
Borders, Cyber Resilience, and the Implications of Data Localization
Proceedings of a Workshop—in Brief
Fred B. Schneider, Cornell University, and chair of the National Academies of Sciences, Engineering, and Medicine’s Forum on Cyber Resilience, provided opening remarks. This event was motivated by a July 16, 2020, decision of the Court of Justice of the European Union (CJEU) concerning data flows between Europe and the United States. The decision is of interest from a cyber resilience perspective not only because of its potential to limit services that rely on flows of personal data from the European Union to the United States but also because it is a fresh reminder of broader global data sovereignty trends. Symposium speakers reviewed the CJEU decision, provided perspectives on its policy context and implications, discussed historical antecedents and broader issues surrounding digital trade, and considered the technology and cybersecurity implications of this and other data localization regulations.
CONTEXT SETTING—POLICY AND TECHNOLOGY
Peter Swire, Georgia Institute of Technology, and member of the Forum on Cyber Resilience, began by recalling the history leading up to the July 16, 2020, CJEU decision. The European Union’s Data Protection Directive, which went into effect in 1998, was a major historical milestone in EU privacy regulation. The directive required member countries to adopt uniform data protection laws in order to make it possible for data to flow freely within the European Union while protecting privacy in keeping with its designation as a fundamental right. Among the key provisions of the directive were its definition of “adequate protection” and its call for data about EU citizens to receive the same protection abroad. In 2000, an EU–U.S. Safe Harbor agreement on privacy principles was signed and approved by the European Commission and the U.S. Department of Commerce, to ensure that EU-level privacy protections would apply to data transferred to the United States. Although the legal protections were very strict on paper, Swire observed that there was a low level of compliance or enforcement.
A decade and a half later, in October 2015, the CJEU invalidated the Safe Harbor framework. This change was precipitated by Max Schrems, an Austrian lawyer and privacy activist, filing a complaint against Facebook in Ireland, Facebook’s European headquarters. Schrems claimed that the Safe Harbor agreement was inadequate in light of U.S. surveillance activities. Reflecting on the CJEU decision, Swire commented that in his view, the court’s decision was based on an inaccurate factual record, including a newspaper article erroneously stating
![]()
that the U.S. intelligence community had unrestricted bulk access to Facebook’s data.
In the wake of the Schrems decision, a new EU–U.S. agreement on transatlantic data, known as Privacy Shield, was put in place. Meanwhile, believing that the United States still had not done enough to fix its surveillance laws, Schrems filed another legal challenge in Ireland. The December 2015 complaint focused on Facebook’s use of Model Clauses as an adequate protection mechanism. When the case came to trial in 2017, Swire testified as an expert on U.S. surveillance law. The Irish High Court referred the question to the CJEU in 2018, and in a July 16, 2020, decision that has come to be known as Schrems II, the Privacy Shield agreement was invalidated.
Swire recounted debating Schrems in Brussels in 2016. During the debate, Swire highlighted that many countries have no laws governing surveillance practices and emphasized the practical impacts of the decision to forgo Model Clauses. Schrems recognized the tendency of European law to protect privacy and security very strictly. He observed that the argument that to protect data privacy is to protect fundamental rights, and that all surveillance violates those rights, is very persuasive in Europe. When Schrems won the second case, the Privacy Shield agreement became invalid because it did not provide essential equivalence—that is, ensuring rights and freedoms protections essentially equivalent to those guaranteed within the European Union. According to the court, there were two issues with the U.S. system: no right of individual redress—that is, the ability of EU persons to receive a determination that their rights have not been violated by U.S. national security surveillance; and a lack of proportionality between U.S. intelligence activities and the justification for such surveillance. At the time of this workshop, Swire, along with others, had proposed ways to create a system of individual redress that might be workable. The second weakness of the U.S. system, what European law called “lack of proportionality,” is a matter of not adhering to the European Union’s general principles for processing personal data. In the European Union, one is allowed to process data only when doing so is “necessary and proportionate.” This is because under European law, processing personal data in general is illegal without a legitimate basis. The European Union cited two programs as too broad. The first is section 702 of the Foreign Intelligence Surveillance Act (FISA), and the second is data collection outside the United States authorized under Executive Order 12333. In response, the United States is considering a variety of measures such as limiting the use of FISA section 702 surveillance of EU persons.
Looking beyond the Schrems II decision, Swire suggested that in the short term the United States and European Union will attempt to negotiate a new compromise. In the mid-term, Swire believes that companies will conduct due diligence in an effort to establish that they have put adequate safeguards in place themselves. This will spur considerable litigation in the European Union and foster a growing awareness of the seriousness of the situation, which is documented by research at the Cross Border Data Forum on the effects of data localization. In the long term, Swire predicted, there might be a massive disruption of transatlantic flows of personal data, and/or a new EU–U.S. agreement will emerge.
The Schrems II decision, with its scrutiny of government surveillance, will impact not only the United States but also other EU partners. For example, will Brexit render the United Kingdom an inadequate data custodian? And what will happen with respect to China, a major trading partner for EU countries? In response, international discussions are starting to be held, for example, at the Organisation for Economic Co-operation and Development (OECD), on new standards for government access to data held by commercial actors.
Swire went on to outline the November 11, 2020, EU Regulatory Approach guidelines from the European Data Protection Board (EDPB). The European Essential Guarantees for Surveillance Measures summarize constitutional requirements for data access, including the following: processing must be based on clear, precise, and accessible rules; necessity and proportionality with regard to the legitimate objectives pursued must be demonstrated; an independent oversight mechanism
![]()
must be in place; and effective remedies need to be available to the individual.
Swire cited Theodore Christakis’s step-by-step analysis of EDPB guidelines, which highlights how improbably strict and impractical these guidelines are.1 Notably, the guidance rejects risk-based approaches and says that data flows must be stopped if there is any degree of risk. The guidelines also appear to prohibit transfers to any third country that lacks “adequacy,” and would prohibit transfers to the countries such as the United States, China, or India if data are stored in unencrypted form. By contrast, the European Commission’s executive branch has called for a risk-based approach; even within Europe there is disagreement between those favoring a risk-based approach and those favoring broad limits. Swire pointed out that only 11 countries meet current European standards for “adequate,” which could lead to the EU courts stopping companies from transferring data to much of the world. Interestingly, he noted, many technology companies have been reluctant to call out this possibility because they do not want to admit to the regulators or their business customers that their current practices may be contrary to the current European rules.
Swire further noted that some countries outside the European Union are showing increasing interest in data localization. For example, China has “hard” data localization policies that make it illegal for much data to leave the country. Other countries have policies that are somewhat softer. For example, Russia enacted legislation requiring that a copy of the data stays in Russia so that the government can access it, and India has enacted a strict data localization law for financial information. Other countries, such as Indonesia and Malaysia, are considering or implementing some form of data localization regulation.
An emerging approach, as seen in China and some U.S. proposals, is the idea of reciprocal access. This means that country A can, with appropriate legal authorization, access country B’s data, if reciprocal access is given. Over time, negotiations among countries or groups of countries may result in blocs of countries with mutual reciprocal transfer agreements and prohibitions against transferring data to specified countries outside the bloc. Another idea that is spreading is “data sovereignty.” Illustrating the risks of such approaches, Swire pointed to the interruption to globalization that occurred in 1929. The rise in protectionism that was driven by the Depression not only worsened the economic picture but also contributed to political isolation, the rise of authoritarianism, and ultimately World War II. Although that is clearly an extreme case, there are evident risks from a widespread cutoff of global flows of data. In the finance sector, for example, regulators need to be able to oversee corporations on a company-wide basis—for example, to monitor potentially fraudulent transactions. Other sectors, such as cloud computing services, pharmaceutical research, travel, and e-commerce, rely heavily and fundamentally on cross-border data flows.
Swire presented two key lessons about data localization. First, it is much harder to manage data flows among three jurisdictions, two of which have strict localization rules, than it is to manage data flows for two jurisdictions, one of which has strict rules. In the case of the United States and the European Union, a company could store all of its data in the European Union and move data to the United States only as permitted by EU rules. From an EU perspective, this would be effective as a protectionist measure favoring EU business and also protect the privacy of EU persons. However, should another country or bloc adopt strict localization rules, then companies would have to store data in that jurisdiction as well as the European Union, leading to conflicts as companies continue to require cross-border data flows. In other words, strict localization only works well if one party adopts it and does not work nearly as well if others do also.
Second, the details of back-end processing make data localization much harder than is commonly assumed. Many would assume that a data center providing, say, travel services in both the United States and Europe could simply be moved to Europe. However, Swire noted, there are multiple back-end systems involved
__________________
1 T. Christakis, 2020, “‘Schrems III?’ First Thoughts on the EDBP Post Schrems II Recommendations on International Data Transfers (Part 1),” European Law (blog), November 13, https://europeanlawblog.eu/2020/11/13/schrems-iii-first-thoughts-on-the-edpb-post-schrems-ii-recommendations-on-international-data-transfers-part-1.
![]()
for a traveler from the European Union to the United States—car rental, airplane seat reservations, travel loyalty programs, and anti-fraud cross-checking of numerous databases. What might seem like a simple transaction in fact requires access to multiple systems in both jurisdictions, and thus is not consistent with data localization rules.
Swire identified two links between data localization and cyber resilience concerns: the creation of safe zones for hackers and obstacles to fraud detection. Many cyber defense techniques require collecting and sharing data about the source of attacks, including IP addresses. However, the European Union considers IP addresses to be “personal data” and thus subject to strict privacy rules. Swire posited that such restrictions would make the European Union a great target for hackers to launch attacks on the rest of the world and that the European Union itself might be cut off from receiving data from the rest of the world about attacks that hit the European Union. Additionally, restrictions on cross-border data flows would, Swire believes, reduce the effectiveness of many anti-fraud programs because they rely on analyzing and correlating diverse sources of data to detect potentially fraudulent activity.
Swire concluded by raising the following questions: What would the effects on cybersecurity be from strict restrictions on data flows? Who would be affected most? What strategies or techniques could be used to mitigate these risks? And how can the issues and trade-offs best be communicated to non-technical policy audiences?
HISTORICAL AND ECONOMIC CONTEXT
Douglas Irwin, Dartmouth College, followed Swire’s presentation with a talk on the historical and economic context of globalization. He began with an overview of periods in the past when globalization has had some difficulties. Irwin noted that we are at an interesting inflection point in terms of the direction of globalization, which is referred to as “slowbalisation.”2 Since the global financial crisis in 2008, economists have seen curtailed levels of growth in world trade. There had already been a diminution in global investment flows, and then the pandemic came along, adding momentum to the fragile state of globalization.
As shown in Figure 1, from the late 19th century to World War I, there was a slow trend increase in integration across markets that was being driven by markets moving closer together (period 1 in graph). This was facilitated by the growth of steamships and the telegraph, which expanded capital flows across countries. After the war, recovery and reconstruction of institutional arrangements that facilitated the rise in period 1 were very slow. Many countries did not get rid of the high tariff exchange controls soon enough, and with the shock of the Great Depression, there was a downward spiral and a very low level of economic integration (period 2). After World War II, there was a modest recovery bounce-back, opening trade and capital flows among OECD countries (period 3), which continued to grow in the 1980s and 1990s into the 2000s (period 4). In period 3, mostly Western Europe and the United States had joined the world economy. By period 4, China, India, Latin American countries, and the former Soviet Union countries began opening up and engaging in trade. Irwin emphasized that this was an unprecedented historical epoch in terms of the degree to which it became a world market economy. As in previous periods, there were technological innovations, and the advent of containerization (standardization of shipping containers), that led to increased flows. The impact of
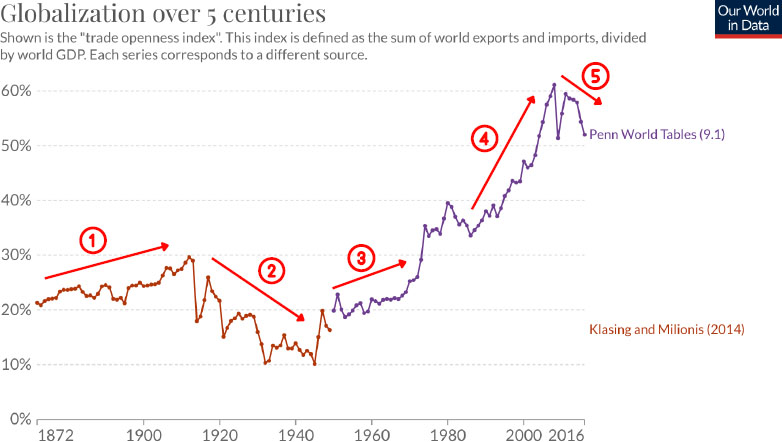
NOTE: Not including services for which there is not much historical data, but the service data would move in sync with that data to some extent.
SOURCE: Douglas Irwin, Dartmouth College, presentation to the workshop. Created and adapted using chart tool and data for 1872–2016 in “Globalization Over 5 Centuries,” Our World in Data, https://ourworldindata.org/grapher/globalization-over-5-centuries-km?time=1872..2016, CC BY-SA 3.0 AU.
__________________
2Economist, 2019, “Slowbalisation: The Future of Global Commerce,” January 24, https://www.economist.com/weeklyedition/2019-01-26.
![]()
the Internet is obviously much harder to measure than air freight, but it turned out to be very important for trade flows as well. The fall-and-rise between periods 4 and 5 was caused by the global financial crisis. There is a bounce-back, but the indicators have been going down. Now, Irwin believes, we are in the fifth period of not just globalization but also potentially a bit of de-globalization.
In the 1920s and 1930s, there was brief de-globalization in which there was a prolonged period of less global integration. The Great Depression was catastrophic for national economies and world trade, and the recovery was also very slow. By the end of the 1930s, world trade was still at a lower level than it had been in 1929. Irwin noted that while there is a huge debate about the extent to which economic difficulties during this period contributed to social upheavals, there is no doubt that economic difficulties were accompanied by grave political difficulties.
When a country is cut off from trade and does not have access to markets for the supplies to keep its industries going, it can make products internally, if it cannot buy those products off the market. This is when there was a big change in U.S. trade policy. Previously, the United States had maintained relatively high tariffs, and while this did not trigger the downward spiral, it certainly did not help anything. When the Roosevelt administration came in, they thought that the goal for the United States should be to repair trade relations that were adversely affecting U.S. recovery. Secretary Cordell Hull almost single-handedly was the intellectual inspiration for the U.S. engagement in the world and the United States’ movement away from isolationism. Hull ended up creating the push that would lead to the General Agreement on Trade and Tariffs (GATT) in 1946–1947 and made the connection that peace and trade go hand in hand.
Since 2008, the de-globalization trend has been seen again—“slowbalisation”—leading to speculation about what is causing it. Some of the previous issues in the 1980s and 1990s driving globalization included the containerization revolution, air freight, and developing country economic reforms. Today, some of the reasons for slowbalisation include global value chains topped off, retreat on reform, the COVID-19 pandemic, and national security. Global value chains, which are supply chains across countries, have topped off after the financial crisis. There was incredible growth in the 1990s and 2000s, and after the financial crisis, this growth went down but came back up. Since then, it has tapered off a bit. Whether growth will continue to go down remains to be seen, but it is difficult to believe that it will explode again because what was driving the growth was countries opening their economies to the rest of the world. Previously, these were countries like China and India, but now countries like Bangladesh are passing Indian per-capita income because they have reformed more effectively and attracted more foreign investment. One of the factors leading to this, to some extent, is globalization retreat.
After 2000, there was an incredible ramp-up of China’s exports as a percentage of gross domestic product from 20 percent to 35 percent by 2006. This is what is known among economists as the China shock because it had an impact on labor markets in the United States, including the decline of manufacturing employment and, to some degree, the closure of factories in many rural communities. Around 2012, China began moving in a different direction.3 Irwin noted how China is not merely inhibiting but taking over and redirecting the private sector,4 adopting policies that have reversed earlier economic reforms.5 Both internal and external pressures have led China’s economic strategy to be more inward-looking, with a greater emphasis on Indigenous technology.6 Their goal of not wanting to be dependent on the United States for semiconductors or other high-tech products has manifested itself in a decline in China’s dependency on the world economy
__________________
3 Irwin noted that Nick Lardy’s 2019 book, The State Strikes Back: The End of Economic Reform in China?, provides a nice overview of what has been going on in China in recent years.
4 L. Wei, 2020, “China’s Xi Ramps Up Control of Private Sector. ‘We Have No Choice But to Follow the Party,’” The Wall Street Journal, December 10, https://www.wsj.com/articles/china-xi-clampdown-private-sector-communist-party-11607612531.
5 K. Rudd and D. Rosen, 2020, “China Backslides on Economic Reform,” The Wall Street Journal, September 22, https://www.wsj.com/articles/china-backslides-on-economic-reform-11600813771.
6 C. Buckley, 2020, “Xi’s Post-Virus Economic Strategy for China Looks Inward,” The New York Times, September 7, https://www.nytimes.com/2020/09/07/business/china-xi-economy.html.
![]()
for exports. China’s inward policy includes escalating its punishment diplomacy. They started using trade as a diplomatic weapon against countries that showed support to Taiwan or Hong Kong, or that tolerate a media that can be critical of China. Most recently, this has been aimed mainly at Australia and the National Basketball Association. These tactics are aggressive and used to punish and control those outside China in order to get them to respect China or fall in line.
When the United States started imposing tariffs against China, the Chinese government immediately retaliated on very politically sensitive exports coming from the United States—namely, farm exports. The U.S. tariffs have meant higher prices for U.S. consumers and farms that rely on imports from China. On top of this, the ongoing pandemic has resulted in at least a temporary closure of the world economy. The pandemic has also resulted in countries thinking about where they get their pharmaceuticals and where those pharmaceuticals are going to be manufactured, which could lead to policy changes down the road to avoid being dependent on the foreign market. While there are sensationalist headlines and articles in The Economist or Foreign Policy magazine stating “goodbye to globalization,” Irwin personally believes that globalization is not dying, but it is evolving.7
Now, Irwin stated, there is a need to look at whether world trade will bounce back. When comparing the effects of the pandemic with the financial crisis in 2008, there is a faster rebound in world trade, so there will not be a prolonged slump like there was with the financial crisis. Of course, no one knows exactly. While COVID-19 could be temporary in terms of its impact on world trade, its impact on the attitudes toward trade among policy makers might not be temporary. When people become fearful or worried about overdependence, particularly in China, there is a backlash that is not forgotten, and people tend to turn inward when they are in situations of fear.8
Irwin observed that there is a lot of talk about moving away from former president Trump’s policies in order to repair Western alliances and get back together with Europe. However, as trained negotiators have pointed out, it is extremely hard to negotiate with Europe. These negotiations are made even more complicated by the differences in sectors, which can lead to complex negotiations and difficulty harmonizing different policies. President Emmanuel Macron of France stated that coronavirus “will change the nature of globalization, with which we have lived for the past 40 years,” adding that it was “clear this kind of globalization was reaching the end of its cycle.”9 In some sense, the data are showing that there is not currently an upward path, but, Irwin concluded, this is not the end of globalization, even if there is a partial retreat.
OPPORTUNITIES AND CHALLENGES FOR TRADE IN THE DIGITAL ERA
Susan Stone, OECD, began with the disclaimer that there may be terminology differences in how the OECD defines terms and what those terms mean in different contexts. When OECD discusses digital trade, it considers different perspectives, including the following: (1) digital trade enhances traditional trade by cutting across all sectors and changing the level of competition across traditional trade channels; (2) digitally ordered parcels are crossing borders, which has implications for customs and related authorities; (3) digitally delivered trade, which includes new tech (platforms combined with devices), can make things more blurry about where the trade comes from and how to categorize it; (4) added confusion when discussing bundled products (smart products that have several types of trade combined into one); and (5) more cross-border data flows, which underpin all digital trade transactions, but raise new issues. OECD recognized that everyone has a different perspective on describing digital trade. The first step was defining what OECD meant as it tried to categorize and look at the different elements of digital trade (Figure 2).
Stone emphasized that data are at the core of digital trade as (1) a means of production; (2) an asset that can be traded; (3) a means through which services are
__________________
7 S. Donnan and L. Leatherby, 2019, “Globalization Isn’t Dying, Just Evolving,” Bloomberg, July 23, https://www.bloomberg.com/graphics/2019-globalization.
8 J. Smyth, 2020, “Coronavirus Shortages Prompt Australia to Bring Manufacturing Home,” Financial Times, https://www.ft.com/content/04ac783d-8ced-4e66-9437-78b607cbd8d4. E. O’Toole, 2020, “‘Canada First’ Strategy Means Economic Self-Sufficiency, Getting Tough on China,” CBC News, Twitter, September 8.
9 D. Irwin, 2020, “The Pandemic Adds Momentum to the Deglobalization Trend,” VOX EU CEPR, https://voxeu.org/article/pandemic-adds-momentum-deglobalisation-trend?fbclid=IwAR2aa5GkEf5b6rojN2ZtEhM7uCQmulSSJ2tZBKwuwQQPV1HCR36WGh.
![]()
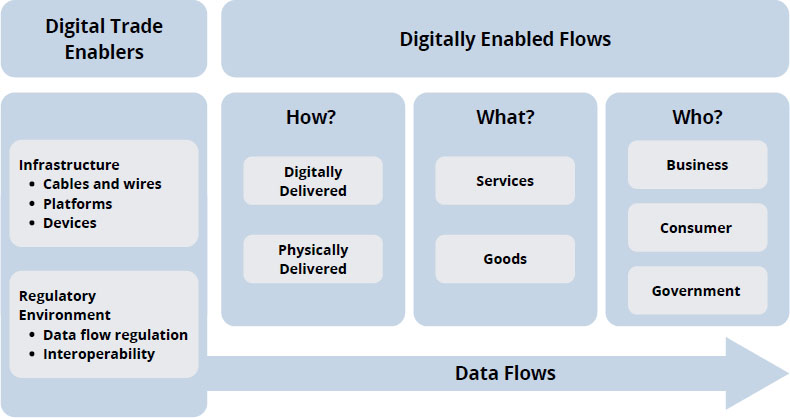
SOURCE: Susan Stone, Organisation for Economic Co-operation and Development, presentation to the workshop.
traded; (4) a means through which production and global value chains are organized; and (5) an enabler for implementation of trade facilitation. This was a new way of thinking for the trade policy community, and the biggest challenge was to examine the infrastructure of transactions in order to identify emerging trade policy challenges. Traditionally, when someone called a taxi service, that transaction was straightforward. Now, if someone orders a ride via a ride-sharing platform, that platform may be located in a different country. The data flows have changed, and trying to measure that in order to determine what to do with trade policy becomes difficult.
Stone noted that the first issue related to measurement is underestimating small-value transactions. A lot of trade minimums means that the amount of trade that crosses the border does not get accounted for by tariffs or other kinds of policies. There is a need to get better at understanding and tracking what these are. OECD, along with the World Trade Organization (WTO) and International Monetary Fund, published the Handbook on Measuring Digital Trade. They consider this a living document that is already in a second edition; and with the constant change in information, they expect to quickly be producing a third. While trade has been around for a very long time, there are not great statistics for measuring services trade, so, Stone noted, they are behind. With the importance of looking at empirical work, OECD is looking at the relative effects and importance of how these things play out in generating growth in jobs and generating ideas for trade-offs in trade negotiations.
Being able to transmit products digitally can reduce trade costs by as much as 30 percent, and these estimates can be even higher for low- and middle-income countries. OECD looked at the idea of tariff revenue reductions because even though the OECD countries by and large have very low tariffs, this is not the same for other countries outside OECD. Especially in many developing countries, the government revenue is dependent on tariff revenue, so a loss in tariff revenue is a big deal in terms of their ability to meet their domestic obligations. Thus, the team needs to provide an idea of what digitalization is and how it affects traditional trade and tariff revenue.
The digitalization of trade is not only about information and communication technology (ICT) sectors but also about trading goods and services. Bilateral trade is increased when there is digitalization increasing in those particular sectors. Digital technologies are not just about services but also about goods, and they enhance the entire economy. OECD created a figure to conceptualize this for policy makers. On average, when two countries sign a Free Trade Agreement, there is an increase of flows by 19 percent. Different proxies were used to measure digital connectivity, but it was found that digital connectivity increases bilateral trade flows by an additional 2.2 percent. When provisions are put in place that define digital connectivity, and consistent means of allowing two countries to trade are developed, digital trade flows increase by an additional 2.3 percent. This shows that there is value in putting time, energy, and effort into having digital provisions in trade agreements.
There is evidence that Internet use has a statistically significant increase on imports. If you import ICT goods, the increase in exports of your services is statistically significant, especially if you have digital connection. The lesson here is that it is important to keep open to trade, even if you do not produce the goods yourself, because this still supports exports in other sectors. These are the types of factors that OECD is trying to quantify to convince the policy community of the importance of digital trade. Concurrently, the landscape is shifting, and
![]()
it is important to understand the changes in order to provide an overview of different regulations that affect data.
Stone asked, why regulate data? Data regulation can apply to different types of data or sectors and reflect a number of different objectives, including the following:
- Much of the debate involves movement of personal data, raising concerns about privacy.
- Some objectives are aimed at meeting regulatory objectives (access for audit purposes) and involve sector-specific data.
- Others relate to national security, protection of information deemed sensitive.
- Others still aim to develop domestic capacity in digitally intensive sectors, a kind of digital industrial policy.
The pervasive exchange of data itself has fueled concerns about the use and misuse of data, leading to new data policies. These new data policies have included a tremendous increase in the regulations surrounding data flows and mainly fall under two categories: data flows and storage requirements. The policy community is trying to develop trade rules in this changing environment. For governments and individuals, there are growing uncertainties related to the applicable rules in any given situation. For firms, challenges arise from the ability to internationalize, and also it is more difficult to know what level of data protection to provide for consumers in different markets. Firms often start engaging in international trade having no idea what the rules and regulations are, or whether they are in compliance with all of the different standards. One OECD project is trying to map the environment to aid with this process. OECD looked at a tool that catalogues and quantifies cross-cutting barriers that affect services traded digitally. It did this in five categories: (1) infrastructure and connectivity; (2) electronic transactions; (3) payment systems; (4) intellectual property rights; and (5) other barriers affecting trade in digitally enabled services (Table 1). From what OECD can see, regulations that affect digital trading are tightening and the regulations are becoming more burdensome.
TABLE 1
The Digital Services Trade Restrictiveness Index Framework Being Developed to Catalogue and Quantify Cross-Cutting Barriers That affect Services Traded Digitally
| 1. Infrastructure and Connectivity |
|
| 2. Electronic Transactions |
|
| 3. Payment Systems |
|
| 4. Intellectual Property Rights |
|
| 5. Other Barriers Affecting Trade in Digitally Enabled Services |
|
SOURCE: Susan Stone, Organisation for Economic Co-operation and Development, presentation to the workshop.
Some regulations that have been implemented include increased limitations on online payments for foreign services providers and increased localization requirements for digital services suppliers. There have also been new relicensing requirements for on-demand
![]()
service providers with localization requirements; mandatory routing of Internet traffic through domestic exchange points; and tightening requirements on cloud computing services (e.g., specific approval for foreign providers, and burdensome conditions on the use of foreign cloud computing services in public procurement). While trade rules continue to apply, how trade rules apply has become more complex owing to blurring distinctions between goods and services, old measures raising new issues, new measures raising new challenges, and simple transactions resting on a series of enabling or supporting factors. Governments have turned to different instruments to enable data flows with trust including plurilateral arrangements,10 trade agreements and partnerships,11 unilateral instruments,12 and private sector and other initiatives.13
Since 1998, WTO members have regularly extended a moratorium on imposing customs duties on electronic transmissions. However, Stone highlighted that with the growing digital trade and tangential issues on digital tax, many countries are finding this problematic and are worried about revenue implications. With no easy answer as to what the counterfactual to the moratorium should be, there is value in taking a step back to put current estimates into perspective, deepen the debate about the impact of tariffs, and broaden the debate to take into account the benefits of electronic transmissions.
Stone concluded that even when facing new challenges, the old principles of market openness can help: transparency, non-discrimination, avoiding unnecessary trade restrictiveness, and interoperability. For transparency, firms should see the costs of operating in a digital trade environment, and consumers should understand what these disciplines mean to them and how it affects as well as protects them. For non-discrimination, domestic and foreign firms and operations should be treated the same to avoid unnecessary trade restrictions, including finding solutions to their domestic issues to have the least impact and restriction to international trade. For interoperability, cohesive language or comprehensive commonalities should be used that can also be extended to procedures and regulations.
IMPLICATIONS FOR TECHNOLOGY AND CYBERSECURITY
Eric Grosse, independent consultant and former vice president of privacy and security engineering at Google, began by noting that it does not sound as if the engineers are going to be the ones to solve the problem of data localization. There is a real risk of courts and regulations acting based on misunderstanding and creating big engineering or user interface effects for little net value in the end. For example, a user gets a cookie consent popup every day but knows that the browser is going to wipe all that data. So much effort is put into what the user thinks is “security theater” and believes is a needless cost.
Grosse referenced a 2017 Lawfare article by Dillon Reisman, “Where Is Your Data, Really?: The Technical Case Against Data Localization.”14 He noted that the article gives good reasons as to why data localization is pretty much a non-starter. Reisman pointed out that net latency raises issues, and a person’s data must be cached close to the location of the person using it. In a world where people travel and data inherently moves around the world, this would be a difficult hurdle. People will not appreciate that in order to read their e-mail, they must have a connection from their local machine and data center all the way back around the world. A second issue is redundancy across failure zones. There are not going to be lots of redundant systems in every country in the world, so it is crucial to have the ability to store things in many countries even if that is just a matter of storage backup. Then there is a need for specialized central batch processing for things like spam e-mails. Grosse previously explained that the reason he uses Gmail in the first place is because it has a better spam filtering system than any other alternative. When a user gets spam in their main mailbox, they can identify it as spam, along with millions of others doing
__________________
10 For example, OECD Privacy Guidelines, ASEAN DPD framework, convention 108+, and APEC CBPR.
11 For example, WTO (GATT, GATS), CPTPP and USMCA, DEPA, and U.S.–Japan.
12 For example, adequacy or equivalence such as Privacy Shield, EU–Japan, or binding corporate rules and standard contractual clauses.
13 For example, ISO standards and sandboxes/data sharing partnerships.
14 D. Reisman, 2017, “Where Is Your Data, Really?: The Technical Case Against Data Localization,” Lawfare (blog), May 22, https://www.lawfareblog.com/where-your-data-really-technical-case-against-data-localization.
![]()
the same thing, and this gets even very novel, clever spam identified. However, if there was a limited pool of data, they would not get identified as quickly. Last, Reisman mentioned global infrastructure. There are debug systems and engineers who can reach into systems around the world to understand why they are failing. It is not feasible or practical to fragment those engineering teams to one debug team per country.
Grosse expanded on an additional issue that was not mentioned in the article: there is often one common software used across the globe, and no one is going to write software over and over again for each “zone.” To do that, engineers would have to start from scratch and write all of the software, which would be prohibitively expensive. There are plenty of technical issues that make data localization impractical. Grosse noted that this is not a new insight and pointed out that it has been well discussed in previous Lawfare publications. There are also some legal interpretations of the EDPB November recommendations, which Swire referred to in his introduction. It says that total data localization is not considered legally adequate with this rare exception of “strong encryption.” However, that means losing all of the advantages that Grosse referred to earlier. While he hopes data localization can be taken off the table, he knows that cannot be done. There are even some reasons to do data localization that deal with protecting against insider abuse or providing better access to transparency. These issues are aided by data localization to some extent but are not related to the goals of the European Union. He stated that his frustration is that data localization is being approached through diplomatic negotiations, when in fact, the way to make any real progress is to have discussions at the engineering level. While progress is going to need to happen on both fronts, they should not be pursued so independently.
Related to authorization authentication, Grosse noted that when someone signs up for e-mail, they do not show their passport. Therefore, there is no way for Gmail to know what country they are a citizen of, which is an intrinsic problem that needs to be considered. To some extent, geolocation is assigned based on the IP address they are signing in from or mostly logging in from. That is adequate for some purposes, but it is not good enough for letting companies understand what legal rules an account is subject to. The plea to policy makers would be to identify whether there is a better way to strengthen the citizenship of an account or keep it global. The latter is consequential owing to the question of whether companies need to have different rules for different customers in different countries. If they need to do that, then there needs to be a better way to know who has which account, which is not being done well today. When Grosse discussed this with lawyers, they threw up their hands and said, “we don’t want to even address that.” Not addressing it will create loopholes in at least the surveillance apparatus. Regarding borders, the toughest privacy problem that individuals have in today’s world is that when someone crosses the customs boundary, their data may be taken to a “back room.” In this case, a person can lose a lot of data without even understanding whether that has happened. While a person may put additional security on the data that crosses borders, most people do not do that, and when encryption is broken on a device or a data flow, there is no way to know what else has been tampered with.
Companies and others are trying to meet standards so that EU data in the United States are receiving the equivalent protections as would be provided in Europe. Instead of dealing with changing the law in the United States, another way to achieve change is to show that data are not very well protected in Europe. This is not in reference to the surveillance teams in the countries themselves, but rather there is a misperception that data are safer from the National Security Agency (NSA) if those data are stored in the European Union than if stored in the United States. That may or may not be true with respect to legal warrants, but as a pragmatic matter of freedom of action for NSA offensive teams, Grosse is convinced that is false. While he cannot prove it, his best estimate was that the NSA bulk collection against Google was mostly done abroad, not inside the country. Grosse stated that it would be great if there was some way for the government to make a safe, public demonstration that shows that the data in those systems are already completely available to NSA. However, he acknowledged that he does not know how exactly to say or do that in a
![]()
nice way that will not offend people, but he emphasized that he believes people are missing the facts on the ground.
There is a popular view in Europe that chief executive officers and general counsels in Silicon Valley are so driven by corporate greed or U.S. government orders that their data are not protected. For the sake of argument, even if that were true, it is also still true that there are senior engineers who actually run the systems who do not feel that way. These engineers are trying to protect the users’ data, and are really trying as hard as they can to preserve privacy. Ten years ago, Grosse saw his job as protecting the billions of Gmail users from government espionage from all countries and thought of himself as a citizen of the world in a way. If the European Union had chosen to develop trust relationships with the senior engineers who live and work inside the European Union, and really know the insides of the systems and what is actually happening regarding privacy, he believed the European Union would have been better off than any Privacy Shield negotiations could ever ensure.
There is a concern for the trajectory that policy makers are on in the absence of a strong account-to-citizenship link. Down this path, a judge anywhere in the world at any future date can be convinced to sign a warrant and someone’s data may get turned over to some law firm. That law firm’s information technology systems can be easily hacked, which means that data are not private in any useful sense, and because of gag orders, the person will not even know if that has happened. Grosse emphasized that he feels the path that is being taken is bad and, in a way, he sympathizes with the EU privacy activist. He stated that he is not happy with the legal system we are heading toward, but companies’ legal teams and discovery teams that respond to warrants do push back, although their ability to push back is ultimately somewhat limited and they are just getting swamped.
Grosse stated that, given this legal trend, if you want strict privacy, you need something beyond plain Gmail or other cloud-enhanced messaging. If someone wants something to not appear in the newspaper, they better not use a system like Gmail. Instead, it would be better to switch to a system like Signal, where there is end-to-end encrypted messaging. That does not mean that the user has no possible chance of their words ending up in the newspaper because law enforcement may be the other person they are communicating with or might persuade the other person to release the material. However, it is a vastly better way to protect yourself and to know when there has been some legal process against your communications. Leaning back on Swire’s comments, these systems are creating a safe zone for hackers and if there had originally been greater trust in law enforcement, it might not have gotten to this point. Safe, encrypted messaging is here to stay unless such software is outlawed completely, and that is unlikely to happen in the United States or the European Union.
Possible policy changes aim to limit bulk centralized processing of data from the European Union, which might seem acceptable, but those accounts would not be allowed access to engineering products that were built on centralized processing. For example, if there is a language that has only 10,000 speakers left and they say that machine learning cannot be used across any of their communications, you do not get the translation. This ties to Google translate, which is a nice feature, but if a group does not participate, then that product gets withheld. There may be better ways to convey that there are consequences to these rules about cross-border data flows because, as Swire indicated, it seems like companies are too scared to say anything about the consequences. If, for example, Gmail were no longer available in the European Union, Google just has to turn off the service, but that likely will not actually happen. Grosse observed that in practice there are ways to fudge the legal language, so the company can decide what is in compliance even though it knows that certain things are not because they are not technically feasible. This is what Grosse expects will happen here—and noted disappointment that there is no alternative way of signaling the consequences.
Grosse noted that now that we are in the thick of things, it can be difficult, and there is no guarantee that a global Internet will continue, even though it has been wonderful
![]()
to have. Grosse recalled the inefficiency of doing open source and international scientific research in an era before the Internet was widely available and fears that we are heading back in that direction. There is nothing that guarantees that information will always be on the World Wide Web. Grosse concluded by stating that this would have been better resolved with a meeting of the minds between privacy activists in the European Union and elsewhere along with engineering-oriented people at technology companies who felt similarly. The legal process that is being used instead is adversarial litigation and will just be a slow path for getting to an endpoint that could have been reached in a less painful way.
DISCLAIMER This Proceedings of a Workshop—in Brief was prepared by Katiria Ortiz as a factual summary of what occurred at the workshop. The statements made are those of the rapporteur or individual workshop participants and do not necessarily represent the views of all workshop participants; the planning committee; or the National Academies of Sciences, Engineering, and Medicine.
WORKSHOP PLANNING COMMITTEE John L. Manferdelli (Chair), VMware; Fred B. Schneider (NAE) (Chair Emeritus), Cornell University; Yair Amri, Johns Hopkins University; Katherine Charlet, Carnegie Endowment for International Peace; Srini Devadas, Massachusetts Institute of Technology; Curtis W. Dukes, Center for Internet Security; Kristen Eichensehr, University of Virginia School of Law; Melissa E. Hathaway, Hathaway Global Strategies; Galen Hunt, Microsoft; Maritza Johnson, University of San Diego; Brian LaMacchia, Microsoft Research; Susan Landau, Tufts University; John Launchbury, Galois; Dave Levin, University of Maryland; James N. Miller, Adaptive Strategies and Johns Hopkins University; James A. Ozment, Capital One; Audrey Plonk, OECD; Ari Schwartz, Venable; and Parisa Tabriz, Google.
STAFF Tho Nguyen, Senior Program Officer; Katiria Ortiz, Associate Program Officer; and Shenae Bradley, Administrative Assistant.
REVIEWERS To ensure that it meets institutional standards for quality and objectivity, this Proceedings of a Workshop—in Brief was reviewed by Anupam Chander, Georgetown Law, and Peter Swire, Georgia Institute of Technology. Liz Panos, National Academies of Sciences, Engineering, and Medicine, served as the review coordinator.
SPONSORS This workshop was supported by the Department of Defense, National Institute of Standards and Technology, and National Science Foundation.
For additional information regarding the workshop, visit https://www.nationalacademies.org/event/12-11-2020/winter-2020-meeting-of-the-forum-on-cyber-resilience-workshop-on-borders-cyber-resilience-and-the-implications-of-data-localization.
SUGGESTED CITATION National Academies of Sciences, Engineering, and Medicine. 2023. Borders, Cyber Resilience, and the Implications of Data Localization: Proceedings of a Workshop—in Brief. Washington, DC: The National Academies Press. https://doi.org/10.17226/26670.













