1
The Security Context for Future Naval Forces
The United States emerged from the Cold War as the strongest nation in the world—economically, politically, and militarily. Compared with any other military capability on Earth, U.S. armed forces enjoy decided advantages in equipment, training, and readiness. They have a long lead in the adaptation and use of modern technologies across the spectrum of military missions. U.S. forces are uniquely able to operate, on relatively short notice and with stunning effectiveness, in any region of the globe.
Yet the tragic events of September 11, 2001, reveal that the vast power of the United States cannot always be summoned to ensure the safety of its people. In addition, experiences in recent years demonstrate that the U.S. military is still vulnerable in some settings to threats from weaker forces. Moreover, the same technological advances that have opened the door to new commercial opportunities and military capabilities can also result in fresh challenges. Nor does the nation’s great military lead always translate into successful outcomes in the international arena.
Reflecting the changes in the national security landscape of the past decade and a half, the United States has revamped foreign policy, updated alliance commitments, and overhauled the national security strategy.1 In addition, the Depart-
ment of Defense (DOD) has updated the operational yardstick by which it measures the size of the military force that the nation needs and has developed new time lines for achieving success in military operations.2 The U.S. Navy and U.S. Marine Corps are responding to the altered strategic landscape with new force structures, new concepts of operations, new organizational constructs, and new personnel policies.
This chapter addresses the challenges and opportunities posed by the new security and technological environments for naval forces today and during the next two decades. It begins with a discussion of the national security environment, followed by an examination of the technological environment and its implications for naval forces. The chapter then presents an overview of changing requirements and missions for naval operations and the changing organizational constructs that the Navy and Marine Corps are adopting to face the new threats and capitalize on emerging technologies. The chapter concludes with findings and recommendations.
1.1 THE NATIONAL SECURITY ENVIRONMENT
Despite the vulnerabilities revealed so visibly on September 11, 2001, U.S. advantages in the economic and military dimensions are extraordinary. The lead that the United States holds over all the other great powers in the world combined is greater than at any other period in the past two centuries.3 In the military dimension, as compared with any other country in the world, the United States spends vastly more on its military (Figure 1.1) and has substantially more modern military equipment.4 U.S. naval capability far exceeds the capability of its closest peer.
|
|
W. Bush), 2002, The National Strategy for Homeland Security, Washington, D.C., July; The White House (George W. Bush), 2002, The National Strategy to Combat Weapons of Mass Destruction, Washington, D.C., December; and The White House (George W. Bush), 2003, The National Strategy for Combating Terrorism, Washington, D.C., February. In addition, since 1996, successive Secretaries of Defense (in consultation with the Chairman of the Joint Chiefs of Staff) are required to provide Congress with a quadrennial review of defense strategy, force structure, modernization and infrastructure plans, and budget plans. The first quadrennial defense review (QDR) of Secretary of Defense Rumsfeld was published within weeks of September 11, 2001: Secretary of Defense (Donald R. Rumsfeld). 2001. Report of the Quadrennial Defense Review, Department of Defense, Washington, D.C., September. |
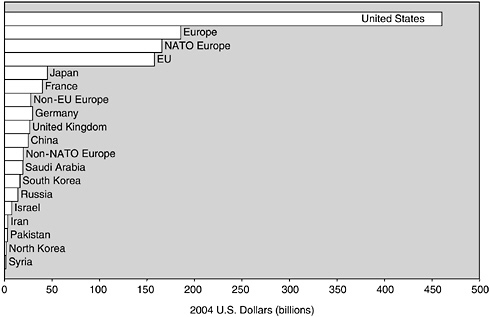
FIGURE 1.1 Defense spending of selected countries, 2004. NOTE: NATO, North Atlantic Treaty Organization; EU, European Union. SOURCE: Based on data from International Institute for Strategic Studies, 2004, The Military Balance 2004/2005, Taylor and Francis Group, London, pp. 261-331.
The United States is the first nation in the world to enjoy “command of the commons”—that is, command of the sea, the skies above 15,000 ft, and space.5 This command of the commons underpins the ability of the United States to project its power globally and to fight and win in regions far from home.
As important as it is to U.S. strength, however, command of the commons cannot guarantee that the U.S. military will win every fight or that the United States will prevail internationally in every instance.6 In the air below 15,000 ft, inexpensive surface-to-air missiles and even antiaircraft artillery can down sophisticated stealth airplanes. On the ground, the advantages proffered by command of the commons cannot ensure that U.S. forces will prevail in close-quarter infantry fights or that they can protect themselves and innocent civilians from
low-technology mortars and improvised explosive devices. In coastal waters, small boats filled with explosives, or underwater mines, or torpedoes from the least-expensive submarines can disable multibillion-dollar ships. When the first large-scale cyberwar is fought, it will provide significant insights into the future role that global networks will play in supporting the United States under such challenging conditions.
1.1.1 Understanding the Threats and Risks
The United States faces a wide array of strategic challenges, including international terrorism; the proliferation of missile technology and of chemical, biological, and nuclear weapons; cyberattacks; the threats posed by dangerous technologies in the hands of rogue states; regional conflicts; state failures; and war among the great powers.7 Some of these threats seem more likely than others to be acted on, and some pose a greater challenge to U.S. security than others do. Figure 1.2 organizes in a four-quadrant chart the types of challenges that the nation faces, showing the threats that appear more likely in the top half of the chart and those that would attack the areas of greatest vulnerability on the right-hand side.8
The most likely risks are those related to the global war on terrorism (see the upper half of Figure 1.3), namely, catastrophic and irregular threats. Catastrophic threats, including attacks on populations or on critical nodes of government, commerce, finance, or infrastructure by rogue states or non-state terrorists, pose risks that are both likely and exceptionally difficult to overcome. The most dangerous catastrophic threats are posed by weapons of mass destruction, including nuclear, chemical, and biological weapons, in the hands of extremists.9 Still likely but less challenging are irregular threats, including terrorism, support to insurgencies, and coercion by third powers.
Less likely are the challenges related to major combat operations (see Figure 1.3). Disruptive threats are less likely than are catastrophic threats, but the dan-
|
7 |
The United States continues to regard competition and even war among the great powers as a possible future risk and the potential rise of China as a possible future threat, but other threats are more immediate. See The White House (George W. Bush), 2002, The National Security Strategy of the United States of America, Washington, D.C., September, pp. 1-5, 26-28. |
|
8 |
Figures 1.2, 1.3, and 1.5 through 1.8 in this chapter are from the presentation “Time, Speed, and Strategy” originally made by the Deputy Chief of Naval Operations for Warfare Requirements and Programs (N6/N7) of the Office of the Chief of Naval Operations at the U.S. Navy Retired Four Star Flag Symposium held December 6, 2004, at the Washington Navy Yard, Washington, D.C. Admiral Archie Clemins, USN (Ret.) presented this information to the committee during its data-gathering meeting on January 11, 2005. |
|
9 |
The Bush administration’s National Security Strategy views weapons of mass destruction in the hands of radicals as the gravest danger that the nation now faces. The White House (George W. Bush). 2002. The National Security Strategy of the United States of America, Washington, D.C., September, p. 2. |
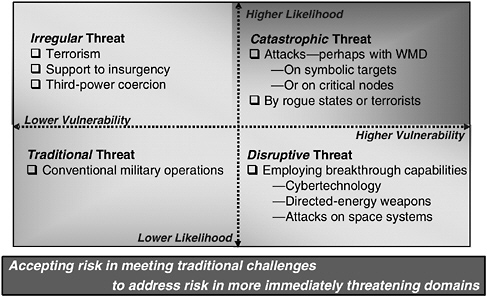
FIGURE 1.2 Types of persistent and emerging strategic challenges faced by the United States. NOTE: WMD, weapons of mass destruction. SOURCE: Adapted from Deputy Chief of Naval Operations for Warfare Requirements and Programs (N6/N7) of the Office of the Chief of Naval Operations, “Time, Speed, and Strategy,” presentation at the U.S. Navy Retired Four Star Flag Symposium, December 6, 2004, Washington Navy Yard, Washington, D.C.
gers that they pose could be just as great—including high-technology breakthroughs that would allow a rising state competitor to attack or disrupt U.S. or global information systems or counter U.S. advantages in space, as well as directed-energy weapons that could be brought to bear against civilian or military resources, as indicated in Figures 1.2 and 1.3. Finally, traditional threats—the conventional air, ground, and naval forces of great powers or rogue states—still represent an area of risk; in today’s world, however, they appear less likely than catastrophic or irregular threats and—for the one military force in the world that enjoys command of the commons—less challenging to overcome than catastrophic or disruptive threats would be.
Not every threat viewed as important to U.S. security has a military solution. The Bush administration’s National Security Strategy calls for using every instrument of state power—political and diplomatic means, law enforcement and domestic security measures, intelligence resources, and economic and financial measures, as well as military efforts, to deal with the threats of today and tomorrow.10
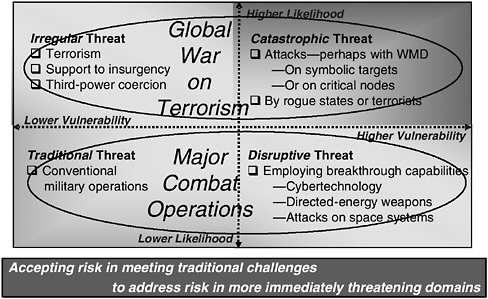
FIGURE 1.3 Persistent and emerging strategic challenges: risks related to the global war on terrorism and risks related to major combat operations. SOURCE: Adapted from Deputy Chief of Naval Operations for Warfare Requirements and Programs (N6/N7) of the Office of the Chief of Naval Operations, “Time, Speed, and Strategy,” presentation at the U.S. Navy Retired Four Star Flag Symposium, December 6, 2004, Washington Navy Yard, Washington, D.C.
1.1.2 New Military Missions
The history of the post–Cold War period indicates that the United States will continue to call on the military across a wide spectrum of operations. U.S. armed forces need to be configured and equipped to handle such activities. To meet the challenging national security environment, the United States has embraced new military objectives and undertaken missions that are vastly different from those of the Cold War.
For example, the Bush administration is unequivocal in the view that military force has a role to perform in countering the threat of terrorism.11 After September 11, 2001, the role of the U.S. military in homeland security also expanded significantly. For U.S. forces, operations aimed at regime change, pre-
ventive war, counterinsurgency, and urban warfare have grown in importance. Such missions are likely to continue growing in importance in the future.
Another significant change is the post–Cold War growth of multinational crisis management, peacekeeping, and stability operations. The U.S. military has participated in multinational peacekeeping operations, sometimes under United Nations auspices, for decades. Such operations expanded in size, scope, intensity, and regional import with interventions in Somalia and the Balkans during the 1990s.
1.1.3 U.S. Alliances and Multinational Operations
Threats and risks constitute one aspect of the U.S. national security environment. Alliances and international support for U.S. initiatives and military operations constitute another. The past decade saw dramatic shifts in U.S. alliances and international strategic relationships and also in the way that the United States looks to friends and allies for support.
For example, under U.S. leadership, the NATO alliance is reinventing itself, with 10 new member states, new partnerships, altered missions, nascent military capabilities and command structures, and ambitious plans for future forces and equipment. Once dedicated almost exclusively to deterring the prospect of large-scale war in Europe and defending the territory of the nations of Western Europe should deterrence fail, NATO now sees multinational crisis management and stability operations outside the boundaries of its member nations as crucial missions.12
In addition to championing change within NATO, the United States has entered bilateral and multilateral partnerships with most of the non-NATO states of Europe as well as with most nations in South and Central Asia—states that can and do provide intelligence, bases and overflight rights, and other resources needed in the fight against terrorism.
More fundamentally, the United States has changed the way that it operates with military partners and allies around the globe. Alliances of long standing are still valued for the advantages that accrue when political and military leaders can plan operations together in advance and armed forces can be equipped and trained together for future operations; nonetheless, the United States increasingly enters into wars and other military operations as a leader in “coalitions of the willing”—that is, more-impromptu and less-lasting coalitions that come together for a single operation and later disband. Operating in coalitions of the willing rather than in established alliances presents important challenges of its own for U.S. forces and for the command, control, communications, computers, intelligence, surveillance, and reconnaissance (C4ISR) structures that support them. These challenges are
|
12 |
NATO Press Release (2002)127. 2002. “Prague Summit Declaration,” issued by the heads of state and government participating in the meeting of the North Atlantic Council in Prague, November 21. Available at <http://www.nato.int/docu/pr/2002/p02-127e.htm>. Accessed March 2, 2005. |
discussed in the U.S. Air Force Scientific Advisory Board’s 2004 summer study, Networking to Enable Coalition Operations.13
1.1.4 The Antiaccess Challenge
New threats and shifting alliances are completely altering another aspect of the strategic environment for U.S. military forces: that of access to established military bases and other infrastructure. The proliferation of missile technology and weapons of mass destruction poses a danger for established ports, military bases, and lines of communication. At the same time, as demonstrated by the Turkish decision not to allow U.S. forces to operate from Turkey in the spring of 2003, shifting alliance politics can mean that the military bases, overflight rights, and other benefits on which the U.S. military once counted may not be available when needed.
In the future, the U.S. military will have to operate under the assumption that access to key locations, bases, and infrastructure may be denied, either through military attacks or for political reasons. The antiaccess challenge has significant implications for future naval forces and concepts of operations, as discussed in Section 1.2, “Technological Environment.”
1.1.5 Recalibrating the Major-Theater-War Measuring Stick
Reflecting the national security environment current at this writing, the DOD is developing a new yardstick by which to measure the size of the forces that the United States requires. At the beginning of this study, a force-sizing principle that goes by the rubric “1-4-2-1” replaced the “two-major-theater-war” sizing principle of the 1990s. The latter demanded that U.S. forces be sized to repel attackers in two major-theater wars nearly simultaneously and then, if necessary, to press counteroffensives and possibly occupy the capitals of both attackers. The 1-4-2-1 principle calls instead for forces sufficient to defend the United States (that is, to protect one homeland), to deter aggression and coercion in four critical regions of the world, to act quickly to defeat attacks against U.S. allies and friends in two theaters of operation in overlapping time frames, and to “win decisively”—that is, to go on the counteroffensive, drive the enemy attacker back home, and occupy the enemy’s capital or set the conditions for regime change if necessary in a single war.14 The new measuring stick translates into challenging
demands on all U.S. forces. As of late 2005, the DOD appears to be modifying its policy anew, but whatever the specifics, DOD’s policies for the indefinite future are certain to involve achieving multiple, simultaneous objectives in widely dispersed theaters.
1.1.6 Critical Time Lines
In addition to the challenging yardstick of 1-4-2-1, the DOD established in mid-2004 stringent demands for the speed with which U.S. armed forces should be able to prepare for, deploy to, and conduct military operations in the future.15 The goal of this stringent time line, which goes by the name “10-30-30,” is to shift from a situation in which it can take months to ready U.S. forces and deploy them into theater, to one in which forces are positioned and ready to deploy to a hot spot and seize the initiative within 10 days, swiftly defeat the adversary within 30 days, and are ready to fight again in 30 days. Meeting the demanding 10-30-30 goal will require heavy reliance on maritime forces, maintenance of forward-deployed forces, and sea basing. Again, the committee anticipates that in time the specifics of DOD’s time line goals will change, but the requirement for rapid reaction will endure.
1.1.7 Capabilities-Based Planning
Making decisions about the size, shape, equipment, infrastructure, and people of tomorrow’s armed forces requires thoughtful planning today. During the Cold War, military force planners in the armed services and the DOD routinely assessed the ability of U.S. forces to meet deployment time lines, conduct operations, and prevail in a limited number of set-piece scenarios based on national perceptions of the threat. Following the end of the Vietnam War in the early 1970s, such planning focused largely on the potential threat from the Soviet Union and Warsaw Pact nations.
In contrast, current DOD policy calls for a “capabilities-based” approach to defense planning. The capabilities-based approach follows from the idea that the United States cannot be confident of knowing in advance who the future enemy might be. Thus, rather than planning for future U.S. forces based on one or a few relatively well understood threats, the department should strive to anticipate a range of capabilities that adversaries might employ and develop a broad portfolio of military capabilities to counter them.16
Unfortunately, while capabilities-based planning is easy to describe, it can be difficult to realize. Even reaching agreement among planners about what constitutes genuine capabilities-based planning can be complex.17 Briefings provided to the committee by analysts and officials from the naval and joint communities suggest that the DOD and the Naval Services are converging on an approach that relies on assessments of U.S. capabilities in some two dozen carefully defined scenarios that together cover the spectrum of potential strategic challenges arrayed in Figure 1.3. The committee notes, however, that while the Office of the Chief of Naval Operations (OPNAV) staff has adopted a capabilities-based approach to planning and is working to assess naval capabilities in a variety of scenarios, the organizational structure of the naval acquisition community is not well matched to the capabilities-based approach.
1.2 THE TECHNOLOGICAL ENVIRONMENT
1.2.1 Observations on the Evolution of Military Communications and Information Technology
A brief recap of the evolution of military communications and information technology in the Navy and Marine Corps will provide a context for the dramatic changes that are occurring. The recap is not intended to be comprehensive, but rather to illustrate how far the Naval Services have recently come and how far they have yet to travel. Chapter 6, “Communications,” surveys today’s communications systems in more detail.
Over the past 50 years, the Navy’s communications have evolved from primarily high-frequency (HF) and very low frequency (VLF) communications through low-frequency (LF) communications supporting nuclear-powered ballistic missile submarines (SSBNs) on patrol, and ultrahigh-frequency (UHF) and very high frequency (VHF) communications supporting tactical operations and airplane communications. Ionospheric conditions could make long-distance HF communications difficult, and sometimes it took innumerable transmissions to get a single message through. As communications evolved, cryptographic equipment also evolved, to protect the information riding on the point-to-point circuits. Even into the early 1970s, manual Morse communications were still in use by some Navy platforms. Communications from a ship at sea were sent to a Navy communications station (NAVCOMSTA) ashore using point-to-point circuits, while NAVCOMSTAs operated in a broadcast mode to deliver communications to ships at sea. Most of the ship-to-shore communication was done at 75 baud, the
limitation of the teletype machine, which had no memory. VLF and LF communications had even more limited data rates.
Satellite communications were introduced in the late 1970s, along with teletype machines that by then had a memory capability enabling an entire broadcast to be received and printed in a fraction of the time needed before. The early satellite capabilities operated in the UHF spectrum in both voice and data modes and were able to transmit and receive data at 300 bits per second (bps).18 While this was a considerable step up from previous capabilities, as late as 1990 a Navy ship could not make a voice telephone call to shore. The first International Maritime Satellite (Inmarsat) terminals were installed on Navy ships in 1990 and were used for voice communications only.
By 1994, ships had been outfitted with Inmarsat antennas that could be used for both voice and data using single or multiple 64 kilohertz (kHz) channels. This is still the principal communication means for smaller surface combatants today. However, by 1996, larger ships with 4 ft or 7 ft antennas (carriers, large-deck amphibious ships, and command ships) were able to get a T1 capability (1.5 megabits per second [Mbps]) using C-band and the superhigh frequency (SHF) spectrum. From 1996 through 2000, the Navy IT-21 (Information Technology-21) program effectively gave all deploying ships bandwidth (BW), together with computers and networks, enabling Internet Protocol (IP) communications throughout the fleet. This, in fact, revolutionized communications and processes, even allowing chat to replace voice as the primary means of tactical communications, while intranet communications, including e-mail and Web-enabled applications, provided the preferred means for operational communications, replacing naval messages. With the advent of the Global Broadcast System operating in the extremely high frequency (EHF) spectrum, with its broad-area coverage and spot-beam coverage, up to 20 Mbps can be received by even the smallest ship if it is outfitted with the appropriate antenna and terminal. Yet even in this environment BW continues to be inadequate, as evidenced by lessons learned from Operation Iraqi Freedom.19 Currently, government satellites and commercial satellites are power-limited as opposed to BW-limited and are used in the dedicated circuit/user mode. Consequently, many small ships are disadvantaged users and must time-share a UHF satellite channel. When they have satellite coverage they are limited to 64 kbps, divided as shown in Figure 1.4—clearly a long way from what one would consider real network-centric communications.
For naval forces ashore, the Navy/Marine Corps Intranet (NMCI) is now in its fourth year of implementation. This is the first government outsourced enterprise intranet; under this arrangement the Navy and Marine Corps are buying
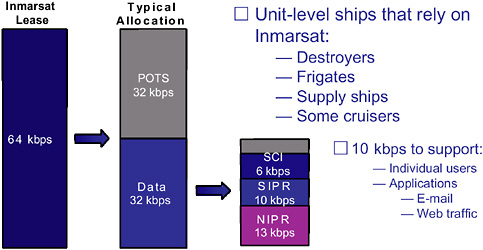
FIGURE 1.4 Inmarsat capacity and capacity allocation to ships at sea. NOTE: Inmarsat, International Maritime Satellite; POTS, plain old telephone service; kbps, kilobits per second; SCI, sensitive compartmented information; SIPR, Secure Internet Protocol Router; NIPR, Non-Secure Internet Protocol Router. SOURCE: Sunoy Banerjee and John Bentrup. 2003. “Understanding Operational Collaboration in the Fleet,” presentation, Center for Naval Analyses, Alexandria, Va., September 10.
their information technology (IT) as a service rather than as a commodity. The commercial contractor must meet Service Level Agreements (for example, delivered capacity, reliability, latency). While there have been delays and obstacles in implementing NMCI, there has also been progress. In 2000 there was no Enterprise Network, many users were still using computers based on Intel 286 chips and running disk operating system (DOS), and many local area networks had no firewalls. Working through the issues has been slower than anticipated, but the NMCI has withstood numerous attacks and viruses during this period.
The Marine Corps communications architecture has focused on operational and tactical communications. This process has been very slow for several reasons, including a lack of discipline in the requirements process, no clear vision, a general lack of involvement by senior leadership, and, until recently, a general lack of funding. In tactical communications the Marine Corps generally followed the Army’s lead in a variety of procurement programs—for example, the Single-Channel Ground-Air Radio System (SINCGARS) and the Enhanced Position Location and Reporting System (EPLRS). During Desert Storm, the Marine Corps had no capability to pass data over its tactical internet (SINCGARS), although the service did patch together a digital capability using commercial systems that flowed north into Kuwait with some elements of the First Marine Expeditionary Force. This proved to be a very immature version of reach-back, in that the Marines were able to request administrative and logistical information using
commercial personal computers strapped inside of vehicles as the attack moved north. The information was passed over this system utilizing commercial UHF satellite communications back to the United States.
At about this time, the Marines were in the process of developing the first systems that would offer digital displays as well as the ability to pass some imagery. Both the Intelligence Analysis System (IAS) and Maneuver Control Systems (Operations) were gradually fielded over the next 10 years. The first deployment of an immature version of IAS went to sea with the 15th Marine Expeditionary Unit (Special Operations Capable) (MEU[SOC]) for the initial operations in Somalia in 1992. This occurred after a deal was struck with the Navy to take Marine TSC-85 and TSC-93 equipment to establish an SHF capability onboard the amphibious assault ship (LPH) that would support the IAS system.
In the early 1990s, the Marine Corps continued with SINCGARS and did not follow the Army in developing the digital capability that existed within that system. It later procured EPLRS in order to provide a digital capability, especially for the artillery; however, it was another 3 to 5 years before any reasonable capability was fielded. In the mid- to late 1990s, a series of experiments was conducted that eventually led to some small tactical satellite systems (PSC-5) that were deployed with the MEU(SOC) units. These are still in the system today.
Several other experiments were conducted that tested a variety of digital systems, most of which went no farther. The one real success story that came out of the experimentation process was the evolution to the Personal Role Radio (PRR), which was the first real Marine-to-Marine communications system that was mounted in the individual helmet with both earphones and a “boom mike” attached to a small receiver on the battle harness. The PRR has been used by Marines in Operation Iraqi Freedom (OIF) with a great deal of success. All other systems, including those for long-range communications, are “old and tired.” Much effort has been put into the Marine Corps’s command-and-control personal computer (C2PC) application that is in some of the Corps’s tactical systems. This worked well at the brigade level and below in the attack across Iraq during OIF. The Army’s version of this device is the Force XXI Battle Command, Brigade-and-Below (FBCB2), and, as expected in separately developed applications, there were interoperability issues with this equipment in OIF. What has come out of the lessons learned is that the Services (Army and Marine Corps) will use C2PC at the levels above brigade, and they will use FBCB2 at all levels below brigade.
Like the other Services, the Marine Corps awaits the Joint Tactical Radio System (JTRS), for which reason no major tactical communications upgrades have been attempted within the acquisition system. Based on the favorable experiences of Special Operations Forces in OIF, the PRC-119 Multiband Inter/Intra-Team Radio has been much sought after. The Marine Corps now has a requirement for some 5,000 of these, and some have been procured. The Marines have used Iridium satellite communications capability with excellent results in both Operation Enduring Freedom and Operation Iraqi Freedom. Currently they have
plans to use this capability for as long as it is available. They would also like to have a similar system available when Iridium capability expires.
At the regiment level and above during OIF, the Marine Corps was able to use EHF (high-data-rate) capability in its mobile command centers. With the fielding of NMCI throughout the Marine Corps, a capable enterprise network is being put into place to support logistics and nontactical operations.
1.2.2 Observations on the Evolution of Military Intelligence, Surveillance, and Reconnaissance
As with the previous subsection, these observations are not intended to be comprehensive, but technologies related to intelligence, surveillance, and reconnaissance (ISR) have also undergone dramatic change in recent decades. Chapter 7, “Intelligence, Surveillance, and Reconnaissance,” and Appendix D, “Some Key ISR Assets, Current and Planned,” survey today’s ISR systems in greater detail. Today’s sophisticated ISR technologies are a far cry from the rudimentary cameras mounted on airplanes or the early radars of World War II. They support the worldwide collection and processing of images and signals from every element of the global commons: space, air, sea (both surface and underwater), and cyberspace.
Technologies for imagery intelligence have advanced dramatically. During the 1950s, the state of the art in imagery intelligence consisted of photographic cameras mounted on U-2 aircraft. With the space age came the National Reconnaissance Office and satellite-based photography. The science of stereophotogrammetry developed to enable precision geolocation of targets and accurate mapping of terrain. The Vietnam War saw the introduction of infrared imaging at night. In the 1970s and 1980s, multispectral imaging, which produces views using measurements of light energy from several wavelength bands from the visible and infrared spectrum, brought improvements in target recognition and introduced a new ability to counter adversaries’ attempts to conceal targets through camouflage or other cover. In the future, hyperspectral imaging, which collects measurements in tens or hundreds of spectral bands, promises further improvements in feature identification and assets to counter concealment efforts. New sensing technologies bring new requirements for data storage, transmission, and processing, thus increasing the importance of decisions about how much information can and should be processed onboard the sensors and how much must be transmitted to platforms or central facilities for processing.
Radar technology has also advanced substantially. Beginning with the magnetron developed during World War II, transmitter technology evolved to traveling-wave tubes during the 1960s and to active transmitting and receiving modules in the 1990s. The evolution to multiple radar frequency bands in the 1990s allowed greatly improved information retrieval. Synthetic aperture radars, which made their debut on reconnaissance aircraft during the 1970s and 1980s and are
now widespread on reconnaissance and surveillance aircraft and spacecraft, allow for day-or-night and all-weather imaging. Radar resolution, once measured in tens of meters, is now often measured in inches.
A major contribution to ISR was the linking of atomic clocks and satellites into the Global Positioning System (GPS). This development afforded new levels of accuracy in location, time, and time interval.
Since the early 1990s, airborne radars have been used operationally for an additional purpose: that of detecting the movement of objects on the ground. The ground moving target indicator (GMTI) onboard the Joint Surveillance Target Attack Radar System (JSTARS) detected the movement of adversary forces during Operation Desert Storm in 1991, with significant strategic and tactical impact. Continued improvements in GMTI technology make broad-area surveillance from space-based radar systems a future possibility.
Signals intelligence and communications intelligence have benefited greatly in recent decades from the same rapid advances in microelectronics and miniaturization that have transformed the world of commercial electronics. From the bulky and relatively unsophisticated direction-finding and listening devices of World War II, U.S. forces have migrated to increasingly precise locators and detectors that are far lighter and more compact. Such sensor technologies create security vulnerabilities at the same time that they open new opportunities, however, thus increasing the relevance of secure communications and networks.
Underwater sensing has also experienced multiple technology breakthroughs. Early antisubmarine warfare efforts required ships to “ping” enemy submarines using powerful sonars that gave away the ships’ positions. The passive Sound Surveillance System array established on the ocean floor during the 1950s and 1960s greatly improved the Navy’s ability to track enemy submarines without revealing sensitive information. Later development of ship-mounted and -towed, phased-array sonar sensors brought further improvement in the ability to track submarines passively. However, the proliferation of technology for quieting submarines in recent decades has rendered much of the nation’s older undersea surveillance capability obsolete.
1.2.3 Migration of Commercial Technology to the Department of Defense
The DOD has embarked on a joint enterprise roadmap to enable full network-centric capabilities. DOD’s centerpiece for network-centric capabilities is the Global Information Grid (GIG). The GIG is described in Chapter 3, “Architecting and Building the Naval C4ISR System,” as having seven primary enabling components:
-
GIG Bandwidth Expansion,
-
JTRS,
-
Transformational Satellite (TSAT),
-
Network Centric Enterprise Services (NCES),
-
An all-IPv6 (Internet Protocol, version 6)-based environment with High Assurance Internet Protocol Encryption (HAIPE),
-
Teleport gateways from satellite to landline, and
-
Joint Network Management System.
These seven items together establish a joint service-oriented architecture (SOA) with a ubiquitous secure high-bandwidth enterprise network that is all IP-based. It is left to the individual Services to ensure that their acquisition priorities will meld seamlessly into the GIG in a nonduplicative manner, while also having the ability to interoperate with coalition partners.
To many, the challenges described above appear Herculean, but more technological advances are likely to occur in the next 5 years than have occurred in the preceding 15 years (from the time when the World Wide Web was invented). Most of these advances, on which the DOD will have to capitalize, will come from the commercial sector, presenting a difficult challenge for the current procurement process. To view some of the expected technological implications, one only has to look as far as the Gartner Group’s “Top Predictions for 2005 and Beyond”:20
-
Microcommerce opportunities for new products and services less than $5 will generate $30 billion revenue per year by 2010.
-
By 2015, collective intelligence (collaboration) breakthroughs will drive a 10 percent productivity increase.
-
The rate of Cyberattacks against software flaws will double by 2006.
-
By 2008, the technological differences between PCs, mobile devices, e-books, televisions, and cellular phones will be eradicated.
-
By 2009, counterfeit reality will account for at least one major media and political scandal.
-
By 2015, 40 percent of today’s IT job roles will be lost to automation.
Considering the future in these terms, for the DOD and the Naval Services, the choices are lead, follow, or get out of the way. The status quo is not an option!
1.3 NAVAL OPERATIONS
1.3.1 Naval Operational Requirements
The 1-4-2-1 and 10-30-30 strategies will stress the naval forces’ ability to maintain sufficient presence to deter hostilities and to respond quickly and forcefully when deterrence fails. The challenges and operational requirements for naval forces in the 21st century have changed and will continue to change, but they will continue to focus on two strategic imperatives—the Global War on Terrorism (GWOT) and Major Combat Operations (MCO). These two strategic imperatives necessitate naval forces with attributes of speed, access, and persistence. To achieve the strategic objectives, naval forces will be required to secure access and provide for an active forward defense. The Naval Services will rely on their ability to operate from the commons (sea, cyberspace, and space) and to conduct network-centric operations. Operational risk in land attacks will be minimized by maintaining early-entry capabilities forward for rapid action and relying on surge capacity for follow-on forces.
Strategies change and evolve. However, the requirements and strategic imperatives of GWOT and MCO are expected to remain the focus of naval forces for the next two decades and beyond. In satisfying naval operational requirements, there are certain facts of life that can present either a limitation or an opportunity. One of these is the budget. Historically the Ship Construction Navy (SCN) budget has been $10 billion per year plus inflation, and the Aircraft Procurement Navy (APN) budget has been $9 billion per year plus inflation.21 These budget numbers, which are not expected to change, will support about a 250-ship Navy. Therefore, the challenge for naval forces is to achieve the maximum capability in existing ships and airplanes, to purchase the most effective new ships and airplanes, and to have a concept of operations and operational availability that achieves the strategic objectives. Additionally, the pressure to reduce manpower (addressed by the Chief of Naval Operations [CNO]) in numerous speeches and public appearances) in order to be able to afford the necessary number of ships, submarines, and aircraft dictates that manpower-reduction technologies be incorporated in the three platform designs, as well as processes.22
1.3.2 Naval Strike Groups
The CNO and the Commandant of the Marine Corps (CMC) recently put forth new organizational constructs as key components of the global integrated naval force necessary to meet the forward-deterrence and rapid-response requirements of the defense strategy. In the near term, carrier strike groups (CSGs) will remain the core of the Navy’s warfighting capability. CSGs will generally consist of an aircraft carrier, a cruiser (CG), two guided-missile destroyers (DDGs), a nuclear-powered attack submarine (SSN), and a fast combat-support ship (T-AOE). Compared with today’s carrier battle group (CVBG), the CSG will have fewer surface combatants and submarines, although it is intended that the CSG continue in the role of providing air defense capabilities for shore- and sea-based joint and coalition forces, as well as strike capabilities, including Time Critical Strike (TCS) capabilities against land and sea targets.
Expeditionary strike groups (ESGs), which are the major new element of this organizational construct, will consist of a standard three-ship amphibious ready group (ARG) augmented with a CG, two DDGs, an SSN, and a future generation of destroyer. The ESG is thus intended to be able to defend itself against air, surface, and subsurface threats; provide a long-range strike capability with Tomahawk missiles; and provide naval surface fire support to its embarked Marine Expeditionary Unit (MEU).
Strike and missile defense surface action groups (SAGs) will be capable of operating independently or with CSGs or ESGs. In the near term, three Tomahawk land-attack missile (TLAM)-equipped SAGs will be established to provide additional independent strike capability, although it is envisioned that this capability will evolve to provide the foundation for a sea-based, mobile ballistic missile defense capability for joint and allied forces ashore.
While the CSGs, SAGs, and ESGs bring their unique and somewhat overlapping capabilities to the GWOT and MCO, the CNO’s and CMC’s future task force of choice will be the expeditionary strike force (ESF), consisting of a combination of CSGs, SAGs, ESGs, combat logistics force ships, and the maritime prepositioning force of the future (MPF[F]). The ESF’s future capabilities will be enhanced by the introduction of the V-22 aircraft, Joint Strike Fighter, advanced E-2D Hawkeye, CVN-21 aircraft carrier, DDX (next-generation, multimission destroyer), CGX (next-generation, guided missile cruiser), LCS (littoral combat ship), Virginia-class SSN and SSGN (nuclear-powered, guided-missile submarines). The MPF(F) ships will form the core of the sea base within the ESF and will support the arrival, employment, and sustainment of a Marine Expeditionary Brigade (MEB) in power-projection missions. This is the fundamental basis for the Sea Basing pillar of the Navy’s capstone concept Sea Power 21. Figures 1.5 through 1.8 reflect the Sea Basing vision and implementation, showing its dependence on speed, access, and persistence and on network-centric operations.
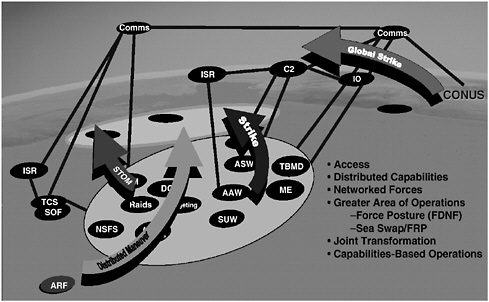
FIGURE 1.5 Sea Basing vision principles of capabilities-based speed, access, and persistence. NOTE: Comms, communications; C2, command and control; IO, Information Operations; ISR, intelligence, surveillance, and reconnaissance; TCS, Time Critical Strike; SOF, Special Operations Forces; ARF, amphibious ready force; NSFS, Naval Surface Fire Support; STOM, Ship-to-Objective Maneuver; SUW, surface warfare; AAW, antiair warfare; ASW, antisubmarine warfare; TBMD, Theater Ballistic Missile Defense; ME, Maneuver Enhancement (Brigade); FRP, Fleet Response Plan; FDNF, Forward Deployed Naval Forces; CONUS, continental United States. SOURCE: Adapted from Deputy Chief of Naval Operations for Warfare Requirements and Programs (N6/N7) of the Office of the Chief of Naval Operations, “Time, Speed, and Strategy,” presentation at the U.S. Navy Retired Four Star Flag Symposium, December 6, 2004, Washington Navy Yard, Washington, D.C.
The need for ESGs, SAGs, and CSGs, and the MPF(F)s to operate independently and to combine to form ESFs will increase the need for flexible, adaptable C4ISR systems. This need will be further increased by the Fleet Response Plan,23 which is reducing the time available for integrating the C4ISR systems and training the people of the various maritime groups.
The Navy’s premise in creating the new naval strike groups was that the new ESG would be more capable of defending itself than the standard ARG was, and therefore the ESG could be sent more readily into harm’s way and employed to
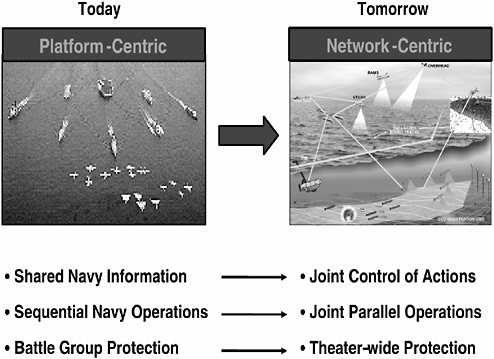
FIGURE 1.6 Joint global concept of operations—Sea Basing vision: interdependent networked joint operations. SOURCE: Adapted from Deputy Chief of Naval Operations for Warfare Requirements and Programs (N6/N7) of the Office of the Chief of Naval Operations, “Time, Speed, and Strategy,” presentation at the U.S. Navy Retired Four Star Flag Symposium, December 6, 2004, Washington Navy Yard, Washington, D.C.
distribute naval forces around the world. While future aircraft will add considerably to the ESG’s capabilities, the ESG will remain clearly less capable in airpower than the CSG is, owing to inherent differences that are reflected in aircraft sortie rate, aircraft operational range, organic surveillance, organic electronic warfare, and other capabilities. However, many key C4ISR shortfalls are similar with respect to the ESG and CSG, and their resolution may involve reach-back, other ships such as the DDG or LCS that will accompany both groups, and off-board, networked sensor systems. That is, solutions to current C4ISR shortfalls may benefit both the ESG and the CSG, as discussed further in Chapter 2, “Principal Naval Missions and C4ISR Impact,” and Chapter 7, “Intelligence, Surveillance, and Reconnaissance.”
The committee has not seen an articulation of the degree of hostile environment into which the ESG may be sent. The committee believes, however, that if the nation’s military will be called on to provide forward deterrence and rapid

FIGURE 1.7 Sea Basing with Maritime Prepositioning Force (Future) MPF[F]): accelerate access … rapidly deployable surge. NOTE: MPSRON, Maritime Prepositioning Ship Squadron. SOURCE: Adapted from Deputy Chief of Naval Operations for Warfare Requirements and Programs (N6/N7) of the Office of the Chief of Naval Operations, “Time, Speed, and Strategy,” presentation at the U.S. Navy Retired Four Star Flag Symposium, December 6, 2004, Washington Navy Yard, Washington, D.C.
response in simultaneous conflicts in widespread theaters and those conflicts fall short of the major combat operations that are the primary focus of this study, then the new force construct and the ESG are concepts worth considering.
The composition of naval strike groups will vary and evolve in response to surrounding operational and technological developments. It will continue to be difficult to predict the nature and location of conflict, and commanders will often find it necessary to respond with forces that are not optimized for the particular crisis at hand. It seems to the committee, therefore, that it would be more beneficial to create a C4ISR architecture that can serve any given force package at hand, rather than specific packages that the Navy may be planning, at any one moment, to deploy. This has been the focus of the committee’s attention.
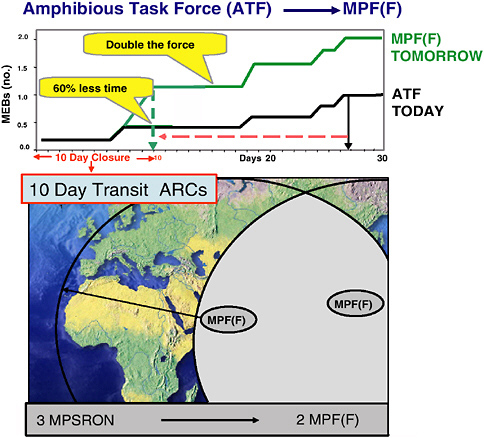
FIGURE 1.8 Joint global concept of operations—capabilities and forces: accelerate access … rapidly deployable surge. NOTE: MPF(F), Maritime Prepositioning Force (Future); ARC, Amphibious Reconnaissance Course; MPSRON, Maritime Prepositioning Ship Squadron. SOURCE: Adapted from Deputy Chief of Naval Operations for Warfare Requirements and Programs (N6/N7) of the Office of the Chief of Naval Operations, “Time, Speed, and Strategy,” presentation at the U.S. Navy Retired Four Star Flag Symposium, December 6, 2004, Washington Navy Yard, Washington, D.C.
1.3.3 Network-Centric Operations, FORCEnet, and Sea Power 21
The DOD and its naval forces have embraced network-centric operations as a vision of its future. The report entitled Network-Centric Naval Forces: A Transition Strategy for Enhancing Operational Capabilities, by the National Research Council’s Naval Studies Board (NSB), defined network-centric operations as follows:
[Network-centric operations are] military operations that exploit state-of-the-art information and networking technology to integrate widely dispersed human
decision makers, situational and targeting sensors, and forces and weapons into a highly adaptive, comprehensive system to achieve unprecedented mission effectiveness.24
FORCEnet is the Navy’s approach for enhancing its capability to perform network-centric operations. The Navy defines it as follows:
[FORCEnet is] the operational construct and architectural framework for Naval warfare in the Information Age which integrates warriors, sensors, networks, command and control, platforms and weapons into a networked, distributed combat force, scalable across the spectrum of conflict from seabed to space and sea to land.25
A recently published NSB study, FORCEnet Implementation Strategy, points out that this definition implies three components:
-
The doctrine, tactics, techniques, and procedures for conducting network-centric operations, and warriors trained in those concepts;
-
Materiel developed and acquired in accordance with an architectural framework that enables these operations; and
-
An information infrastructure that integrates the warriors and materiel in the conduct of these operations.26
That report and the present study refer to the third component listed above as the FORCEnet Information Infrastructure (FnII).
The Navy articulates its vision of the future in the concept of Sea Power 21, which has the three pillars of Sea Strike, Sea Shield, and Sea Basing, enabled by FORCEnet. Naval Power 21 and the Naval Operating Concept for Joint Operations, known informally as the NOC, are the overarching driving forces behind the Navy and Marine Corps acquisition priorities. This vision of the future is capabilities-focused, as opposed to being platform-focused. The importance of FORCEnet to the success of Sea Power 21 has continued to grow. The continuing emphasis on C4ISR and the work of the Committee on C4ISR for Future Naval Strike Groups only highlight the importance that FORCEnet plays in naval strike group capabilities.
1.4 FINDINGS AND RECOMMENDATIONS
Each of the following six chapters presents its own findings and recommendations. Four additional findings and recommendations, not included in Chapters 2 through 7, must be considered in order to implement actual network-centric operations and to enhance the ability of the Navy and Marine Corps to support the President’s policy of spreading democracy throughout the world and conducting the global war on terrorism as well as meeting the MCO requirements. Presented below, these findings and recommendations address the following issues:
-
Reach-back capability to information,
-
Human engineering,
-
Technology procurement, and
-
Coalition operations.
1.4.1 Reach-Back Capability to Information
Finding: The requirement for rapid deployment of U.S. forces to theaters in any region of the world, coupled with declining numbers of people in uniform, mean that U.S. naval forces will have to rely increasingly on reach-back to centralized facilities for support functions. Today, it can take months to assemble and move the equipment, infrastructure, and people that the naval forces need in order to conduct intelligence processing, target identification and weapon-target matching, mission planning, logistics support, and numerous other C4ISR functions in-theater. Conducting such functions onboard ships ties up scarce manpower and footprint. Many such functions could be carried out more quickly and effectively, and with fewer people and less space, if they were consolidated in centralized operations centers.
Recommendation: In developing command, control, communications, computers, intelligence, surveillance, and reconnaissance (C4ISR) architectures, the Naval Network Warfare Command and the Deputy Chief of Naval Operations for Warfare Requirements and Programs (N6/N7) should explore the trade-offs related to reach-back. Where possible, the Naval Services should capitalize on the opportunities afforded by the Global Information Grid and other elements of the Department of Defense’s evolving information infrastructure to shift a substantial share of mission planning, as well as other decision-making support functions, to centralized facilities. It is realized that the reach-back location cannot be chosen in the absence of other strategic objectives. Therefore, reach-back locations should be chosen to support U.S. globalization and democratization objectives and, at the same time, to support the building of scarce and perishable in-country expertise.
1.4.2 Human Engineering
Finding: With the pressure to reduce manpower, qualified uniformed people are going to be available in U.S. naval forces in limited numbers in future years. Therefore, the requirements for speed in deployment and operations mean that U.S. naval systems must be designed to enhance the productivity of the people who operate, maintain, and rely on them.
Recommendation: The Deputy Chief of Naval Operations for Warfare Requirements and Programs (N6/N7) should ensure that naval C4ISR systems are designed for ease of use and maintenance. Built-in, context-related “help” features in these systems should be transparent and easy to access. C4ISR facilities—whether in-theater, onboard ships, or in the continental United States—should be designed for the maximum productivity and effectiveness of those working in them. C4ISR user-system interfaces should be adaptable to the preferences of individual users or commanders. In the rapidly changing information technology areas, educational and informational programs should be made available, including broadly accessible distance-learning programs for deployed personnel and others.
1.4.3 Technology Procurement
Finding: The current procurement process of the Department of Defense concentrates on buying ships, airplanes, tanks, and so on. Most of these items have lives that are measured in decades, with few major upgrades over their lifetime. Information technology is changing on the time line articulated in Moore’s law27 and does not fit into such a process. Similarly, the extent of the experience of government and DOD personnel with IT procurement is limited at best. Goldwater-Nichols28 instituted organizational governance of procurement that needs to be reexamined and changed appropriately on the basis of IT procurement and upgrading requirements. Succinctly stated, real capabilities of the Navy and Marine Corps are going to be relatively more and more dependent on IT and technology insertion than on the procurement of new platforms, vehicles, and weapons. Metcalf’s law29 will be the deciding factor.
The Naval Services will need to use commercial technology as much as possible in future C4ISR systems. This necessity has its challenges. Affordability demands that the Services leverage current and future industrial capacity, with its rapid rate of change, but security, availability, and reliability require the Navy to learn to make up for commercial deficiencies without subsidizing its own costly manufacturing base, as has occurred in shipbuilding.
Recommendation: The Chief of Naval Operations and the Secretary of the Navy should examine Goldwater-Nichols30 in the context of how it should be updated so as to put the most suitable organization for the governance of procurement in place to govern, procure, and upgrade technology in the joint force environment effectively and efficiently. The challenge of accomplishing this task is greater than the challenge that ADM Hyman G. Rickover had in developing the first nuclear submarine or that RADM Wayne E. Meyer had in developing the Aegis weapons system.
1.4.4 Coalition Operations
Finding: The United States operates with coalition forces in major combat operations and in the global war on terror. With few exceptions, U.S. technology development has far surpassed that of other countries, and that gap will continue to grow both in investment and in research and development. Conversely, there is a requirement to be interoperable, where appropriate, with coalition forces in the majority of potential conflicts in the future. While some progress was achieved in OIF regarding the Secure Internet Protocol Router Network (SIPRnet), as well as the exchange of communications equipment with certain members of the coalition, there is a continuing problem with required capabilities as well as air gaps between the established local area network servers such as CENTRIX (Combined Enterprise Regional Information Exchange).
Recommendation: The Naval Network Warfare Command should move aggressively to ensure that the Navy and Marine Corps establish programs with U.S. coalition partners to improve information sharing. In addition, work should be done to expand the ability to secure and ensure information used with coalitions across the full range of communications used by U.S. and coalition forces.


























