6
Creating a More Secure and Resilient Power System
The electric grid is regularly impacted by natural events and accidents, and faces ongoing threats from intentional and unintentional physical and cyber incidents. This chapter first reviews the substantial risks to electric power system resilience from natural events, accidents, and physical attacks, and then focuses on the significant cybersecurity challenges facing power systems. The modern grid is increasingly dependent on information and communications technologies (ICTs) to enable a more safe and secure, clean and sustainable, affordable and equitable, and reliable and resilient grid. However, the more the grid uses digital communication technologies, the greater the risk of cyberattacks. This chapter summarizes the current state of cybersecurity of the electric power system and describes a vision for the future of grid cyber resilience. To be successful, enhancing resiliency will require holistic attention to people, process and technology solutions. Cybersecurity challenges and recommendations to improve the grid’s resiliency, particularly to cyber threats, are the primary focus of this chapter.
THE CHALLENGES
Grid Reliability and Resilience
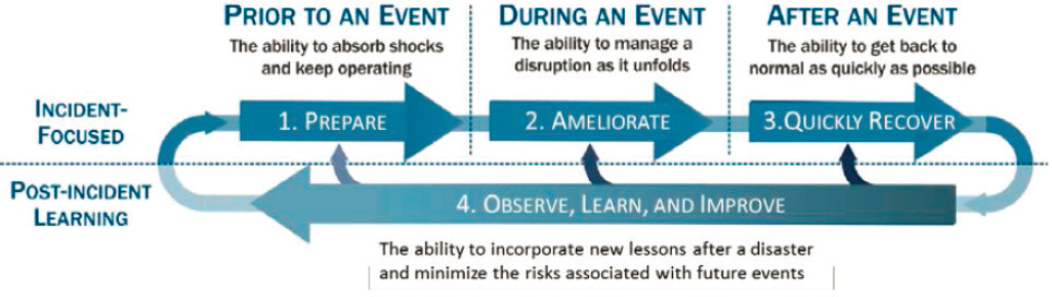
Reliability, availability, and resilience are related but different concepts. Reliability and availability describe the ability of the grid to deliver electricity, and can be measured with a number of standard metrics. Resilience is a relatively newer concept in energy and is broader, integrating four stages: (1) preparations undertaken in advance to make the system as tolerant as possible to possible future stresses or attacks; (2) the strategies (typically preplanned) and resources to manage and lessen the consequences of a stress or an attack once it has occurred; (3) mechanisms for recovering as quickly as possible once the stress or attack has occurred; and, (4) insights and lessons that can be inferred (through all stages of the process) so that if and when another similar stress or attack occurs, a better job can be done at all stages. This is illustrated in Figure 6.1.
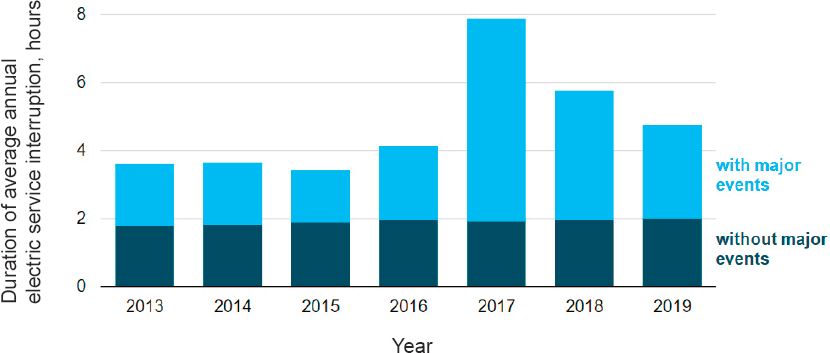
Standard metrics for grid reliability and availability were developed using a rich history of data on past service performance and outages tracked by utilities and regulators and reported nationally by the Energy Information Administration (EIA). For example, Figure 6.2 illustrates one standard measure of grid availability, the System Average Interruption Duration Index (SAIDI) for U.S. electricity customers. It indicates both routine outages that last a few minutes to a few hours, as well as more major outage events, and is primarily related to the distribution system. In contrast, standard metrics for quantifying resilience have not been established for generation, transmission, or distribution. Industry has been making investments in hardware, software, operations and planning that are expected to improve the resilience of the transmission and distribution systems, but currently there are no simple statistical methods to assess how these investments individually or collectively contribute to improved resilience. Developing useful metrics for resilience will require improved simulation tools that capture both the cyber and physical aspects of power grid behavior.
Hazards and Threats to the Grid
The integrity of the grid has been and will continue to be compromised by a variety of stresses and attacks—that is, hazards—including natural events, accidents, and malicious actions. (See Table 6.1.) Two earlier reports from the National Academies, Terrorism and the Electric Power Delivery System (NRC, 2012) and the 2017 report Enhancing the Resilience of the Nation’s Electricity System (NASEM, 2017), focused heavily on the reliability, physical security, and resilience of the electricity system. Box 6.1 summarizes the recommendations from these reports.1
Historically weather-related events, such as hurricanes and ice storms, are the leading source of large-scale grid disruptions in the United States. However, concerns about intentional acts of an adversary against the grid have risen sharply—amplified by salient events (e.g., successful cyber-attacks on the Ukrainian distribution grid in 2015 and a Ukrainan transmission substation in 2016, a physical attack on a U.S. electric distribution substation in 2013) and clarion reports (e.g., Coats, 2019; Cyberspace Solarium Commission, 2020; DSB, 2017; National Commission on Grid Resilience, 2020).
A prominent effect of climate change will be increased severity and/or frequency of extreme weather. These effects will pose a serious challenge to electric system security and reliability. When it comes to natural disasters the industry has a long and strong history of providing mutual assistance capabilities to impacted regions to speed restoration. Line crews are regularly dispatched from unaffected utilities to provide extra manpower and repair
___________________
1 The National Academies reports Enhancing the Resilience of the Nation’s Electricity System (2017), Analytic Research Foundations for the Next-Generation Electric Grid (2016), and Terrorism and the Electric Power Delivery System (2012) are available for download free of charge.
capabilities that accelerate disaster responses. Mutual assistance and preparedness tactics have also been successfully extended to critical equipment; for example, the industry has increased its reserve inventories of high-voltage transformers.
While there has been some progress on improving the physical security of the grid, the system will continue to be vulnerable to physical attacks. Threats of sabotage, vandalism, and theft have been associated with the electric power industry since its inception. The use of fencing and security cameras at remote facilities, and locking up valuable materials (e.g., spools of copper wire) in laydown yards are common practices. Design suggestions have been available for decades, including an IEEE guide on the physical security of substations (IEEE Standards Association, 2000).
Hunters sighting their rifles on rural high-voltage insulators continue to be a routine nuisance. However, the physical attack on a California substation in 2013, in which attackers disabled surveillance equipment and then physically damaged 17 transformers with high-powered rifles, refocused attention on physical security threats. There is a valid concern about more sophisticated physical attacks. This is discussed in more detail in the 2012 National Academies report Terrorism and the Electric Power Delivery System (NRC, 2012). For example, during World War II, saboteurs were caught before they could carry out attacks on domestic infrastructure targets that included U.S. power plants (Ardman, 2006). Throughout the Cold War, in anticipation of physical attacks, some critical electrical assets, including control centers, were built to act as fallout shelters. At least one control center had its own freshwater well for computer cooling in case the municipal water supplies were disrupted. Currently all RTOs maintain back-up control centers. A year after the 2013 substation attack, NERC issued a federal cybersecurity reliability standard specifically addressing physical security (NERC, 2015).
The past few years have seen no apparent changes associated with the nature or level of physical threats, nor substantive and pertinent technological developments (other than a greater ability to implement microgrids or isolate sections of distribution feeders in ways that improve resilience of local grids). Thus, the committee has chosen not to reiterate the complete list of findings and recommendations from the earlier National Academies reports. Readers are urged to reference Box 6.1 and those reports for greater detail.
TABLE 6.1 Events and Actions That Can Disrupt the Operation of the Electricity System
Natural Events
Note that the frequency, intensity, and combinations of the first four of these events are likely to be significantly affected by climate change, as reflected in recent hurricane activity in the SE and Gulf Coasts, and wildfire activity in the West. Accidental Events
Malicious Actions
Note that these threats are likely to originate from hostile nation-states. The role of the electric industry in protecting the grid against national security concerns is addressed in more detail in this chapter. |
Finding 6.1: A number of the recommendations made in the 2012 and 2017 grid resiliency reports of the National Academies have not been implemented and are still relevant. Congress, regulators, and industry stakeholders can do more to improve the physical security and resilience of the U.S. electricity system by advancing those recommendations.
Another physical risk to grid reliability is a geomagnetic disturbance (GMD) or a malicious electromagnetic pulse (EMP) incident. The past two presidential administrations have issued guidance and plans to better prepare for GMD, also called solar storms (Dickinson, 2016; NSTC, 2019). At this time, there is no consensus on the appropriate EMP hardening requirements but research is ongoing to define and test options. (See Box 6.2.) The NERC EMP Task Force was formed to provide recommendations and guidance to the NERC board of trustees on potential risks EMP events may pose to the bulk power system’s reliability based on current research. The Task Force identified strategic recommendations to inform next steps in five areas: policy, research and development, vulnerability assessments, mitigation guidelines, and response and recovery (NERC, 2019a). The Task Force report recognized that cost recovery mechanisms and access to classified information regarding the EMP threat were two areas that needed to be addressed in collaboration with entities outside of NERC.
GMD and EMP were part of the committee’s focus at its November 1, 2019, workshop (NASEM, 2020). At that session, participants discussed electric system vulnerabilities to events and potential solutions. For an EMP attack, primary vulnerabilities were associated with the E1 pulse, which would impact electronic control equipment in substations, and many other critical infrastructures, including all telecommunications, computers, and other
electronic equipment in range. (See Box 6.2 for more details on EMP.) Solutions discussed during the workshop included using low-voltage surge protection devices and filters, shielded control cables, enhanced grounding and bonding practices, and shielded substations. Vulnerabilities to EMP might be mitigated by hardening critical transmission substations, but that would not protect the other critical infrastructures from the impacts. (Further details on EMP risks are provided in Box 6.2.)
While stressing the importance of continued attention to physical security, which is too easily overlooked, the balance of this chapter focuses on cyber risks in part because physical risks have been covered in such detail in other National Academies reports. Cyber threats are increasing as the tactics used by adversaries evolve and the dramatic transformations occurring on the grid, including the accelerating reliance on digital technologies, create new vulnerabilities. Over the past three decades, significant advances have been made to protect the grid but considerably more work will be needed to address the challenges that will be created as the grid evolves.
EVOLUTION OF THE GRID AND CYBERSECURITY THREATS AND CHALLENGES
Grid Control Systems
To improve efficiency and reliability, the electric grid has incorporated automated industrial control systems (ICS). The often unique and proprietary protocols, networks, and specialized devices used in an ICS environment are collectively referred to as operational technology (OT) and may include legacy and modern components. OT systems differ in important ways from conventional information technology (IT) systems. While IT systems focus on storage, management and movement of digital data, OT systems monitor and control physical processes using a tight coupling of digital communications and physical components to generate a physical action. Unlike most IT systems and some other cyber-physical systems, grid OT systems are typically 24/7 operational systems and significant negative consequences may result if they are unavailable for even short periods of time.
The first generation of wide-area ICS, supervisory control and data acquisition (SCADA) systems, was based on centralized mainframe computing technology in the mid-20th century. At that time, cyber threats were not a major concern. The OT communications networking protocols and processes were vendor-specific and custom-designed to meet the unique requirements of their function on the grid. The information communicated from sensors was openly passed to controllers, and actuators would respond to any properly formatted command. Typically, these OT devices were isolated from the IT and corporate environment. Confidentiality was not a concern, integrity was managed by message authentication protocols to protect primarily against noisy data transmission environments not malicious intent, and reliability and availability were ensured through redundancy. The ICT architecture for control systems was designed and deployed in an environment that assumed trustworthy behavior from all who interacted with it, and the protocols and processes emphasized deterministic, low-latency operations, not security.
As cybersecurity became a concern, initial OT security strategies emphasized prevention tactics and perimeter defenses. Because ICS were originally designed to operate in an environment of assumed trust, the security architecture focused on creating an electronic security perimeter that would ensure a trusted space within which the OT and control systems could function isolated from the threats. Security relied on protection defenses such as firewalls, “demilitarized zones,” and “air gaps” to prevent attackers seeking to compromise the availability, integrity, or confidentiality of critical systems from gaining access to the OTnetworks, systems and assets inside the perimeter.
By the early 21st century, automation of grid ICS using ICT increased dramatically by exploiting low-cost Internet-based ICT. One notable example is automated metering—for example, advanced metering infrastructure (AMI) that enables two-way digital communication between the meter and the utility. The deployment of more sophisticated ICS has resulted in reliability and efficiency gains. However, as control systems and networks became more complicated, the underpinning ICT supporting those systems increased in complexity and in cybersecurity risks. Cybersecurity practices have changed over this time to address these new risks, but additional changes will be needed to keep up with future challenges.
Cybersecurity Challenges Presented by the Evolving Grid
The increasing dependence of grid operations on a cyber infrastructure, with varied ICT components for sensing, communication, computation, and actuation, resulted in a power grid that is a cyber-physical system. The current grid is monitored by connected sensors recording physical changes, and the sensor data is telemetered using ICT for analytics and subsequent control decisions, and decisions are telemetered to end points that take physical actions to protect or operate the system. Every component and communication step in this process, and any combination thereof, is potentially subject to cyberattack; the availability of data to the intended recipient can be compromised, the integrity of the data can be altered through malicious intervention, or the confidentiality of the data can be breached. Combinations of these vulnerabilities at various levels of decision making can introduce disruptions with varying degrees of consequences, including cyber-enabled decisions resulting in physical damage to assets.
These cybersecurity vulnerabilities are common to IT systems and many other cyber-physical control systems. The grid, however, faces some unique people, process and technology challenges shaped by its history and cur-
rent pressures. As discussed in previous chapters, today’s power system evolved in fits and starts and was heavily influenced by decades of intense legal and regulatory changes that evolved with the grid. The requirements for reliability and the financial costs associated with gaps in power generation or delivery are high. Utilities have extremely low tolerances for anything that would impact availability of an operational system, resulting in a culture that is relatively risk adverse. This culture has been valuable and effective in maintaining the reliability of the grid. It has also been shaped and reinforced by the expectations and behavior of people who have been working in power systems for decades, which has historically made it difficult to bring rapid changes into utilities.
In addition to the people and process challenges inherent in a risk-averse culture, the current grid includes a high proportion of legacy equipment that is difficult to modify for performing security functions that more recent IT and OT assets can more readily implement. For example, most of the backbone transmission and substation systems currently in operation are based on 1950s technology (NRC, 2009). These legacy systems influence how employees think about cybersecurity, and limit the cybersecurity options and decisions they make.
The technological changes that have occurred took place without a national strategy or strong coordination among the hundreds of stakeholders involved. Changes to the physical grid occurred at different temporal and spatial scales across the continent. This resulted in highly diverse technology capabilities and constraints, and diverse implementations of physical, ICT, and organizational architectures. Each implementation was developed to address the unique requirements of the specific utility. For example, the grid architecture in a small rural utility is very different from the architecture appropriate for a major city. While there are common equipment and operational standards that can be leveraged when utilities provide mutual assistance to recover from the physical damage resulting from a severe weather event, there are very few commonalities in ICT architectures across utilities.
On a broader scale, technological innovations for the grid were historically dominated by a community of incumbents, most innovation came from industry-supported equipment vendors, and the industry was generally unaffected by changes in technology originating from outside the traditional product and service vendor community. Strong relationships developed between industry and the relatively small subset of vendors critical to their operations. This has influenced the cultural expectations of what the vendor is responsible for doing and what the utility is responsible for doing to make a technology function. In the relatively new realm of cybersecurity, where liabilities and expectations have not been refined through a history of regulations, legal actions, and other processes, it is not always clear who is responsible for cybersecurity.
Industry deregulation and restructuring, the need to accommodate changing energy policies and consumer interests, and technology advances have all contributed to a greater use of ICT in OT systems. But many of these changes are happening faster than the cultural shifts needed to create a holistic approach to grid cybersecurity across people, processes, and new technologies. The history of the grid has shaped some of the cybersecurity workforce development, skills training, and cultural challenges; the regulatory and policy hurdles; and the in situ grid technology constraints that are unique to how the electric power industry approaches cybersecurity. Table 6.2 provides a sample of some of the changes that are occurring in cybersecurity for the grid as it evolves, and Box 6.3 provides an overview on the classes of threat agents. The sections on people, processes, and technology provide more details on these challenges.
Finding 6.2: The overall ecosystem of interconnected ICT systems associated with operating the electric power system has become more extensive, complex and rapidly evolving. Existing security paradigms to secure these systems are no longer sufficient. Increasing system complexity expands the attack surface—that is, the number and type of access points for possible intrusions and the magnitude and diversity of vulnerabilities.
Finding 6.3: There are unique challenges in addressing cybersecurity risks for industrial control systems as compared to the cybersecurity risks faced by more general information technology systems.
Finding 6.4: Cybersecurity standards and industry investment focuses more heavily on developing prevention capabilities instead of detection, response and recovery. This imbalance leaves utilities ill-equipped to efficiently handle cyberattacks when they do occur (e.g., cyber black-start).
Cybersecurity Attacks and Advanced Persistent Threats
The U.S. military and federal agencies have experienced significant cybersecurity incidents for decades, and many of the challenges that were revealed in those incidents are still relevant now. In 1989, The Cuckoo’s Egg was published, documenting evidence of a 1986 ongoing cyber-espionage attack on U.S. facilities, including military and national security agencies (Stoll, 1989). Some of the key lessons learned in that incident were difficulties in getting the government to share information, the perceived tension between security and personal privacy, and the double-edge sword of transparency and security.
The first formal federal recognition of the critical risk that cyber threats pose to the electric grid came in Critical Foundations: Protecting America’s Infrastructure (PCCIP, 1997), a report submitted by the President’s
Commission on Critical Infrastructure Protection, in which the authors recognized “that the owners and operators of our critical infrastructures are now on the front lines of our security effort. They are the ones most vulnerable to cyber attacks. And that vulnerability jeopardizes our national security, global economic competitiveness, and domestic well being.” In addition, they noted “Growing complexity and interdependence, especially in the energy and communications infrastructures, create an increased possibility that a rather minor and routine disturbance can cascade into a regional outage. Technical complexity may also permit interdependencies and vulnerabilities to go unrecognized until a major failure occurs.”
In 1998, another widely known cyber-espionage attack on U.S. military and government systems, including DOE, was discovered named Moonlight Maze. Suspected to have started in 1996, the attack utilized backdoors,
TABLE 6.2 Traditional Approaches to Grid Cybersecurity and the Cybersecurity Vulnerabilities Associated with Individual Approaches Resulting from Recent and Future Changes to the Grid
| Traditional Approach to Grid Cybersecurity | Cybersecurity Vulnerabilities Resulting from Recent and Potential Future Changes |
|---|---|
| Emphasis on perimeter security | Significant reduction in the degree of isolation of the industrial control system (ICS) from the outside world. Perimeter security is no longer an effective sole defense. |
| Operational technology (OT) in an environment of implicit trust surrounded by a heavily defended perimeter | More emphasis will be placed on segmentation or micro-segmentation of internal environments and implementation of machine learning/artificial intelligence algorithms to monitor performance. |
| Self-contained OT systems with no connection to external or corporate systems | More requirements for external connections, including control systems that require real-time contact with external parties, market-forced transitions to cloud-based systems, inter-utility connections to renewable energy sources, vendor requirements for remote access to update assets, etc. |
| OT-pure systems | Increased integration of information technology (IT) and information and communications technologies (ICT) driven by technologies and trends discussed in Chapter 5 increases the attack surface and exposure of OT systems to vulnerabilities new to those systems, such as vulnerabilities in the underlying operating systems of Microsoft or Linux. |
| Energy generation, transmission, and distribution primarily owned and operated by utilities | Increased participation by a highly diverse population of stakeholders with unclear roles and responsibilities for cybersecurity. |
| Centralized control of energy transactions | Decentralized distributed control will require additional and novel cybersecurity paradigms. For example, centralized control emphasizing a locked-down perimeter defense cannot work with a distributed control system that includes prosumers and microgrids. |
| Prevention of reliability impacts on the bulk power system owing to cybersecurity incidents primarily under utility control | Increasing interdependencies on other critical infrastructures, alternative energy sources such as renewables, and stakeholders that have few or no equivalent reliability or resilience requirements or expectations will significantly increase risks to utility operations and reliability. |
| Privately and publicly owned communications used and controlled by utilities | Increased use of commercially owned communications systems by new technologies and associated stakeholders that connect to the grid with unclear and undefined roles and responsibilities for cybersecurity of those communication systems. |
| OT and ICT on-premises | Increased use of cloud services by vendors for some utility functions is shifting the market and limiting availability of on-premises solutions and options that enable more utility control over cybersecurity practices. |
| Domestic supply chain as the primary source of physical and cyber assets used in the grid | Increasing reliance on international supply chains creating cybersecurity concerns about risks such as malicious implanted hardware, software, and/or firmware elements. |
| Innovation driven domestically resulting in domestic product development and domestic vendor standards | Increased internationally driven innovation changing the focus of product and services development and associated vendor standards, etc., resulting in potential mismatches between domestic utility requirements for cybersecurity products and internationally driven standards and product development. |
| Reliance on Indicators of Compromise to detect threats | Looking for indictors of things that are known to be bad will continue to be important but will not be sufficient. More of the advanced threats can only be detected by analyzing patterns of multiple events and finding evidence of behaviors indicative of a stress or attack. |
| Adversaries using malware as a primary tactic | Increasing use of native functionality of an ICS to implement attack goals rather than malware (also known as “living off the land”). |
| Cryptography as a cybersecurity tool | Is one tool as part of an overall solution, and will likely be ineffective in its current form if quantum computing advances significantly. |
| Reliance on passwords for authentication | Increasing use of biometric-based (i.e., “something you are”) and ownership-based (i.e., “something you have”) for authentication. |
| Emphasis on prevention of incidents | To detect more sophisticated adversaries, more focus will be needed: to advance utility capabilities for detection and root cause analysis, which can drive resilience and response actions; and, to develop stronger capabilities for containment, remediation and recovery. |
| Traditional Approach to Grid Cybersecurity | Cybersecurity Vulnerabilities Resulting from Recent and Potential Future Changes |
|---|---|
| Black start response and recovery established for grid operations | Increased need to understand how to do black start for the ICT that underpins grid operations, including when under attack, and how to do black start for other critical infrastructures that can impact grid reliability. |
| Speed, uptime, and latencies in communications technology | Anticipated continual advancements in wireless and satellite technologies. Unclear at this time whether the changes will directly or indirectly affect cybersecurity risks. |
| Control theory and tools focused on one-way flow and limited number of end nodes | Increased need to create simulation capabilities and tools that can manage and control a dramatic increase in the number of end-point nodes and two-way energy flow. This will require different architectures. As the number of endpoint data sources increases, the cybersecurity attack surface also increases. |
| Cybersecurity as the focus | Increased attention to data privacy concerns in addition to data security concerns as more consumer data is involved in utility transactions and potentially grid operations. |
left few traces and was undetected for a long time. It “emphasized the crucial need for firewalls and encryptions and, above all, the difficulties of identifying and attributing an attack to a specific adversary” (Haizler, 2017). That same year Presidential Decision Directive 63 (PDD-63) established a national policy for critical infrastructure protection from physical and cyber threats, and assigned DOE responsibility for the electric grid, and oil and natural gas infrastructure cybersecurity. The electricity industry documented the significant work that should be done to secure the grid’s cyber infrastructure as early as 2006 (Energetics, 2006).
In 2017, almost 20 years after PDD-63, the Defense Science Board Task Force on Cyber Deterrence identified three challenges that applied to all critical infrastructures (DSB, 2017):
- “major powers (e.g., Russia and China) have a significant and growing ability to hold U.S. critical infrastructure at risk via cyber attack. … Although progress is being made to reduce the pervasive cyber vulnerabilities of U.S. critical infrastructure, the unfortunate reality is that for at least the next decade, the offensive cyber capabilities of our most capable adversaries are likely to far exceed the United States’ ability to defend key critical infrastructures.”
- “regional powers (e.g., Iran and North Korea) have a growing potential to use indigenous or purchased cyber tools to conduct catastrophic attacks on U.S. critical infrastructure.”
- “a range of state and non-state actors have the capacity for persistent cyber attacks and costly cyber intrusions against the United States.”
Increasing risks from state actors to the grid were specifically highlighted at the committee’s November 2019 workshop (NASEM, 2019). Because the electric grid underpins most critical infrastructure systems in the United States, including water, food, health, communications, transportation, and government functions including national defense, it is a potential target for nation-state adversaries intent on disabling those critical functions.
Workshop participants noted that “China has the ability to launch cyber-attacks that cause localized, temporary disruptive effects on critical infrastructure—such as disruption of a natural gas pipeline for days to weeks—in the United States” and “Moscow is mapping our critical infrastructure with the long-term goal of being able to cause substantial damage” (Coats, 2019). Adversaries that learn the details of grid control systems and the engineering that underpins power system operations can use this knowledge to become capable of more sophisticated attacks. Such attacks may be aimed at disrupting the defense infrastructure of the United States through the electric grid or may be aimed at disrupting society as a whole as a means of attack. Nation-state adversaries could amplify the impacts of a cyber-attack against the electric grid by coupling the attack with other adverse actions to increase the uncertainty and social unrest associated with an electric system disruption (NRC, 2003).
At the committee’s workshop, Dr. Carol Hawk, a program manager leading cybersecurity research at DOE described two general categories of cyberattacks on energy systems: (1) the adversary is attempting to cause the system or the component to do something that is was not designed to do; or (2) the adversary causes the equipment to function in a way it was designed to function but in such a way that it’s in the wrong operational context. The 2015 and 2016 cyberattacks in Ukraine are good examples of both types of attack. In the 2015 attack on Ukrainian distribution utilities, adversaries gained a foothold using a phishing attack and then used a variety of malware tools to pivot within the system until they had direct access to the ICS targets. Months after the initial compromise, the adversaries, using remote access, entered the system, took “control of the operator workstations and thereby lock[ed] the operators out of their systems” (Lee et al., 2016), and used the human machine interfaces (HMIs) to remotely open breakers in at least 27 substations impacting 225,000 customers and causing regional blackouts that lasted approximately 1 hour. In addition, they created malicious firmware that they remotely uploaded to the serial-to-Ethernet gateway devices, rendering them unusable.
In 2016, attackers successfully targeted a Ukrainian transmission substation using a malware framework called CRASHOVERRIDE “that has modules specific to ICS protocol stacks including [International Electrotechnical Commission] IEC 101, IEC 104, IEC 61850, and [Open Platform Communications] OPC.” In contrast to the 2015 attack, the adversaries used the protocols—the native functionality of the system—“to open circuit breakers on [remote terminal units] RTUs and force them into an infinite loop keeping the circuit breakers open even if grid operators attempt to shut them.” This resulted in “de-energizing the substations” (Dragos, 2017). The authors
surmised that “it appears the Kiev transmission substation targeted in 2016 may have been more of a proof of concept attack than a full demonstration of the capability in CRASHOVERRIDE.” They also noted that the malware framework was “designed to allow the inclusion of additional payloads such as [distributed network protocol 3] DNP3 but at this time no such payloads have been confirmed.” The IEC protocol stacks used in the Ukraine attack are used internationally, whereas DNP3 is a communications protocol widely used in the U.S. electric grid.
Two examples of attacks impacting control systems have also occurred in the U.S, confirming that cybersecurity attacks on ICS are not limited to international utility victims. In 2019, NERC released Lessons Learned: Risks Posed by Firewall Firmware Vulnerabilities describing the successful exploitation of a vendor’s firewall that allowed an unauthenticated attacker to “cause unexpected reboots of the devices” resulting in “a denial of service (DoS) condition at a low-impact control center and multiple remote low-impact generation sites” and “brief communications outages (i.e., less than 5 minutes) between field devices at sites and between the sites and the control center” (NERC, 2019c). In 2020, the DHS Cybersecurity and Infrastructure Security Agency (CISA) issued Alert (AA20-049A) on Ransomware Impacting Pipeline Operations describing the successful use of “commodity ransomware” to affect “control and communication assets on the operational technology (OT) network of a natural gas compression facility” (CISA, 2020a). The assets that were attacked experienced “a Loss of Availability [T826] on the OT network” including “(HMIs), data historians, and polling servers. Impacted assets were no longer able to read and aggregate real-time operational data reported from low-level OT devices, resulting in a partial Loss of View [T829] for human operators. The attack did not impact any programmable logic controllers (PLCs) and at no point did the victim lose control of operations.”
Within the academic literature examples of public experiments demonstrating cybersecurity attacks that cause physical damage to grid OT assets are few, in part because of the costs associated with damaging expensive grid equipment. There is, however, research demonstrating damage to IT systems or using simulations to illustrate potential physical damage to OT assets, but only limited research showing physical damage on OT systems. One example, by Angle et al. (2019), demonstrated a small-scale test attacking the software in a variable frequency device (VFD). The cyber-attack caused capacitors in the VFD to explode, and switches in the converter to fail “causing an internal short and blowing the input fuse on the VFD.” Examples of other publicly discussed cyberattacks that have resulted in damage to cyber-physical systems are provided by Ani et al. (2016), Maynard et al. (2020), and Stellios et al. (2016).
Unsophisticated attacks may be thwarted by standard security defenses, but to stop an adversary who directs an attack on a specific target will require more sophisticated, multifaceted defenses. Cybersecurity threats come from many sources, but of particular national security concern are advanced persistent threats (APTs). An APT is defined by the National Institute of Standards and Technology (NIST) as “an adversary that possesses sophisticated levels of expertise and significant resources which allow it to create opportunities to achieve its objectives by using multiple attack vectors including, for example, cyber, physical, and deception. … The APT pursues its objectives repeatedly over an extended period, adapts to defenders’ efforts to resist it, and is determined to maintain the level of interaction needed to execute its objectives.” A nation-state is suspected to be behind the APT attacks that occurred in Ukraine, but not all APT attacks are sponsored by nation-states.
Because of the high level of national security implications, much knowledge concerning particular APTs, including the tactics, techniques and procedures used by malicious actors that represent APTs, and demonstrations that cybersecurity attacks can result in physical damage, is not public. The committee clearly recognizes the seriousness of APTs. However, to ensure that the material covered in this chapter is appropriate for public release, the committee has focused this chapter on the fundamental cybersecurity challenges facing the grid as it changes rather than providing an in-depth review or assessment of APTs specifically.
CURRENT STATUS OF INDUSTRY PREPAREDNESS AGAINST CYBERSECURITY THREATS
Efforts to Secure the Grid
Industry, government, and many other stakeholders have taken many actions to protect the grid. And, although unintentional, another mitigating strategy for the U.S. grid is the variability in architectures deployed across all the
utilities. As stated above, utilities vary in size and complexity to meet the needs of customers and this has created diversity in the use of architectures and assets.
Among the many federal actions that have been taken to advance cybersecurity, of particular note are the mandatory cybersecurity standards required by FERC and developed by NERC. These standards, called the Critical Infrastructure Protection (CIP) standards, are part of the larger body of NERC Reliability Standards. All bulk power system owners, operators, and users must comply with the CIP standards. Initially drafted in 2006, the first eight cybersecurity standards were approved by FERC in 2008 to “provide baseline requirements for the protection of critical cyber assets that support the nation’s Bulk-Power System” (FERC, 2008). There are currently 12 CIP standards subject to enforcement (NERC, n.d.). All CIP standards undergo an intensive review process that includes voluntary participation by industry, and each standard has been revised as needed to accommodate changes in threats and best practices. The CIP standards review process can consume a considerable amount of voluntary time provided by utility staff. The electric grid is the only critical infrastructure that is required to comply with mandatory federal cybersecurity standards, and the CIP standards have been used as a model in other industries and in other countries.
Congress has made federal investments in cybersecurity research, development, and deployment of cybersecurity technologies, and in supporting actions to strengthen the nation’s cybersecurity response capabilities. Federal agencies have hosted national cybersecurity exercises and provided funding to states to facilitate the development of a stronger cybersecurity posture at regional, state and local scales. These investments have created resources widely used by industry, including DOE’s Cybersecurity Capability Maturity Model (C2M2), used to complete voluntary evaluations of the maturity of a utility’s cybersecurity capabilities and posture (DOE, 2014), and the Cybersecurity Risk Information Sharing Program (CRISP), a collaboration with NERC’s Electricity Information Sharing and Analysis Center (E-ISAC) to collect, analyze, and distribute actionable threat information to the energy sector (DOE, n.d.).
At the state level, “in 2019 at least 16 states considered almost 50 measures to address the cybersecurity of the electric grid and other critical infrastructures” (Shea, 2020) and 11 of those states enacted cybersecurity measures. Proposed measures were focused on creating task forces or committees to review cybersecurity in the energy sector, looking at cybersecurity standards and reporting requirements, passing open records exemptions laws to prevent public access to critical infrastructure cybersecurity information, and exploring how to finance cybersecurity programs, recognizing that funding what might be an ongoing investment through a cost-recovery mechanism is challenging. Twenty-five states currently have established cybersecurity task forces, working groups and councils, and 30 states have official partnerships with universities and colleges for cybersecurity-related support and services (McFarland et al., 2020). While these efforts may not be specifically focused on grid cybersecurity, states and local governments are very concerned about the rise in cybersecurity attacks, particularly ransomware attacks, on municipal governments.
To strengthen state-level responses, more state governments are “providing services to county and municipal governments, including endpoint protection, shared service agreements for cyber defensive tools, incident response and statewide cybersecurity awareness and training” (NASCIO and NGA, 2020). In a 2019 survey representing responses from 49 states and territories, 65 percent of state Chief Information Officers said they were providing security infrastructure services to localities. Based on the survey results, more states are expected to pursue a “whole-of-state approach to cybersecurity,” where there is “collaboration among state agencies, local governments, utilities, private companies, universities, healthcare and others,” Of the survey participants, “25 percent of states report they have taken a whole-of-state approach,” 39 percent said it was in progress, and 14 percent said it was planned.
Within industry, the Electricity Subsector Coordinating Council (ESCC) is a chief executive officer (CEO)led effort (ESCC, 2013). The ESCC acts as “the principal liaison between the federal government and the electric power industry on efforts to prepare for, and respond to, national-level disasters or threats to critical infrastructure” (ESCC, 2020). Formed in 2013 following the release of the National Infrastructure Advisory Council (NIAC)’s 2010 report, A Framework for Establishing Critical Infrastructure Resilience Goals, the ESCC includes CEOs and executives from up to 30 electric utilities and their trade associations who meet regularly with senior administration officials from the White House, cabinet agencies, federal law enforcement, and national security organizations,
and Canadian electric company executives (NIAC, 2010). The ESCC’s four strategic committees focus on threat and information sharing; industry-government coordination; research and development; and cross-sector liaisons.
One of the many actions the ESCC has taken to improve grid security was the development of the voluntary Cyber Mutual Assistance (CMA) Program. The CMA Program builds on the long history of the energy sector’s culture of voluntary mutual assistance following natural disasters. Through the program, industry cyber experts agree to “provide voluntary assistance to each other in advance of, or in the event of, a disruption of electric or natural gas service, systems, and/or IT infrastructure due to a cyber emergency” (ESCC, 2019). Participation in the program is free to “all entities that provide or materially support the provision of electricity or natural gas service” and execute a mutual nondisclosure agreement provided by the CMA Program. In addition, the ESCC Playbook was created for senior industry and government executives to coordinate their response and recovery efforts and communicate with the public during incidents. The playbook is updated annually, tested in exercises, and has been used in events (ESCC, 2020).
Additionally, the industry is very involved with the E-ISAC. The E-ISAC’s goal is to “be a world-class, trusted source of quality analysis and rapid sharing of security information for the electricity industry.” Membership is open to all “vetted electricity owners and operators in North America” and members receive: “private-level situational awareness on security threats, including alerts; physical security and cybersecurity bulletins; remediation; task force reviews; events calendars; and other security-specific resources” (DOE, n.d.).
The E-ISAC organizes and leads GridEx, a distributed play grid exercise that simulates a cyber and physical attack on the North American electric grid and other critical infrastructures. GridEx gives participants a forum to demonstrate how they would respond to and recover from coordinated cyber and physical security threats and incidents, strengthen crisis communications relationships, and provide feedback to all of industry on lessons learned during the exercise. Additional perspectives on critical security policy issues are gathered at the invitation-only Executive Tabletop from senior executives in industry and government. The fifth iteration of the drill, held November 2019, convened more than 7,000 people across North America, from employees of multistate utilities to smaller cooperatives to U.S. government agencies. More than 500 organizations participated. It was a record turnout, and the first time that utilities tested their ability to respond to an emergency order from the Secretary of Energy to restore grid operations. In addition to GridEx, other exercises are sponsored by DOE, DARPA, the states and other government entities to improve cybersecurity incident response, and many utilities conduct their own cybersecurity exercises.
Investments in cybersecurity research have greatly expanded and improved the technologies and resources needed to protect the grid from physical and cyber threats. Research occurs across many federal agencies, national laboratories, academic institutions, syndicated research organizations, industry trade organizations, vendors, and other stakeholder organizations. Industry participation is frequently required to receive federal funding for research, and many utilities are active partners working to help create new cybersecurity tools, technologies, and resources. Other industry networks and stakeholder organizations, like the North American Transmission Forum, provide opportunities for utility staff to develop and exchange cybersecurity best practices.
DOE’s research and development programs are critically important to improving and advancing grid cybersecurity and must be continued and expanded. DOE has historically organized its cybersecurity research agenda around priorities identified in a roadmap developed in collaboration with industry, vendors, academia, and government stakeholders. The first roadmap was completed in 2006 (DOE, 2006), and it was updated in 2011 (DOE, 2011) in a process that included more than 80 stakeholders. Progress toward milestones and goals was tracked on an Interactive Energy Roadmap website. A new roadmap is needed to capture and structure the stakeholder community’s priorities for grid infrastructure and operations cybersecurity research and development (R&D). As the role of ICT continues to expand to support grid operations, there is an increased importance in understanding how to optimize computing, communications, and control technologies for grid operations without compromising security. A new basic research program is critically needed that explores the implications and applications of rapidly evolving computing, communications, and control technologies on grid cybersecurity and cyber resiliency.
Recommendation 6.1: The Department of Energy (DOE) research program in grid cybersecurity is an important source of innovation to improve the resiliency of future grid infrastructure and operations.
DOE should develop a regularly updated research and development (R&D) priority roadmap in collaboration with the electric industry, with input from academic and national laboratory researchers and the vendor community. The R&D priorities in the roadmap should be funded by appropriations from Congress to DOE. The roadmap should be oriented to develop and demonstrate new technologies for resilient architectures that will enable energy delivery systems, and any interconnected systems, to be designed, installed, operated, and maintained to survive a cyber incident while sustaining critical functionality and enabling quick recovery.
Recommendation 6.2: Owing to the increasing importance of computing, communications, and control technologies for the operation of the current and future grid, Congress should appropriate funds to the National Science Foundation (NSF), in consultation with the Department of Energy (DOE), to specifically focus on research programs exploring the implications and applications of rapidly evolving computing, communications, and control technologies on grid cybersecurity and cyber resiliency.
Challenges in Measuring the Current State of Grid Cybersecurity
There is a strong desire to know the grid’s security status and an inherent tendency to assess grid cybersecurity based solely on the cybersecurity practices of utilities. In reality, the strong dependence of grid reliability and resiliency on other critical infrastructures, and the dramatic increase in stakeholders that could impact grid reliability means grid cybersecurity and cyber resiliency now relies on the cybersecurity practices of many more entities than just the utilities. Currently, there are no directories listing all of the stakeholders that could influence the cybersecurity and cyber resiliency of grid operations. And there are no centralized repositories for information summarizing what cybersecurity and cyber resiliency practices are being used by these stakeholders. For comprehensive situational awareness of the cybersecurity and cyber resiliency posture of the power system, all of the relevant participants would need to participate in sharing their cybersecurity practices, including government, the other interdependent critical infrastructures such as communications and natural gas, supply chain vendors, markets, and so on. As new stakeholders and technologies increase their role in enabling, providing, managing, and storing energy, accurately estimating the cybersecurity and cyber resiliency of the power system based on utility practices will be increasingly difficult.
Data summarizing the utilities’ cybersecurity and cyber resiliency posture are very limited. Similar to the national security concerns associated with protecting information on APTs, there are national security concerns associated with collecting, sending, storing, and managing detailed data on grid systems and security practices.
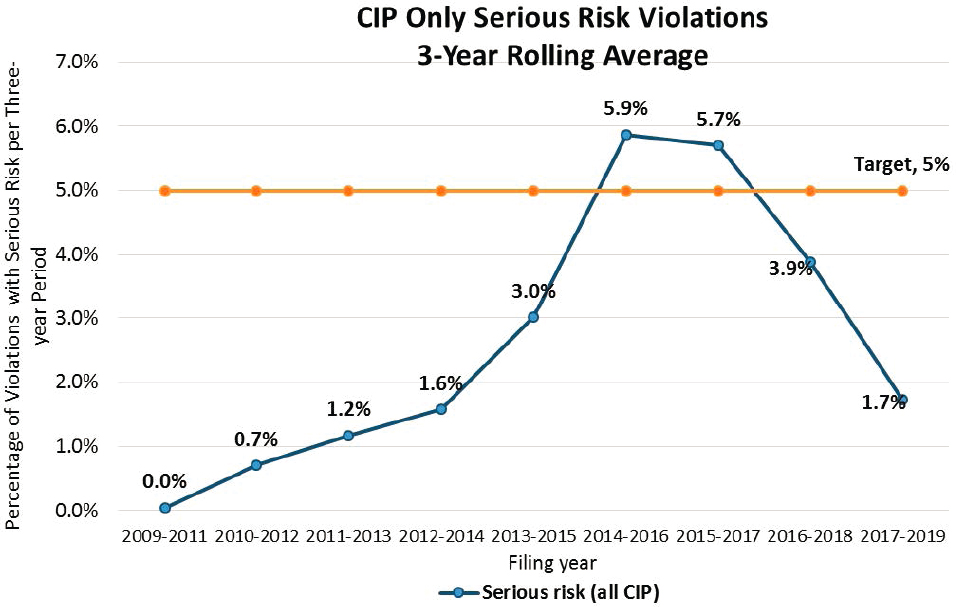
Two sets of data that do exist evaluating the industry’s state of cybersecurity preparedness include NERC’s Compliance Monitoring and Enforcement Program (CMEP) Annual Report, which documents the industry’s performance against the CIP Standards, and the 2018 CIP Themes and Lessons Learned: Mitigating Risks Behind the Critical Infrastructure Protection Reliability Standards, Second Edition, which is less up-to-date and is focused on compliance with the CIP standards as of 2018. There have been changes to the CIP standards since the release of this report.
Figure 6.3 from the 2020 CMEP Annual Report illustrates changes in the percentage of serious risk violations of the CIP standards between 2009 and 2019. These results show that over time, industry CIP audits have reported fewer serious risk violations of the CIP standards. The majority of 2019 serious risk violations highlighted in the report were related to Electronic Security Perimeters, interactive remote access, ports and services, security patches, account management, and baselines.
The 2018 CIP Themes and Lessons Learned report is a collaboration between NERC, ReliabilityFirst Corporation (RF), Western Electricity Coordination Council (WECC), and SERC Reliability Corporation (SERC). This report identified four risk themes that cause difficulty for some entities in mitigating CIP standard related risks:
- Disassociation between compliance and security (45 percent): Treating security and compliance as completely separate functions that serve separate purposes, resulting in a diminished value or emphasis on compliance;
- Development of organizational silos (29 percent): Lack of internal coordination and uniformity between business units, departments, or layers from the top down;
- Lack of awareness of an entity’s needs or deficiencies (15 percent): Not understanding how an entity’s systems work or how its compliance department is functioning and performing; and
- Inadequate tools or ineffective use of tools (11 percent): Not using tools that are necessary given an entity’s environment, improper configuration of tools, and over-reliance on automated tools.
The authors provided a percentage indicating the frequency of each theme, but noted that in general multiple, overlapping, interrelated causes are involved in compliance deficiencies.
These two reports provide a different perspective on industry challenges to meeting compliance with the CIP standards. Neither study was intended to provide a global assessment of the current state of grid cybersecurity, particularly when the CIP standards are only applicable to the bulk power system (generation and transmission). Also, these deficiencies are not unique to the electric sector. However, since the bulk power system is required to meet specific standards, this analysis is possible. The CMEP Report lists the technology practices that were most frequently out of compliance. The CIP Themes and Lessons Learned Report puts the technology practices into a relative perspective against the people and process challenges. The results of this study showed that only 11 percent of the issues were directly related to tools; the majority of the noncompliance issues stemmed from individual behavior or organizational processes.
The committee recognizes the high level of interest many stakeholders have in wanting to know: How secure is the grid? The committee agrees that this is a critically important question. But there are no models or sufficient data that can answer this question today. As the grid continues on its current evolutionary path, determining the
level of security risk facing the power system will require new model and data-driven analysis techniques that make use of more information than the status of utility cybersecurity practices alone.
A RESILIENT FUTURE VISION
As outlined earlier in this chapter, progress has been made in the past two decades toward building a grid that is reliable, secure, and resilient. However, current efforts to prepare for, defend against, and recover from attack are certainly not sufficient to maintain the reliability, security, and resilience of the grid in the future, nor is it known to what extent they protect the grid of today, as argued in the preceding section. In particular, the electric grid’s inherent complexity demands a system-centric rather than a component-centric approach to cybersecurity and cyber resiliency, and the use of system-level resilience as the approach to provide that cybersecurity. Just as the Enhancing the Resilience of the Nation’s Electricity System report argued that the overall grid must be made resilient (NASEM, 2017), the challenges to grid cybersecurity argue that the grid’s cyber infrastructure itself must be made resilient.
Building the grid’s cyber infrastructure out of components that are reliable, secure or resilient will not ensure the resulting infrastructure is reliable, secure or resilient, since reliability, security, and resilience are inherently system-level properties. Said another way, a system that is built from components that are individually secure may not be secure as a whole owing to unintended interactions between its components. For example, a microgrid may involve components from multiple vendors, including generation technologies, storage technologies, communications infrastructure, protection devices, controllable loads, and so on. Each component may be tested to ensure the cybersecurity controls built into the component function as expected. But in order to permit components from different manufacturers to interact, the system integrator may need to create unique code that acts as a translation bridge and enables the two proprietary communications protocols used by the different manufactures to talk to each other. In the process, the code developed by the integrator may not be secure, or the integrator may have to compromise the cybersecurity integrity of one of the components to get the two components to interact as expected, creating a vulnerability in the system.
To make the grid’s cyber infrastructure resilient, it is important to minimize the risk of intrusion and attack, but at the same time, design a resilient grid cyber infrastructure under the assumption some attacks will be successful. The ability to detect a compromise to the grid’s physical and ICT systems is a foundational first step toward security and resilience. The future grid will enable operators to see and understand the state of the grid and its cyber infrastructure in real-time at all times. A resilient ICT cyber architecture will, as a first step, actively monitor both the cyber and physical portions of the grid for intrusions and anomalies, detect when compromises occur, and learn from such incidents to alert on compromises.
Second, the grid cyber infrastructure must have the capacity to understand events in context and respond once an intrusion is detected in order to maintain system operations. A cyber resilient system will enable the operator to quickly and accurately diagnose the cause of an incident, assess the negative impacts occurring now, and predict the negative impacts that could result from the attack later. Third, response actions will limit and control the impact of an attack and enable the system to maintain critical functionally during the attack. Training and tools will enable system owners to quickly understand response scenario options, compare risks of each response scenario, and recommend or execute an appropriate response. Ultimately, a resilient cyber infrastructure will be able to restore full functionality after the attack. For example, if power delivery is compromised, cyber and physical operational data will be recorded to accelerate restoration of the control system and power delivery functionality.
A resilient grid will also include a well-trained workforce that reinforces a cybersecurity culture within their organization, utilizes effective information sharing mechanisms, embraces novel response methods and modifies response skills as the threats evolve. And it will include cybersecurity and resilience metrics or processes that can be used to validate the effectiveness of different cyber resilience approaches, and understand trade-offs, risks and costs associated with different approaches.
It should also be understood that the grid and its cyber infrastructure are not a single system, but rather a “system of systems” that while loosely coupled, can be worked on separately to make progress toward our overall goal of grid cyber resilience. Therefore, in contrast to the example of interacting components given earlier in this
section, progress toward cyber resilience can be made incrementally on different systems within the grid’s cyber infrastructure. For example, in practice, the grid’s transmission cyber infrastructure’s security and resilience can be improved independently of security and resilience improvements to the grid’s advanced metering infrastructure. Because of this, it is important not to let “perfect be the enemy of the good” and assume that unless you can make the entire grid cyber infrastructure resilient, you have failed to improve the grid’s cyber resilience.
With this understanding in mind, the remainder of this chapter focuses on specific strategies that can be used to improve the resilience of the grid, rather than a specific application of those strategies to specific grid systems or architectures, since those systems and architectures will change in unknowable ways over time. Improving the grid’s cyber resilience rests on strategies related to three pillars: people, processes, and technology. According to the SANS 2019 OT/ICS survey, “People present the greatest risk (62%) for compromise to an organization’s OT/control systems—not surprising, because the human element lies at the heart of cybersecurity incidents and breaches. This element is followed rather distantly by technology (22%) and process (14%)” (Filkins and Wylie, 2019). Within these categories, there are many focal points, but challenges and opportunities for improvements exist in each category. Actions must be taken in a coordinated manner across all three categories to build the resilient cybersecurity infrastructure needed. For electric system cybersecurity, people are pivotal in implementing effective controls successfully; processes define options for what is encouraged or discouraged; and technology extends the limitations of our human abilities to understand systems and take actions. The following sections describe some specific challenges and opportunities in the areas of people, process and technology that need to be addressed to achieve cyber resilience.
Finding 6.5: Effective electric system cybersecurity requires more than technology. It hinges on people, processes, and technology, where a vulnerability in any one of these categories can jeopardize the entire system. While data support the importance of all three pillars, there is a historic imbalance in the allocation of attention and resources toward technical solutions. A more balanced approach is needed.
ADVANCING CYBER RESILIENCE THROUGH PEOPLE
Achieving cybersecurity is momentary and maintaining it requires a dynamic on-going back-and-forth exchange between people, adversaries and defenders, using technology. People play a role in every aspect of creating and sustaining an organization’s cybersecurity posture, and in maliciously compromising it. Their ability to be successful in either goal depends on cultural, behavioral, cognitive, and physiological capacities and limitations.
People are both a vulnerability and the first line of defense. Significant investments in cybersecurity technology can be undermined when organizations fail to adequately invest in supporting the training and security culture of their people, or technology developers fail to understand the human dimension. In an analysis of nine successful attacks on critical infrastructure ICS, the most common methods used to gain access were through people via spear-phishing, removable media storage, and water hole attacks (Maynard et al., 2020). A strong cybersecurity culture combined with appropriate training can improve the knowledge and skills of an organization’s workforce increasing their capacity to prevent and respond to an attack. And understanding how adversaries think and the TTPs they use in an attack can help focus investments on appropriate defenses, and response and recovery actions.
Cybersecurity Risk, Tools, and Training
Individuals interpret information in complicated ways. The order in which information is presented, the information’s source, and how easy it is to collect data that confirms or refutes an already established belief all impact how a person decides and responds. These are examples of cognitive biases (Table 6.3). One important area where cognitive biases affect cybersecurity is the assessment of risk. People are inherently bad at accurately estimating low-probability risks. This can impact how senior leadership evaluates and prioritizes cybersecurity among competing demands.
Many cybersecurity attacks employ digital or physical “social engineering,” such as a phishing email or manipulating a situation to gain physical access. “Social engineering, almost by definition, capitalizes on human
psychology, such as cognitive limitations and biases, which attackers exploit to deceive the victim” (Greitzer, 2014). Greitzer et al. (2014) identified a few reasons why social engineering is successful including: lack of attention to cues or lack of knowledge about the exploitative nature of a malicious message; narrowing of attention exacerbated by high cognitive load (high subjective mental workload); problems with poor judgment or cognitive biases; people underestimate the likelihood of threats and thus ignore them; and, differences in risk tolerance and risk perception across employees, as well as employee values and attitudes. Conteh and Schmick (2016) concluded that “while technology has a role to play in reducing the impact of social engineering attacks, the vulnerability resides with human behavior, human impulses and psychological predispositions.” Attackers understand these limitations and intentionally use this knowledge to gain access to systems by manipulating human behavior (Aldawood and Skinner, 2018).
Cognitive biases also impact decisions on how to respond to cybersecurity incidents. Jalali et al. (2019) found that more experienced managers achieved more optimal decisions than inexperienced individuals when cybersecurity incidents were predictable, but fared no better than inexperienced individuals when cybersecurity incidents were random. Less experienced individuals attempted alternatives that experienced managers avoided owing to perceived risks associated with trying new responses. Their results supported previous findings that more experienced individuals employ less exhaustive search procedures, and leverage cognition biased by past experiences (Jalali et al., 2019). More work is needed to apply research results on how decisions are made and how biases impact decision making, including work by Simon (1991) on the bounded rationality of decision makers, and many others to improve cybersecurity efforts. For example, awareness of cognitive limitations and biases can be used to improve risk assessment, to develop awareness training programs to prevent and mitigate social engineering, and to improve cybersecurity decision support tools used by control operators and engineers, and security professionals.
In addition to leveraging knowledge about cognitive biases, the effectiveness of cybersecurity tools can be improved by incorporating an understanding of human factors2 and using human-centered design3 principles. For example, people have physiological and cognitive limitations and “displays that use graphics, colors, and symbols are processed more quickly than displays that are text- or digit-heavy” (NASA, 2014). The design of a graphical user interface will impact whether the most important information is successfully conveyed, and if it results in the human operator taking the desired control action. Software developers who understand cognitive efficiency can make the information easier to process and understand, enabling the user to make and implement critical decisions faster. These principles were used to improve visualizations of power system information by Overbye et al. (2005) who showed, using human factor experiments, that solution times and accuracy in task completion to evaluate line violations were improved by changes to visualizations of the data presented to the user.
In addition, “As the amount of information on a display increases (Wickens and Hollands, 2000), the time it takes the user to find a given piece of information increases … the more information … the slower the users will be in completing their tasks. It is often erroneously believed that the best approach to a good display is to minimize the number of clicks the operator must make by putting a large amount of information on the display” (NASA, 2014). When control engineers and operators are under duress, their cognitive capabilities, “the mental processes of attention, memory, reasoning, decision-making, judgment, and problem-solving” (NASA, 2014) change. “The use of cluttered displays requires high levels of attention and serially searching for information, resulting in high mental effort and increased risk of errors, especially under conditions of high stress or arousal” (NASA, 2014). Software developers who do not understand that a person’s physiological and cognitive states are not static are likely to develop GUIs that remain static when in fact the amount of information provided to the operator should decrease under conditions of stress.
___________________
2 Human factors: the application of psychological and physiological principles to the engineering and design of products, processes, and systems with a specific focus on the interaction between the human and the thing of interest, and a goal of reducing human error, increasing productivity, and enhancing safety and comfort.
3 Human-centered design: “an approach to interactive systems development that aims to make systems usable and useful by focusing on the users, their needs and requirements, and by applying human factors/ergonomics, and usability knowledge and techniques. This approach enhances effectiveness and efficiency, improves human well-being, user satisfaction, accessibility and sustainability; and counteracts possible adverse effects of use on human health, safety and performance” (British Standards Institution, 2019).
Understanding human factors may become even more important for developing cybersecurity software that uses nontraditional interfaces. As technologies move away from passwords, other authentication options are being used that fall into the “something you are” category, such as haptic (sensations of touch), hand and face gestures, locomotion using gross motor movements, or auditory or speech information.
As the complexity of the electric grid and its underlying components increases, software developers will also need to consider that human response times to assess and act on new information may be orders of magnitude slower than the time scale of a needed grid response. Some tools will need to use a combination of automated responses and human decisions, and some tools may need to be completely automated. Rather than choosing between control practices that are decided by people versus automated machine learning (ML)/artificial intelligence (AI), research is needed to define the optimal hybrid balance leveraging both the decision processes that humans excel at and ML/AI. Because many OT devices are deterministic, a typical IT response to a cyber event may “brick” the device. That is, the device will stop functioning and it may be necessary to send a field electrician to either replace the device or reconfigure it. Involving ICS engineers and operators in the development process will ensure that automated responses do not compromise the reliability of the grid or the safety of people. Unlike IT systems, the impact of an ICS error may result in the maiming or death of an electrical worker or environmental damage. Potential health and safety impacts are primary reasons why the management of the electric grid has adopted a risk averse attitude.
Human factors and human-centered design can also be used to improve cybersecurity training programs vendors create for new security tools. Training is most effective when the designers consider, and experimentally test in advance, how users will use their product. System designers are typically not a representative sample of the user population (NASA, 2014). Errors can be reduced if training considerations are integrated into the development cycle of hardware and software, and product design is optimized to minimize training time, rather than developing training programs after the design of the product is complete (Maguire, 2001). The cost of errors and of compensating for design savings through complex procedures, extended training, and longer time on task over the full life cycle of a system is notably greater than that of integrating trainability into the initial design (NASA, 2014).
This is particularly relevant for transitioning tools originally developed for IT cybersecurity into OT cybersecurity. Working closely with the target audience during the design or redesign of product training materials can facilitate a clearer understanding of the users’ priorities and constraints. Cybersecurity tools and training programs that are closely aligned with the user’s needs can increase the probability they will be properly installed, configured securely, maintained securely, and utilized effectively.
Cybersecurity Culture
The ability of an organization to advance its cybersecurity efforts depends on the individuals in leadership positions and the culture of the organization. An organization’s leadership will set the tone, budget, and policies that define and reinforce a particular cultural attitude toward cybersecurity. In addition, leadership will influence employee behavior based on how they individually role-model and follow cybersecurity policies and practices.
Ideally, all employees recognize their unique roles in achieving cyber resilience. NIST provides general guidance on what different job roles in an organization could do to protect the organization from cyber threats based on the type of work performed by the individual (NIST, 2018a). Unfortunately, for many organizations, cybersecurity is treated as solely the responsibility of the IT department and is not fully integrated into all departments as part of a holistic risk management endeavor.
Many utilities consider cybersecurity, like utility vegetation management or an insurance policy, to be a cost center but there are other cultural scenarios that exist. In an analysis of extended interviews with 25 Chief Information Security Officers (CISOs) from 17 companies (ADP, Aetna, Allergan, Bank of America, Cisco, Citizens Bank, Eli Lilly, Facebook, Fannie Mae, Goldman Sachs, HSBC, Human Longevity, JPMorgan Chase, LifeLock, Morningstar, Starbucks, and U.S. Bank) four distinct “tribes” were identified in how CISOs approached cybersecurity (McGraw et al., 2017):
TABLE 6.3 Cognitive Biases That Could Affect How an Operator Interprets Data About and Responds to a Cyber Incident
| Bias Category | Bias | Description |
|---|---|---|
| Information integration, communication, and presentation | Selective perception | The active screening out of information that is not thought to be salient or important (e.g., website banner blindness). |
| Wishful thinking or optimism bias | The tendency to see things in a positive light and resultant distortion of perception and thinking. | |
| Anchoring and adjustment | Our decisions are unduly influenced by initial information that shapes our view of subsequent information. | |
| Underestimating uncertainty and the illusion of control | The underestimation of future uncertainty owing to the belief an individual has more control over events than they really do. We believe we have the control to minimize potential problems in our decisions. Displays could include the probability of events determined by the “learning” software. | |
| Selective search for evidence | The willingness to gather facts that support certain conclusions but disregard other facts that support different conclusions. | |
| Inertia | The unwillingness to change thought patterns used in the past in the face of new circumstances. | |
| Choice-supportive bias | The distortion of memories of chosen and rejected options to make the chosen options seem relatively more attractive. | |
| Decision aids | Premature termination of search for evidence | The tendency to accept the first alternative that looks like it might work. |
| Repetition bias | The willingness to believe what we have been told most often and by the greatest number of different sources. | |
| Group think | Peer pressure to conform to the opinions held by the group. | |
| Source credibility bias | Rejection if the individual has a bias against the person, organization, or group to which the person delivering a message belongs: we are inclined to accept a statement by someone we like. Itoh et al. (1999) found that if automation continuously malfunctions, the user’s trust will significantly decrease, and the longer the automation malfunctions, the longer the human distrusts it. On the other hand, occasional malfunctions have less of an effect on trust. The user may not depend on the automation for a difficult task, but this mistrust does not last long. | |
| Incremental decision making and escalating commitment | The view that a decision is a small step in a process that tends to perpetuate a series of similar decisions. | |
| Attribution asymmetry | The tendency to attribute success to individual abilities and talents while attributing failures to bad luck and external factors. We attribute others’ success to good luck, and their failures to their mistakes. | |
| Role fulfillment (self-fulfilling prophecy) | The conformity to the decision making expectations that others have of someone in our position. |
SOURCE: NASA (2014).
- Tribe 1: Security as Enabler. Distinguished by a culture where the security mission has evolved from compliance to commitment, it prioritizes security and gets compliance as a planned side effect. Security is not just a technical problem, all lines of business participate in the security mission.
- Tribe 2: Security as Technology. Distinguished by an approach to security that is not bounded by compliance but has a world view that tends to overemphasize the technical aspects of security challenges. The CISO has not “attained the senior executive gravitas of the Enabler tribe” and gets down in the weeds of problems instead of delegating.
- Tribe 3: Security as Compliance. Distinguished by leveraging compliance requirements to make real security progress, but often historical underinvestment in security lead these firms to continue to underinvest
- Tribe 4: Security as a Cost Center. Distinguished by a security leadership that sits under several levels of executive leadership and is overwhelmed and under-resourced. Security consumes budget, but it never drives budget creation and in some cases has a glass ceiling.
in security even in the face of compliance requirements. Limited resources are being properly allocated and clear progress is made, even while technical debt is accumulating.
To improve safety, utilities have worked to develop a culture of safety over a culture of compliance, which has led to better safety performance. Although safety has been a number-one concern from the earliest development of the electric grid, the transformation from a compliance culture to a safety culture has taken decades of continuous focused efforts. An analogous culture of security and resilience has not yet developed within the grid or other critical infrastructures. Staff operating within a culture of security and resilience can identify and implement controls faster than the existing standards development process can finalize a new standard. A security and resilience mindset would encourage utility staff to learn and innovate, which could lead to better trained grid defenders who can quickly adapt their defenses to detect, respond, and recover from unanticipated events.
One area where internal cultural differences have created tension is the relationship between IT and OT professionals. Because OT systems were initially designed with an assumption of being deployed in an environment of implicit trust, cybersecurity controls were less extensively integrated into the devices, equipment, and network architecture. In addition, many legacy OT power system devices are 30 to 50 years old and were installed when security was not considered. However, many IT-centric security tools and practices are unsuitable in an OT environment without adaptation. For example, vulnerability scanning tools that are commonly used in IT systems could adversely impact the availability/reliability of OT systems. OT systems typically operate 24/7/365, and classic IT security controls, such as account locking or account logout, could render critical devices inaccessible causing a lack of situational awareness or even an unplanned outage. If an IT component is compromised, the typical response is to remove the device and replace it or reconfigure it. For OT systems, removing an OT device may require a planned outage and replacing it could have cascading impacts if it is misconfigured during replacement. A tool designed by IT cybersecurity developers for an IT system that reflects an inherent understanding of how to engage with an adversary may not be appropriate in OT systems, where engaging the adversary is not an acceptable approach and may have severe consequences.
In general, OT security as a field is less mature than IT security and few engineers and control system operators were required to learn IT security principles. Similarly, most IT security professionals were never required to learn OT systems and don’t understand the sensitivities described above. According to a 2019 survey on the state of OT/ICS cybersecurity, “IT takes a leading role in managing corporate security policy and implementing the necessary controls, including into OT’s domain, while OT often controls the budget for safeguarding the ICS. The goals and objectives of these two domains are not well aligned: IT governance and risk management center on uptime and the protection of information and reputation (privacy), while OT focuses on the safety and reliability of cyberphysical processes” (SANS, 2019). In a 2007 whitepaper by Honeywell, the authors described how “corporate IT policies pressure control system engineers to manage their system differently … creating a situation where IT practices conflict with the priorities of a live production environment.” As a result, “There are many teams who detest the involvement of IT owing to negative past experiences. In many organizations, conflicting priorities, a lack of trust, understanding, and limited technical knowledge about each others’ skill set and area of expertise, has produced an uncooperative environment between production and IT.”
This cultural tension has persisted. Ten years later, in a 2017 survey of IT and ICS security practitioners across a variety of industries, more than 60 percent of the respondents said the two largest impediments to advancing IT and ICS technology integration were (1) “Technical integration of legacy and aging ICS technology with modern IT systems”; and (2) “IT staff does not understand ICS operational requirements” (Gregory-Brown, 2017). The 2019 version of the survey did not show much improvement (Filkins and Wylie, 2019). In 2017, 67 percent of the participants considered IT-OT collaboration to be moderate or better, and in 2019, 65 percent of respondents considered the current collaboration level to be moderate or better. Unfortunately, there has been limited cross-functional training provided to IT security practitioners, and OT control engineers and system operators to facilitate a trusted,
respectful, and effective interaction between the different job roles. More focused effort is needed to understand cognitive biases and existing cultural tensions and to build effective cross-functional training programs. There will be an increasing use of ICT in OT systems, and more IT vulnerabilities will be found in the OT domain. Respectful collaboration between IT security professionals and ICS engineers and operators will be essential to resolve the many technical and security challenges that are coming, and to ensure that responsibilities and expectations around security are well defined and implemented.
Another area where culture impacts cybersecurity is information sharing. Defenders of systems continue to face a persistent asymmetry in the speed with which attackers share information compared with defenders. Cybersecurity adversaries share information. The open source community for malicious cybersecurity tools and techniques is very active, and successful methods using existing tools and novel innovations spread quickly. Attackers are rapidly improving their cybersecurity skills. In contrast, the defender community across utilities and in the government is less efficient at sharing information and defensive tools. A review of cybersecurity information sharing literature by Pala and Zhuang (2019) points out “the risk–benefit asymmetry between defenders and attackers is significant … publicly disclosed security breaches of the defenders could easily be exploited by the attackers to detect more vulnerabilities and redesign current/future attacks. In brief, attackers can exploit information-sharing transactions of defenders but not vice versa.”
Reaching Human Limits in Complexity
In the workshop on grid cybersecurity and cyber resiliency that the committee ran in November 2019, participants suggested that we are reaching the limits of human understandability in some of our grid systems. It is an increasing challenge for most utilities to accurately enumerate everything in their systems: physical assets, data, configurations, connectivity, software/hardware/firmware versions, communication links, among many other elements. Only 36 percent of respondents to a 2019 OT/ICS cybersecurity survey (SANS, 2019) claimed that “they have a comprehensive overview of all the elements of control system security for their enterprise or plant.” More than 75 percent of servers and workstations associated with control systems had been identified and inventoried by 64 percent of the respondents, but only 45 percent of respondents said they had identified and inventoried their control system devices, and 44 percent had done so for software applications (SANS, 2019). Workshop participants noted that many of the people operating grid systems do not realize that they cannot describe in detail everything in their systems anymore. In the workshop, Tim Roxey stated, “We are reaching the limits of defensibility mostly because we are reaching the limits of detectability” (NASEM, 2020, p. 23). He argued that a system that cannot be completely enumerated is much more difficult to defend, and that we have entirely too much faith in our ability to defend complex systems that we cannot enumerate.
The technical and economic drivers leading to system complexity in the electric grid and its supporting infrastructures will continue. Systems will not revert to simpler architectures and mechanical components, in part because that would remove many features that improve reliability and would limit the use of new technologies. Alternative methods have been proposed to protect grid systems when the complexity exceeds human capabilities. Using ML/AI and machine-to-machine controls that take humans out-of-the loop is one option (NASEM, 2019; NSTC, 2020). At the other end of the spectrum, identifying pivotal points in grid operations and architectures, and installing backstop safety equipment that responds to the physics of the system and is not digitally controlled can provide redundant controls that prevent operations that are outside of safe specifications regardless of the cause of a disruption.
Finding 6.6: As grid systems continue to become increasingly complex, the resulting cybersecurity landscape is increasingly difficult for even experienced individuals to comprehend and even enumerate, is highly susceptible to the limits of human behavior and physiology, and is increasingly difficult to protect.
Adversaries, Defenders, and Insider Threats
Understanding human behavior can provide key insights into understanding adversary and defender behaviors. This is one area of research where the people and technology pillars are tightly entwined. It is only through forensic analyses of the technical artifacts and traces that are left behind that researchers can find clues to understanding what happened in a cyberattack. This technical information can be combined with an understanding of people to begin to develop threat models of adversary behavior. More research is needed to develop combined cyber-physical simulation and emulation capabilities that can accurately mimic utility systems to explore different adversary capabilities and begin to test defensive responses.
Insider threats are a rising security concern. During the committee’s cyber issues workshop, Brian Harrell, assistant secretary for infrastructure protection at CISA, stated “We are convinced that the next major attack on critical infrastructure is going to have some kind of insider threat component to it, either directly or indirectly” (NASEM, 2020).
Recognized in 2007 in the National Research Council and National Academy of Engineering report Toward a Safer and More Secure Cyberspace (NRC-NAE, 2007), considerable progress has been made since then to understand insider threats. An insider threat is defined as “the potential for an individual who has or had authorized access to an organization’s assets to use their access, either maliciously or unintentionally, to act in a way that could negatively affect the organization” (Costa, 2017). With this definition, an “insider threat” includes people with malicious intent, and threats resulting from cybersecurity incidents caused by negligence or accident. Many insider threats are created by employees who unintentionally take an action that opens up the utility to a security risk as a result of a social engineering attack, a misconfiguration error, or other human errors. By definition, a person must have authorized access to be an insider threat. Perimeter-based security methods, and “static and traditional security models focused on threats from external threat actors … are ineffective against insider threats” (SEI, n.d.).
The U.S. Computer Emergency Readiness Team (CERT) National Insider Threat Center provides resources and training to develop insider threat programs, and maintains a database of more than 3,000 insider threat incidents (SEI, n.d.). For those incidents that involved sabotage, the most commonly targeted assets were computer systems (27 targets, 15.9 percent), servers (20 targets, 11.8 percent), passwords (18 targets, 10.6 percent), files (15 targets, 8.8 percent), and data (15 targets, 8.8 percent) (Miller, 2020).
To combat the insider threat, CISA’s Insider Threat Mitigation Guide recommends that organizations consider proactive and prevention-focused mitigation programs (CISA, 2020b). Four core behavioral principles have been identified by the Defense Personnel and Security Research Center (Jaros, 2018) as associated with insider threats:
- The risk of becoming an insider is not randomly distributed across any population. Certain individuals are more likely to pose threats.
- Insider threats occur in a social context. Certain environments are more likely to facilitate insider threat behavior.
- An individual’s transformation from a trusted insider to a malicious actor is a process, not an event.
- High-impact, low-frequency insider threat behavior correlates with and is preceded by common indicators that can be observed, modeled, and mitigated.
An effective insider threat program will require close coordination between an organization’s leadership, human resources, legal, IT, OT, and security professionals. The organization’s internal culture and leadership will have a significant impact on the success of an insider threat program.
Assessing and Building a Skilled Cybersecurity Workforce
While many organizations understand the need to do vulnerability assessments of systems and technology solutions, and there are security frameworks and guidelines that can be used to assess an organization’s cybersecurity governance and processes, very few organizations do cybersecurity vulnerability assessments of their workforce. Given the high level of security risks associated with human behaviors, more attention is needed to define risks
and identify gaps that need to be addressed by training or other actions. Ani et al. (2018) developed an approach to quantify potential cybersecurity capability aptitudes in the workforce and to identify the least security-capable workforce with the greatest susceptibility to cyberattacks. The method is intended to evaluate knowledge and skills to reveal variations in capability and over- or underperformance in security capacity.
One of the major challenges for the electric sector is the aging population of engineers. These individuals have worked on the existing systems for decades and understand them well. As these older systems are being replaced with new technology that is digitally based, the historical knowledge resident in existing employees must be translated and tailored to apply to new technologies when applicable. Knowledge capture is a challenge across the industry, not just for cybersecurity.
As mentioned in Chapter 5, there is an extreme shortage in the cybersecurity workforce. A better understanding of what motivates people to enter the ICS cybersecurity workforce, and what is needed to retain cybersecurity workers in utilities, is needed to inform training and recruitment programs. Gartner, an international research and advisory firm, suggests that traditional cybersecurity recruiting practices have proven inadequate, and that managers need to adjust their expectations in the short term, be prepared to outsource operational functions, and train for missing skills in current staff. Respondents in a recent Gartner gender diversity survey pointed to culture and recruiting issues that further limit the available candidate pool (Olyaei et al., 2018). Understanding the human dimension of workforce recruitment and retention will be critical to utilities competing for a scarce talent pool of cybersecurity professionals.
Finding 6.7: The U.S. workforce faces a critical shortage in cybersecurity skills, particularly for ICS in utilities, compared to the workforce needed to meet the demands of secure electric control systems over the next 30 years.
Recommendation 6.3: Congress should appropriate funds to the Department of Energy (DOE), Department of Homeland Security (DHS), and Department of Labor (DOL) to establish programs that provide cybersecurity training specifically for the current and future workforce of engineers, operators, technicians, and information technology (IT) and operational technology (OT) positions associated with the real-time operation of electric grid systems.
ADVANCING CYBER RESILIENCE THROUGH PROCESSES
While people are often the vehicle for implementing a decision or action, processes govern the context in which decisions are made. Processes include everything from written and unwritten procedures and board approved policies, to projects, programs, rules, standards, regulations, and laws. In the end, people develop processes, so processes are inherently affected by the same cognitive biases and human limitations. Processes are also impacted by the diverse technologies, architectures and business models implemented across the country. There will be no one cybersecurity solution that will fit all utilities, let alone all stakeholders in the electric grid. Below are some key topics affecting processes that will be important to address in the future grid to achieve cyber resilience: motivating cybersecurity investments; cybersecurity information sharing; impact of market forces and supply chain on cybersecurity; administrative overlaps, interdependencies and national security; cybersecurity insurance; and cybersecurity standards, guidelines, and frameworks.
Motivating Cybersecurity Investments
Cybersecurity is considered important by owners and operators of grid assets. In a recent survey, 85 percent of 527 utility executives and professional respondents from the United States and Canada indicated that physical and/or cyber grid security was “important” or “very important,” putting that topic at the top of the list for the third straight year (Utility Dive, 2019). Navigant Research estimates that the global market for energy IT and cybersecurity software and services is expected to surpass $19 billion and will reach $32 billion by 2028 (Navigant Research, 2020). The data suggests utilities in general are prioritizing investments in cybersecurity, but verbal support needs
to translate into actual resource allocations and those decisions will depend on the utility’s cybersecurity culture and leadership priorities.
The authors of Toward a Safer and More Secure Cyberspace (NRC, 2007) identified two reasons why it is difficult to motivate investments that still apply today: conflicting interests and incentives among the many actors that affect cybersecurity; and difficulties in assessing cybersecurity risks and the benefits of countermeasures. The authors posited that having more accurate information about vulnerabilities could help and they recommended the use of bug bounties to identify vulnerabilities. The mechanisms identified for incentivizing behavioral change included insurance, standards, government procurement, government cybersecurity practices, tax policy, public recognition, regulation and penalties, and using liability as a tool to force vendors and users to improve their practices.
Three examples of mechanisms that could motivate investments in cybersecurity were identified during the committee’s November 2019 cybersecurity workshop: more detailed information on current cybersecurity threats; understanding the specific impacts an outage resulting from a cyberattack could have on a utility; and financial penalties for noncompliance with regulations or standards (NASEM, 2020). According to Joe McClelland, Director of the FERC Office of Energy Infrastructure Security, one of the motivations for cybersecurity investment is a clear understanding of the cyber threats facing the energy sector. “When we have shown those threats and vulnerabilities—we have never had anyone say I am not doing that. So it is a matter of information” (NASEM, 2020).
Information on the costs of potential impacts of cybersecurity incidents can help CEOs prioritize the risk against other threats. The American Public Power Association (Public Power) created a “Ukraine” scenario that allows their members to simulate an outage on their system similar to the 2015 outage in Ukraine (Sullivan and Kamensky, 2017). The Interruption Cost Estimate (ICE) calculator developed by Public Power gives a utility an estimate for what the cost of such an outage would be for their system. “That gives them impactful data that now they can go to the city council, the mayor, the alderman, whoever is running that utility and say this is what it’s going to cost this community if we are down for eight hours,” explained Michael Hyland, Senior Vice President of Engineering Services at Public Power (NASEM, 2020).
There are very few metrics available for utilities to quantify the benefits of cybersecurity investments. In one example, a 2018 study funded by the European Commission and the Horizon 2020 Program calculated estimated costs of cybercrimes and benefits associated with selected cybersecurity products and solutions for each of the European Union’s 28 countries. The results were calculated in terms of the net present value and “showed that significant cost savings can be achieved if there is an adoption of the cybersecurity products and solutions that are available in the market” (SAINT Consortium, 2018). Though the study is focused on costs associated with IT crimes, and IT solutions and products, it does provide an example of a financial return on investment.
Some aspects of cyber-resilience may initially add costs to the system, such as adding redundant components, or backstops to build a resilient architecture from insecure components. Other cyber-resilience investments, such as operator training, may reduce costs owing to improved operations. Some systemic changes, such as improved information sharing, may be at least cost-neutral when first implemented. Another barrier may be current rate structures and business models for utilities that do not adequately fund cybersecurity investments.
The NERC Critical Infrastructure Protection (CIP) standards utilize financial penalties as a motivating factor. In 2019 NERC filed a Notice of Penalty and Settlement Agreement with FERC for a record $10 million fine against Duke Energy Corp for 127 separate violations of the CIP standards occurring between 2015 and 2018 (NERC, 2019b; Sobczak and Behr, 2019). There is currently insufficient data to evaluate whether this significant fine is resulting in changes in behavior.
In a study of the effects of security investments in health care, where legislation mandates data breach disclosures, researchers found proactive security investments were associated with lower security failure rates and were more cost-effective. When external pressures were included in the analysis the researchers found the effect of proactive investments on security performance decreased. They concluded that “proactive investments, voluntarily made, have more impact than those involuntarily made” (Kwon and Johnson, 2014). In June 2020, FERC recognized that existing federally mandated cybersecurity reliability standards “have certain limitations.” FERC proposed new voluntary mechanisms to incentivize utilities to “be more agile in monitoring and responding to new and (un)anticipated cybersecurity threats, to identify and respond to a wider range of threats, and to address threats with comprehensive and more effective solutions” (FERC, 2020). The voluntary improvements, if effective, could become the basis for future mandatory requirements.
Cybersecurity Information Sharing
Cybersecurity information sharing to help industry understand threats has been repeatedly recognized as a challenge (NASEM, 2017). As noted above in the section on cybersecurity culture, information sharing is an attribute of attackers, and less-so of defenders.
Technology can make it faster and easier for utilities to share information, but the primary barriers that limit effective information sharing are not technical. Pala and Zhuang (2019) identified seven barriers to sharing: privacy and civil liberties; liability; loss of trust; loss of reputation; attracting more attacks; costs of information leakage; and costs of sharing operations. They divide the type of information that is shared into cyber-indicators, such as incidents, vulnerabilities, and threats, and defensive measures. Technical indicators, such as IP addresses and file hashes, are considered to pose a lower risk to privacy and an organization’s market value, whereas contextual threat intelligence, such as exploited targets, incident details, and countermeasures, have a greater potential for privacy violations and economic damage. In their review of 83 papers, they observed a lack of analytical models that studied the types of information that should be shared given liability and information-leakage concerns. And while they found many studies that analyzed the regulator role, what they called the “promotive role,” they found that providing financial incentives and subsidies was generally ignored. They concluded that “the necessity, feasibility, and effectiveness of government-based incentives should be investigated to better understand the trade-offs of government incentives.”
CRISP, a voluntary data sharing and analysis platform created by DOE and owned and operated by the E-ISAC since 2014, shares threat information among stakeholders for an annual fee. The larger utilities have paid to participate and those utilities cover roughly 75 percent of the U.S. electricity customers. The program sends information collected from participating utilities to government analysts that can access other relevant information that would not normally be available to the private sector and use that information to enhance their analysis of the industry’s threat information. Specific results are sent to program subscribers and generalized results are shared with all E-ISAC members at a later date.
In the Unclassified Joint Report on the Implementation of the Cybersecurity Information Sharing Act of 2015 by the Office of the Inspector General of the Intelligence Community, the authors concluded that within the federal agencies there had been improved sharing of cyber threat indicators and defensive measures from 2017 to 2019, and that efforts were under way to expand information accessibility. The report identified four barriers that hindered sharing of cyber threat indicators and defensive measures:
- Restrictive security classifications limit cyber threat information from being widely shared.
- Inability of machines to communicate with each other reduces the speed at which cyber threat information sharing occurs.
- Uncertainty about the protection from liability provided by the Statute impacts the willingness of private sector entities to share cyber threat information.
- Challenges with the threat intelligence platform that deter its use including “low quality cyber threat indicators require research,” and “lack of context included with the cyber threat indicators to allow the information to be actionable.” In June 2019, only four agencies and six nonfederal entities were using the platform.
It is important that appropriate information sharing and learning is facilitated between the government and the private sector. The government holds security-level information that is of value to industry to understand and integrate into their security decisions, and the private sector owns and operates the systems necessary for national defense operations. The private sector needs greater access to relevant intelligence information, and the government needs access to more data and situational awareness on what is happening in the power sector and other interdependent critical infrastructures to better assess threats. As the report by the Office of the Inspector General of the Intelligence Community found, restrictive security classifications are limiting information sharing, which can create risks resulting from limited situational awareness. Possible solutions could include the following: (1) these vulnerabilities are accepted; (2) more information is shared rather than classified; (3) security clearances
are expanded for relevant electric grid personnel; and (4) more classified briefings are held with asset owners and operators. Industry collective decision making must be informed to the greatest extent possible by a comprehensive situational understanding of the threats (including the capabilities of adversaries and the likelihood of various potential attack scenarios), and their impacts on deployed ICT and OT components.
More work is needed to address the barriers that limit effective information sharing. The asymmetric nature of information sharing and skills development between attackers and defenders amplifies the urgency in finding solutions to facilitate information sharing. The electricity industry is capable of managing a risk portfolio calculus within individual organizations, however current programs are not sufficient to fully incentivize information sharing among private sector organizations, including the electricity industry and its vendors, and the government. The seven barriers identified by Pala and Zhuang (2019), including the disincentive created by the potential of enforcement actions by NERC or other federal agencies need to be explored, and examples of other models where information sharing is more successful need to tested.
Recommendation 6.4: Congress should instruct the Department of Energy (DOE) to create a joint task force that includes the Federal Energy Regulatory Commission (FERC), the North American Electric Reliability Corporation (NERC), the Electricity Information Sharing and Analysis Center (E-ISAC), and the electric industry to identify new legislative authority needed for obtaining early warnings associated with self-reporting security conditions that may potentially disrupt the electric power grid. A mechanism analogous to the independent nonregulatory Aviation Safety Reporting System (ASRS) operated through the National Aeronautics and Space Administration (NASA) is needed to support anonymous reporting and quickly assess and inform relevant decision makers. The intention would be that security audit findings would not incur financial penalties to the reporting entity if the violation was (1) within the scope of a self-reported concern; (2) within the time frame of a correction action timeline; and (3) did not result in any customer outages. (See Recommendation 3.1 for other tasks that would be assigned to this joint task force.)
Recommendation 6.5: Pertinent information about known and emerging advanced persistent foreign and domestic cybersecurity threats should be communicated to industry stakeholders in a proactive, timely, and effective manner. Department of Energy (DOE), Department of Homeland Security (DHS), Department of Defense) DoD, their partners in the intelligence community, and relevant Information Sharing and Analysis Centers (ISACs), should, in coordination with industry, collectively identify parameters defining the most relevant information to share, and create a process for securely releasing information to industry.
Impact of Market Forces and Supply Chain on Cybersecurity
Innovations in technology, consumer demands, international trade, and other changes in the grid supply chain are radically shifting the security landscape of products and services. The Government Accountability Office identified five categories of cybersecurity threats federal agencies face in their supply chain: installation of intentionally harmful hardware or software; installation of counterfeit hardware or software; failure or disruption in the production or distribution of critical products; reliance on malicious or unqualified service providers for the performance of technical services; and installation of hardware or software containing unintentional vulnerabilities, such as defective code (Wilshusen, 2018). Key factors the authors identified that can impact supply chain cybersecurity are pressures to quickly commercialize new technologies without adequate cyber protections; the increasing use of cloud computing putting important security assets offsite; and increasingly global sourcing for components. It is likely that other consumers face similar threats in their supply chains.
The market incentivizes a “first to market” ecosystem, and that pressure is reflected in a “fail fast” product development philosophy prioritizing speed over security (NRC, 2007). This is particularly visible in the release of IoT products. Bieler (2019) identified two market failures in IoT electronics: “a market for lemons induced by consumers’ limited cybersecurity knowledge, and a tragedy of the commons created by the fact that these devices
externalize their major harms.” He suggested that the existing regulatory ecosystem was not sufficient to counterbalance the economic incentives that promote poor cybersecurity in IoT. Extensive reuse of code that has known vulnerabilities is another market-driven behavior resulting in cybersecurity risks in grid ICT. Sometimes it is only when an exploitable vulnerability is publicly disclosed that vendors are motivated to address the vulnerability and even that may not be sufficient motivation for some vendors.
Where once utilities could own and control all of the assets that stored and moved their data, more vendors are taking advantage of the economies of cloud computing and decreasing the production of equipment used on premises by an individual utility. As a result, the physical assets a utility would purchase to store and manage data on premises are getting harder to find. Concurrently, Palo Alto Networks found significant vulnerabilities from developers failing to adequately monitor and enforce cloud configurations, resulting in exposed ports and use of outdated versions of communication protocols (Unit 42 by Palo Alto Networks, 2020).
As the reliance of grid operations on cyber infrastructure grows, the global and multifaceted nature of the marketplace for components needed to implement that infrastructure raises concerns over the introduction of potentially untrustworthy components. It is important that supply chain rules are established that allow for the verification of the provenance of grid components and their compliance with security standards to mitigate cyberattacks and other security breaches enabled by components either deliberately placed by malevolent actors or that can be exploited owing to inherent security weaknesses.
Like many other consumers, utilities face limits on what they can expect a vendor to do in cybersecurity. In cases where sections of a utility’s system are dominated by equipment from one vendor, it is less likely that the utility would switch from that vendor to another vendor and replace its entire system. This barrier to vendor switching can limit the leverage a utility has to require a vendor to implement stronger cybersecurity controls.
Even if the grid is designed with no critical components, supply chain vulnerabilities diminish resilience for the grid, and must be addressed before an attack occurs. Supply chain vulnerabilities are being addressed by the private sector, but the government can influence what is addressed and how. In industry, this could include evaluating sources of components for their cybersecurity, sourcing from multiple suppliers for a given component to have diversity in cyber vulnerabilities, or stockpiling supplies of certain components, such as large transformers, to be able to recover quickly after a cyberattack. The federal government could publish cybersecurity guidelines for vendors and purchasers of equipment, or mandate that certain practices be followed in procurement, integration, and use of products through regulations. As discussed below, the standards development process is slow and imperfect but could provide another option to manage supply chain risks in the light of the growing and expanding set of vendors.
Finding 6.8: The market incentivizes vendors to focus on the short-term goal of quickly developing and delivering products, often without adequate testing and refinement, rather than prioritizing the comprehensive security of those products.
Finding 6.9: In an increasingly diverse vendor ecosystem, lack of full control of supply chain critical components and technologies is a growing concern for grid cybersecurity.
Recommendation 6.6: Congress should give regulatory authority to the Department of Homeland Security (DHS), which should work with the sector-specific agencies and other relevant government and industry stakeholders, to establish cybersecurity regulations across all critical infrastructure sectors for equipment, devices, and software used in those sectors. The goal of these regulations is to specify standards that vendors will implement to develop products with superior cybersecurity attributes.
Who Owns Cybersecurity Risk: Administrative Overlaps, Interdependencies, and National Security
Grid reliability is increasingly dependent on sectors and stakeholders outside the electricity system. At the same time, nation-state attackers and APTs are threatening the power system. Caught between these national-scale pressures, asset owners and operators are challenged to maintain a safe and secure, clean and sustainable, affordable and equitable, and reliable and resilient grid. The answer to who owns cybersecurity risk is not easily resolved.
More than 12 federal agencies have cybersecurity responsibilities and are overseen by at least 9 congressional committees and 22 subcommittees (CRS, 2017a). (See Figure 6.4, Table 6.4, and Annex Table 6.A.1.) This fragmented division of responsibilities in Congress is amplified in fragmented authorities and expectations assigned to DOE, DHS, NIST, DoD, NSF, FTC, DOT, DOJ, SEC, NSA, and the intelligence community.
As of 2020, DHS’s Information Sharing and Analysis Organizations’ (ISAO) Standards Organization listed more than 60 federal cybersecurity government programs and services, many of which are relevant to grid security efforts (ISAO Standards Organization, 2020). The Networking and Information Technology Research and Development (NITRD) Program coordinates activities of 23 federal agencies organized into 12 Interagency Working Groups, that invest approximately $5 billion annually in programs that fund research and development in advanced technology areas that are relevant to the grid, including IT computing, networking, software, and cyber-physical systems (NITRD, 2019a,b).
In the background of this diversity of domestic federal agencies, the intelligence community plays a critical role in collecting, curating, and analyzing information needed to understand the nation-state and APT cybersecurity threat landscape.
Currently, DOE, FERC, DHS, and DOT have statutory authority to regulate cybersecurity for energy infrastructure under their relative jurisdictions. DOE is the Sector Specific Agency with primary responsibility for grid and oil and natural gas cybersecurity but not pipeline security. DOE is also the designated lead federal coordinator to facilitate the reestablishment of damaged energy systems and components for incidents requiring a coordinated federal response as Emergency Support Function #12 (ESF-12) under the National Response Framework (NRF).
FERC has authority over the reliability of the bulk power grid, and can request and approve mandatory CIP standards proposed by NERC, but it does not have authority to create standards or to regulate pipeline security. DHS is the lead agency for pipeline security, and the Transportation Security Administration (TSA), under DHS, has primary responsibility and regulatory authority for the security of natural gas and hazardous liquid (e.g., oil, refined products, and carbon dioxide) pipelines in the United States. The Department of Transportation (DOT) regulates the safety of oil and natural gas pipelines and the pipeline safety program is administered by the Pipeline and Hazardous Materials Safety Administration (PHMSA) under DOT.
The CIP standards set a baseline of cybersecurity practices for the bulk electric system. Other critical infrastructures that can impact grid reliability without such standards are softer targets for adversaries and are therefore a risk to the grid. The stronger the interdependent connection between grid reliability and other infrastructures, the more important it is that those stakeholders manage their cybersecurity risks. For example, the natural gas sector, and in particular, the natural gas interstate transmission and local distribution infrastructure is an important contributor to electric grid reliability. And commercial communications carriers whose systems are used by the electric grid can also impact reliability. Though large utilities generally own and operate their own private networks for operation critical communications, they frequently rely on commercial carriers for their enterprise network. Smaller utilities rely almost entirely on commercial carriers. It is unrealistic to expect power system utilities to maintain reliability if interdependent infrastructure owners experience a significant cybersecurity incident, but it is not clear what level of responsibility and accountability the natural gas or commercial communications industries should carry for managing their own cybersecurity risks.
Reliability risks to the grid are expected to be exacerbated as the grid relies more heavily on 5G and subsequent generations of cellular technology, and on Internet-of-Things (IoT) technologies. Greater adoption of these technologies for demand-side and other distributed grid management functions are anticipated as the grid evolves. Responsibilities for mitigating cybersecurity risks that can impact the commercial carriers, or the stakeholders using smart devices, DER, or enabling transactions are not clearly assigned.
IoT device owners and aggregators that can impact load balance via controlled and coordinated demand operation do not have any requirements for communications with the relevant distribution utility, including how to secure those communications (Soltan, 2018). Similar issues will arises for cloud computing dependencies and reliability. As grid management becomes much more data-intensive and reliant on ML/AI and other data analytics, dependencies on communications carriers and the cloud providers they support is anticipated to increase.
In terms of national defense, focused assessments of our critical defense energy infrastructure are revealing the extensive dependence of the nation’s defense infrastructure on the private sector, particularly the energy sector.
According to Andres and Breetz (2011), “domestic military installations receive 99 percent of their electricity from the civilian power grid,” and “even with massive investment in efficiency and renewables, most bases would not be able to function for more than a few days after the civilian grid went offline.”
The dependence of military and critical infrastructure civilian facilities on civilian-owned power systems creates a special situation in which the object of a nation-state attack, and the defenders, may be in the private sector, but the impact of an attack may be felt by the public, at a local, regional or national scale. Protecting these systems against attacks by nation-state adversaries presents a serious jurisdictional and financial challenge since the boundaries of government and private-sector responsibility, including cost recovery, are not clear in in this situation.
The boundaries clarifying what aspects of national defense against cyberattacks are the responsibility of the government, what aspects are the responsibility of industry, and who should make the needed investments, are blurring. At the individual utility scale, ownership of cybersecurity risk is treated as an end point reliability issue. From a workforce perspective, most employees at utilities and generation facilities did not sign on to work in an active war zone and did not train for the high level of cyber skills to defend against sophisticated adversaries in their systems.
Existing electric industry business priorities may not align perfectly with the allocation of resources needed to meet national security objectives. Individual owners or operators may not be well prepared to respond to threats from nation-states. The extreme shortage of cybersecurity professionals experienced in ICS cybersecurity translates into a lack of workers trained to do root cause analyses or conduct the active threat hunting needed to detect, respond, and recover from a sophisticated adversarial attack.
While owners and operators of the electric grid are on the front lines defending against ongoing nation state and criminal attackers who have an intent to compromise the integrity of the grid or its business operations, the business case for addressing cyber threats often does not provide sufficient motivation to secure assets at the level that addresses the risks to national defense (NRC, 2014). Civil liability may be a means for incentivizing the users of IT and OT products and services to pay increased attention to cybersecurity. However, there are still few incentives that result in any organizations accepting cybersecurity risks beyond their own border.
TABLE 6.4 Laws, Presidential Directives, and Executive Orders Related to Grid Cybersecurity
| Date | Event | Description |
|---|---|---|
| 1998 | Presidential Decision Directive 63 (PPD-63) | First executive-level action to establish a national policy for critical infrastructure protection from physical and cyber threats. The U.S. Department of Energy (DOE) was formally assigned responsibility for the electric grid, and oil and natural gas infrastructure cybersecurity. |
| 2003 | Homeland Security Presidential Directive 7 (HSPD-7) | Superseded PPD-63, assigning DOE as the Sector Specific Agency (SSA) for the electric power, oil and natural gas subsectors, and the Department of Homeland Security (DHS) as the SSA for pipelines. |
| 2007 | Energy Independence and Security Act of 2007 (EISA) | Created a national policy for grid: Modernization, and outlined cybersecurity requirements for the smart grid, including increased use of digital information and control technology to improve reliability, security, and efficiency; and the dynamic optimization of grid operations and resources with full cybersecurity. |
| 2011 | Presidential Policy Directive 8 (PPD-8) | Built on the National Response Framework (NRF), and designated DOE as the lead federal coordinator to facilitate the reestablishment of damaged energy systems and components for incidents requiring a coordinated federal response as Emergency Support Function #12 (ESF-12). |
| 2013 | Executive Order 13636 (EO 13636) | Directed NIST to develop a cybersecurity framework consisting of voluntary standards, methodologies, procedures, and processes to address cyber risks, and Section 9 directed all SSAs to designate critical infrastructure at greatest risk within each sector. |
| 2013 | Presidential Policy Directive 21 (PPD-21) | Superseded HSPD-7; retained DOE as the SSA for electric power, oil and natural gas, and DHS was named co-chair with the U.S. Department of Transportation for pipelines. PPD-21 also directed DOE to serve as the day-to-day federal interface for energy infrastructure security and resilience; carrying out incident coordination; and providing technical assistance and consultations to the sector to identify vulnerabilities and help prevent or mitigate the effects of incidents. |
| 2015 | Fixing America’s Surface Transportation Act of 2015 (FAST Act; P.L. 114-94) | Directed DOE to collaborate with DHS and electric grid owners and operators to prioritize activity, incident management, and vulnerability identification for the electricity subsector, and gave DOE new authority to order electric utilities and NERC to implement emergency security actions. |
| 2016 | Presidential Policy Directive 41 (PPD-41) United States Cyber Incident Coordination | Outlines three concurrent lines of effort to respond to any cyber incident involving government or private-sector entities: threat response; asset response; and intelligence support and related activities. The Office of Electricity, in implementing DOE’s role as the SSA for the energy sector, will coordinate federal government efforts to understand the potential business or operational impact of any cyber incident on critical infrastructure in the energy sector. If a significant incident directly impacts DOE operations, DOE OCIO will initiate a fourth line of effort to directly address the cyber-attack. In addition, DOE will participate in national policy and operational coordination efforts for significant cyber incidents affecting the energy sector. |
| 2017 | Executive Order 13800 (E.O. 13800) | Required DOE and DHS to assess U.S. readiness to managing the consequences of a prolonged power outage as a result of a significant cyber incident. |
| 2020 | Executive Order 13920 (E.O. 13920) | President “declared a national emergency with respect to the threat” to the U.S. bulk-power system in E.O. 13920 is focused on protecting “the security, integrity, and reliability of bulk-power system electric equipment used in the United States” from “foreign adversaries.” |
Finding 6.10: The electric grid is fundamentally dependent on other infrastructures, especially commercial and private communications systems and enterprise information technologies. Modern industrial control systems require a combination of hardware, firmware, and software (often including commodity operating systems), and a combination of communications technologies integrated through a complex networking architecture. Therefore, failures (including cyberattack-induced failures) in other infrastructures could have significant effects on the proper operation of the grid.
Recommendation 6.7: The Department of Energy (DOE) should partner with relevant agencies to develop a joint utility and industry-driven analysis of electric system interdependencies with connected
infrastructure (e.g., communications networks, natural gas system) and provide guidelines on how to address the reliability and security vulnerabilities from such interdependencies.
Finding 6.11: There is an insufficient understanding of roles and authorities, too many of which remain unresolved between government agencies, between the government and the private sector, and for cybersecurity issues that cut across industries and critical infrastructures.
Recommendation 6.8: Because investor-owned utilities, coops, and municipals cannot, on their own, justify covering the cost of implementing protections of the power system against electromagnetic pulse (EMP) or major state-sponsored cyber and other attacks, Congress should directly address this issue and initiate a process to develop a solution for how to cover the costs of implementing appropriate protections.
Cybersecurity Insurance
Insurance is a common tool for managing risk. Levite et al. (2018) identified six core cyber risk mitigation functions the insurance industry could perform: (1) engineering risks, (2) channeling corporate risk, (3) managing systemic risks, (4) harnessing collective security insights, (5) shaping broader risk trends, and (6) harmonizing risk-related standards and practices internationally. The paper identified at least nine types of insurance policies designed to cover the losses associated with a cybersecurity incident (Levite et al., 2018).
At a 2019 meeting in Paris, SCOR Chairman and Chief Executive Officer Denis Kessler said cyber risk could exceed $600 billion per year “in the worst-case scenario.” This “would dwarf” the yearly cost of natural catastrophes, which he said is about $230 billion (Fouquet and Horobin, 2019). The Insurance Journal reported in early 2020 that “U.S. insurers are ramping up cyber-insurance rates by as much as 25% and trying to curb exposure to vulnerable customers after a surge of costly claims” following a year of ransomware attacks (Barlyn, 2020). In 2019, the same journal reported that the “cost to businesses and insurers of a single global ransomware attack could hit $193 billion, with 86% of that uninsured” (Griffin et al., 2019). In the meantime, the U.S. courts are working through whether the NotPetya attack that crippled Merck in 2017, resulting in $1.3 billion in claimed losses, was an act of war and should be excluded from coverage (Griffin et al., 2019).
The future of cybersecurity insurance is unclear. Unlike other insurance products, which have been through years and years of court proceedings resulting in more mature risk and cost estimates, the cybersecurity insurance industry is relatively new. The majority of cyber insurance products on the domestic market are focused on IT risks, not ICS risks. To accurately assess a utility’s security posture takes both time and acceptable methods to collect the necessary data. While the primary role of the insurance industry is to understand and manage risk, there are no incentives for insurance companies to invest the time to identify a method to assess risks in this area. The market currently has more demand than product. Insurance might be a reasonable approach for a utility worried about its exposure, however, it is almost certainly not a reasonable approach to address the national security or grid resilience issues addressed in the previous section.
Cybersecurity Standards, Guidelines, and Frameworks
As attention to grid cybersecurity increases, there has been an increase in cybersecurity standards, guidelines and frameworks. Many organizations are creating cybersecurity standards, including federal and state agencies and governments; manufacturers and vendors; certification and testing companies; professional organizations; international and domestic standards development organizations; and the broader security community. Historically, these standards have focused on IT systems and not OT systems. Some are general, some technical, and only a few are mandatory. (See Annex Table 6.A.3 for examples of grid-related cybersecurity standards, guidelines, and frameworks.) Cybersecurity standards have played a significant role in grid cybersecurity but, in general, they only establish a baseline security level. Some of the challenges with standards include the following: (1) the standards development process is inherently slow and cannot keep pace with rapidly changing attack methods or the deploy-
ment of new technologies; (2) standards can be biased by the influence of stakeholders who invest more time and resources in the development process; and (3) proprietary or expensive standards may have only limited use. One unintended consequence of mandatory standards is an incentive to address “the minimum (cost competitive) set of features to achieve compliance, without a focus on achieving comprehensive and effective cybersecurity” (Johnson, 2017).
No standard is applied in isolation. The integration of components into a system frequently requires combining components with different networking, communications, and security requirements that may be in conflict, resulting in technological incompatibility or legal noncompliance. When standards and protocols are not interoperable—that is, they do not enable networks or components to easily, securely, and effectively exchange and use information across vendors and technologies—security vulnerabilities can be created during the integration, installation, and configuration process in an effort to ensure that the components interact smoothly. When system and component protocols and standards are interoperable, it can decrease implementation costs and increase security and reliability efficiencies. Cybersecurity tools used by security practices face similar interoperability challenges. According to the Open Cybersecurity Alliance (OCA) “Enterprise cybersecurity teams use on average 25 to 49 different security tools” sourced from different vendors. The Alliance is working to “develop and promote sets of common code, patterns, and practices so that cybersecurity tools can share data” to enable products that support the cybersecurity ecosystem “to seamlessly interoperate with one another” (OCA, n.d.).
This section is not intended to provide a comprehensive overview of standards relevant to grid cybersecurity but some key examples are highlighted. A survey of the most important regulations, standards, and best practices used by utilities is shown in Table 6.5.
The voluntary NIST Framework for Improving Critical Infrastructure Cybersecurity Version 1.1 (Cybersecurity Framework) provides standards, guidelines, and best practices to manage cybersecurity risk that are organized around five core functions: identify, protect, detect, respond, and recover (NIST, 2018b). It provides the basis for many derivative guidelines and standards, and is used by many organizations to assess and prioritize their cybersecurity efforts” (Johnson, 2017). In the 2019 SANS State of OT/ICS Cybersecurity Survey the NIST Cybersecurity Framework was ranked first in the top 10 regulations, standards and best practices being used by utilities (Table 6.5). According to Gartner research, in 2015, 30 percent of U.S. organizations in 16 critical industries and 20 states were using the NIST Cybersecurity Framework (NIST, 2017).
The NERC CIP standards are a prescriptive standard, as opposed to a performance-based standard, and are one of the most widely recognized cybersecurity standards impacting the grid. The CIP Reliability Standards are mandatory and enforceable and “require certain users, owners, and operators of the Bulk-Power System to comply
TABLE 6.5 Survey Responses Ranking the Top 10 Regulations, Standards, and Best Practices Used by Utilities as of 2019
| Rank | Regulation | % Response |
|---|---|---|
| 1 | NIST CSF (Cybersecurity Framework) | 38.1 |
| 2 | ISO 27000 series | 32.0 |
| 3 | NIST 800-53 | 31.4 |
| 4 | NIST 800-82 | 30.9 |
| 5 | ISA/IEC 62443 | 30.4 |
| 6 | CIS Critical Security Controls | 29.9 |
| 7 | NERC CIP | 23.7 |
| 8 | GDPR | 15.5 |
| 9 | C2M2 (Cybersecurity Capability Maturity Model) | 10.3 |
| 10 | NIS Directive (EU) | 8.3 |
SOURCE: B. Filkins and D. Wylie, 2019, “SANS 2019 State of OT/ICS Cybersecurity Survey,” June, https://www.sans.org/reading-room/whitepapers/analyst/membership/38995.
with specific requirements to safeguard critical cyber assets” (122 FERC ¶ 61,040). There is general agreement that the CIP standards successfully resulted in widespread implementation of baseline cybersecurity requirements to protect critical cyber assets in the bulk power system. The standards were phased in, so that owners, operators and vendors had time to implement changes effectively. And the compliance regime produced relationships, collaborations and a common dialogue between asset owners and vendors. The CIP standards continue to play an important role in reducing vulnerabilities. Some of the limitations with the CIP standards raised by participates in the committee’s cyber workshop (NASEM, 2020) include the following:
- The standards only apply to the bulk electricity system. The grid of the future is likely to have a much broader range of stakeholders that could impact grid cybersecurity and reliability, including the distribution infrastructure; commercial product developers and vendors, such as solar, wind, energy storage and other distributed energy and IoT manufacturers; the broader electric grid supply chain; aggregators; integrators; communications carriers; government entities that collect and manage utility cybersecurity data; and the end-of-the-line prosumers who invest in grid connected devices that rely on ICT.
- The CIP standards take an asset-centric risk-based approach to security that may not fully recognize and address the rapidly expanding interconnected nature of cyber systems.
- The CIP standards regime, by the nature of its implementation and penalties, has resulted in a culture of compliance across the industry. The CIP standards incentivize financial investments and decisions to meet audit requirements. In some cases, the audit requirements have unintentionally made it more difficult for asset owners and operators to innovate and take actions or utilize technologies that might improve security (NASEM, 2020). In other cases, the cost to reach compliance becomes an upper limit to investments in cybersecurity, and additional efforts, even if they would increase security, are not supported by budget allocations.
- Similar to challenges faced by other standards, the standards process is slower than the speed at which attackers are developing new TTPs.
- The lack of widely accepted and tested metrics that accurately measure cybersecurity limits the ability of the standard to create auditable processes that predictably result in increased security.
- The standards do not provide sufficient flexibility to allow utilities to maximize the use of security controls that are uniquely appropriate for each system; they require compliant technology and newer technology that is more efficient or cutting edge may not be compliant.
- Standardizing compliance plans across the bulk electric system might increase risks to the grid’s overall cyber posture. Marc Child explained “we have developed maybe inadvertently a model where all of the utilities are starting to look alike from a cyber defense posture perspective. … [for] example … the jump host … a great security technology, but the NERC CIP standard says every utility has to have one.” (NASEM, 2020).
Solutions proposed by workshop participants included finding a way to shift the role of the CIP auditor from being an adversary, to creating a culture of cooperation where the auditor is a partner with the utility to identify vulnerabilities and solutions, and moving from financial penalties to binding recommendations for improvement (NASEM, 2020).
NIST’s Special Publication (SP) 800 series is a collection of guidelines, recommendations, and technical specifications. NIST SP 800-53 Rev. 5 Security and Privacy Controls for Information Systems and Organizations, and NIST SP 800-171 Rev. 2 Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations, are mandatory security and privacy information system standards for all federal agencies except national security systems (Joint Task Force Interagency Working Group, 2020; Ross et al., 2021). DoD recently created a Cybersecurity Maturity Model Certification (CMMC) that will be required for all prime contractors and subcontractors as a verification mechanism ensuring appropriate levels of cybersecurity practices and processes are in place to protect controlled unclassified information (CUI). The CMMC has five levels. Level 3 includes the 110 security requirements specified in NIST SP 800-171 rev. 1, and additional practices and processes from NIST SP 800-53, the Aerospace Industries Association (AIA) National Aerospace Standard (NAS) 9933 “Critical Secu-
rity Controls for Effective Capability in Cyber Defense,” and the Computer Emergency Response Team (CERT) Resilience Management Model (RMM) v1.2. It is anticipated that more than 300,000 DoD defense industrial base (DIB) contractors will be required to comply with the CMMC cybersecurity standards (Gray and Freese, 2020), including utilities that provide power to military installations under a utility privatization contract. There have been discussions to extend the CMMC requirement beyond the DIB which could require all electric utilities providing power to a military facility to comply with the CMMC.
DOE’s C2M2 was designed as a self-evaluation toolkit to help organizations of all sectors, types, and sizes assess their cybersecurity programs and make improvements to strengthen their operational resilience. It focuses on the implementation and management of cybersecurity practices associated with data, and IT and OT assets and the environments in which they operate. The model can be used to:
- Strengthen an organization’s cybersecurity capabilities;
- Enable organizations to effectively and consistently evaluate and benchmark cybersecurity capabilities;
- Share knowledge, best practices, and relevant references across organizations as a means to improve cybersecurity capabilities; and
- Enable organizations to prioritize actions and investments to improve cybersecurity capabilities.
A self-evaluation using the toolkit can be completed in one day, but the toolkit can be adapted for a more rigorous evaluation effort. The C2M2 provides descriptive rather than prescriptive guidance. The model content is presented at a high level of abstraction so it can be interpreted by organizations of various types, structures, sizes, and industries. The C2M2 Program is following DoD’s CMMC effort closely to facilitate coordination between the two efforts.
Other assessment and maturity model tools include the Transmission Resilience Maturity Model (TRMM), developed for individual electric transmission system utilities to evaluate and benchmark the relative maturity of a utility’s transmission resilience program, and the Cybersecurity Evaluation Tool (CSET®), developed by DHS to guide asset owners and operators in evaluating ICS and IT security practices (CISA, n.d.; NATF, 2020).
Obert et al. (2019) provide an overview of the current state of distributed energy resource (DER) security standards. The IEEE Std. 1547, revised in 2018, defines interconnection and interoperability requirements for grid-interconnected DER. The revised standard requires DER to include a SunSpec Modbus, IEEE 2030.5 (Smart Energy Profile, SEP 2.0), or IEEE 1815 (DNP3) communication interface. It leaves the security requirements to be defined by the individual communication protocols, rather than providing normative overarching requirements. The authors provide the following summary of the three standards:
- IEEE 1815 Standard for Electric Power Systems Communications-Distributed Network Protocol (DNP3), started with no security features. Updates in IEEE 1815-2012 included a number of security upgrades commonly referred to as DNP3 Secure Authentication (DNP3-SA), which included encryption options and X.509 certificates.
- SunSpec Modbus has become a de facto standard communication protocol and is now a commonly available means of connecting industrial electronic devices. Modbus has traditionally had no encryption requirements whatsoever and has relied on bump-in-the-wire technologies for add-on security. In October 2018, the Modbus Organization announced the Modbus/TCP Security specification.
- IEEE 2030.5 is an approved interoperability standard for communications for IoT devices like energy sensors, smart light bulbs, solar inverters, and electric vehicles.
Of the three, the authors concluded that IEEE 2030.5 and associated implementation requirements for California, known as the California Smart Inverter Profile (CSIP), prescribe the greatest security features—including encryption, authentication, and key management requirements. A revision to IEEE 1547-2018, IEEE 1547.3—Guide for Cybersecurity of Distributed Energy Resources Interconnected with Electric Power Systems, is currently in progress and will more specifically address cybersecurity issues with DER.
In addition to the Cybersecurity Framework, NIST published SP 800-82 Rev. 2 Guide to Industrial Control Systems (ICS) Security, which covers cybersecurity practices to defend SCADA systems, Distributed Control Systems (DCS), and Programmable Logic Controllers (PLCs), and the National Institute of Standards and Technology Interagency Report (NISTIR) 7628 Rev. 1: Guidelines for Smart Grid Cybersecurity, a three-volume report that presents an analytical framework for organizations to develop cybersecurity strategies for smart grid-related characteristics, risks, and vulnerabilities (Smart Grid Interoperability Panel-Smart Grid Cybersecurity Committee, 2014; Stouffer et al., 2015). For reviews of cybersecurity smart grid standards, see Kuzlu et al. (2017) and Leszczyna (2018).
The development of standards is an ongoing process. For example, two that are in development and are focused on the challenges associated with verification and validation of cybersecurity in devices include IEEE Std. P2808—Standard for Function Designations used in Electrical Power Systems for Cyber Services and Cybersecurity, a standard for designing, procuring, and documenting cybersecurity controls, and IEEE Std. P2658—Guide for Cybersecurity Testing in Electric Powers Systems, to create a common method to test cybersecurity controls. As more control system endpoints, field devices, sensors, and actuators utilize remote connectivity for communications, control, configuration, and data collection connect to the grid, the need for methods to ensure security and enable interoperability will increase.
Finding 6.12: A culture of security and resilience for the grid would provide a state of improved and adaptable security, but has not yet been developed. Because NERC CIP standards are limited to bulk electric system registered entities, key components of the electric system (e.g., distribution) do not have mandatory cybersecurity protection and preparedness standards, leading to a patchwork of inconsistent standards and protection measures.
Recommendation 6.9: Congress should appropriate funds to Department of Energy (DOE) for the National Association of Regulatory Utility Commissioners (NARUC) to develop guidance for distribution-level resiliency requirements to be implemented at the state and local level, in coordination with the National Rural Electric Cooperative Association (NRECA), American Public Power Association (APPA), Large Public Power Council (LPPC), Edison Electric Institute (EEI), and other relevant stakeholders.
ADVANCING CYBER RESILIENCE THROUGH TECHNOLOGY
While technology alone cannot solve the problem of grid cybersecurity, improved technology is a critical foundation for achieving cyber resilience. Technology solutions for grid cybersecurity must consider both IT and OT systems. Cybersecurity solutions for energy delivery OT systems must be tailored to support operations as their first priority rather than data confidentiality. As a result, there are constraints in OT cybersecurity, including
- No down time allowable for system upgrades or repairs: Power systems must operate 24/7. This requires redundancy for all essential OT systems.
- Power system components are distributed over wide geographical regions, and are often publicly accessible and subject to tampering. Ensuring physical security and limiting physical access for all components may not be possible.
- Legacy equipment and protocols are often not designed to, or capable of, supporting cybersecurity measures.
- Excessive latency is unacceptable; real-time OT systems have specific requirements and supporting ICT infrastructures cannot be allowed to slow system operations.
- Active scanning of OT networks can interfere with equipment operations.
- A real-time emergency response capability is necessary.
- Patches/upgrades require rigorous, prolonged testing before deployment.
The motivation for, methods of, and consequences of attacks on IT systems can be different from those directed at OT systems. The electric system must be resilient to both. When an attack is directed at the IT system, if the OT
system is not completely isolated then there could be risk of a disruption to critical functionality. If the OT system is successfully breached, impacts to the grid are much more likely, including the potential for an outage and/or damage to physical equipment, which jeopardizes public safety, the environment, prosperity, and national security.
As discussed previously, the electric grid was one of the first industrial systems to use large-scale communications-enabled ICT. Early computer-based electric power control systems had virtually no cybersecurity controls other than relying on isolation from outside systems. But as these systems became increasingly interconnected, there was a broader recognition that stronger controls would be necessary. Initially, security technology was deployed in a largely ad hoc attempt to catch up with the deployment of interconnected control systems that leveraged the deployment of more traditional elements of computing and communications technology. More sophisticated cybersecurity deployments have emerged in the ensuing years. A summary of best practices to deploy security technology associated with these systems was prepared in 2014 by the Smart Grid Cybersecurity Committee, part of the Smart Grid Interoperability Panel. This document published guidelines for smart grid cybersecurity as NIST Interagency Report (NIST, 2014) and included examples of security technology and services deployed at that time to meet the high-level security requirements of the burgeoning smart grid.
Some pertinent examples of the technologies in the 2014 NIST report include identification and authorization technologies for securing remote system connections, which includes network segmentation of security domains to allow or deny entities and services from making a remote connection, and system partition to classify traffic and processes, requiring access verification and network-based or physical separation. This can include firewalls that provide a rule-based access control of ports and addresses, operating system process execution separation, or “data diodes” which provide hardware segmentation. This further includes cryptographic technologies to support public key infrastructures, and key management, and may involve secure remote certificate enrollment, with technology to allow enrollment and enforcement of authorization policies. Authentication, providing nonrepudiation of the origin and/or receipt of messages provides message integrity, is of high priority for control system applications. This enables role-based access control technology, which encompasses data, attributes, functions, management roles, and separation of duties. This further includes secure name and address resolution service that restricts transaction to entities based on valid addresses, and should also include password management technologies that enforce complexity and provisions for testing.
The grid of today and the future requires even more recognition of the trade-off between the benefits of cybersecurity and the benefits of increasing bulk and distributed power system connectivity, automation, and deployment of non-utility-owned devices. Given that grid operators and consumers will not forfeit the benefits stemming from greater connectivity, automation, and edge device deployment, future grid planners and operators will need to continue to improve commensurate security technologies to meet the challenge. In particular, ensuring cybersecurity of a future grid with many non-utility owned IoT system components is an increasingly formidable challenge.
Security of an IoT-based platform for grid operation and control that operates over a public network is of foremost importance. For example, IoT networks of low-cost, low-complexity terminals (e.g., sensors) are much more difficult to secure than networks of more capable devices like smart phones. This is owing to the lack of sufficient processing power to implement traditional security methods, the random access (and often parsimonious) nature of communications, and the large number of terminals involved in a typical application. If compromised, it can allow an adversary to manipulate the system at will resulting in degraded reliability (Dabrowski et al., 2017; Soltan et al., 2018, 2019). However, since most of the IoT devices are installed by consumers, their security cannot be ensured by the grid operators alone. Hence, to ensure the security of controllable IoT devices requires a close collaboration between policy makers (to put new regulations on IoT devices manufacturers), communication network operators (to monitor suspicious activity in the communication network), and grid operators (to design for containment, proactively monitor the physical state, and share their data with network operators to help them to detect cyber-attacks). Further compounding the challenge is that these IoT technologies will be developed by multinational vendors and deployed across multiple sectors of the economy, not limited to the energy infrastructure.
In addition to security, consumers’ privacy should also be considered in processing data collected for power grid operation and control. As mentioned in Chapter 2, power consumption patterns, for example, can reveal the degree of religious observance, traveling periods, sleeping patterns, and many other types of personal information. Therefore, privacy preservation should be an integral part of an IoT-based platform for the smart grid. In addition
to the solutions based on edge computing concepts that minimize the amount of data that is transferred to a central server, this could make use of developing privacy-aware ML algorithms and anonymization techniques (Efthymiou and Kalogridis, 2010; Duchi et al., 2014). For example, new concepts like federated learning (Konečný, 2016) can effectively be used to infer important information from data in a distributed manner without collecting the data from different parties, although these techniques can leak private information even without direct data sharing.
Introduction of new paradigms in 5G technology may also result in more or fewer security threats (depending on the type) against an IoT-based platform for grid operation and control. For example, the 5G network slicing concept can allow the implementation of different security requirements for different services, but at the same time opens the possibility of unknown security threats (Dotaro, 2018). Moreover, network slicing allows 5G to provide security-as-a-service by deploying security functions within different slices.
Given that thousands of global manufacturers may be manufacturing millions of edge devices, ensuring that there are no cyber threats buried in any of them will be challenging, and requires software-centric, systems-approach-based solutions. By addressing the problem from a cyber-physical system point of view, which specifies and regulates allowable actions, better security and resilience may be achievable. In some cases, one solution might be to allow only connections between the point of common coupling device and the customer device through a “publish-subscribe” port in the cloud (Uzunov, 2016). An alternative strategy may be to provide guidelines for edge-device manufacturers and follow up to the extent feasible, but to then also have a utility-owned device at the point of common coupling that ensures that the customer-owned device is not behaving in a malevolent manner, or compromising safety for utility crews or customers. Robust strategies that are delay-tolerant such as Open FMB (Smallwood, 2017) may need to be deployed, but would require that the power devices be able to operate autonomously.
Design Principles for Cyber Resilience
Design principles associated with technology architecture provide a valuable tool for defining and understanding the many complex interactions existing in present and future grids. Grid architecture’s primary uses are to help manage complexity and risk; assist in communication among stakeholders around a shared vision of the future grid; identify and remove barriers and defining essential limits; identifying gaps in theory, technology, organization, regulation; and providing a framework for complex grid-related development activities. What follows is a brief description of some general design principles that will aid future deployers of technology to ensure that security is addressed in the system they deploy. These principles are baked-in security, segmentation, graceful degradation, detection, and response and recovery.
Baked In Versus Bolted On
Security for ICT is now a central aspect of ensuring reliable operation, and there needs to be inherent security built into the ICT components and systems utilized in ICS. Air gaps between sensitive systems and the enterprise environment and boundary protection are no longer practicable in many cases, and bolted on security becomes increasingly infeasible as systems continue to increase in complexity and interdependence. Particularly, security must be regarded as an element of the performance requirements. Going forward, security must be intrinsically included at all layers and pertinent to the functionality associated with this protection, versus an add-on application or appliance. At the same time, a system will need to remain secure even with legacy equipment that does not have intrinsic security features baked in. Analog checkpoints on connected equipment, such as digital protected relays, can protect equipment from unintended operation while not losing the reliability benefits of connected systems.
Technologies for code inspection, signing and verification for mobile code to ensure software quality assurance are also important, including failsafe, fail-secure, or fail-in-a-known-state mechanisms to provide trusted recovery at the application, system, and firmware levels. When errors are detected, there is an error handling process that provides mechanisms for enhancing software quality assurance. There is also a need to validate the integrity of
the data that are provided to critical processes or control systems. This includes authentication, nonrepudiation, data transfer integrity, and internal system data protection technologies.
Segmentation
Segmenting critical systems into functional subsystems that can operate independently from each other is an important design principle to enhance the resilience of grid ICT systems. If a vulnerability is exploited that compromises a component or part of the system, the design of the overall system needs to limit the consequences from cascading to other parts of the system in both the cyber and physical dimensions. Segmentation can prevent an attacker from exploiting additional ICT assets after an initial breach, as well as prevent cascading effects from an ICT failure from propagating to other portions of the system. This concept also applies to both preventing larger consequences from the initial event, as well as enhancing quick reconstitution of compromised subsystems. Granular and micro-segmentation can provide further cybersecurity protection.
It is clear that the “pipes” of information flow in ICT systems cannot be fully secured. Given this, the data “flows” need to be secured and validated in real-time. Improved data science techniques, including packet-level authentication and encryption, better language for data exchange, data dictionaries for operations, context-aware inspection, and data that extends beyond the electricity operations, can be used in monitoring, detection, diagnosis, and response. This may include adopting a graduated zero-trust model that integrates both modern and legacy devices, and takes into account both the cyber and physical footprints and the constraint of not impeding valid operations.
Graceful Degradation and Continued Operation Under Attack
Graceful degradation is a concept that enables a partially failed system to continue to operate. The goal is maintaining critical functionality as a result of a wide range of attack and/or failure scenarios. Graceful degradation techniques can leverage the aforementioned segmentation design principle. A failure or compromise in one subsystem should not be exploitable across other subsystems, thereby reducing the risk of a cascading failure (or an attacker seamlessly traversing a flat network architecture).
Because OT systems cannot simply be shut down as a response to a cyberattack, development of improved redundancy and failover systems is essential. More attention should be given to how these systems operate during an active attack scenario, where critical subsystems may be insidiously compromised, rather than their primary design consideration focused on continued operation given component failure(s). Such enhancements in this design principle would also allow for more effective red-teaming exercises, where a specialized team takes an adversarial approach to simulate an attack using realistic tools and techniques to gain access, and the ability to more comprehensively test ICT cybersecurity measures.
Certain architectures are more resilient under attack than others. For example, segmented architectures can be implemented to stop the propagation of an attack or fault. Watchdog circuits that detect compromises can be incorporated that force an adversary to compromise both the watchdog system and the active system. In future ICT deployments, software defined networking can allow operators to dynamically change the architecture in response to an attack, or the system can automatically adapt to a context-proven threat and reconfigure the architecture to limit the impact.
Detection
Detection technologies across the cyber and physical domains are necessary to understanding when compromises or breaches are occurring. In the case of sophisticated adversaries who might have a persistent presence for the purposes of reconnaissance and/or covertly exfiltrating information, detection technologies that can thwart their continued presence are important components of an overarching risk mitigation strategy. Detection includes monitoring data, collecting and managing data, data fusion, alert correlation, forensic analysis, and action. Challenges in detection include obtaining data from both ICS and ICT systems in real-time, limited tools for visibility
into the status of systems, limited ability to assess the trust-level of systems and components at scale, challenges in analyzing disparate data sources, and realizing synergies between cybersecurity and the efficiency and reliability improvements possible through improved sensing, measurement, and visibility of grid operations.
Robust, comprehensive processes need to be developed for obtaining system data at the scale and rate required to detect cyber-incursions. There are few technologies currently available that provide granular, accurate, and timely visibility into network traffic on operational systems, or can create real-time network maps for operational systems. Protocols used in operations are not interoperable, and a single protocol may be uniquely implemented by multiple vendors. This limits the ability to parse OT network traffic and packages rapidly using a single method. In the absence of real-time detailed visibility into operational networks it is extremely difficult to establish baselines of behavior that can be used to identify “abnormal” behavior in the system.
Limited visibility into operational network traffic can be the result of legacy equipment, limited infrastructure bandwidth, lack of appropriate devices to gather information, regulatory policies that deter the use of newer technologies, an aging workforce with insufficient incentives and/or skills to reengineer networks and/or analyze operational network traffic, lack of appropriate tools and resources, and so on. Additional research to develop the tools, skills, and culture within the engineering and operations fields would be beneficial. A better understanding of the boundaries within which the system should operate under normal conditions is also needed.
Sensing and measurement technologies are substantially increasing the amount of information available to a system operator. This has the potential to dramatically improve an operator’s situational awareness about the state of the system in real time, opening up opportunities for control decisions that improve the reliability and efficiency of all aspects of the grid, spanning generation, transmission, distribution and end use.
Converting the large amounts of data from these sensors and IoT to actionable information is a high priority in many grid modernization efforts. The trend for grid operations to be increasingly dependent on new sources of digitally communicated data will not change. These data sources are likely to provide benefits in efforts to detect cybersecurity events and incidents, but there may be a trade-off because these data source may require increased attention to IT-centric data security issues and also data privacy issues, particularly regarding energy usage and meter data, that will need to be addressed.
Log management systems that provide centralized logging and monitoring by a system operations center or equivalent with 24/7 real-time event notification are important. This includes scalable log filtering and parsing, and standardized audit records that enable security audit reviews and forensic analysis. By providing security audits with automatic data generation, and responses to verify that application-level auditing is implemented in commercial-off-the-shelf and custom code, these techniques can verify that operating system-level auditing exists. System use notifications should include system access history; failed login attempt lockouts; use of other access controls to limit multiple concurrent sessions; and limitation of network access. Managing logs should include regular archiving and retention of logs; centralized logging; automatic file system checks; and other log management activities. Even systems with baked-in security can fall to a determined adversary. When an OT system is compromised, the system and/or device must have a mechanism to support a trustworthy and secure way to extract necessary forensic evidence.
Key to effective detection and proper interpretation of attack indicators is the fusion of data from sensors into information that can lead to detection. Information fusion is the process of combining data from various sensors to create higher-level information for making better inferences about malicious behavior. When done correctly, it can result in alerts that are more accurate, and lead to faster detection. Information fusion is grounded in mathematical and heuristic techniques from multiple research areas, including statistics, digital signal processing, artificial intelligence, and information theory.
Fusion of diverse information is less well-developed in cybersecurity than other contexts but has been used to improve intrusion detection in various fields such as wireless sensor networks and industrial control systems. Further research and development would be required to fuse information from diverse monitors deployed in the system. This information can potentially include host and network-level activity information, hardware related features, and physical information such as power usage by a computer. An important focus is to develop information fusion and anomaly detection techniques in a semi-supervised and data-driven way. In doing so, one should minimize
the involvement of human experts and learn from the monitor data to identify important features, anomalies, and intrusions. Another desired property of these techniques is to be computationally lightweight.
Alert correlation is the process of conceptually interpreting multiple events to assign new meaning to them. These events mainly include alerts generated by intrusion detection systems such as anomaly detection modules. To conceptually interpret these alerts about the protected system, different types of information need to be correlated including but not limited to information related to the cyber and physical systems, information about vulnerabilities, information about the security tools and algorithms, and alerts generated by these tools. An important goal for alert correlation is to formally define the alert correlation framework with respect to the fusion and response techniques that are developed, in order to reduce false alerts, detect high-level patterns of attacks, increase the meaning of incidents, and predict the future steps of attacks by leveraging causal reasoning. A hierarchical approach to reasoning about the underlying data and synthesizing it with an understanding of the context will be essential.
Many of the analytical methods used in IT cybersecurity could be applied to data collected from OT systems if there was more visibility. For example, thresholds for device/equipment operations could be established to restrict actions that would cause the device/equipment to act outside of those boundaries, or to alert when messages and commands are sent that would result in the device/equipment acting outside of a known “good state.”
An important goal for alert correlation is to formally define the alert correlation framework with respect to the fusion and response techniques that are developed, in order to reduce false alerts, detect high-level patterns of attacks, increase the meaning of incidents, and predict the future steps of attacks.
Figure 6.5 shows a prototypical monitoring, fusion and event correlation, and response framework. In this framework, monitors are deployed in a system at different locations and at different levels (with diverse sources of input). The information generated by the monitors then serve as input to fusion and alert correlation algorithms whose goal is to detect attacks. The fusion and alert correlation algorithms aim to exploit the diversity of the information collected to increase the confidence in and trust of the inferred attack state. The fusion algorithms then provide attack alerts to response selection algorithms. Response selection algorithms use these inputs and developed games and decision algorithms to find good or optimal response strategies. The chosen response strategy is implemented through actuation of the selected response mechanisms that verifies that the effect of the mechanism’s actuation was as intended. In this way, the ICT architecture aims to maintain critical system performance even when under attack, and restore full system performance in reasonable time.
IT security information and event management systems have advanced to enable one-pane-of-glass visibility (one view of all sources) into network traffic of both headers and packet contents, but this capability is nascent for OT networks and systems.
For full visibility into the entire grid, from generation source to end-user and all the stakeholders that impact power generation, transmission, and delivery, there would need to be sensors that read both the cyber and physical state of the grid, a better understanding of what normal systems look like over the course of a year, analysis methods to identify anomalous behavior, and forensic capabilities to track the origin and spread of that behavior through the systems.
Response and Recovery
Cyber resilience includes the ability to quickly respond and recover from an attack or other off-normal situation. Effective response and recovery capabilities include robust detection to enhance situational awareness of ongoing attacks, mature reconstitution capabilities to restore normal system operation, comprehensive plans to address a variety of scenarios, and diverse training capabilities to drill and test response and recovery procedures and capabilities. After an incident has been identified, ideally a defender can access the system or device at a lower level than the adversary to evaluate the device state and return it to a safe operations state. For legacy OT devices, this might not be possible, and different components within a system may need to operate across a gradient of confirmed trust levels during restoration and recovery.
One effective action that can be taken to enhance response and recovery is conducting exercises to practice response and recovery plans under various attack or failure scenarios. Such exercises are often undertaken at the bulk system level but could greatly benefit smaller operators if they were expanded to regional, state, or local levels of the system. Joint cybersecurity exercises that include many stakeholders can be used to highlight interdependencies between the grid and other local, state, federal entities, and critical infrastructures. Joint exercises can provide first responders and operators associated with the other critical infrastructures insights into how to engage with the utilities in the exercise.
The electricity subsector conducts exercises for a variety of emergency situations that could impact their ability to provide electricity. The following list summarizes several national-level exercises that have occurred:
- Clear Path VII (DOE, May 2019) participants from the federal government and the energy sector tested their restoration roles, responsibilities, plans and procedures following a fictitious 7.7 magnitude earthquake along the New Madrid Seismic Zone (NMSZ), stressing interdependencies between multiple critical infrastructure sectors.
- FEMA Region 1 and 9 (FEMA, May 2020): The 2020 National Level Exercise focused on cybersecurity and involved a complex, multidimensional attack that reflects the global threat environment. In the scenario, widespread cyberattacks led to significant impacts on critical infrastructure and community lifelines. Federal department and agencies focused on participation from their headquarters locations.
- Joint Financial Services—Electric Sector Cyber Exercise (Treasury, August 2016) examined incident response capabilities and interdependencies between the two sectors.
- Cyber Guard (DoD/NSA, June 2017): A 1-week exercise that tested the response capabilities of 700 cyber operators and critical infrastructure experts from USCYBERCOM, the National Guard and Reserves, the intelligence community, and public- and private-sector organizations.
- GridEx V (NERC, November 2019): A 2-day distributed play exercise for stakeholders in the electricity industry to respond to simulated cyber and physical attacks that affected the reliable operation of the grid. More than 7,000 players from 526 organizations from electric utilities, government agencies, and partners in Canada and Mexico participated. GridEx V also included an executive tabletop exercise where more than 100 electric sector executives and senior U.S. government officials worked through incident response protocols to address widespread outages.
- DARPA has been conducting “black-start” exercises, simulating a significant blackout triggered by a cyberattack, and attempting to restore power as quickly and effectively as possible (Sobczak, 2018). A DOE grid modernization project launched in 2019 is exploring black start system recovery after simulated physical or cyber incidents on a small island with an isolated grid, and distributed energy resources and storage (DOE, 2019). The industry would benefit from sharing lessons from these exercises across the
industry and government, which could enable the creation of post-event tools for detection, analysis, and restoration to complement prevention tools.
In addition to exercises, red team and purple team training can provide value to utility control operators and engineers who may not have much experience in cybersecurity. Red teamers are specialized cybersecurity professionals who are brought in to attempt to access a target system using tools used by adversaries. Purple team training occurs when a red team expert works directly with a utility staff defender and shows the defender how the red team can get access and trains the defender to identify vulnerabilities and tactics to prevent access.
Recommendation 6.10: The Department of Energy (DOE) and Department of Homeland Security (DHS, including the Federal Emergency Management Agency [FEMA]) should expand interactions with industry through exercises, red and purple teaming, and assessments to enhance the electric power system’s security posture. DOE and DHS should provide funding to regional, state, and local entities to support exercises in collaboration with industry to enhance grid cybersecurity incident response.
An unresolved problem in response and recovery is determining the correct response to a cyberattack. One possibility is to employ game theoretic techniques. Using this approach, one can view the decision making process as an online game of incomplete (and possibly imperfect) information between the response function (the defender) and an unknown attacker. In this case, although the defender is at a disadvantage by not knowing the strategy of the attacker, a defender can make use of personal knowledge of the network and the information obtained from the monitoring and fusion algorithms in order to learn the attacker’s employed strategy and predict the attacker’s future moves. If possible, historical attack data should be used to guide the design of the response function, especially when modeling the state of the grid and its evolution over time.
The attraction of employing game theoretic techniques stems from the danger of using static predefined attacker models. Once the attacker model is fixed, any deviation on the end of the attacker (which is most likely to happen given the attacker’s malicious intentions) constitutes a new attack vector that the response engine has not accounted for. Therefore, the committee emphasizes the usage of ML techniques to use observed monitoring and fusion data to build, and refine, a model of the attacker’s strategy. The online and data-driven nature of such techniques will ensure that the response engine will be able to refine its response model in the case of any deviation by the attacker.
CONCLUSIONS
Advances in ICT have enabled the U.S. electric grid to be more efficient and reliable through automation of many grid systems. Though attempts are made to keep the grid’s ICT safe from compromise, the system remains under constant threat of attack by adversaries and failure from natural events and human error.
While the primary responsibility for securing ICT resides with the grid operators, the federal government has an important role in enhancing grid cyber resilience. This chapter has discussed the many threats to the electric system, and gaps that could be addressed. It is also the case that many things are working. The growing recognition of the importance of cybersecurity associated with grid ICT led the Federal government, in collaboration with industry, to develop standards, research funding to advance grid-specific ICT cybersecurity, with training, research projects, and other resources made available to assist asset owners and operators. The development and enforcement of mandatory cybersecurity standards has been led by NERC (under FERC jurisdiction). The development of voluntary cybersecurity standards has been led by NIST. The majority of research funding for grid cybersecurity has been provided by DOE as the lead sector specific agency, with additional funding from DHS, NSF, DoD, DARPA, and NIST in related areas that often support and/or supplement DOE’s research agenda.
Electric grid owners and operators have agreements that facilitate sharing information about threats and defenses before, during and after incursions occur, and many peer organizations have agreements for mutual aid in the event of an attack. While all transmission operators are subject to the aforementioned NERC CIP requirements, and while many states have additional cybersecurity requirements associated with distribution-level cybersecurity, the electricity utility industry has a number of initiatives and activities to exchange best practices and fostering
research to enhance the cybersecurity technology pertinent to their operational systems. For example, EPRI, the North American Transmission Forum, the Edison Electric Institute (EEI), and other trade organizations have a number of projects and activities related to developing and exchanging best practices associated with cybersecurity of critical electric infrastructure.
Cybersecurity, when properly implemented, is not cheap. Investing in the people, processes, and technology described in this chapter requires adequate funding. In most cases, this funding comes from ratepayers. For regulated utilities, that requires approval that the cost is justified as “used and useful” by the regulators. For some items of expenditure, such as complying with mandatory cybersecurity requirements, it is an easier justification by executive management to approve those necessary activities. However, for more discretionary activities, which may be perceived as above and beyond the minimum mandatory requirements, there may need to be additional justification for an advanced cybersecurity program. These generally include the need to remain abreast of rapidly evolving threats and vulnerabilities related to advanced technologies, and the need to ensure that the organization’s operational integrity and reputation are not tarnished.
Ultimately, the decision to invest in a robust cybersecurity program is the responsibility of executive management for the various grid operators, who must balance these decisions with other priorities of the organization. Organizations that have robust risk management processes evaluate all risks and estimates of mitigation based on the effectiveness of these investments to maximize the benefit of these investments, often in conjunction with their regulators (Keogh and Thomas, 2016). The federal government has a role in supporting electric utilities and others involved in cybersecurity of the grid, as the risks are not just to the private companies but to the entire U.S. society on which the grid depends, and the threats are not just from individual attackers but also coordinated nation-state attacks. A lack of adequate cybersecurity and resilience metrics that could shed light on the financial and security benefits of investments hinders the ability to develop a business case to support expenditures to develop a robust program of cyber protection. The market incentivizes vendors to focus on short-term goals of quickly developing and delivering products—sometimes without adequate testing and refinement—rather than prioritizing the comprehensive security of those products.
The complexity of the grid is increasing as it serves more customers and more end uses, incorporates more diverse sources of power, increases the number and diversity of stakeholders that can impact reliability, and utilizes more data, automation, and technologies throughout the controls, generation, transmission, and distribution systems. Many of the technologies being contemplated for the grid of the future, especially those capabilities described in Chapter 5 that utilize more distributed energy resources (DER) and advanced controls, will necessarily require more attention to the cybersecurity of those technologies. Existing security paradigms will be challenged through the increased diversity of technologies, many of which will be leveraged from other domains, such as high-speed communication and other distributed computational platforms. This will include the use of more commodity ICT solutions. There will also be more edge computing and analytics, which will challenge traditional security approaches that aim to protect critical assets through isolation and security perimeters. As electric utility systems become more complex and interdependent on other infrastructures, the ICT supporting those systems increases in complexity. In addition, there is a related decrease in clarity of what assets should be considered part of a utility’s ICS. The use of virtual assets and off-site services, including cloud services, creates nebulous boundaries that make it hard to accurately inventory all of the ICT assets that could impact a utility’s ICS security.
For example, distribution automation technologies, smart grid technologies that integrate customer-side demand response with transmission and distribution real-time constraints, require greater communications and control capabilities than currently exist. Vulnerabilities in these technologies could potentially be exploited by an adversary. Metrics are needed to assess the security of these systems against the risks that they introduce to the system, with assurances that the overall benefits of the technology minus the commensurate risk that is introduced is a net gain. Such metrics may be attainable through simulation of model systems.
Last, as threats to the power system from state actors grow, it is not realistic to expect private parties to address adequately all the associated national security concerns. The United States has devoted far too little attention to this issue. There is an urgent need to enhance information sharing initiatives, and develop, implement, and find appropriate ways to pay for the needed protections.
REFERENCES
Aldawood, H., and G. Skinner. 2018. “Educating and Raising Awareness on Cybersecurity Social Engineering: A Literature Review.” In 2018 IEEE International Conference on Teaching, Assessment, and Learning for Engineering (TALE), 62–68. Wollongong, NSW: IEEE. https://doi.org/10.1109/TALE.2018.8615162.
Andres, R.B., and H.L. Breetz. 2011. “Small Nuclear Reactors for Military Installations: Capabilities, Costs, and Technological Implications.” Strategic Forum, 262. Washington, DC: Institute for National Strategic Studies: National Defense University.
Angle, M.G., S. Madnick, J.L. Kirtley, and S. Khan. 2019. Identifying and anticipating cyberattacks that could cause physical damage to industrial control systems. IEEE Power and Energy Technology Systems Journal 6(4):172–182. https://doi.org/10.1109/JPETS.2019.2923970.
Ani, U.P.D., H. He, and A. Tiwari. 2017. Review of cybersecurity issues in industrial critical infrastructure: Manufacturing in perspective. Journal of Cybersecurity Technology 1(1):32–74. https://doi.org/10.1080/23742917.2016.1252211.
Barlyn, S. 2020. “Ransomware Exposure Driving Up Cyber Insurance Costs.” Insurance Journal. January 22. https://www.insurancejournal.com/news/national/2020/01/22/555479.htm.
BSI (British Standards Institution). 2019. “ISO 9241-210: Ergonomics of Human-System Interaction—Part 210: HumanCentred Design for Interactive Systems.” http://www.standardsuk.com/.
CISA (Cybersecurity and Infrastructure Security Agency). n.d. “Downloading and Installing CSET.” https://us-cert.cisa.gov/ics/Downloading-and-Installing-CSET.
CISA. 2020a. “Alert (AA20-049A): Ransomware Impacting Pipeline Operations.” October 24. https://us-cert.cisa.gov/ncas/alerts/aa20-049a.
CISA. 2020b. Insider Threat Mitigation Guide. Washington, DC: Cybersecurity and Infrastructure Security Agency. https://www.cisa.gov/sites/default/files/publications/Insider%20Threat%20Mitigation%20Guide_Final_508.pdf.
Coats, D.R. 2019. “Worldwide Threat Assessment of the U.S. Intelligence Community.” Statement for the Senate Select Committee on Intelligence.” https://www.dni.gov/files/ODNI/documents/2019-ATA-SFR---SSCI.pdf.
Conteh, N., and P. Schmick. 2016. Cybersecurity: Risks, vulnerabilities and countermeasures to prevent social engineering attacks. International Journal of Advanced Computer Research 6 (February):31–38. https://doi.org/10.19101/IJACR.2016.623006.
Costa, D. 2017. “CERT Definition of ‘Insider Threat’—Updated.” Insider Threat (blog). March 7. https://insights.sei.cmu.edu/insider-threat/2017/03/cert-definition-of-insider-threat---updated.html.
CRS (Congressional Research Service). 2017a. “Cybersecurity: Federal Agency Roles.” February 13, IF10602, by E. Fischer. https://crsreports.congress.gov/product/pdf/IF/IF10602.
CRS. 2017b. “Cybersecurity for Energy Delivery Systems: DOE Programs.” August 28, R44939, by P. Parfomak, R. Campbell, and C. Jaikaran. Version 3. https://crsreports.congress.gov/product/pdf/R/R44939.
CRS. 2018. “Electric Grid Cybersecurity.” September 4, R45312, by R. Campbell. Version 2. https://crsreports.congress.gov/product/pdf/R/R45312.
Cyberspace Solarium Commission. 2020. Cyberspace Solarium Commission Final Report. Washington, DC: U.S. Cyberspace Solarium Commission. https://www.solarium.gov/report.
Dabrowski, A., J. Ullrich, and E.R. Weippl. 2017. “Grid Shock: Coordinated Load-Changing Attacks on Power Grids: The Non-Smart Power Grid Is Vulnerable to Cyber-Attacks as Well.” In Proceedings of ACM, ACSAC’17, December.
DHS (Department of Homeland Security). 2020. “FY 2021 Budget in Brief.” https://www.dhs.gov/sites/default/files/publications/fy_2021_dhs_bib_0.pdf.
DOE (U.S. Department of Energy). n.d. “Energy Sector Cybersecurity Preparedness.” Energy.gov. https://www.energy.gov/ceser/activities/cybersecurity-critical-energy-infrastructure/energy-sector-cybersecurity.
DOE. 2006. “Roadmap to Secure Control Systems in the Energy Sector.” January. https://www.energy.gov/sites/prod/files/oeprod/DocumentsandMedia/roadmap.pdf.
DOE. 2011. “Roadmap to Achieve Energy Delivery Systems Cybersecurity.” September. https://www.energy.gov/sites/prod/files/Energy%20Delivery%20Systems%20Cybersecurity%20Roadmap_finalweb.pdf.
DOE. 2014. Cybersecurity Capability Maturity Model (C2M2) Version 1.1. Washington, DC: U.S. Department of Energy. https://www.energy.gov/sites/prod/files/2014/03/f13/C2M2-v1-1_cor.pdf.
DOE. 2016. “Smart Grid Investment Grant Program Final Report.” December 20. https://www.smartgrid.gov/files/documents/Final_SGIG_Report_20161220.pdf.
DOE. 2018a. “From Innovation to Practice: Re-designing Energy Delivery Systems to Survive Cyberattacks.” https://www.energy.gov/sites/prod/files/2018/09/f55/CEDS%20From%20Innovation%20to%20Practice%20FINAL_0.pdf.
DOE. 2018b. “Multiyear Plan for Energy Sector Cybersecurity.” March. https://www.energy.gov/sites/prod/files/2018/05/f51/DOE%20Multiyear%20Plan%20for%20Energy%20Sector%20Cybersecurity%20_0.pdf.
DOE. 2018c. “Secretary of Energy Rick Perry Forms New Office of Cybersecurity, Energy Security, and Emergency Response.” February 14. https://www.energy.gov/articles/secretary-energy-rick-perry-forms-new-office-cybersecurity-energy-security-and-emergency.
DOE. 2019. “2019 Grid Modernization Lab Call Awards.” https://www.energy.gov/2019-grid-modernization-lab-call-awards.
DOE. 2020a. “Budget (Justification and Supporting Documents).” https://www.energy.gov/cfo/listings/budget-justification-supporting-documents.
DOE. 2020b. “Department of Energy FY 2021 Congressional Budget Request: Volume 3, Part 1.” DOE/CF-0163. https://www.energy.gov/sites/prod/files/2020/04/f73/doe-fy2021-budget-volume-3-part-1.pdf.
Dotaro, E. 2018. “5G Network Slicing and Security.” IEEE Software Defined Networks. https://sdn.ieee.org/newsletter/january-2018/5g-network-slicing-and-security.
Dragos. 2017. “CRASHOVERRIDE: Analyzing the Malware That Attacks Power Grids | Dragos.” Dragos. June 12. https://www.dragos.com/resource/crashoverride-analyzing-the-malware-that-attacks-power-grids/.
DSB (Defense Science Board). 2017. Final Report of the Defense Science Board (DSB) Task Force on Cyber Deterrence. Washington, DC: Department of Defense. https://apps.dtic.mil/dtic/tr/fulltext/u2/1028516.pdf.
Duchi, J.C., M.I. Jordan, and M.J. Wainwright. 2014. Privacy aware learning. Journal of ACM, December.
Efthymiou, C., and G. Kalogridis. 2010. “Smart Grid Privacy via Anonymization of Smart Metering Data.” In IEEE International Conference on Smart Grid Communications.
EIA (U.S. Energy Information Administration). 2020. “U.S. Customers Experienced an Average of Nearly Six Hours of Power Interruptions in 2018—Today in Energy—U.S. Energy Information Administration (EIA).” Today in Energy. https://www.eia.gov/todayinenergy/detail.php?id=43915.
Energetics. 2006. Roadmap to Secure Control Systems in the Energy Sector. Washington, DC: U.S. Department of Energy. https://www.energy.gov/sites/prod/files/oeprod/DocumentsandMedia/roadmap.pdf.
E.O. (Executive Order) 13920. 2020. “Securing the United States Bulk Power System (Executive Order).” 85 FR 26595, E.O. 13920 of May 1, 2020.
EPRI (Electric Power Research Institute). 2019. “High-Altitude Electromagnetic Pulse and the Bulk Power System: Potential Impacts and Mitigation Strategies.” EPRI Technical Report 3002014979. Palo Alto, CA.
ESCC (Electricity Subsector Coordinating Council). 2013. “Electricity Subsector Coordinating Council Charter.” https://www.cisa.gov/sites/default/files/publications/Energy-Electricity-SCC-Charter-2013-508.pdf.
ESCC. 2019. “The ESCC’s Cyber Mutual Assistance Program.” https://www.electricitysubsector.org/-/media/Files/ESCC/Documents/CMA/Cyber-Mutual-Assistance-Program-One-Pager_013119.ashx?la=en&hash=F4D3445C75E3B9884458E403390DBBD120F9D8D4
ESCC. 2020. “Electricity Subsector Coordinating Council Brochure.” https://www.electricitysubsector.org/-/media/Files/ESCC/Documents/ESCC_Brochure.ashx?la=en&hash=00901B6AD252F5AF940C1012619A43C39967F9C9.
Fagan, M., K.N. Megas, K. Scarfone, and M. Smith. 2020. “IoT Device Cybersecurity Capability Core Baseline.” NISTIR 8259A. May. https://doi.org/10.6028/NIST.IR.8259A.
FERC (Federal Energy Regulatory Commission). 2008. 18 CFR Part 40, Docket No. RM06-22-000; Order No. 706: Mandatory Reliability Standards for Critical Infrastructure Protection. Issued January 18. 122 FERC ¶ 61,040.
FERC Staff. 2020. “Cybersecurity Incentives Policy White Paper.” Federal Energy Regulatory Commission.
FERC and NERC (Federal Energy Regulatory Commission and North American Electric Reliability Corporation). 2020. Second Joint Staff White Paper on Notices of Penalty Pertaining to Violations of Critical Infrastructure Protection Reliability Standards. Docket No. Ad19-18-000.
Filkins, B., and D. Wylie. 2019. “SANS 2019 State of OT/ICS Cybersecurity Survey.” June. https://www.sans.org/reading-room/whitepapers/analyst/membership/38995.
Fouquet, H., and W. Horobin. 2019. “Warning: Cyber Will Soon Cost Insurers More Than Natural Disasters.” Insurance Journal. May 12. https://www.insurancejournal.com/news/international/2019/05/12/526164.htm.
Gray, C., and D. Freese. 2020 “Cybersecurity Maturity Model Certification (CMMC) for Defense Contractors,” PwC. https://www.pwc.com/us/en/services/consulting/cybersecurity/cmmc-aerospace-defense.html.
Gregory-Brown, B. 2017. “Securing Industrial Control Systems-2017.” SANS Institute. https://www.sans.org/reading-room/whitepapers/ICS/paper/37860.
Greitzer, F.L., J.R. Strozer, S. Cohen, A.P. Moore, D. Mundie, and J. Cowley. 2014. “Analysis of Unintentional Insider Threats Deriving from Social Engineering Exploits.” In 2014 IEEE Security and Privacy Workshops, 236–250. https://doi.org/10.1109/SPW.2014.39.
Griffin, R., K. Chiglinsky, and D. Voreacos. 2019. “Was It an Act of War? That’s Merck Cyber-Attack’s $1.3 Billion Insurance Question.” Insurance Journal. December 3. https://www.insurancejournal.com/news/national/2019/12/03/550039.htm.
Haizler, O. 2017. The United States’ cyber warfare history: Implications on modern cyber operational structures and policy-making. Cyber, Intelligence, and Security 1(1):15.
Hawk, C., and DOE Office of Cybersecurity, Energy Security, and Emergency Response. 2019. “Cybersecurity for Energy Delivery Systems (CEDS) Division Overview.” Presentation at the first meeting of the Committee on the Future of Electric Power in the United States. March 4. Washington, DC: National Research Council.
Honeywell Process Solutions. 2007. “Cybersecurity in Manufacturing and Production.” https://www.honeywellprocess.com/library/marketing/whitepapers/HoneywellIndustrialCyberSecurity_CyberSecurityinManufacturingandProduction_WP686.pdf.
INL (Idaho National Laboratory). 2016. “Strategies, Protections, and Mitigations for the Electric Grid from Electromagnetic Pulse Effects.” INL/EXT-15-35582. https://inldigitallibrary.inl.gov/sites/STI/STI/INL-EXT-15-35582.pdf.
ISAO (Information Sharing and Analysis Organization) Standards Organization. 2020. “Resource Library.” https://www.isao.org/resources/resource-library/#government-programs.
(ISC)2 (International Information System Security Certification Consortium). 2019a. “(ISC)2 Finds the Cybersecurity Workforce Needs to Grow 145% to Close Skills Gap and Better Defend Organizations Worldwide.” November 6. https://www.isc2.org/News-and-Events/Press-Room/Posts/2019/11/06/ISC2-Finds-the-Cybersecurity-Workforce-Needs-to-Grow—145.
(ISC)2. 2019b. “Women in Cybersecurity.” https://www.isc2.org/research/women-in-cybersecurity.
Jalali, M.S., M. Siegel, and S. Madnick. 2019. Decision-making and biases in cybersecurity capability development: Evidence from a simulation game experiment. Journal of Strategic Information Systems 28(1):66–82. https://doi.org/10.1016/j.jsis.2018.09.003.
Jaros, S.L. 2018. “Strategic Plan to Leverage the Social and Behavioral Sciences to Counter the Insider Threat.” Homeland Security Digital Library. Defense Personnel Security Research Center (U.S.). October 1. https://www.hsdl.org/?abstract&did=.
Johnson, J. 2017. “Roadmap for Photovoltaic Cybersecurity.” SAND2017-13262. Albequerque, NM: Sandia National Laboratories. https://sunspec.org/wp-content/uploads/2020/01/Roadmap-for-Photovoltaic-Cyber-Security-SAND2017-132624-10-2018.pdf.
Joint Task Force Interagency Working Group. 2020. “Security and Privacy Controls for Information Systems and Organizations.” Revision 5. Washington, DC: National Institute of Standards and Technology. https://doi.org/10.6028/NIST.SP.800-53r5.
Keogh, M., and S. Thomas. 2016. “Risk Management in Critical Infrastructure Protection: An Introduction for State Utility Regulators.” NARUC Research Lab. https://pubs.naruc.org/pub/D10AF40A-AD04-3983-7421-9FBE970D87F3.
Konečný, J., H.B. McMahan, F.X. Yu, P. Richtárik, A.T. Suresh, and D. Bacon. 2016. “Federated Learning: Strategies for Improving Communication Efficiency.” NIPS Workshop on Private Multi-Party Machine Learning, December.
Kuzlu, M., M. Pipattanasompom, and S. Rahman. 2017. “A Comprehensive Review of Smart Grid Related Standards and Protocols.” In 2017 5th International Istanbul Smart Grid and Cities Congress and Fair (ICSG), 12–16. Istanbul, Turkey: IEEE. https://doi.org/10.1109/SGCF.2017.7947600.
Kwon, J., and M.E. Johnson. 2014. “Proactive Versus Reactive Security Investments in the Healthcare Sector.” MIS Quarterly 38(2):451–471. https://misq.org/proactive-versus-reactive-security-investments-in-the-healthcare-sector.htm.
Lee, R.M., M.J. Assante, and T. Conway. 2016. “Analysis of the Cyber Attack on the Ukrainian Power Grid.” TLP White. Washington, DC: E-ISAC and SANS. https://ics.sans.org/media/E-ISAC_SANS_Ukraine_DUC_5.pdf.
Levite, A.E., S. Kannry, and W. Hoffman. 2018. “Addressing the Private Sector Cybersecurity Predicament: The Indispensable Role of Insurance.” Carnegie Endowment for International Peace Working Paper. https://carnegieendowment.org/files/Cyber_Insurance_Formatted_FINAL_WEB.PDF.
Leszczyna, R. 2018. A review of standards with cybersecurity requirements for smart grid. Computers and Security 77 (August):262–276. https://doi.org/10.1016/j.cose.2018.03.011.
Maguire, M. 2001. Methods to support human-centred design. International Journal of Human-Computer Studies 55:587–634.
Maynard, P., K. McLaughlin, and S. Sezer. 2020. Decomposition and sequential-AND analysis of known cyber-attacks on critical infrastructure control systems. Journal of Cybersecurity 6(1):tyaa020. https://doi.org/10.1093/cybsec/tyaa020.
McFarland, C.K., B. Rivett, K. Funk, R. Kim, and S. Wagner. 2020. State and Local Partnerships for Cybersecurity: A State-by-State Analysis. Washington, DC: National League of Cities. https://www.nlc.org/wp-content/uploads/2020/04/SML_2020Report_web-1.pdf.
McGraw, G., S. Migues, and B. Chess. 2017. “Four CISO Tribes and Where to Find Them.” CISO Report. https://www.garym-cgraw.com/wp-content/uploads/2018/01/CISO-2017.pdf.
Miller, S. 2020. “Insider Threat Incidents: Assets Targeted by Malicious Insiders.” Insider Threat (blog). September 29. https://insights.sei.cmu.edu/insider-threat/2020/09/insider-threat-incidents-assets-targeted-by-malicious-insiders.html.
NASA (National Aeronautics and Space Administration). 2014. Human Integration Design Handbook (HIDH). NASA/SP-2010-3407/REV1. Washington, DC.
NASEM (National Academies of Sciences, Engineering, and Medicine). 2017. Enhancing the Resilience of the Nation’s Electricity System. Washington, DC: National Academies Press. https://doi.org/10.17226/24836.
NASEM. 2020. Communications, Cyber Resilience, and the Future of the U.S. Electric Power System: Proceedings of a Workshop. Washington, DC: National Academies Press. https://doi.org/10.17226/25782.
NASCIO and NGA (National Association of State Chief Information Officers and National Governors Association). 2020. Stronger Together: State and Local Cybersecurity Collaboration. https://www.nga.org/wp-content/uploads/2020/01/NASCIO_NGAStatesLocalCollaboration.pdf.
NATF (North American Transmission Forum). 2020. “NATF RESTORE Program Frequently Asked Questions (FAQ).” https://www.natf.net/docs/natf/documents/natf-restore-program-faq.pdf.
National Commission on Grid Resilience. 2020. “Grid Resilience: Priorities for the Next Administration.” https://gridresilience.org/wp-content/uploads/2020/11/NCGR-Report-2020-Full-v2.pdf.
Navigant Research. 2020. “Global Annual Market for Energy IT and Cybersecurity for Software and Services Is Expected to Reach $32 Billion by 2028.” February 11. https://www.navigantresearch.com/news-and-views/global-annual-marketfor-energy-it-and-cybersecurity-for-software-and-services-is-expected-to-reach.
NERC (North American Electric Reliability Corporation). n.d. “United States Mandatory Standards Subject to Enforcement.” NERC. https://www.nerc.com/pa/stand/Pages/ReliabilityStandardsUnitedStates.aspx?jurisdiction=United%20States.
NERC. 2015. “Project 2014-04 Physical Security.” NERC. May 7. https://www.nerc.com/pa/Stand/Pages/Project-2014-04-Physical-Security.aspx.
NERC. 2019a. “EMP Task Force: Strategic Recommendations.” NERC. November 5. https://www.nerc.com/pa/Stand/EMP%20Task%20Force%20Posting%20DL/NERC_EMP_Task_Force_Report.pdf.
NERC. 2019b. “Lesson Learned: Risks Posed by Firewall Firmware Vulnerabilities.” NERC. https://www.nerc.com/pa/rrm/ea/Lessons%20Learned%20Document%20Library/20190901_Risks_Posed_by_Firewall_Firmware_Vulnerabilities.pdf.
NERC. 2019c. “NERC Full Notice of Penalty Regarding FERC Docket No. NP19-000.” Via electronic filing, January 25. https://www.nerc.com/pa/comp/CE/Enforcement%20Actions%20DL/Public_FinalFiled_NOP_NOC-2605_Part%201.pdf.
NERC. 2020. Compliance Monitoring and Enforcement Program Annual Report. Washington, DC: NERC. https://www.nerc.com/pa/comp/CE/ReportsDL/2019%20Annual%20CMEP%20Report.pdf.
NIAC (National Infrastructure Advisory Council). 2010. “A Framework for Establishing Critical Infrastructure Resilience Goals: Final Report and Recommendations by the Council.” https://www.dhs.gov/xlibrary/assets/niac/niac-a-framework-for-establishing-critical-infrastructure-resilience-goals-2010-10-19.pdf.
NIST (National Institute of Standards and Technology). 2014. “Guidelines for Smart Grid Cybersecurity.” Interagency Report 7628 Rev. 1, Vol. 1. http://dx.doi.org/10.6028/NIST.IR.7628r1.
NIST. 2017. “Cybersecurity Framework.” Text. NIST. March 13. https://www.nist.gov/industry-impacts/cybersecurity-framework.
NIST. 2018a. “Cybersecurity Is Everyone’s Job.” October. https://www.nist.gov/itl/applied-cybersecurity/nice/workforce-management-guidebook.
NIST. 2018b. “Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1.” NIST CSWP 04162018. Gaithersburg, MD: National Institute of Standards and Technology. https://doi.org/10.6028/NIST.CSWP.04162018.
NIST. 2020. “President’s FY 2021 Budget Request to Congress for the National Institute of Standards and Technology.” February 11. https://www.nist.gov/system/files/documents/2020/02/11/FY2021-NIST-Budget-Book.pdf.
NITRD (Networking and Information Technology Research and Development Program). 2019a. “About the NITRD Program.” December 30. https://www.nitrd.gov/about/.
NITRD. 2019b. “FY 2020 Federal Cybersecurity R&D Strategic Plan Implementation Roadmap: Appendix to the Networking and Information Technology Research and Development Program Supplement to the President’s FY 2020 Budget.” Product of the Cybersecurity and Information Assurance Interagency Working Group. September. https://www.nitrd.gov/pubs/FY2020-Cybersecurity-RD-Roadmap.pdf.
North American Transmission Forum. 2020. “Strengthen Your Transmission Resilience.” TRMM (Transmission Resilience Maturity Model). December 7. https://trmm.labworks.org/.
NRC (National Research Council). 2007. Toward a Safer and More Secure Cyberspace. Washington, DC: National Academies Press. https://doi.org/10.17226/11925.
NRC. 2012. Terrorism and the Electric Power Delivery System. Washington, DC: National Academies Press. https://doi.org/10.17226/12050.
NRC. 2014. At the Nexus of Cybersecurity and Public Policy. Washington, DC: National Academies Press. https://doi.org/10.17226/18749.
NRC-NAE (National Research Council and National Academy of Engineering). 2007. Toward a Safer and More Secure Cyberspace. Washington, DC: National Academies Press.
NSTC (National Science and Technology Council). 2019. “National Space Weather Strategy and Action Plan.” https://aerospace.org/sites/default/files/2019-03/Natl%20Space%20Weather%20Strategy%20Mar19.pdf.
NSTC. 2020. Artificial Intelligence and Cybersecurity: Opportunities and Challenges: Technical Workshop Summary Report. Networking and Information Technology Research and Development Subcommittee and Machine Learning and Artificial Intelligence Subcommittee. March. https://www.nitrd.gov/pubs/AI-CS-Tech-Summary-2020.pdf.
Obert, J., P. Cordeiro, J. Johnson, G. Lum, T. Tansy, M. Pala, and R. Ih. 2019. Recommendations for Trust and Encryption in DER Interoperability Standards. SAND2019-1490, 1761841, 672487. Albequerque, NM: Sandia National Laboratories. https://doi.org/10.2172/1761841.
OCA (Open Cybersecurity Alliance). n.d. “Our Mission.” https://opencybersecurityalliance.org/mission/.
Office of the Inspector General of the Intelligence Community. 2019. Unclassified Joint Report on the Implementation of the Cybersecurity Information Sharing Act of 2015. AUD-2019-005-U. Washington, DC. https://www.oversight.gov/sites/default/files/oig-reports/Unclassified%2020191219_AUD-2019-005-U_Joint%20Report.pdf.
Olyaei, S., M. Coleman, and M.T. Stamper. 2018. “Adapt Your Traditional Staffing Practices for Cybersecurity.” Gartner. May 2. https://www.gartner.com/en/doc/3566417-adapt-your-traditional-staffing-practices-for-cybersecurity.
Overbye, T.J., et al. 2005. “Visualization of Power Systems and Components.” PSerc Publication 05-65. Power Systems Engineering Research Center.
Pala, A., and J. Zhuang. 2019. Information Sharing in Cybersecurity: A Review. Decision Analysis 16(3):172–196. https://doi.org/10.1287/deca.2018.0387.
PCCIP (President’s Commission on Critical Infrastructure Protection). 1997. Critical Foundations: Protecting America’s Infrastructures. Report of the President’s Commission on Critical Infrastructure Protection. Washington, DC. October.
Ross, R., V. Pillitteri, K. Dempsey, M. Riddle, and G. Guissanie. 2021. “Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations.” NIST Special Publication (SP) 800-171 Rev. 2. National Institute of Standards and Technology. https://doi.org/10.6028/NIST.SP.800-171r2.
SAINT Consortium. 2018. “Report on Cost-Benefit Analysis of Cyber-Security Solutions, Products, and Models.” D4.4 V1.0 WP 4. https://project-saint.eu/sites/default/files/d4.4.pdf.
SEI (Software Engineering Institute). n.d. “Insider Threat | Our Work.” Carnegie Mellon University. n.d. https://www.sei.cmu.edu/our-work/insider-threat/index.cfm.
Shea, D. 2020. “Cybersecurity and the Electric Grid.” Energy. Washington, DC: National Conference of State Legislatures. https://www.ncsl.org/Portals/1/Documents/energy/Cybersecurity-Electric-Grid_v04.pdf.
Simon, H. 1991. “Bounded Rationality and Organizational Learning.” Organizational Science. Vol. 2, No. 1. https://doi.org/10.1287/orsc.2.1.125.
Smallwood, A. 2017. “OpenFMB Charts New Paths for Grid-Edge Interoperability and Communication.” SEPA. July 20, 2017. https://sepapower.org/knowledge/openfmb-charts-new-paths/.
Smart Grid Interoperability Panel-Smart Grid Cybersecurity Committee. 2014. “Guidelines for Smart Grid Cybersecurity.” NIST Internal or Interagency Report (NISTIR) 7628 Rev. 1. National Institute of Standards and Technology. https://doi.org/10.6028/NIST.IR.7628r1.
Sobczak, B. 2018. “Grid Planners Put ‘Black Start’ Technology to the Test.” November 13. https://www.eenews.net/stories/1060106027.
Sobczak, B., and P. Behr. 2019. “Duke Agreed to Pay Record Fine for Lax Security—Sources.” E&E News. February 1. https://www.eenews.net/stories/1060119265.
Soltan S., P. Mittal, and H.V. Poor. 2018. “BlackIoT: IoT Botnet of High-Wattage Devices Can Disrupt the Power Grid.” In Proceedings USENIX Security ’18, August.
Soltan, S., P. Mittal, and V. Poor. 2019. Protecting the grid against MAD attacks. IEEE Transactions on Network Science and Engineering. https://doi.org/10.1109/TNSE.2019.2922131.
Stellios, I., P. Kotzanikolaou, M. Psarakis, C. Alcaraz, and J. Lopez. 2018. A Survey of IoT-enabled cyberattacks: Assessing attack paths to critical infrastructures and services. IEEE Communications Surveys and Tutorials 20(4):3453–3495. https://doi.org/10.1109/COMST.2018.2855563.
Stoll, C. 1989. The Cuckoo’s Egg: Tracking a Spy Through the Maze of Computer Espionage. New York, NY: Doubleday. Stouffer, K., S. Lightman, V. Pillitteri, M. Abrams, and A. Hahn. 2015. “Guide to Industrial Control Systems (ICS) Security.” NIST Special Publication (SP) 800-82 Rev. 2. National Institute of Standards and Technology. https://doi.org/10.6028/NIST.SP.800-82r2.
Sullivan, J.E., and D. Kamensky. 2017. How cyber-attacks in Ukraine show the vulnerability of the U.S. power grid. Electricity Journal 30(3):30–35. https://doi.org/10.1016/j.tej.2017.02.006.
Unit 42 by Palo Alto Networks. 2020. “Executive Summary: Unit 42 Cloud Threat Report.” Cloud Threat Report. https://thelevantnews.com/wp-content/uploads/2020/02/digital-executive-summary-unit-42-cloud-threat-report-spring-2020.pdf.
Utility Dive. 2019. “State of the Electric Utility Survey 2019.” https://resources.industrydive.com/State-of-the-Electric-Utility-2019-Survey-Report.
Uzunov, A.V. 2016. A survey of security solutions for distributed publish/subscribe systems. Computers and Security 61 (August):94–129. https://doi.org/10.1016/j.cose.2016.04.008.
Wilshusen, G.C. 2018. “Information Security: Supply Chain Risks Affecting Federal Agencies.” Testimony Before the Subcommittees on Counterterrorism and Intelligence, and Oversight and Management Efficiency, Committee on Homeland Security, House of Representatives. July 12. https://www.gao.gov/products/GAO-18-667T.
ANNEX 6.A: CYBERSECURITY JURISTICTIONS, CAPABILITY BASELINES, AND STANDARDS
TABLE 6.A.1 Congressional Committees with Jurisdiction over Cybersecurity
| Congressional Committee or Caucus | Key Subcommittees Addressing Cybersecurity Topics | Relevant Agencies |
|---|---|---|
|
Senate—Commerce, Science, and Transportation |
Subcommittee on Communications, Technology, Innovation, and the Internet Subcommittee on Manufacturing, Trade, and Consumer Protection Subcommittee on Security |
Department of Commerce Department of Defense Department of Energy Department of Homeland Security Department of Transportation Federal Communications Commission Transportation Security Administration |
|
Senate—Homeland Security and Governmental Affairs |
Permanent Subcommittee on Investigations |
Central Intelligence Agency Department of Defense Department of Homeland Security National Security Agency |
|
Senate—Energy and Natural Resources |
Subcommittee on Energy |
Department of Energy Department of the Interior |
|
House—Homeland Security |
Subcommittee on Cybersecurity, Infrastructure Protection, and Innovation |
Central Intelligence Agency Department of Defense Department of Homeland Security National Security Agency |
|
House—Energy and Commerce |
Subcommittee on Communications and Technology Subcommittee on Consumer Protection and Commerce Subcommittee on Energy |
Department of Commerce Department of Energy Federal Communications Commission |
|
House—Permanent Select Committee on Intelligence |
Strategic Technologies and Advanced Research Subcommittee Counterterrorism, Counterintelligence, and Counterproliferation (C3) Subcommittee Intelligence Modernization and Readiness Subcommittee Defense Intelligence and Warfighter Support Subcommittee |
Central Intelligence Agency Department of Defense Department of Homeland Security National Security Agency |
|
House—Oversight and Reform |
Subcommittee on Economic and Consumer Policy Subcommittee on Government Operations Subcommittee on National Security |
Department of Commerce Department of Defense Department of Homeland Security General Services Administration |
|
House—Science, Space and Technology |
Subcommittee on Energy Subcommittee on Research and Technology |
Department of Defense Department of Energy |
|
House—Transportation and Infrastructure |
Subcommittee on Aviation Subcommittee on Coast Guard and Maritime Transportation Subcommittee on Economic Development, Public Buildings, and Emergency Management Subcommittee on Railroads, Pipelines, and Hazardous Materials |
Department of Defense Department of Energy Department of Homeland Security Department of Transportation General Services Administration Transportation Security Administration |
|
Congressional Cybersecurity Caucus |
Department of Defense Department of Homeland Security |
TABLE 6.A.2 The Core Device Cybersecurity Capability Baseline for Securable Internet of Things (IoT) Devices
| Device Cybersecurity Capability | Key Elements |
|---|---|
| Device Identification: The IoT device can be uniquely identified logically and physically. |
Note: the physical and logical identifiers may represent the same value, but they do not have to. |
| Device Configuration: The configuration of the IoT device’s software and firmware can be changed, and such changes can be performed by authorized entities only. |
|
| Data Protection: The IoT device can protect the data it stores and transmits from unauthorized access and modification. |
|
| Logical Access to Interfaces: The IoT device can restrict logical access to its local and network interfaces, and the protocols and services used by those interfaces, to authorized entities only. |
|
| Software and Firmware Update: The IoT device’s software and firmware can be updated by authorized entities only using a secure and configurable mechanism. |
|
| Cybersecurity State Awareness: The IoT device can report on its cybersecurity state and make that information accessible to authorized entities only. |
|
SOURCE: M. Fagan, K.N. Megas, K. Scarfone, and M. Smith, 2020, IoT Device Cybersecurity Capability Core Baseline, NIST IR 8259A, Gaithersburg, MD: National Institute of Standards and Technology, https://doi.org/10.6028/NIST.IR.8259a.
TABLE 6.A.3 Examples of Cybersecurity Standards, Guidelines, and Frameworks
| Organization | Standards, Guidelines, and Frameworks |
|---|---|
| North American Electric Reliability Corporation (NERC) | Designated by FERC as the Electric Reliability Organization (ERO), NERC develops mandatory Critical Infrastructure Protection (CIP) standards for the bulk electric system. |
| Rural Utilities Service, U.S. Department of Agriculture |
Provides guidance for emergency restoration including cybersecurity for rural utilities through Bulletin 1730B-2, RD-GD-2005-51: Guide for Electric System Emergency Restoration Plan https://www.rd.usda.gov/files/UEP_Bulletin_1730B-2.pdf. |
| National Institute of Standards and Technology (NIST), U.S. Department of Commerce |
The goal of NIST is to promote U.S. innovation and industrial competitiveness by advancing measurement science, standards, and technology. Examples of NIST publications and voluntary standards for cybersecurity include the following:
|
| Institute of Electrical and Electronics Engineers (IEEE) |
A professional organization dedicated to advancing technological innovation and excellence for the benefit of humanity. IEEE standards on cybersecurity include the following:
|
| International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) |
|
| Internet Engineering Task Force (IETF) |
International community of network designers, operators, vendors, and researchers with a mission of developing open standards to make the Internet work better. The IETF Security Area has more than 20 working groups. https://www.ietf.org/topics/security/ |
| Organization | Standards, Guidelines, and Frameworks |
|---|---|
| International Society for Automation (ISA) |
Nonprofit professional association that develops standards, educational materials and products for automation technologies, including the ISA/IEC 62443 Industrial Automation and Control Systems Security series of standards, a framework to address and mitigate security vulnerabilities in industrial automation and control systems. https://www.isa.org/ |
| International Telecommunications Union (ITU) |
The United Nations specialized agency for information and communication technologies (ICT). ITU allocates global radio spectrum and satellite orbits, develops technical standards that ensure networks and technologies seamlessly interconnect, and strives to improve access to ICTs to underserved communities worldwide. https://www.itu.int/en/Pages/default.aspx |
| Organization for the Advancement of Structure Information Standards (OASIS) |
Nonprofit international standards body focused on open source and open standards for developing code, APIs, specifications, or reference implementations including Web services security. Launched the Open Security Alliance in 2019 to develop and promote sets of open-source common content, code, tooling, patterns and practices to maximize interoperability and the sharing of data among cybersecurity tools. https://www.oasis-open.org/ |
| SunSpec Alliance |
Alliance of stakeholders to specify de facto standards—information models, data formats, communication protocols, system interfaces, best practices and other artifacts—that enable solar PV and energy storage Distributed Energy power plants to interoperate transparently with system components, software applications, financial systems, and the Smart Grid. https://sunspec.org/ |
| American National Standards Institute (ANSI) |
ANSI sponsors cybersecurity related working groups and provides access to a wide range of cybersecurity standards. https://webstore.ansi.org/ |
| UL |
Supports the production and use of physically and environmentally safe products to prevent or reduce loss of life and property. National Certification Body (NCB) and CB Test Lab (CBTL) for the IEC 62443 standards and develops proprietary standards. https://www.ul.com/ |
| Payment Card Industry Data Security Standard (PCI DSS) |
Developed by the Payment Card Industry, the PCI DSS is a voluntary commercial standard that sets the operational and technical requirements for organizations accepting or processing payment transactions, and for software developers and manufacturers of applications and devices used in those transactions. All entities that accept or process payment cards are required to follow the PCI DSS. https://www.pcisecuritystandards.org/ |
























































