long as its economy remains stable, so too will the policy environment. China remains behind the United States in many key areas but is approaching parity in many others, and it continues actively pursuing partnerships and investments in Silicon Valley. China’s Strategic Support Force (SSF), which was stood up in 2016, combines its space and cyber forces. He noted that if something can affect space operations, it can affect cyber operations, and thus the two are integrally linked. He said that Xi Jinping, the Chairman of the Central Military Commission for the Communist Party in China, expects that the next war will be won in the information domain. Therefore, China is investing in space and counterspace operations, including cyberspace operations. China’s military still has some stovepipes, but it has a plan to transform by 2049. With the initial efforts in networkization, China’s theater commands (similar to the U.S. Combatant Commands) already have more information and easier access to that information. China’s theater commands are moving toward a joint model for staffing, authorities, and lines of communications.
Dr. Mulvaney mentioned that China has a substantial amount of fiber, which is protected, encrypted, and has backups from low-tech to quantum relays and satellites. All of that information is flowing into SSF Headquarters and down to the theater commands. The eventual goal is for the theater commands to have the ability to push tasking and information and intelligence to individual units that will move forward in operation. He cautioned that China is quickly closing the gap with the United States in its collection and analysis capabilities and might already be on par with some U.S. capabilities. China has also increased its training and exercises to practice networkization, with an emphasis on contested environments, and is working to improve the synchronization of its acquisition efforts at a national level.
Dr. Marv Langston (USN, ret.), independent consultant, asked Dr. Mulvaney about the prediction made in AI Superpowers that China will be ahead of the United States in AI by 2023. Dr. Mulvaney replied that China has surpassed the United States in some areas of AI, but the United States is still ahead in most areas of AI—although China is quickly closing the gap. Dr. Langston also wondered whether the Chinese have operationalized quantum communications and networks with Air Force Satellite Communications. Dr. Mulvaney noted that China has quantum encryption keys and key distribution through terrestrial networks but has not operationalized quantum communications in networks yet. He added that the Austrians are engaging in similar efforts and if they partner with the Chinese, there could be direct impacts.
Ms. Westphal pointed out that the Chinese are collecting data on individual U.S. citizens. She wondered about the need to rethink warfare if airmen’s personal lives are targeted in an attempt to influence their decisions during operations. Dr. Mulvaney remarked that this is an area China considers to be part of the information domain, and it actively collects information on its own and U.S. citizens. He acknowledged Ms. Westphal’s concern that U.S. airmen, who are in constant contact with their families, could lose focus on the battlefield if China has the power to interfere in a situation (e.g., financial or personal) on the home front. He added that the benefits of a free and open society such as the United States can become detrimental when adversaries have ready access to information. He expressed with certainty that China will use information to gain advantage. Ms. Westphal suggested that the Air Force spend more time thinking about its defensive posture as civilian life and military operations begin to overlap. Dr. Mulvaney agreed with Ms. Westphal that the Air Force should consider its role in protecting civilian infrastructure and communication nodes as well as individual airmen.
Dr. Langston questioned whether China has taken advantage of the Office of Personnel Management (OPM) hack on security background data. Dr. Mulvaney responded that the OPM hack revealed who has clearance, how old the clearance is, how often it is updated, and the level of the clearance as well as some
background information (e.g., identities of friends and families). He hypothesized that China would have tried to compromise some of these sources by using the information to entice people to partner with a particular laboratory of interest to China, for example. Dr. Langston asked how China’s digital money system has improved its ability to track its own citizens. Dr. Mulvaney said that China promotes its approach to domestic security as a “smart city” that will be safer and run more smoothly. Yet, people are constantly monitored (e.g., someone crossing a public street outside of an authorized crosswalk is captured with facial recognition on a camera and immediately receives an alert on his phone that he has been ticketed and fined for jaywalking; his fine is removed from his state-owned bank account and his social credit score reduced). He cautioned that China is exporting this smart-cities technology to other countries, and information from those countries flows back to China. Ms. Westphal wondered if there are strategies to prevent the United States from collecting information on Chinese citizens. Dr. Mulvaney explained that the Chinese view their “Great Firewall” as an effective way to eliminate threats. He said that the United States will have to find ways to counter the systemic differences between the countries’ approaches to information. Dr. Langston asked if the Chinese Communist party is surveilled. Dr. Mulvaney replied that, to the best of his knowledge, although there are likely secure rooms for senior party officials, no one is exempt from surveillance.
Mr. Alden Munson, senior fellow and member, Board of Regents, Potomac Institute for Policy Studies, asked if the Chinese would make the Air Force a high-priority cyber target if it successfully creates a digitized force. Dr. Mulvaney emphasized that the Air Force is already a high-priority cyber target, but China will want to learn more about how the Air Force’s digitized system works and how to disrupt it. He suggested that the Air Force enhance its training in a contested environment to be prepared for this situation.
Dr. Rama Chellappa, Bloomberg Distinguished Professor of electrical and computer engineering and biomedical engineering, Johns Hopkins University, pointed out that although China has far more data to train on, success with facial recognition does not translate to general progress in AI. He added that although China has made progress, a free society will survive—one can never underestimate free people’s ability to win. Dr. Mulvaney acknowledged the difference between specific AI and generalized AI. He mentioned that the Chinese have emphasized “indigenous innovation,” but it is difficult to convince free thinkers to do creative design in an environment like China where they will have no academic or political freedom.
Dr. Annie Green, data governance specialist, George Mason University, wondered if China is monitoring whether its personal tracking efforts add value to the economy or increase monetary sources for residents. Dr. Mulvaney replied that China is not tracking its citizens for added financial value; it tracks people to increase the party’s control, which adds “value” to the society. China expects that if people know they are being monitored, they will be more likely to follow the party’s rules.
Ms. Westphal asked Dr. Mulvaney about areas in which the Air Force could be paying more attention, given his perspective of China. Dr. Mulvaney asserted that the Air Force should be training to fight in a contested environment without satellite communications. The Air Force also needs to improve agile combat employment. Utilizing U.S. partners and allies will be the only way to succeed, he continued, so it is imperative to cultivate those relationships.
WHAT DOCTRINE, CONCEPTS OF OPERATIONS, AND TACTICS, TECHNIQUES, AND PROCEDURES DO WE NEED TO OPERATE IN A DIGITALLY TRANSFORMED AIR FORCE? PANEL ONE
Maj. Evan “Switch” Hatter, Chief of Doctrine Outreach, the Curtis E. LeMay Center for Doctrine Development and Education, defined doctrine as agreed-upon best practices that are supported by history, debate, analysis, wargame exercises, and contingencies. Doctrine serves as official advice or guidance, and it is authoritative, not directive; thus, “should” is used instead of “shall” or “will.” Doctrine provides guidance and stability for the Air Force, and the Air Force drives how doctrine proceeds over time. The two key pillars of doctrine are unity of command and mission command.
Maj. Hatter explained that between initial concept and doctrine, “emerging doctrine” describes something on the horizon to becoming a best practice. The LeMay Center’s Chennault Series, in particular, pursues gaps and seams in the doctrine. The LeMay Center also forms doctrine writing subgroups, which are comprised of subject matter experts from the field, and conducts Joint All-Domain Operations Symposium wargames.
He noted that when the digital modernization strategy emerged in 2019, Gen. David Goldfein requested that the LeMay Center establish the joint all-domain operations (JADO) doctrine, which became the Air Force’s first “doctrine note” (AFDP 3-99). In March 2021, Air Force Doctrine Publication 1 was a major effort to rewrite the Air Force’s core foundational principles for air power. Gen. Charles Brown has requested that the LeMay Center also provide the service doctrine on agile combat employment, which is expected to be published as an Air Force doctrine note in mid-October 2021.
Maj. Hatter discussed Air Force Doctrine Publication 1 in greater detail, emphasizing that the focus has shifted from “phases of war” to “competition continuum at scale.” “Airpower” has also been redefined as the ability to project military power through control and exploitation in, from, and through the air. Air Force Doctrine Publication 1 prioritizes the air domain, as well as the information environment, the cyberspace domain, and the electromagnetic spectrum. He stressed the importance of airmen understanding that any of their actions (e.g., written, spoken, social media) have informational components that communicate messages, which could be leveraged for operations and planning. The airmen’s philosophy for the command and control of airpower (i.e., mission command) is centralized command, distributed control, and decentralized execution. Mission command is communicated through a commander’s intent through mission-type orders, which require different authorities (e.g., conditions-based, delegated, or flexible command).
He emphasized that joint all-domain command and control (JADC2), referenced in AFDP 3-99 and in the doctrine note for agile combat employment, requires a level of redundant and resilient command and control nodes to ensure disconnected and distributed command and control when the higher-level command and control fails. JADC2 also requires edge computing and self-healing mesh networks. He said that airmen should be trained and equipped to employ communications equipment in distributed operations, and the system should be secure but simplistic enough to work in these environments. Commanders have to coordinate across domains, but the Chennault Series revealed a gap within command authorities—is direct liaison authority and tactical control or operational control sufficient to work not only in a joint environment but also in an all-domain environment? He remarked that doctrine is pursuing that and other key questions. For example, the LeMay Center considered what key elements need to be provided to an airman for mission command via a mission-type order. With the assistance of subject matter experts, an overall framework was developed. Commander’s intent is provided throughout a mission-type order, but the pace plan is critical and posture is foundational—agile combat employment posture provides deterrence to the adversaries and assurance to the allies that distributed operations will be maintained in a disconnected environment.
Maj. Hatter referenced the doctrine, which explains that to operate disconnected in a distributed location, capability development should include accessible and redundant cloud-based systems that function seamlessly when disconnected and reconnect without interruption. The doctrine also suggests that secure, adaptable, interoperable, and integrated data networks provide information synthesis, distributed decision making, and assessment, which are essential to work with joint partners. The force should be optimized for these major combat operations in a contested environment, he continued, and this approach should work not only at main operating bases but also in the least capable, small contingency locations functioning as network nodes to generate combat air power. Both the agile combat employment and JADO doctrine notes address how AI and ML could enable decision superiority within agile distributed operations.
In closing, Maj. Hatter reiterated that doctrine is codified best practice. When the field determines that an emerging concept should be put into doctrine, the LeMay Center either codifies those best practices into existing doctrine, or works to develop a doctrine note and codifies the note into a living document that can be rapidly iterated (versus the traditional 2-year doctrine rewrite timeline). Since the initial JADO doctrine note was published in 2019, it has been iterated on three times.
Ms. Westphal wondered how best practices are codified if the Air Force is not yet training digitally. Maj. Hatter said that the LeMay Center could lead a writing group to determine whether a path forward exists, but he reiterated that the “best practice” has to come from the field before it can be codified. Mr. Munson asked if doctrine could be used to generate use cases to define the base features of a digitized force. Maj. Hatter noted that agile combat employment will only succeed with cloud-based architectures, mesh networks, and self-healing networks. Similarly, successful JADO requires AI, ML, and human-machine interfaces. Those components have to be functional for the JADO and agile combat employment doctrine to be successful. Mr. Munson added that issues need to be addressed on behalf of the entire force instead of by individual commands and activities. Maj. Hatter replied that doctrine is not meant to contain force requirements; however, vignettes could be presented (e.g., the use case for cloud-based architecture or edge computing) without having undergone doctrine testing. He stressed that the Air Force would not want to reveal specific requirements in its doctrine (e.g., how many gigs of transfer speed are needed for mesh computing).
Col. Charles Galbreath, Deputy for the Chief Technology and Innovation Office (CTIO), U.S. Space Force Headquarters, explained that the CTIO emerged in response to Gen. John Raymond’s intent for the Space Force to become a digital service. The Human Capital Office, the Operations Office, the Strategy and Requirements Office, and the CTIO collaborate to achieve this vision. The CTIO’s primary responsibility is to lead the digital transformation for the Space Force. For example, it pilots efforts from Headquarters and coordinates across the field commands and other L2s to infuse digital capabilities and processes into activities across the Space Force. In addition to the application of digital tools and the development of an enterprise IT infrastructure and data governance standards, the transformation includes science and technology and analytic components. The CTIO currently has 30 government billets but plans to have 80 to 90 over the next 2 to 3 years, and it has opportunities within four directorates overseen by Dr. Lisa Costa, the incoming chief technology and innovation officer: Innovation and Digital Transformation; Science, Technology, and Research; IT, Data, and Data Analytics; and Analysis.
Col. Galbreath noted that the first document to codify the Space Force as digital was the Chief of Space Operation’s Planning Guidance, released in November 2020. The direction was to create the Space Force as a digital service to accelerate innovation. It also introduced four key focus areas for the Space Force: (1) digital workforce (i.e., education and cultural changes with the creation of the right attitudes and digital fluency), (2) digital engineering (i.e., an end-to-end digital thread of capabilities from design, to acquisition, to operational testing and evaluation, to development, to mission planning, to robust digital twins to support anomaly resolution and attack identification), (3) digital headquarters (i.e., decision making at all levels by producing streamlined capabilities to make informed data-driven decisions and using the available manpower to the best extent), and (4) digital operations (i.e., delivery of capabilities and effects in more rapid and meaningful ways).
In May 2021, the CTIO released the Space Force Vision for a Digital Service, which was built around those four key focus areas and defined what it means to be a digital service. He described the Space Force Vision for a Digital Service as an aspirational and educational document. Immediately after its release, a roadmap was developed to achieve the vision. While the roadmap (a living document) is not constrained by manpower or resource limitations, it expanded the four focus areas into a series of objectives, activities, and tasks that are now being evaluated for execution potential, and adjustments will be made based on available funding. He emphasized the need to confront the emerging threat, accelerate delivery of innovative capabilities, leverage the small size of the service to be more agile and adaptable, and override existing bureaucracies to compete. The Vision states that the Space Force should be interconnected, innovative, and digitally dominant—that is, turn the “cumulative technical prowess into potent force-multiplying effects to develop, field, and operate capabilities more quickly and effectively than any potential adversary.”
Col. Galbreath commented on the CTIO’s Software Development Immersive, which includes intensive coding coursework over several weeks, followed by an applications period and an internship with the Space Operations Command or other Space Force organizations. This program teaches government personnel with basic coding knowledge how to lead a coding effort as well as provides them with additional coding
skills. The goal of this program is to increase DevSecOps activities across the Space Force. The CTIO has also created force multiplier courses through Digital University to educate everyone in the Space Force about digital tools and practices, and offers virtual sessions on various digital activities.
Dr. Pamela Drew, former executive vice president and president of information systems, Exelis, asked Col. Galbreath to elaborate on the CTIO’s pilot efforts. He explained that there are pilot efforts across all four of the key focus areas. One effort relates to the creation of digital engineering capabilities for missile warning as part of the next generation of programs of record. In a digital headquarters effort, the CTIO is leveraging Rhombus Guardian and Brown Heron for displays of force readiness for the chief of operations and to support manpower decisions with the evaluation of the right personnel mix (i.e., backgrounds and experiences). Another effort uses a natural language processing algorithm with AI to evaluate resumes to enhance the digital workforce. In terms of digital operations, the CTIO is focused on JADC2 and the Advanced Battle Management System (ABMS) as well as leveraging AI to support space domain awareness.
A participant wondered how legacy systems are being addressed with respect to digital engineering. Col. Galbreath replied that consideration for the future force design includes an understanding of the current architecture and essential modifications. A macro-level representation of the legacy architecture is needed to compare any proposed modifications for the future force design against a known baseline. Achieving the detailed level of digital twin that will be possible for future systems is unlikely for the current system: that approach would not create a significant return on investment. He expected some amount of “grandfathering” to the guidance that all systems will have a digital twin by a certain milestone.
Mr. Munson asked if there is an effort to define how the Space Force will be different from the Air Force. Col. Galbreath noted that the Space Force has a strong partnership with the Air Force, in particular with the Office of the Chief Information Officer. Although the Space Force relies on the existing enterprise information technology system provided by the Air Force, it will define its own unique requirements as it moves forward with digital tools and processes. The Air Force is willing to work with the Space Force, and, because the Space Force is so small, it can experiment (e.g., with new tool sets) in ways that the larger Air Force cannot. The Space Force is also leveraging the Air Force’s Digital University and providing additional courses. Because the Army, Navy, Marine Corps, and Coast Guard are also pursuing digitization, he continued, a digital engineering ecosystem would be beneficial so that all of the services can communicate and engage with open system architecture modeling and simulation. Mr. Munson inquired about relevant use cases that span important features of a digitized environment. Col. Galbreath said that the CTIO is utilizing use cases in all of its pilot efforts; because the CTIO has increased in size, it is important to have a specific focus.
Mr. Jay Santee (USAF, ret.), vice president, Strategic Space Operations, Defense Systems Group, The Aerospace Corporation, asked about the “digital ecosystem” and how it will support transformation efforts. Col. Galbreath expressed his hope that all current and future systems will have an associated digital twin. With adequate funding, these digital twins could work together in a virtual environment, where every detail is represented. In the meantime, the CTIO has several pilot efforts that initiate a set of digital engineering capabilities, which will grow over time and federate into multiple enclaves of capabilities at different security classification levels. He also shared a few examples of how the Space Force could leverage AI. He described a recent robotic process automation workshop that utilized AI tools to release operators and acquirers from more mundane tasks, which could be applied today. The Space Force also hopes to leverage AI for space domain awareness (i.e., to discern patterns of life and activity for satellites and determine if something is abnormal). Ultimately, the digital ecosystem could emulate an operator and a threat operator in a potential combat scenario.
Ms. Westphal wondered if enough time and effort are being spent to understand how authorities and decision making at the edge could change in a digitized force. Col. Galbreath replied that space has always been much more digitally inclined than any of the other domains. The Space Force will have to rely on AI and automation to support many of its activities owing to the associated time elements (e.g., latency has a bigger impact farther into the cislunar space). In the terrestrial sphere, AI tools help to sort large data sets rapidly and support decision making. AI can also categorize activities quickly, allowing humans to focus
on more critical issues. Weapons release authority, for example, will always be in the hands of a human, but automation could be useful for identifying threats. He noted that during the recent evacuations from Afghanistan, data on how many people were onboard, how long people had been on the tarmac, and how long people waited once they landed were used to support decision making. Ms. Westphal emphasized that decision making in a timely fashion is about trust—delays arise in conflicts over who owns the data.
Dr. Andrew Stricker, analyst, Strategy and Concepts, the Curtis E. LeMay Center for Doctrine Development and Education, discussed his previous experience working on a digital transformation effort with several universities—Vanderbilt University, Harvard University, the Massachusetts Institute of Technology (MIT), Northwestern University, and the University of Texas at Austin. Although this effort was on a much smaller scale than what the Air Force is trying to accomplish, there are useful insights and commonalities. He echoed the notion that transformation is not about technology; it is about changing culture and establishing trust. He posited that the digital transformation cycle model used to help these universities transform (see Figure 5.1) could be utilized by the Department of the Air Force (DAF).
Dr. Stricker explained that these universities were motivated to transform to become more competitive on the international spectrum of new discoveries. Although they had a history of working in partnership, they had not established digital connections with federal laboratory structures, high-performance computing areas, and other new capabilities. Taking a “whole-of-government perspective,” he continued, the universities began to establish new partnerships. However, just as the Air Force is now realizing, the universities recognized that it is difficult to focus simultaneously on a digital transformation and existing efforts. He emphasized that the digital transformation cycle is a continuous journey. An “all-hands” effort was required for the digital transformation to gain traction among the universities; the students and staff mattered tremendously in this effort, not just the administrators.
Similar to the Air Force’s concern about competitive advantage on the world stage, the universities sought to revolutionize capabilities with AI and ML to augment teaching, research, and other areas of scholarship. Visualization was a powerful tool in transforming how researchers were developing theories, real-time insights, and new research directions. He observed that the Air Force is trying to implement similar visualization tools so that people on the functional lines can better understand patterns and challenges. As part of the university effort, real-time digitization tools and model-based reasoning were used across all disciplinary areas to create “what-if” scenarios with data-informed infusions of information from several federal data sets. The model-based reasoning “energized” the faculty and students, showcasing just how many more discoveries remained to be made.
Dr. Stricker noted that digital transformations have significant changes for people’s day-to-day work. In the universities, people accustomed to exerting leadership were reluctant to expose the vulnerability of learning new things; a comfort level had to be created, with multiple entry points for engaging leaders, staff, and students. Small teams emerged across the universities to foster new ways of experimentation. It also became clear that a new infrastructure was needed to enhance connectivity. In the past, government laboratories and universities grew in stovepipes because the work was independent, creating robust infrastructure within some domains but creating barriers when trying to share data and connect resources across departments or disciplines. An enterprise-level architectural perspective was needed, he continued, which requires much patience to iterate and balance the use of legacy infrastructure capabilities and new capabilities.
Turning to a discussion of his work with the LeMay Center, he explained that he writes a weekly brief on translating cognition and AI efforts at universities across the world for military usage and applications. One important issue is the need for trustworthy data. Although data may be collected electronically, that does not mean they can be accessed, cleansed, or used. Cloud computing capabilities are fundamental in establishing areas to work with data. He noted that funding remains a challenge for universities and the Department of Defense (DoD) alike, especially in relation to small business efforts to simulate new capabilities. Finding the right security balance is also difficult: organizations have to protect assets but also have the ability to work within open systems. He underscored the need for DoD to harvest the “incredible ingenuity” taking place in the open-source community, vet it, and operationalize it to serve military needs.
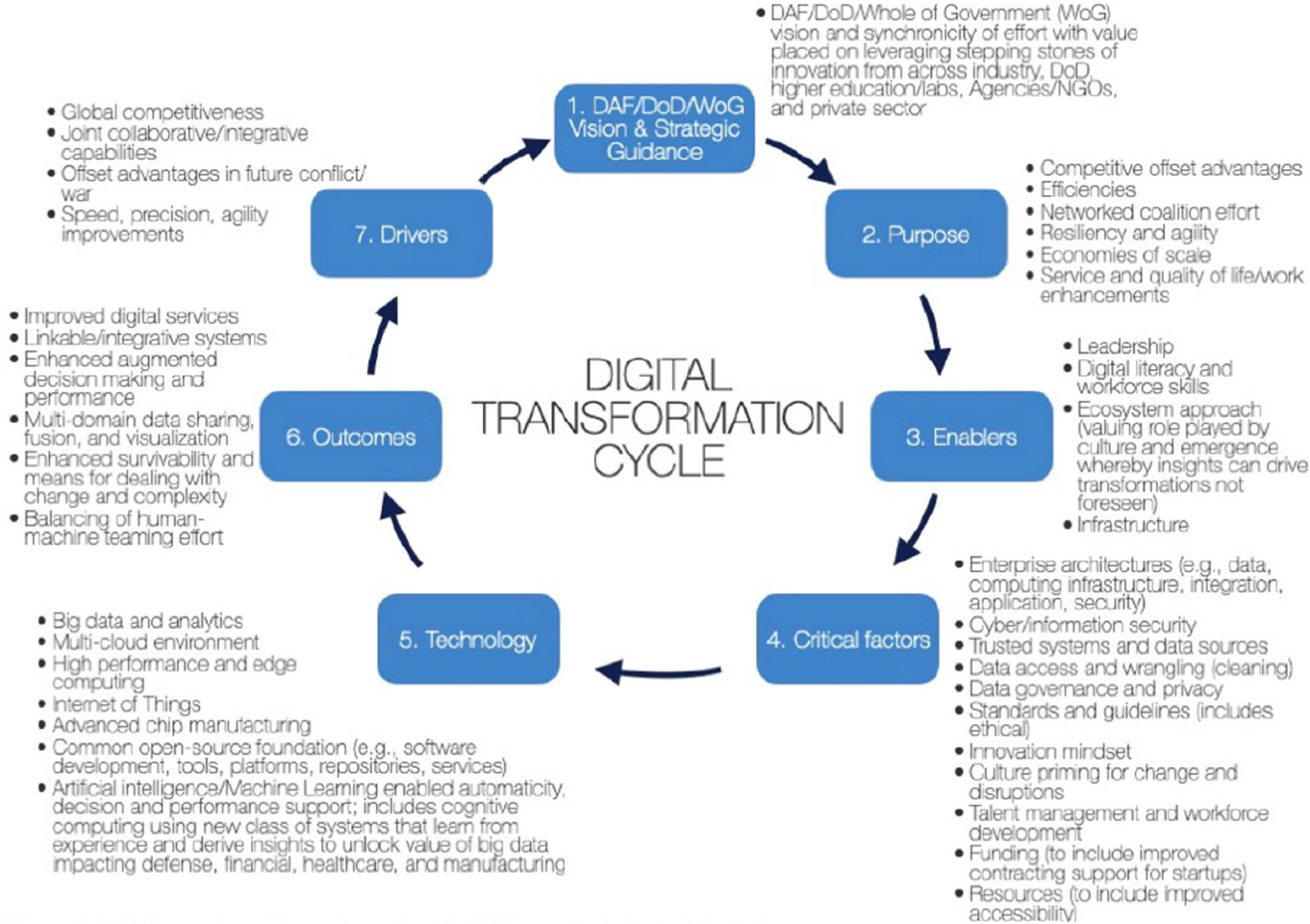
In terms of overall progress with AI, Dr. Stricker said that work remains to be done in assistance with common sense. Because humans can be overconfident and underestimate threats, this technology could aid decision makers in DoD, especially in the case of large data sets. A key part of realizing these technologies is having the right people in place who can work with the toolsets and in the data sciences, and help leaders to use and apply the tools for decision making. An important outcome of digital transformation is improving human-machine teaming, although this is challenging given that human teams already find it difficult to trust other human teams.
Dr. Stricker cautioned that the United States is in a “foot race” with China, and China has been able to leapfrog the United States in some areas. It is important for the United States to leverage its unique contributions to global competition. Agility and adaptability are key—accelerating digital transformation with AI will help to automate the speed at which data are processed and fused in support of decision making, which will also help to realign the human-machine structure. He emphasized that digital transformation should enable the use of AI and ML to stay in communication with dispersed forces and support reaggregation.
Dr. Langston asked about the value of model-based reasoning as well as whether general AI techniques could support human-intensive functions such as command and control. Dr. Stricker replied that general AI is taking place in “baby steps” (e.g., MIT’s Lincoln Labs is working on one-shot learning capabilities; others are working on abductive reasoning developments). Model-based reasoning has revolutionized research, medicine, biology, and engineering, and he expected that it could revolutionize the Air Force in its ability to examine the “what-ifs” (e.g., to understand potential effects of model manipulations during wargames and simulations). He noted that the U.S. Department of Energy already leverages tools for building and manipulating models to identify gaps.
Ms. Westphal invited Dr. Stricker to identify a few areas on which the Air Force could focus to make the digital strategy successful. He said that the Air Force is a few years behind in developing the infrastructural components needed for digital transformation. It will take several levels of effort to get the appropriate infrastructure in place to work with data and use them in models. For example, Vanderbilt invested more than $120 million in infrastructural improvements for high-performance computing. He reiterated that the United States does not have much time to catch up in the foot race with China. In response to a question about a unity of effort across the Air Force, Dr. Stricker observed that the unity of effort is taking place on paper and in discussions but not in action. He asserted that the Air Force needs to realize that the digital transformation is much larger than project milestones and objectives.
Mr. Todd Carter, A2/6 Cyber Talent Management, mentioned the Air Force’s challenges in developing the right level of workforce expertise and battling with the civilian sector to retain that expertise. He asked how to address these challenges, beyond traditional incentive structures. Dr. Stricker suggested directly engaging the best talent in an organization’s biggest problems. Giving top talent small, insignificant tasks will discourage and disincentivize them. He also proposed that the Air Force consider new ways to associate with talent (perhaps for shorter-term assignments) beyond the civil service and uniform structures. Mr. Carter added that empowering people to take ownership increases retention, but hands-on leadership and management are essential. Dr. Stricker pointed out that this leadership style might be foreign to some members of the Air Force; the culture has to encourage creativity and minimize bureaucracy. Mr. Edward Drolet, deputy director, Chief of Staff of the Air Force Strategic Studies Group, noted that the Joint Artificial Intelligence Center is working to develop AI talent for the DAF.
WHAT DOCTRINE, CONCEPTS OF OPERATIONS, AND TACTICS, TECHNIQUES, AND PROCEDURES DO WE NEED TO OPERATE IN A DIGITALLY TRANSFORMED AIR FORCE?
PANEL TWO
Lt. Col. Brian “Dante” Burgoon, 561st Weapons Squadron Commander, Nellis Air Force Base, explained that the 561st is responsible for Air Force Tactics, Techniques, and Procedures (AFTTP) support
and development for all Air Force documents. The 561st is currently developing 113 AFTTP 3-1s or 3-3s and is responsible for more than 200 manuals. The 561st is engaged in a continuous cycle of writing, publishing, and notifying end users. The current construct requires a 2-year rewrite timeline for manuals—during the 2-year process, end users codify new tactics that should be included in the manual, subject matter experts collaborate, and then the document can be updated. A working group meeting with end users and subject matter experts is hosted every week at Nellis, during which a PDF is created that can be pushed out to end users after editing and approval. During the 1.5- to 2-year gap between the rewrite of entire documents, flash bulletins are released to end users. He emphasized that, on this timeline, it is taking too long for many good tactical ideas to make their way into documents. Notification is also a problem, as only some end users are signed up for email alerts.
Lt. Col. Burgoon noted that the 561st developed the KNITE program to address two issues: (1) from the user perspective, cross-document knowledge was low and access was difficult; and (2) from the perspectives of AFTTP or doctrine writers, the writing process was difficult. The purpose of the KNITE program is to shift from taking months or years to capture ideas in documents and distribute them to end users, to developing a more iterative process.
In the KNITE program’s proof-of-concept, a host service is used for the rewrite process and dissemination. He compared it to a Google search that leads into a Wiki page: the end user can search by keyword and find guidance in one place instead of sorting through multiple PDFs. When users log-in to this system, the system will know the person’s credentials and background and provide the right level of access to information and search capabilities. People with more experience and a higher level of need-to-know will thus have a larger volume in their search results. A comment feature will be available to input desired changes, the contents of which will be captured and provided to the subject matter experts and adjudicators to consider for publication and updates. With this new approach, he continued, it would be possible to update ideas and new tactics quickly instead of waiting for 2 years to contribute to the publication of a rewrite. The KNITE architecture is useful not only for AFTTP development but also for doctrine.
Lt. Col. Burgoon revealed that the KNITE program has several goals: (1) transform how tactics are captured and disseminated; (2) streamline the creation and update of tactics through a knowledge curation tool, allowing rapid response to emerging threats and capabilities; (3) store data elements as nodes, allowing for robust semantic queries that can be output in several user-selectable formats; (4) standardize common content across communities and ensure that every operator has the most up-to-date tactics; (5) perform context sensitive queries based on tactician profile and viewing history; and (6) create a collaborative web-based content creation, editing, and approval environment, streamlining the tactics dissemination process. The Air Combat Command/A3 established KNITE as a requirement in March 2021, and the target goal for development at scale is June 2022.
Ms. Westphal asked about disconnects among planning, acquiring, and using systems. Lt. Col. Burgoon replied that the Air Force is trying to develop tactics as quickly as possible. Ninety percent of AFTTP is dedicated to rewrites and adapting to the enemy with new tactics. The 2-year cycle, however, is not adaptive—allowing subject matter experts to provide direct input in the new construct will drastically speed up this process. Ms. Westphal wondered if AI would be used to collect those inputs and present options for the best way to update tactics. Lt. Col. Burgoon mentioned that his team is working with MIT on AI initiatives to aggregate faster. However, the base architecture has to be developed first before AI can be injected and executed.
Mr. Munson asked if other Air Force users would benefit from having a similar tool and whether this capability could be hosted in the Air Force’s digital environment. He also wondered if KNITE would serve as a helpful use case for the architects of that digital environment. Lt. Col. Burgoon responded that KNITE will likely be hosted on Platform One. He remarked that opportunities exist for other users to leverage the KNITE architecture for document publication. Gen. James (Mike) Holmes (USAF, ret.), senior advisor, The Roosevelt Group, expressed his concern that even with the application of digital tools, there will still be a shortage of subject matter experts to work through the material. Lt. Col. Burgoon recognized this challenge but said that the 561st is now linked directly to the weapons school instructor pilots, who are the
subject matter experts for the rewrites, to enable monthly releases of information. Gen. Holmes suggested involving wing weapons officers, who can provide information about resource availability for execution. Lt. Col. Burgoon noted that the new system will promote cross-talk among the subject matter experts as opposed to only having occasional meetings. Gen. Holmes asked how the system will be secured, and Lt. Col. Burgoon emphasized that software is being developed inside the constraints of Platform One so as to adhere to its security standards.
Ms. Westphal asked if enough attention is being paid to the edges of the Air Force in terms of structural and cultural change. Gen. Holmes described the KNITE initiative as an example of the Air Force making a good decision to push authority and responsibility down to the experts in the weapons school and in the 561st. Now, the 561st needs the tools to make this new culture successful.
In response to a question from Dr. Green about whether auto-tagging and auto-classification methods are being used in the KNITE program, Lt. Col. Burgoon noted that there are search-based queries for each paragraph. Dr. Green added that even if the documents are parsed down to the paragraph level, there can still be categories for tag values that can be role based and pushed out to the appropriate people. Lt. Col. Burgoon explained that while it is possible to tag everything, doing so could be ineffective if people with lower levels of classification are accessing only portions of documents. Gen. Holmes remarked that natural language/ML tools could be helpful with this issue. Although such tools would be useful, Lt. Col. Burgoon described them as “higher ticket items” because more programming capability would be needed first. Ms. Westphal asked about gaps in Air Force effort that need to be refocused to operate in a more digitally rich environment. Lt. Col. Burgoon expressed his concern about maintaining the funding needed to continue improving—increased buy-in and sustained investment enable robust capabilities.
Mr. James Crocker, Chief Technology Officer, BESPIN (Business and Enterprise Systems Product Innovation), explained that BESPIN emerged to address two challenges: (1) how to build a software factory to target mobile application development, which had not been done previously in the Air Force; and (2) how to create a software factory that focused across all of the functional areas, within the policy constraints and hurdles of the government. BESPIN started ~2 years ago with eight people focused on the “art of the possible.” They concentrated on user-centered design and quick resolution of pain points through automation and applications. He emphasized the value in having metrics to demonstrate impact and the ability to scale, which increase buy-in and a willingness to partner to improve overall manpower capabilities. BESPIN has paired Airmen one-to-one with industry, which helps capability to progress faster. BESPIN is able to capitalize on all of the functional airmen across the Program Executive Office to create the capability to focus on needs and direct them to meet the functional owners’ requirements.
Ms. Westphal asked what BESPIN has accomplished thus far and what issues it plans to address in the future. Mr. Crocker said that since BESPIN received its second continuous Authority to Operate, it can push to any endpoint and deliver to any edge network or backend cloud infrastructure. He described the ability to facilitate different tech stacks as a significant achievement. Furthermore, there are efforts to democratize and understand data that are siloed between different systems (e.g., there are 2,000 data sources in the Air Force, none of which talk to each other). An enterprise-level effort, Data-as-a-Service, aims to make these data cross-functional. Twenty different applications and five enterprise efforts are in production, as well as Digital University, which has expanded from its grass-roots movement by airmen to facilitate operational capabilities and training. He remarked that the integration of DevSecOps has revealed a massive manpower shortage. In the coming year, BESPIN hopes to engage more with Digital University to address this issue, as Digital University is changing the framework of how the Air Force trains, assesses, and vets for Air Force capabilities. Another important BESPIN goal is to drive down the cost of developing software for squadrons, wings, groups, and flights, for example, and to drive down the time to production. He envisioned eventually driving down the 800 man-hours needed to deliver an application to cloud infrastructure to 100 man-hours, which would lower full-time equivalent costs and produce capabilities faster. Ms. Westphal wondered how this improvement would factor into the acquisition process and into companies and industry. Mr. Crocker acknowledged that acquisition presents a hurdle; BESPIN is trying to establish pre-vetted contracts focused on blueprinting application types, which could reduce contracting time from 90 to 30 days.
Ms. Westphal asked if there are any culture clashes between old and new processes as the organization matures. Mr. Crocker revealed that these clashes arise every day. He described the “frozen middle” that spends more time trying not to change than the time it would take to change. Repeated demonstrations of performance are key to showing stakeholders the art of the possible and “thawing” this frozen middle.
Dr. Green asked if BESPIN has an integrated platform-as-a-service so that when the data are integrated, a catalogue would show the classification levels of those data. Mr. Crocker said that BESPIN is working on the ingestion and virtualization layers to better understand metadata—everything being targeted is Impact Level 4 and is being tagged. BESPIN works with Palantir for some of the virtualization pieces, and meta-tagging efforts continue as the data are normalized. Dr. Green wondered if a data catalogue with data lineage exists. Mr. Crocker replied that this work is ongoing, but it is challenging given how much of the data are siloed.
Mr. Crocker explained that as BESPIN began to build applications, it realized that for 30 percent of each application, the development cycles were consumed by trying to get the data to work, trying to couple with data, trying to reach back for data, or trying to share data. He described this as a major pain point: the ~312 squadrons across the Air Force were spending an average of 100 man-hours each per week working with data. This was the impetus for moving Data-as-a-Service to an enterprise level effort, and a new contracting methodology made it possible to “double-dip” contract dollars for capabilities and realize substantial cost savings.
Mr. Santee observed that much of this work relates to process reform. He asked about BESPIN’s process to move from a document-driven to a data-driven practice. Mr. Crocker noted that the first step was to consider how the user requirement could be addressed. He emphasized the value of involving people in solving problems instead of forcing them to adopt preconceived solutions. Once the problem was understood, solutions had been exhausted, and the best solution had been identified, a directive emerged. That then drove the process reform of the Air Force Instruction. He added that DoD’s discomfort with policy change remains a challenge, but this is a better approach.
Ms. Westphal inquired about challenges or opportunities to accelerate to a digital force. Mr. Crocker replied that innovation efforts need more champions and should be vectored under a functional owner. Having topcover and an established funding line for at least 3 years for these innovation efforts would help to thaw the frozen middle overall, he continued. Ms. Westphal wondered if innovative people will stay with the Air Force or will seek more interesting careers elsewhere. Mr. Crocker noted that the Air Force needs to prevent industry from hiring its experts by providing relevant training, topcover for flexible innovation, and an empowering career path.
CONSTRAINTS AND CONSIDERATIONS FOR OPERATING IN THE FUTURE: A PANEL PRESENTATION
Dr. Julie Ryan, chief executive officer, Wyndrose Technical Group, and study lead for the National Academies of Sciences, Engineering, and Medicine report Energizing Data-Driven Operations at the Tactical Edge: Challenges and Concerns,1 noted that the Air Force uses a significant amount of energy; in 2017, it used 48 percent of energy expenditures for the entire DoD. Of that, 86 percent was for aviation fuel and 11 percent was for installation expenditures. With 97 percent of expenditures being used for aviation fuel and installation, a question arises about the tactical edge. The conversation about the future revolves around everything being wired for sensors and communication and coordinated using AI and ML, and creating sense and process data for a highly coordinated decision cycle capability against adversaries.
She explained that the National Academies was charged to investigate and produce a report on energy challenges and opportunities for future data-driven operations. The study committee was expected to
___________________
1 National Academies of Sciences, Engineering, and Medicine, 2021, Energizing Data-Driven Operations at the Tactical Edge: Challenges and Concerns, The National Academies Press, Washington, DC, https://doi.org/10.17226/26183.
investigate the current state of Air Force planning, research and development, and expectations related to energy usage for military operations in the 2030 time frame; investigate potential threats to energy assurance and access based on recent events and assumptions of future energy dependence that should inform Air Force/government planning for energy generation, storage, and use; investigate and describe current research and state of the art in energy efficient computation including hardware, software, and big data; investigate and describe the energy needs for advanced weapons platforms including the static infrastructure that provides support to ML, AI, and integrated operations; and recommend manpower, research, and expertise requirements needed for the future energy environment.
Dr. Ryan commented that we live in an energy rich environment where we take power flow for granted—a bad assumption for operating in a contested environment. With the explosion of IT within warfighting systems (e.g., wearables, and emerging concepts such as JADO and dynamic basing), two questions arise: (1) How will devices that enable the knowledge-based future be powered? (2) How will devices that are farthest from stable and permanent locations manage their energy needs? She emphasized that without power, there are no data, no communications, no data processing, and no collaboration. She described one of the models used by the study committee to explore these questions. The Energy Ecosystem model includes transmission (data and energy), protection (energy grid, mission/force), time horizon (today and 10 years into the future), and environmental controls (temperature, humidity, and particulates), all anchored by compute and storage capabilities.
The study committee came to consensus on 47 findings and 16 recommendations in its report, some of which Dr. Ryan summarized for workshop participants as follows:
- Energy needs associated with readiness are not expressly collected. No one knows how much energy will be needed for the functionality of data processing or to support combat operations at the tactical edge. Yet, the impact from loss of power is potentially devastating. The ability to execute mission requirements with knowledge-intensive systems must be reflected in both unit and mission readiness associated with the energy required. The committee recommended including energy needs in readiness reporting metrics for all weapons systems. The committee also recommended that resource and capability readiness assessments should include the availability of adequate and appropriate energy to ensure data capabilities at the tactical edge.
- Pull-the-plug activities are not included in most field exercises; in fact, most field exercises have extremely robust energy infrastructures. Yet, power and other infrastructures associated with power will be the targets of attack and will not be continuously available. Losses may stem from existing poor commercial infrastructure, enemy denial, lack of maintenance, lack of fuel, or human error. The committee recommended conducting pull-the-plug exercises for all realistic field exercises. Data from those exercises should be used by the mission planners, and the results of the pull-the-plug exercises on tactical edge data capabilities should be used to revise and update mission readiness assessments.
- Energy needs for computational support are not defined in any major weapons system or mission profile. The committee made the recommendation to include energy needs associated with data expectations, both for support and internal to the mission or system, as explicit requirements for all missions and systems. The contracts should include language that requires specific and complete descriptions of energy needs, types, and compatibility with logistics support. It is also essential to explicitly address the energy minimization, power consumption monitoring, and energy generation for the tactical edge information environment, including all small devices and Internet of Things capabilities.
- The manpower skillset needed to maintain, install, and upkeep energy at the tactical edge is rare. The committee recommended establishing a manpower program to recruit, educate, assign, and train both military and civilian personnel to address the energy challenges associated with data-driven operations, particularly those not likely to be solved by the commercial enterprise. The committee also recommended that energy engineers (particularly specialists such as antenna and
- radio frequency engineers) should be incentivized with interesting work opportunities.
- Delivering energy to users (especially small users) is a challenge. The committee made the recommendations to develop an economic benefit model exploring the utility, opportunity costs, risks, and benefits for different energy delivery modes; explore alternative methods of harvesting, storing, and reusing power; and consider the logistics tail for the energy types and methods of delivery from the perspective of cost efficiency of energy delivery and operational costs associated with single energy sourcing. Dr. Ryan added that the Marines are experimenting with using drones to deliver batteries to small users (as opposed to conventional fuel convoys), which mitigates human risk and reduces opportunity cost if the drone is shot down and another needs to be sent.
- Technological interoperability is a concern for deployed American forces, particularly in foreign countries that have different energy infrastructures. The committee recommended considering interoperability with foreign nation power systems and partner military forces when designing power systems, including standardization of certain elements and plug-and-play capability.
- The energy implications of planning and design choices need to be understood. The committee made the recommendation to invest in future research (e.g., product and process technologies associated with reducing energy usage, minimizing energy logistics risk, and improving energy resiliencies; energy-aware algorithms in practical deployable software; and approximation techniques in software algorithms that are effective in energy reduction without compromising accuracy) and conduct experimental campaigns in realistic scenarios, including a variety of systems and deployment characteristics of tactical-edge units, to guide the research and implementation potentials.
Dr. Ryan described energy as an urgent consideration for the Air Force. She noted that because it will take a substantial amount of time to develop a comprehensive research program, these areas have to be prioritized. The committee suggested the following plan:
- Near term—energy needs and readiness, pull-the-plug exercises, explicit energy requirements, and manpower.
- Midterm—energy minimization, skillsets, energy resilience, and interoperability.
- Longer term—research.
Ms. Westphal asked which aspects of energy the Air Force could consider, given that it may have different energy sources in the future than it had in the past. Dr. Ryan said that it might not be possible to develop airplanes that run on batteries with the same thrust and capability as those that run on petroleum-based fuel. She explained that as global warming becomes an even more significant problem, petroleum-based fuels will likely be reserved for trucks and planes, while everything else will be forced to use renewable waste systems, kinetic energy generation, and transportable solar grids and wind systems. This transition would require new knowledge capabilities, implementation strategies, and transformers. Ms. Westphal inquired about operational partnerships around energy, and Dr. Ryan noted that potential conflict areas such as the Sahara Desert or the Himalayas create particular challenges because of the environments and the particulates (e.g., if the humidity is at the wrong level, technology does not function). Because the Air Force will operate in so many different environments, this as a nontrivial engineering challenge.
Ms. Westphal wondered if the study committee considered the relationship between energy and competition with China. Although the committee did not address this issue in its report, Dr. Ryan mentioned that Elizabeth Economy has done research on how China relies on Africa and other places to obtain energy and grow food for its people. China is resource poor, and its primary raw material for energy is coal, but in order to achieve the national priority to reduce pollution, coal use would need to be reduced. China has thus begun to embrace solar and wind energy. She explained that China is moving into energy independence faster than the United States; however, because China is pushing down the per-unit cost, the rest of the world now has more opportunity to become energy-independent.
Dr. Drew stressed that the Air Force has to invest in this issue because industry does not have a ready solution for the energy problem. Dr. Ryan underscored that the solution demands collaboration between civil engineers and operators, which is a challenge given that they speak different languages and work in different time horizons. Dr. Chellappa added that energy will be extremely important to enable AI-based systems in space. He also noted that AI would benefit substantially if low-power graphics processing units could be designed that are easier to cool.
Col. Jonathan Zall, ABMS Cross-Functional Team (CFT), Air Force Futures, Headquarters Air Force (HAF) A5, described ABMS as the DAF’s contribution to the joint force’s JADC2 effort. The ABMS CFT developed a campaign plan to address what the warfighters have identified as major capability gaps associated with command and control and battle management. Many of these gaps and opportunities relate to digitization; he asserted that when the outcome is increasing success on the battlefield and bringing airmen home safely, these opportunities to digitize become obligations.
Ms. Westphal asked about the role of the CFT as well as its relationship to the larger DAF architecture and technology effort. Col. Zall described the CFT as the bridge between (1) the warfighters and their capability needs; and (2) the acquisitions team and others who will develop the DOTMLPF-P (doctrine, organization, training, materiel, leadership, personnel, facilities, and policy) solution set. He emphasized that the CFT is not comprised of technologists; the CFT’s role is to understand and codify capability gaps and accelerate the delivery of usable solutions. The CFT first assembles an operations planning team to address specific warfighter-required capabilities (e.g., communications, connectivity, decision making). After identifying gaps and opportunities, the CFT assembles an integrated development team to accelerate the delivery of solutions to the warfighter—instead of writing requirements and then providing a capability 10 years later. The goal is to emerge from this process with a list of requirements, a test plan, and the documentation to move forward quickly to achieve minimum viable products and prepare to transition to a sustainable program for the warfighter.
Ms. Westphal wondered whether the CFT has quantitative or anecdotal data to demonstrate that this approach has increased the speed of the process. Col. Zall replied that because this is a new effort, there are no measurable data available yet. The CFT is adjusting to the vision of the new leadership and is optimistic that once the campaign plan has full approval, the CFT can move forward and begin to measure success, which is important to demonstrate value.
Ms. Westphal asked whether ABMS is issuing warfighting capabilities in a way that embraces the desired operational speed and behavior of the digital transformation. Col. Zall explained that ABMS plans to leverage the efficiencies that the Rapid Capabilities Office can achieve in delivering capabilities, and translate those into broad, scalable, sustainable programs of record for warfighters to use operationally. However, limitations and constraints exist: instead of writing new laws, ABMS is trying to work within the existing framework and use efficiencies within the broader system. In response to a question from Ms. Westphal about priority areas for the CFT, Col. Zall stressed that addressing “the China problem,” is a top priority, because previous approaches to executing battle management and command and control will not lead to the desired results in a competition with China. The CFT is considering how ABMS could provide operational advantage—particularly decision advantage. The CFT is also focused on data sharing as the key enabler for progress: data sharing will establish the information flow to achieve decision superiority. In response to a question from Mr. Munson about the Chinese DF-21D, Col. Zall said that owing to its organizational construct, the CFT views problems holistically instead of addressing specific threats. Mr. Munson suggested that focusing on that particular threat could lead to more expedited acquisition authorities.
Ms. Westphal asked if there is a unity of effort in the Air Force to become a digital force, which would enable solutions for the data-sharing problem. Col. Zall noted that while many people within the Air Force are working on this urgent problem, it is not happening under a single authority. Individual commands, geographic areas, and agencies are working on different solutions, and many efforts are duplicative. To achieve unity of effort, Col. Zall suggested establishing the credibility of the CFT (including the Rapid Capabilities Office and others involved in the process) as warfighter advocates who are capable of
delivering something worthwhile before another problem emerges. At that point, he continued, it may be possible to expand ABMS and achieve coherence across efforts.
Col. Zall expressed his concern about balancing the optimization of the day-to-day office environment with the optimization of a dynamic combat environment, and wondered if others consider that tension when prioritizing efforts for the digital transformation. Mr. Santee noted that there is a difference between formatting data for a repository for future analysis and formatting data in motion, such as those for ABMS’s purposes. The Aerospace Corporation is trying to determine the optimum trade-off between data in motion (e.g., weapons systems data) and data at rest (e.g., maintenance data) for the Space Force. Gen. Holmes encouraged the CFT to continue to optimize its approach to best support the warfighter. Dr. Paul Nielsen (USAF, ret.), director and chief executive officer, Software Engineering Institute, Carnegie Mellon University, posited that although digitization could improve almost everything in the Air Force, that does not mean that everything has to be on the same network or be fully integrated (e.g., things with different time scales of operations than the warfighter capabilities). Gen. Holmes cautioned against optimizing Cloud One for analysis at the expense of latency for warfighters and highlighted the advantage of having multiple providers.
Col. Zall asked workshop participants for their perspectives on decision advantage as well as on the optimization of data flow and data management for a human decision maker versus for analysis. Mr. Santee emphasized that while increased decision-making speed is critical, improved decision-making quality is even more important—with higher quality data from exquisite sensors and more data informing the decision. He said that The Aerospace Corporation is encouraging the Space Force to use the Unified Data Library but noted that using it in an ABMS environment might not be as effective. Col. Zall noted that speed often results from the elimination of unnecessary delays that have been baked into processes. He echoed Mr. Santee’s assertion about decision-making quality, because if a person makes the wrong decision, it will not matter how quickly he did so. He added that ABMS is not only improving command and control processes but also creating a gap between the decision capability and the decision quality of the adversary.
Ms. Victoria Yan Pillitteri, acting manager for Security Engineering and Risk Management Group, Information Technology Laboratory, National Institute of Standards and Technology (NIST), explained that NIST’s mission is to promote U.S. innovation and industrial competitiveness by advancing measurement science, standards, and technology in ways that enhance the economic security and improve overall quality of life. One of NIST’s strengths is its reputation as a neutral technical entity. It strives for technical excellence and integrity; is uncompromising in its pursuit of truth; is rigorous in its processes and methodologies; and provides an unbiased industry-focused result of standards, technology transfer, and research outputs. Serving as a non-regulatory agency within the U.S. Department of Commerce, NIST promotes the competitiveness of U.S. companies worldwide. NIST cultivates trust in technology and cybersecurity through research and development, the transition of research products to practice, the development of standards and best practices, outreach, and interagency and private sector coordination and collaboration to ensure that the research and products developed serve relevant communities of interest. NIST’s technical guidance is leveraged by the federal agencies, the private sector, industry, academia, and international governments and companies.
Ms. Pillitteri noted that NIST has three types of publications related to cybersecurity and privacy standards and guidelines: (1) the Federal Information Processing Standards (FIPS) are developed when required by statute and/or a compelling federal government requirement for cybersecurity; (2) Special Publications (SPs) serve as guidelines, technical specifications, recommendations, and technical reference materials; and (3) Interagency Reports are reports of research findings, including background information for FIPS and SPs. All three types of publications are intended to help organizations of any sector or size better manage risk. NIST’s research staff also develops research papers for technical conferences, presents poster sessions, and issues white papers and green papers. She explained that a robust and participatory process is used for the research and development of NIST standards and guidelines, based on the following foundational principles: transparency, openness, balance, integrity, technical merit, global acceptability, usability, continuous improvement, and innovation. First, NIST identifies a research topic for publication
or update. NIST then conducts research and seeks preliminary stakeholder input. The NIST staff will continue researching and begin to draft the publication. When ready, it will be published for a public comment period. At the end of the comment period, NIST collects all input received, and reviews, analyzes, and adjudicates it. A decision is made whether additional stakeholder input is necessary and, if so, whether additional research is needed before the final publication of the document. She emphasized that NIST is committed to vetting its publications thoroughly, and releasing timely and relevant information to support the needs of industry.
Dr. Chellappa pointed out that the NIST-800 series standards are too restrictive for universities. If the federal government were to require universities to follow NIST-800, universities would not be able to accept grants from the federal government. He wondered how NIST balances security concerns with the value of working in an open environment. Ms. Pillitteri replied that NIST guidance advocates that all organizations in all sectors do basic due diligence in protecting their systems and information. She said that many DoD organizations use NIST SP 800-171 to protect the confidentiality of controlled unclassified information, but she acknowledged the need to balance openness to allow critical collaborations with the protection of federal information. Although specific federal agencies determine their own security protocols for their partnerships, a university that is processing, sorting, or transmitting federally controlled unclassified information would have to follow the minimum safeguarding requirements in NIST SP 800-171, which are required by law.
Dr. Langston remarked that the NIST-800 series is human-intensive, and he wondered why automated penetration testing tools are not used to validate the security of systems. Ms. Pillitteri commented that there is no “silver bullet” to address all security concerns. She said that there is a place for the processes and procedures at the governance level, and a place for the specific technical tests. How tests are conducted at different organizations depends on each organization’s system architecture, security architecture, solutions, and processes. Because NIST has no insight into many of these variables, when it writes technical guidelines, it is building a foundation that can be customized by environment. Dr. Langston expressed his concern about the cottage industry of “cyber experts” who are not true cyber experts and thus are unable to secure organizations. Ms. Pillitteri articulated that this reinforces the need for standards, which provide a common language and common principles.
Gen. Holmes observed that a compliance-based system measures compliance, not security. Although there are many opportunities for people to write standards and for consultants to ensure compliance, systems do not become more secure unless they transition to a zero-trust approach, in which the data are secured through encryption—and even then, no system is ever truly safe from potential violation. Ms. Pilliterri stressed that there is no one-size-fits-all solution for security. She stated that there is a role for compliance with the bare minimum level of security for all systems, but it is important to incorporate critical risk management concepts. Gen. Holmes pointed out that the Air Force has a non-functional network; it is meaningless if this system is compliant when the performance is so poor. Ms. Pilliterri described this as an example of the value of good system design and engineering: it is important to build better systems (e.g., with cybersecurity, privacy, functionality, safety) from the ground up.
Ms. Westphal noted that if the plan is to build well-designed systems, it is important to take a future perspective of design. She also said that “digital trade” has several interpretations, owing to different perspectives on privacy and data across the globe. She wondered if NIST’s standards could address some of these issues. Ms. Pillitteri noted that in addition to developing standards, NIST’s experts participate in international standardization activities to ensure that the United States’ position is well represented. She explained that it is difficult to design systems that are “future-proof” because of the challenges associated with anticipating future needs.
Mr. Munson reiterated that the Air Force needs a clear understanding of how attractive of a cyber target this proposed digital environment would create. He wondered how to achieve the best industrial strength cyber defense capability and whether a partnership with NIST could be suggested to the Air Force. Ms. Pillitteri responded that NIST is always interested in working with any of the federal agencies. She noted that this is a difficult problem to solve, especially given the shortage of the cyber workforce across the government and the private sector, and the challenge of securing the supply chain. She underscored that it
will never be impossible to commit a cyber breach. Mr. Munson stressed that if it is not possible to create defenses to protect this rich data repository with facilitated access and tools, the Air Force should not develop a highly integrated, highly facilitated data architecture to underpin its digitization; it should instead use physical separations where necessary so that it is impossible for someone to breach and access the entire combination of data sets critical to the Air Force’s functioning. Ms. Pillitteri replied that the Air Force has to understand the value of its information and integrate protection that is commensurate with the associated level of risk, but it also has to understand that there are no security guarantees.


















